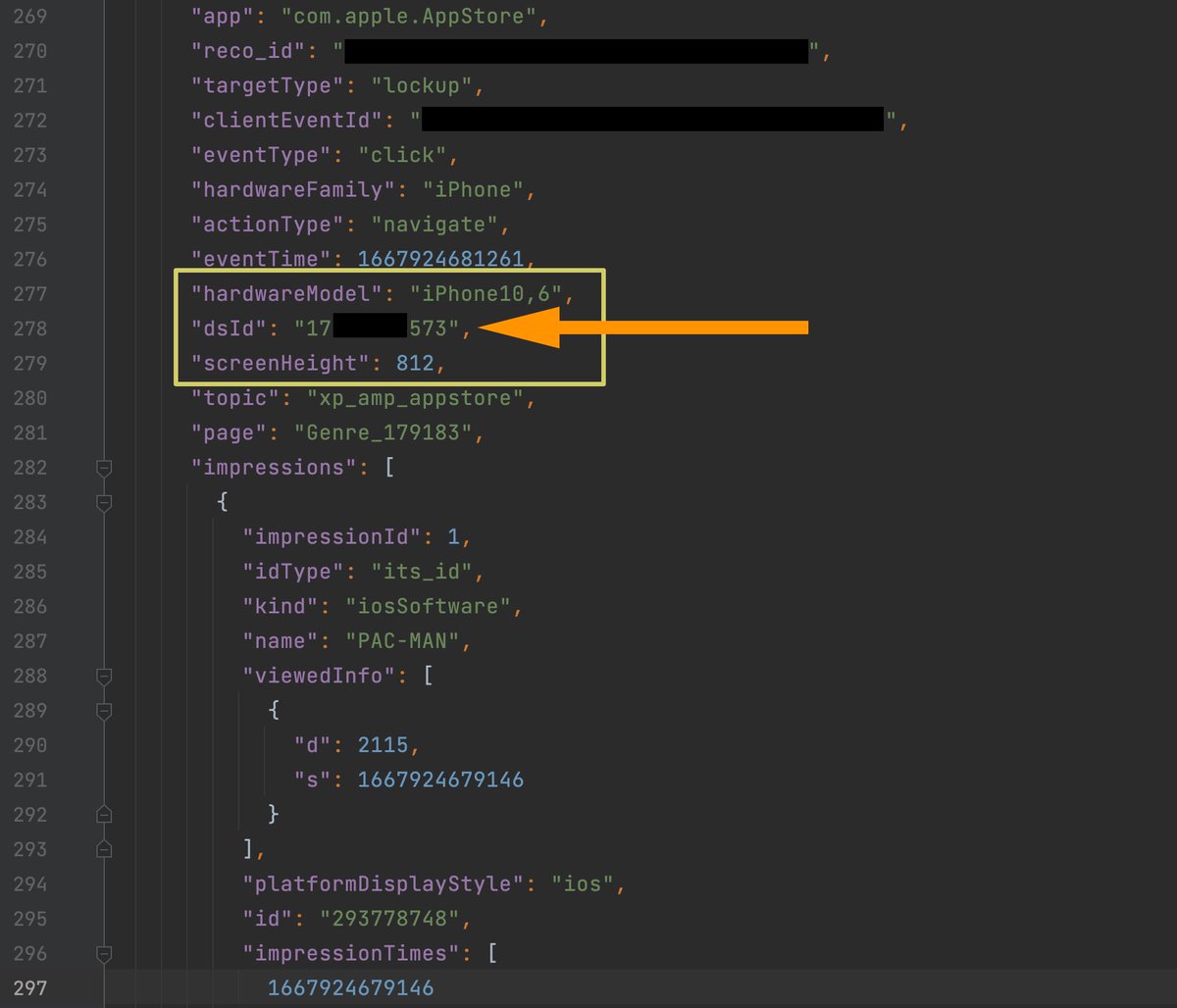
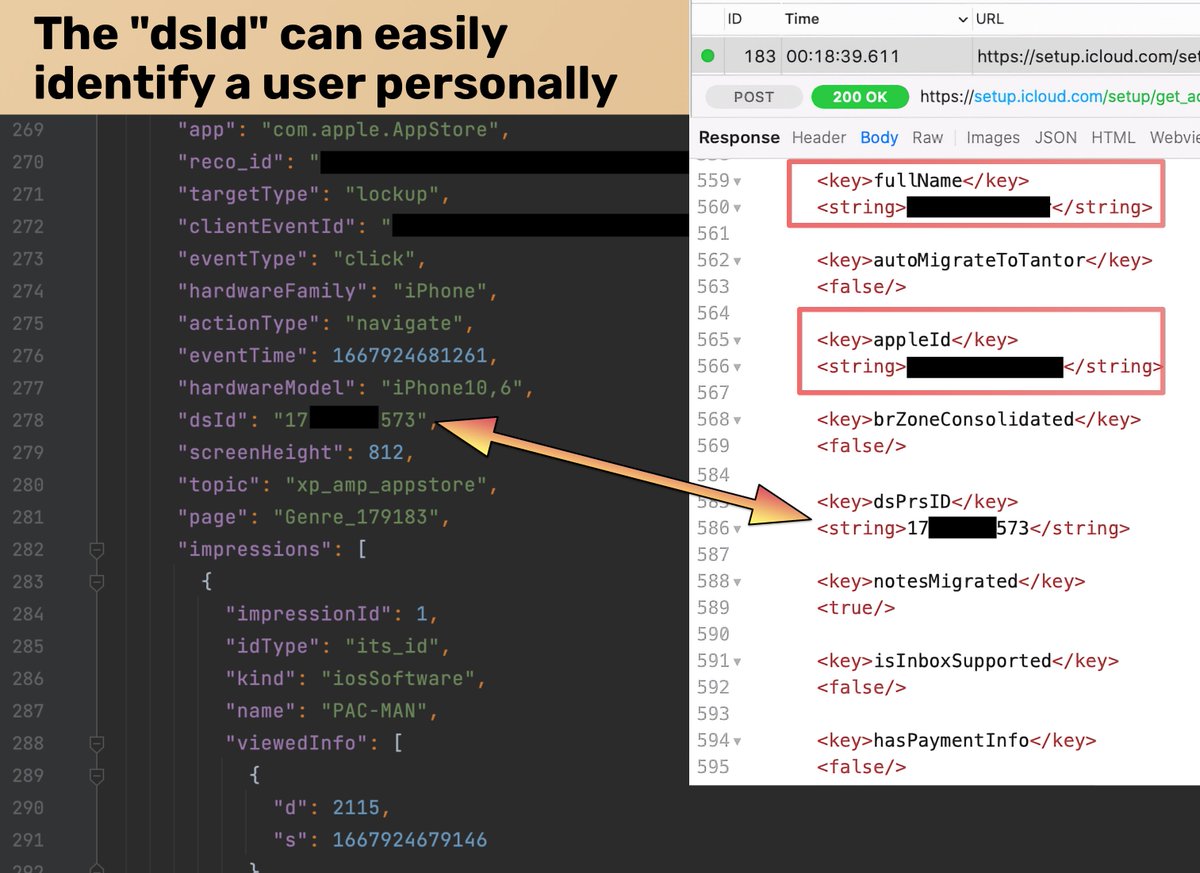
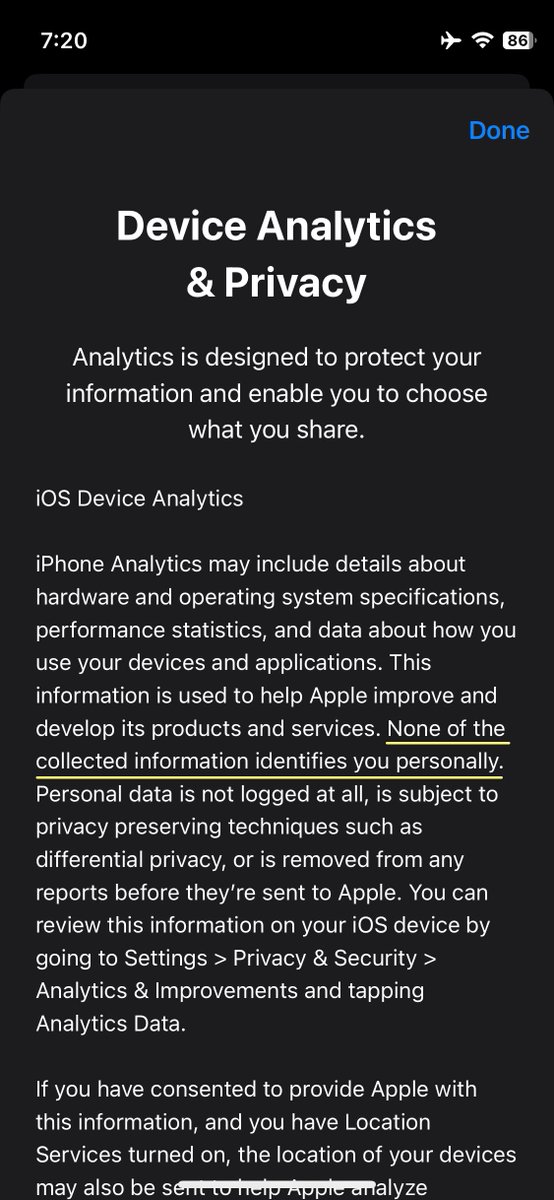
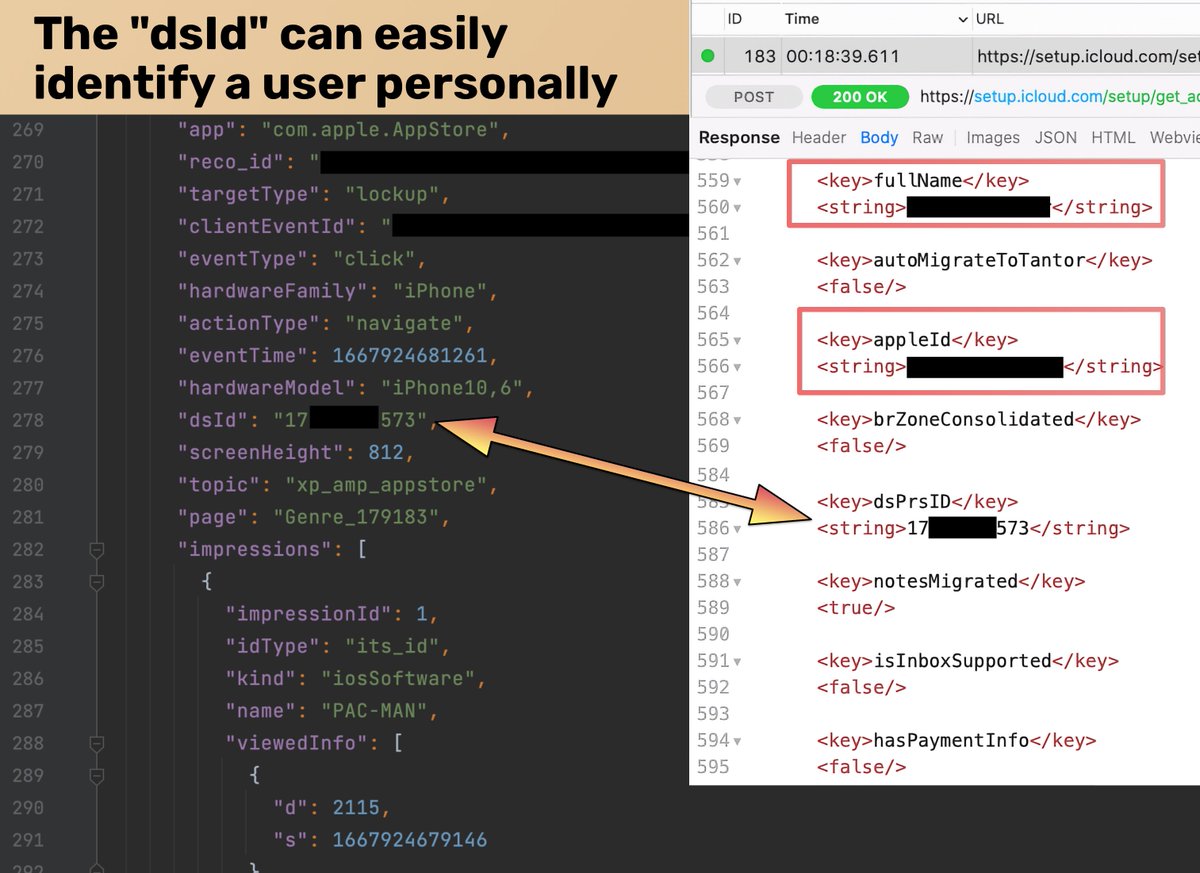
When you join a Wi-Fi network that shows a captive portal on the iPhone, iOS opens the captive portal in a Safari web view regardless of which default browser you've chosen.
This little experiment implements a captive portal that detects the browser. Brave was the default browser, but iOS opened the captive portal in Safari. The second screenshot shows what this sample website displays if opened with Brave.


This little experiment implements a captive portal that detects the browser. Brave was the default browser, but iOS opened the captive portal in Safari. The second screenshot shows what this sample website displays if opened with Brave.



• • •
Missing some Tweet in this thread? You can try to
force a refresh