[#thread 🧵] I've released a tool to automatically extract, parse #windows build numbers from #ISO files in order to automatically sort them 🥳🎉
This is pretty useful if, let's say, you have a few Terabytes of ISOs 😏
github.com/p0dalirius/Win…
This is pretty useful if, let's say, you have a few Terabytes of ISOs 😏
github.com/p0dalirius/Win…
[#thread 🧵(2/4)] With this tool, you can automatically sort your ISO files in folders sorted by build numbers like this: 

[#thread 🧵(3/4)] How does this work ?
Simple! This tool mounts the ISO file to a temporary location, and extract the xml file [1].xml from the Windows imaging (WIM) image in ./sources/boot.wim:
Simple! This tool mounts the ISO file to a temporary location, and extract the xml file [1].xml from the Windows imaging (WIM) image in ./sources/boot.wim:

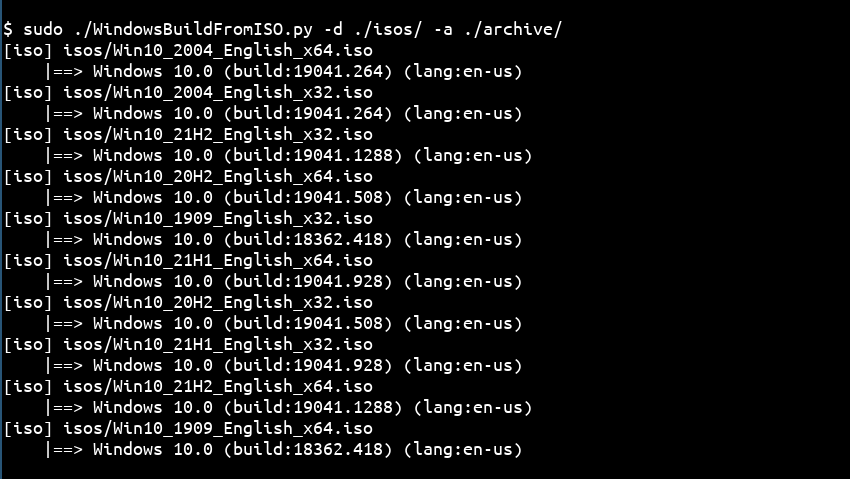
[#thread 🧵(4/4)] You can also use the tool to identify build numbers on a batch of ISO files without moving or renaming them: 
• • •
Missing some Tweet in this thread? You can try to
force a refresh