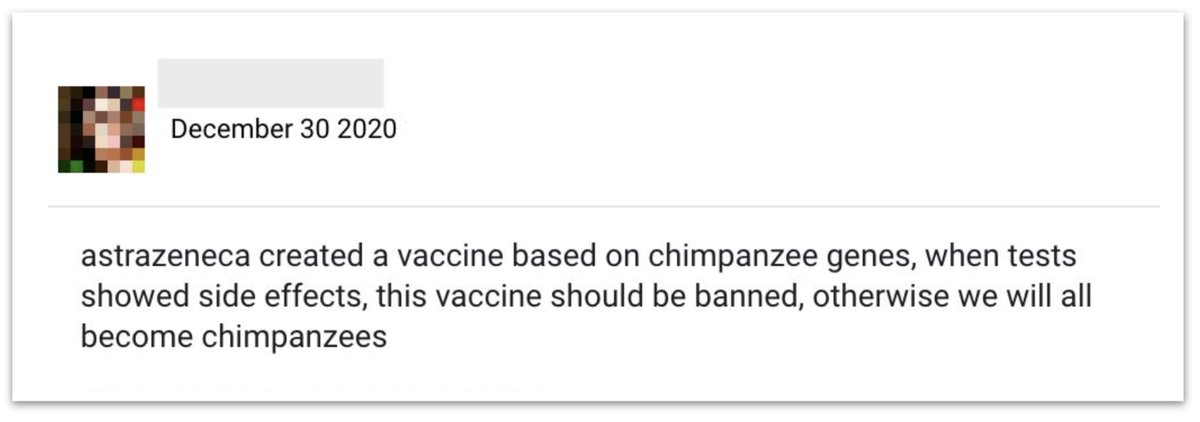
JUST OUT: In-depth report on the #Fazze case — a campaign from Russia targeting primarily India and LATAM, and to a lesser extent the US.
It was focused on the Pfizer and AstraZeneca COVID-19 vaccines, but got close to zero traction across the internet.
about.fb.com/news/2021/08/j…
It was focused on the Pfizer and AstraZeneca COVID-19 vaccines, but got close to zero traction across the internet.
about.fb.com/news/2021/08/j…
There’s already been reporting on the Pfizer phase, in May (h/t @daniellaufer, @toniodaoust, @FloraCarmichael, @charliehtweets, @arawnsley).
Our investigation uncovered that in December, the same op targeted AstraZeneca.
Our investigation uncovered that in December, the same op targeted AstraZeneca.
We attributed this operation to Fazze, a marketing firm primarily operating from Russia.
It functioned as a disinformation laundromat.
It’d start by planting content on a few online forums. It then amplified that content on other platforms, including social media, with the basic message, “Look what I found on the internet!”
It’d start by planting content on a few online forums. It then amplified that content on other platforms, including social media, with the basic message, “Look what I found on the internet!”

The message was boosted by a couple of hundred spammy Instagram accounts that pushed out similar memes with hashtags in English or Portuguese.
A lot of the memes with Portuguese hashtags had Hindi text. Maybe not surprisingly, the vast majority got zero likes.
A lot of the memes with Portuguese hashtags had Hindi text. Maybe not surprisingly, the vast majority got zero likes.

A handful of influencers in India and LATAM appeared to amplify the same message and hashtags at the same time.
That fits the pattern from May 2021, when the op reportedly offered to pay influencers for amplification.
An influencer operation, not just an influence operation.
That fits the pattern from May 2021, when the op reportedly offered to pay influencers for amplification.
An influencer operation, not just an influence operation.
The operation went silent until May, when it began focusing on the Pfizer vaccine.
Again, this was a cross-platform effort, with blogs and long-form articles across over a dozen platforms.
Again, this was a cross-platform effort, with blogs and long-form articles across over a dozen platforms.

We know from open-source reporting that the operation tried to recruit influencers. But we also know that it backfired: two of the influencers went public.
bbc.com/news/blogs-tre…
bbc.com/news/blogs-tre…
That highlights the dilemma for influence operations. Do you go for low-impact tactics and stay hidden, or do you go for the big bang of influencers with built-in audiences, and risk having your operation exposed?
https://twitter.com/dirtybiology/status/1396719090321010688
Final point: there’s been awesome research into this operation by the open-source community, and we owe the initial exposure to @dirtybiology and @mrwissen2go.
Hats off to all of them for breaking the ground on this one.
Hats off to all of them for breaking the ground on this one.
• • •
Missing some Tweet in this thread? You can try to
force a refresh