How to get URL link on X (Twitter) App


 (2/6)
(2/6)




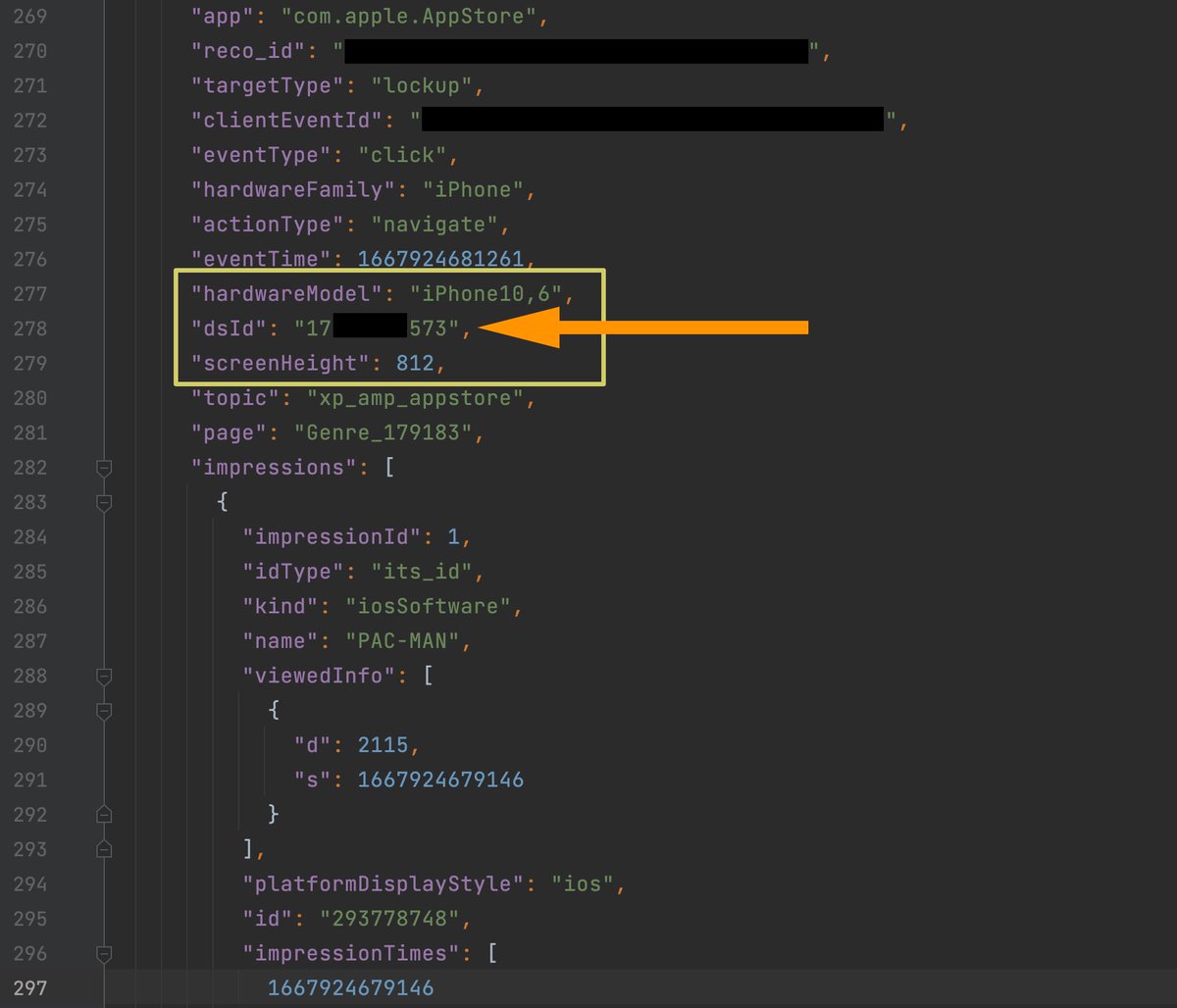
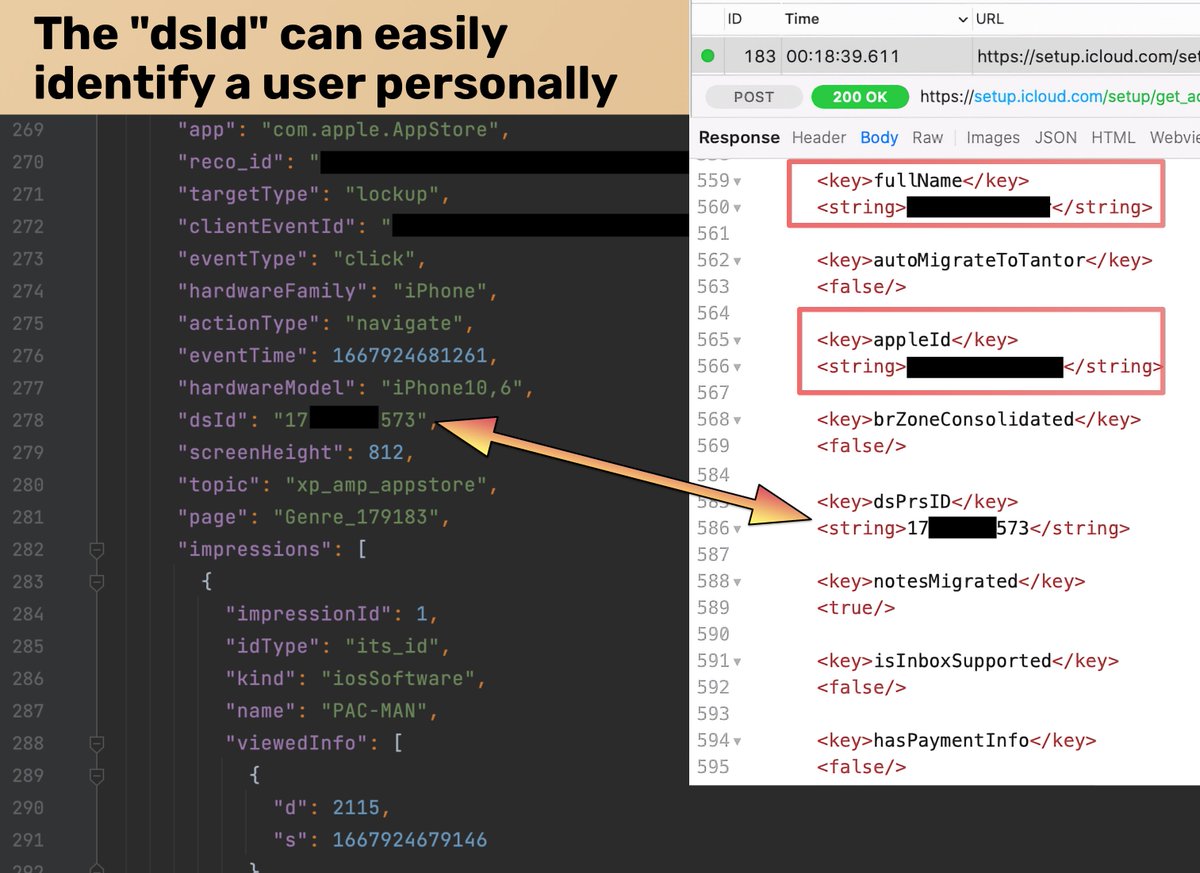
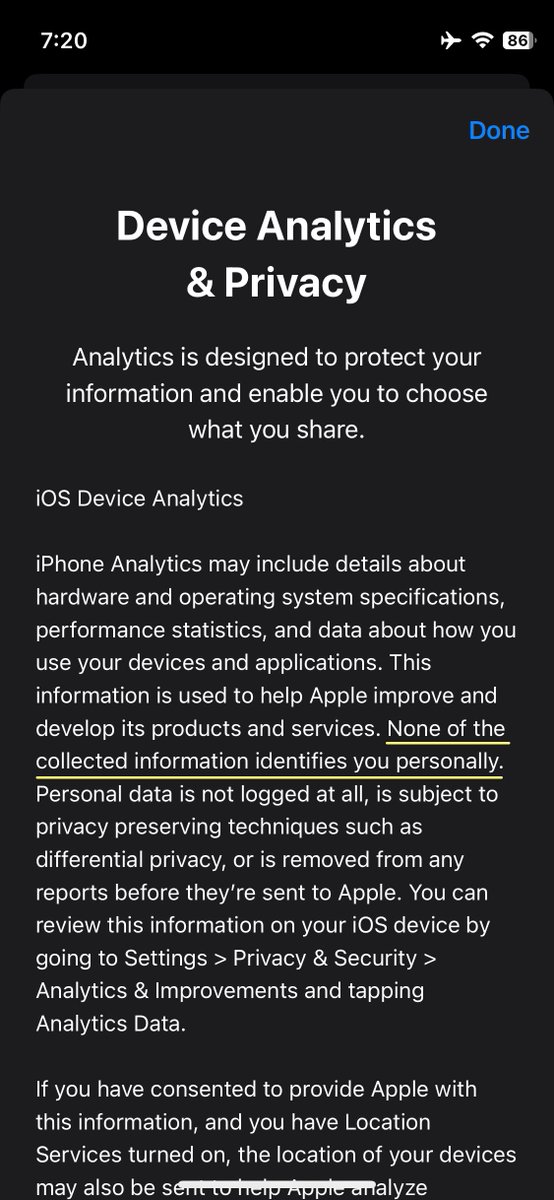 2/6
2/6


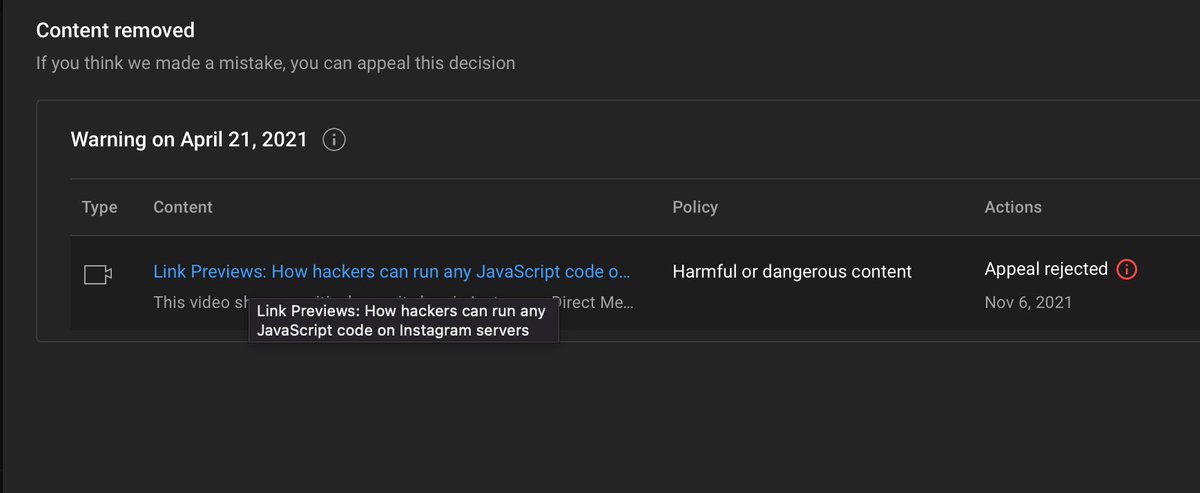 2/7
2/7



 2/6
2/6


https://twitter.com/mysk_co/status/1575242159132971016
