UPDATE: I reached the person who claims to have hacked Optus. I've also been contacted by a second, separate source who says the hacker's version of events is approximately correct. Here's what they said. #OptusHack #infosec #auspol
The Optus hacker says they accessed an unauthenticated API endpoint. This means they didn't have to login. The person says: "No authenticate needed. That is bad access control. All open to internet for any one to use." #infosec #auspol 
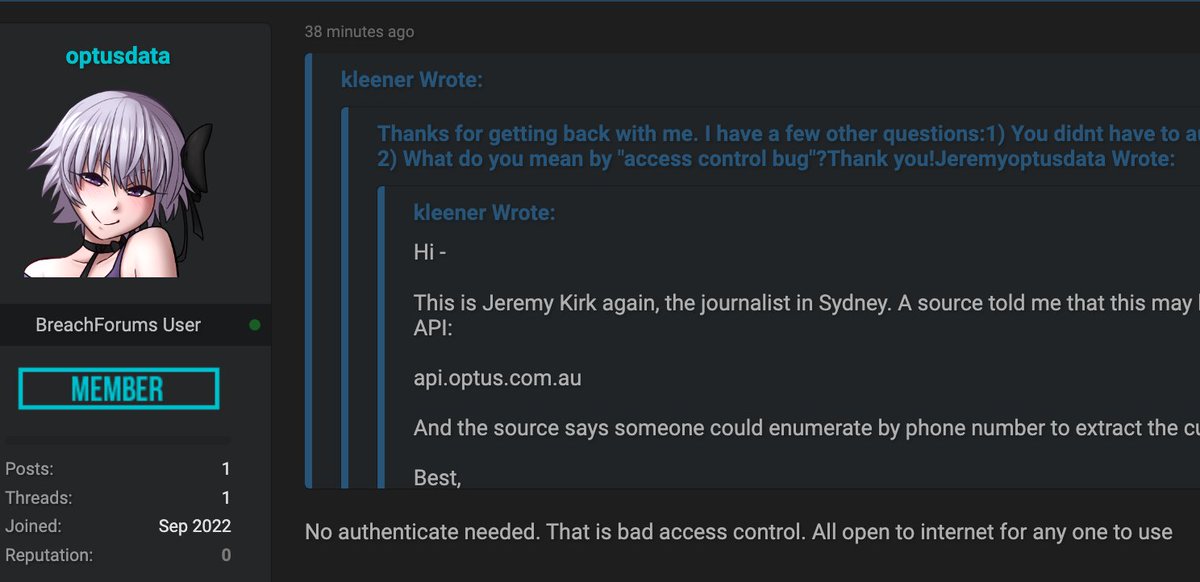
The API endpoint was api[dot]optus.com.au. Yes, that looks weird, but the hacker says it worked otherwise a DNS error occurred. That API is now offline, so there is no more risk for Optus. It was used in part to let Optus customers access their own data. 

That API address was passed to me by a second source. That was hosted in Google Cloud/Apigee. When the hacker started hitting that API hard, it triggered a security alert. In other words, a suspiciously high volume of data was coming from that API. #OptusHack
The hacker says they enumerated the customer records via the "contactid," which is a field that appears in the leaked data samples. Not sure exactly what the contactid is. By enumerating, the hacker means they accessed the records sequentially by the contactid. #OptusHack 

Here's a tidy news story that wraps up all my Optus data breach tweets. I've tried to make this understandable for everyone. It's important we understand how our personal data is at risk if not protected. #OptusHack #auspol #infosec bankinfosecurity.com/optus-under-1-…
Sorry I made a slight error when writing the URL for that API endpoint. It was: api.www[dot]optus.com.au.
• • •
Missing some Tweet in this thread? You can try to
force a refresh












