However...
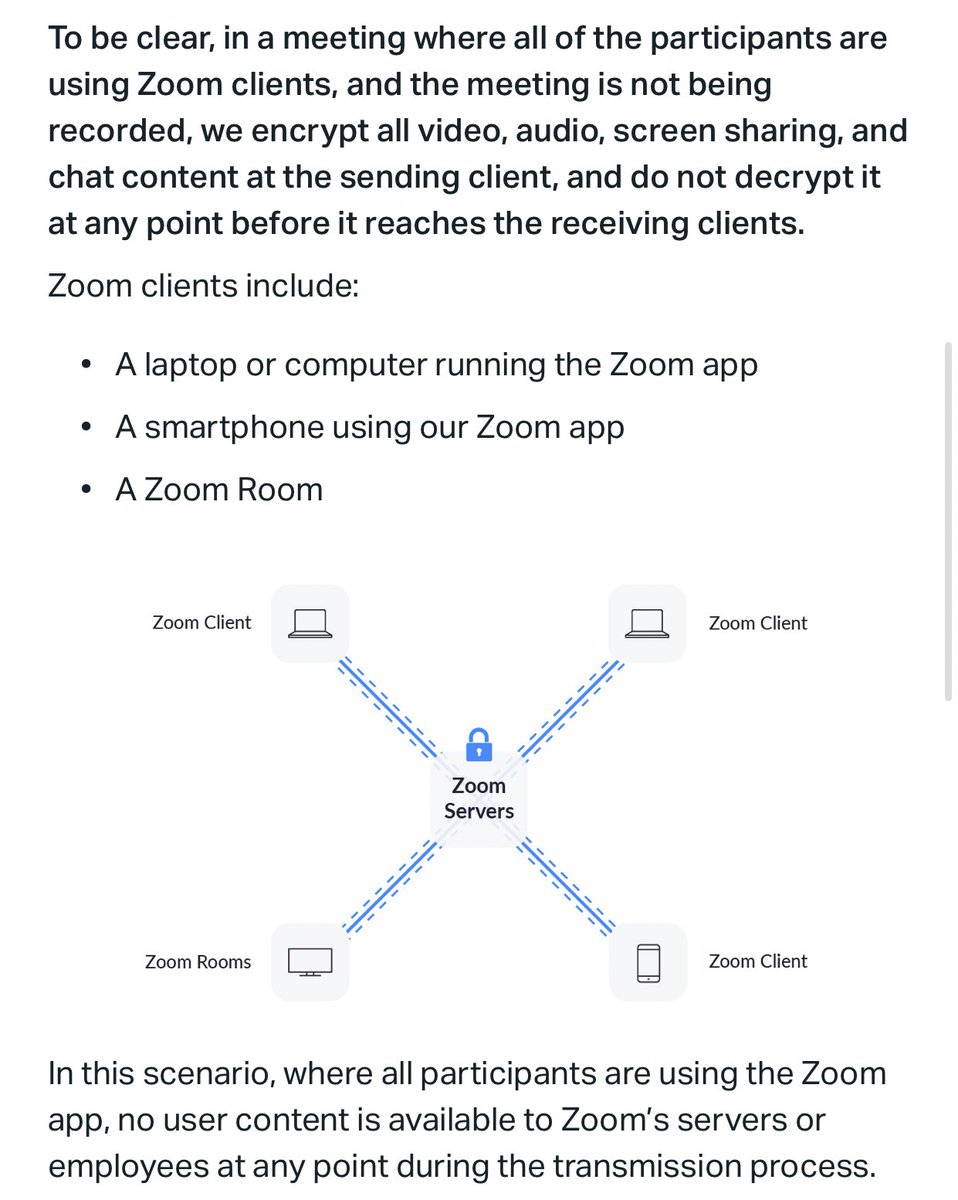
1. If users don’t have the explicit capability to control whether Zoom’s servers (bridges) get access, then it’s not really e2e.
2. If users can’t tell whether a Zoom server has access, then that’s not really e2e either.
Hopefully they’ll clear things up in the future. //
It’s not their fault they became a critical piece of software everyone needs to depend on. But that’s where they are, and they will hopefully rise to the occasion.