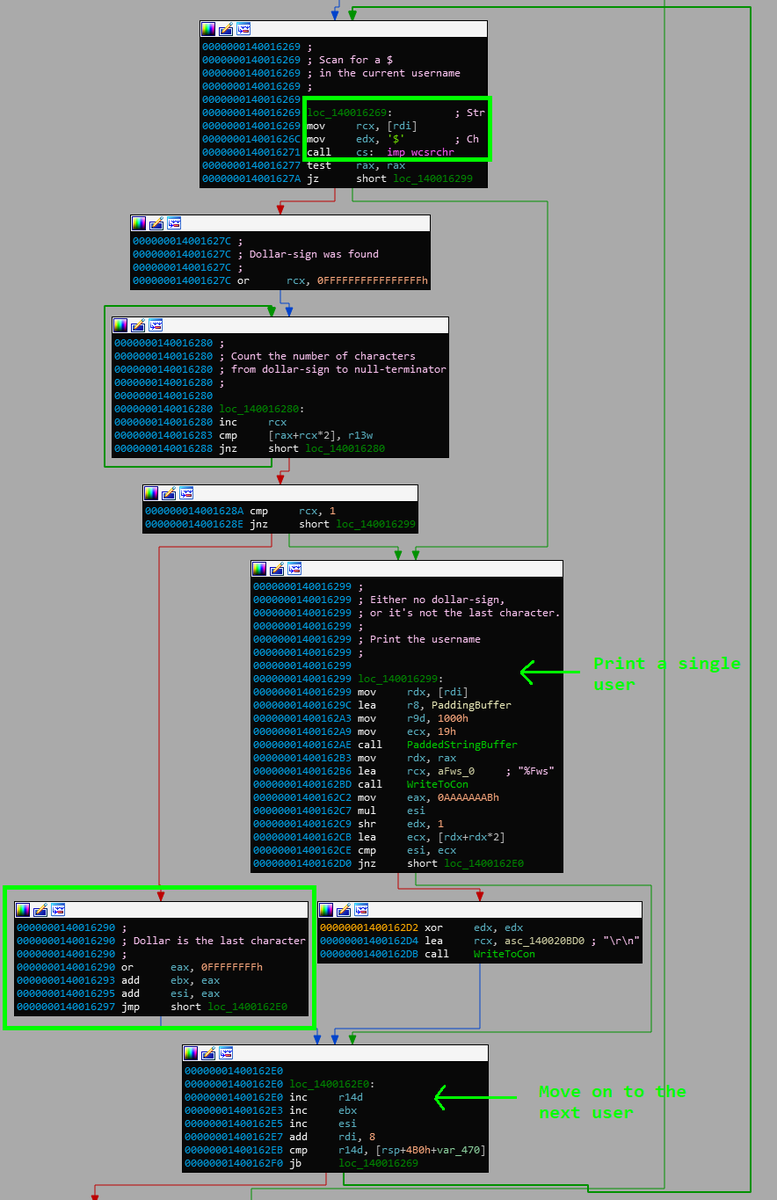
I swear I couldn't find one place in the internet where #PetitPotam is explained in a way that I can truly understand it. So I'm dumping the attack flow here as a future reference for myself. If any of you finds it useful - good. If any of you wishes to add - comment. 1/7 

The attack starts when an attacker, from her controlled machine, triggers a (possibly privileged) Windows host to authenticate to *her*. She does it by requesting EFS-RPC - Encrypted File System service - to open a remote file on her own machine. No domain creds are needed! 2/7
Technically speaking, the attacker invokes EfsRpcOpenFileRaw, specifying a file path that points to her remote machine:
'\\<attacker_address>\test\Settings.ini'
(from @topotam77's PoC
github.com/topotam/PetitP…)
This is basically the essence of #PetitPotam.
3/7
'\\<attacker_address>\test\Settings.ini'
(from @topotam77's PoC
github.com/topotam/PetitP…)
This is basically the essence of #PetitPotam.
3/7
Next, the attacker performs an NTLM Relay attack against AD-CS (Active Directory Certificate Services) and "impersonates" the victim machine.
This part is based on @SpecterOps's findings (ESC8 in posts.specterops.io/certified-pre-…) and isn't PetitPotam-specific.
[img: @HackAndDo] 4/7
This part is based on @SpecterOps's findings (ESC8 in posts.specterops.io/certified-pre-…) and isn't PetitPotam-specific.
[img: @HackAndDo] 4/7

2 services in AD-CS are vulnerable to NTLM Relay:
1. CA Web Enrollment
2. Certificate Enrollment Web Service
With her (privileged) access to these services, the attacker requests a new certificate, thus obtaining *persistent* privileged access to other services & resources. 5/7
1. CA Web Enrollment
2. Certificate Enrollment Web Service
With her (privileged) access to these services, the attacker requests a new certificate, thus obtaining *persistent* privileged access to other services & resources. 5/7
So basically 2 services are exploited:
* EFS-RPC, as one can coerce it into performing authentication;
* One of the AD-CS services mentioned above, as they don't have NTLM relay protection enabled by default. Any other service prone to NTLM relay can be exploited instead. 6/7
* EFS-RPC, as one can coerce it into performing authentication;
* One of the AD-CS services mentioned above, as they don't have NTLM relay protection enabled by default. Any other service prone to NTLM relay can be exploited instead. 6/7
Thanks @oridavid123 and @kupsul, my two goto people in @Guardicore for everything related to Windows domain attacks ♥ 7/7
I wish to clarify: PetitPotam stands for only arrows (1) and (2), namely, the part where an attacker makes EFS-RPC initiate NTLM authentication. Thanks @wdormann for highlighting this.
• • •
Missing some Tweet in this thread? You can try to
force a refresh