31 December 2020 #MAGAanalysis #Overturn
Comments on @OptimisticCon's Article - Part 3
As I forgot to give the link to the article, yesterday, let's get that covered right now!
libertyunyielding.com/2020/12/21/the…
Comments on @OptimisticCon's Article - Part 3
As I forgot to give the link to the article, yesterday, let's get that covered right now!
libertyunyielding.com/2020/12/21/the…
2) And here's yesterday's 85-tweet thread. Do mind that Twitter breaks it at #31. You have to hit "show replies" and then my bandaid shows up, where I reattached #34. Click on it and you should be able to go the distance.
https://twitter.com/ThyConsigliori/status/1344258328516587521?s=20
3) I'm not sure how the spirit will move me tomorrow morning, but assuming I can finish up our last 9 slides today, I may see if I can't organize the entire suite of threads I've completed on J.E.'s 2 articles to date. We'll see, but that's what I'm thinking right now.
4) Yesterday's work left a couple of dangling threads (of thought and research) which I was able to tie together this morning in a small, unnumbered prep thread. If you didn't see it, you will find it helpful context for today's work to come.
https://twitter.com/ThyConsigliori/status/1344637514217304066?s=20
5) Actually, I cannot TOO STRONGLY encourage you to glance through the prep thread. We are at war. Not metaphorically. It's no mere analogy. We are at war. War has been declared and is being waged. If nothing else, read this and heed.
presentdangerchina.org/2019/05/china-…
presentdangerchina.org/2019/05/china-…
6) Who among us could have, in our worst nightmares, have dream of the collapse of the World Trade Centers before that fateful morning? We face precisely such coming devastating attacks in this war, and we remain 100% oblivious. China is fighting to destroy us utterly.
7) Stick with me a step or two further. This is an existential war, no mere skirmish over territory or supply routes. This is a war over far more than today's world, or even the future. It is a war over the past as well. In previous eras, China had no word for nation.
8) There was just China, and everyone and everything else were just barbarians. China was the only nation, and as such, needed no word to term it so. Their Emperor was Lord of All Under Heaven. The USSR never had any such tradition to subsume into its Communist Mission.
9) That is our context as we turn again to J.E. Dyer @OptimisticCon's article. We have to pick up where we left off yesterday with...
Slide 15
Slide 15
10) Here's J.E.'s most important point on this slide, from P36.
"...the split-up would be to close the barn door BEFORE more horses get out."
Here, she's talking about the long history of NSA tools being leaked to the world from P35.
"...the split-up would be to close the barn door BEFORE more horses get out."
Here, she's talking about the long history of NSA tools being leaked to the world from P35.
11) But if you combing yesterday's work, especially #s 73 - 85, with today's prep thread and our intro here, what you find is a setting within which these vulnerabilities hold historic, existential significance. Spell that...
T
H
R
E
A
T
T
H
R
E
A
T
12) To complete our review/pickup from where we left off, the tactical question - with VAST strategic implications - is, should we separate US Cyber Command from the NSA where they are both currently combined? The answer is undoubtedly yes.
13) I must abandon you there with the requisite of reading yesterday's thread if you're still feeling a bit lost on these specifics. The rest of us must move on to...
Slide 16
Slide 16
14) I attempted (and deleted a comment) glancing over this slide and leaping forward a bit. It was an error, which I'm now correcting. Let me explain the compositional problem. It's one I often suffer, too.
15) There are many stories in life where the beginning and middle just don't make sense until we get to the end. This is often the basis of wonderful suspense stories, where in the final scene, all our previous assumptions are challenged. In fiction, it's wonderful.
16) In analysis, not so much. What makes it even worse is when this detail, that detail and the other are all connected (or worse, about to be disconnected) and just don't make sense until all the pieces are tied (with some being untied, etc.). There is ONLY one answer.
17) Well, there are two. If you're the writer, you rewrite. You resequence. You judge every detail against the analytical momentum and purpose, and you ensure your reader's comprehension at each individual step. You also often give up the end at the beginning.
18) But for us readers, there is ONLY one answer. And that is the combination of slow and repeated readings. It's a special form of patience to acknowledge confusion, letting go of its irritation and continue working toward the segment's conclusion. Then, repeat.
19) So please bear with me while I go take my own pill. It's back to this section of the article for Pasquale, and I'll be back in a bit with a clearer head. If you're as dedicated as me, please join me!
20) Oh my! Here's another mistake I'm so often guilty of. I'm often afraid to OVERSELL my case, that I end up committing the equally sinful error of UNDERSELL. It's kind of like saying, look, you do want to keep breathing, but if not, well, the choice is yours. WRONG!
21) And I think I now know how to crack this critically important point down. I say, start here, with the WikiLeaks tweet. Read it, and its screenshot statement in full. Then come back here.
https://twitter.com/wikileaks/status/839117937042735104?s=20
22) It is a thick plot, to be sure. Let's break it down.
1) The CIA not only DEVELOPS but also COLLECTS attack techniques.
2) It even has a Remote Devices Branch called, ironically enough, UMBRAGE. UMBRAGE is the fence's warehouse for stolen attack techniques.
1) The CIA not only DEVELOPS but also COLLECTS attack techniques.
2) It even has a Remote Devices Branch called, ironically enough, UMBRAGE. UMBRAGE is the fence's warehouse for stolen attack techniques.
23) Continuing...
3) Since attack techniques all leave distinct fingerprints, the CIA realized, rightly, that its own fingerprints would be everywhere they attacked. So...
4) Like plastic film that lifts someone else's fingerprint, and then puts in on the gun...
3) Since attack techniques all leave distinct fingerprints, the CIA realized, rightly, that its own fingerprints would be everywhere they attacked. So...
4) Like plastic film that lifts someone else's fingerprint, and then puts in on the gun...
24) Continuing...
5) UMBRAGE Branch can pick and choose attack modules to generate FALSE FLAG Operations.
In a word, the CIA has the capability to replicate another nations digital fingerprint, employ that technique, and the other nation gets the blame, not the CIA.
5) UMBRAGE Branch can pick and choose attack modules to generate FALSE FLAG Operations.
In a word, the CIA has the capability to replicate another nations digital fingerprint, employ that technique, and the other nation gets the blame, not the CIA.
25) What J.E. undersells here is this. THIS IS EXACTLY WHAT IS OCCURRING RIGHT NOW IN ELECTION 2020. By design, this is obviously close to impossible to prove. And all the more so when you follow her bouncing ball back to Comey!
26) The time frame was the Russia Hoax rolling out in February and March 2017. Forget all those familiar players and scenes though, they're just what was happening (I think). We pick up at P38. Comey's sabotaging a deal with WikiLeaks. But why?
Cue Slides 17 & 18.

Cue Slides 17 & 18.

27) Remembering that Comey is FBI, a subset of but completely separate from DOJ, it is DOJ that wants to cut this limited immunity deal with Assange. They want to stave of his release of CIA tools into the world. Comey wants them to NOT make the deal. She's right, that's weird.
28) We already covered the contents of Slide 17, above. We pick up on Slide 18 where the story comes together, powerfully! P40 is still stage setting. P41 is where the resolution to the confusing factors begins to emerge. Comey WANTS those tools released. Why?
29) The tools were released. We learn in P42 that Comey surely did NOT desire to have Assange on record when any Guccifer info came out about the Democratic files.
But finally...
Cue Slide 19
But finally...
Cue Slide 19
30) In P44 we see that Comey did as could have been predicted (by anyone who knew all the facts, of course) and blamed Russia for the use of "Fancy Bear" tools to do what? J.E. says, "to maraud through the Democrats' IT system."
We have to pause on that, for sure.
We have to pause on that, for sure.
31) {Note: this is Twitter's favorite break point in a long thread. Remember to click the "show replies" button.}
Who remembers The Rolling Stone magazine? And who remembers Seth Rich? You do, come on! Now check here:
rollingstone.com/politics/polit…
Who remembers The Rolling Stone magazine? And who remembers Seth Rich? You do, come on! Now check here:
rollingstone.com/politics/polit…
32) Now do you see what I'm saying about an analyst's risk of UNDERSELL? This is the sexiest, most exciting part of our trip down memory lane. Back then, death by suicide or botched robberies simply SHOUTED Hillary Rodham Clinton. Nothing more need be said.
33) I never followed the slightest Comey, DOJ, or CIA connections to the Seth Rich/Democrat Files story at all. Did you? You great Q souls will love this! This was precisely the time of Pizzagate, right? The Podesta Files were right there at WikiLeaks. But nothing to see here.
34) In P45 our story ends, not with a bang but a whimper of those boring words: plausible deniability. Ever since Watergate we've always been told that the cover up is worse than the crime. Well, that assumes very low-caliber crimes of course. But even still, this is COVER UP.
35) And there was a critical lesson learned, an evil one. If you can cover something like this up, maybe you can use those same "Fancy Bear" tools to flip elections of national significance on a scale never before imagined, such as the coming 2018 Midterms.
36) And if, as was shown in 2018, you can get away with that? Why mightn't you be able to wipe out an entire National Presidential Election, even if it's a landslide? What might we NOT be able to do with these "Fancy Bear" tools?
37) It's not that plausible deniability is inaccurate. It is absolute correct, completely. But it misses, well, by a country mile's worth of tone. It's more like the basis upon which we sell out the entire nation, and not just now, but for all history forward and backward.
39) Before I go take a needed coffee break, let's go ahead and cue up Slide 20, and take a quick peak, eh? Ah yes. This is another, read the entire section before trying to unpack the first parts...
Definitely coffee first...
Definitely coffee first...

40) While I was making my coffee (espresso again today), I couldn't help but think of the famed (if maybe not scientifically accurate) case of the frog that doesn't notice it's being boiled, due to gentle changes on the way there, not noticeable in their own right.
41) As you might have noticed, those 2018 Midterms and my failed analysis of them still stings, and the sting isn't growing less as time passes. It's not personal. The evil doers know that countless millions of us still had faith in the integrity of the vote system as I did.
42) May I NOT be wrong now. My inner vision turns to the difference between words that will not hurt me and the sticks and stones that will. My grandmother did not wear army boots, and I really don't have to respond. But if you shove me to the floor telling me don't get up?
43) What could any of us have done about Seth Rich's death? We were still more sleepy eyed than awake, really. Why didn't we march on DC over it? The prosaic answer is that one man's cloaked murder does not a nation awaken. It's sad but true.
44) It is my observation that what sleep we may have had left has been obliterated by all of 2020, culminating in this stolen election, the inner workings of which J.E. is guiding us over. Let me say this more. We need to know. We cannot let "computer stuff" seem beyond us.
45) What I see emerging is an essential map, a guide if you will, to The Swamp itself. In future, we'll track Progressivism more carefully than we can right now. But I must comment that their "progress" is NOT yours or my progress. Their progress is to total Government, period.
46) Truly this is the long fight of freedom to arise upon the Earth, root, take hold, and grow its ripened harvest of human fulfillment over our entire world. Totalitarianism is just the modern version of authoritarianism, King's Right to Fascism or Communism, no matter.
47) But make no mistake, this episode, here, now, this 2020 Election Steal matters. Perhaps it is that shove to the floor with the command to not get up that we have required before we could know the fight of our time, of our day.
48) In this section, Trump and Pompeo: Out of pattern, J.E. leads us into her thoughts on the flow from the standard Russia, Russia cry to the real enemy, as we discussed in our prep work this morning, China. Here's Slide 20, again. 
49) Noting how I've been so tempted to skip steps, I have to open up those two links she gives in P46 and P47, and see if we need anything from them here. I'll give you both links also. Come and check with me.
libertyunyielding.com/2020/12/15/old…
libertyunyielding.com/2020/12/15/old…
51) The APT 29 "Cozy Bear" attribution (from #49 above), is a perfect representation of precisely what J.E. explained to us that Comey was on about over releasing the CIA toolkit via WikiLeaks, in kibashing that deal. Yet, it does offer a critical reminder, also.
52) "This is the advanced persistent threat (APT 29) attributed to the Russian government by CrowdStrike, in the analysis the FBI never had the opportunity to verify because it didn’t get the original DNC server affected in 2015-16."
This is needed: crowdstrike.com/blog/who-is-co…
This is needed: crowdstrike.com/blog/who-is-co…
53) We have to learn the players, right? Here, however, is the most important fact from that link. We are reminded that the FBI did NOT take possession of the DNC's affected server. Here again, why do we not march of such matters?
54) A known Russian tool called Cozy Bear is blamed. But we don't know. We don't know because the FBI never got the evidence. Here we are, 5 entire years after the breach took place at the DNC, and the same blame game is still being played over our Election. Amazing.
55) The Mail Online story (from #50 above) is utterly chilling.
Headline:
Pompeo confirms Russia WAS behind cyber attack on US that one Congressman compared to PEARL HARBOR - as experts say infected networks must be 'burned to the ground' and Senator calls it 'act of war'
Headline:
Pompeo confirms Russia WAS behind cyber attack on US that one Congressman compared to PEARL HARBOR - as experts say infected networks must be 'burned to the ground' and Senator calls it 'act of war'
56) J.E. is about to tell us that is wasn't Russia. It was China. But the summary points are still cogent:
* Mike Pompeo on Friday became first official to attribute breach to Russia
* Colorado congressman compares SUNBURST attack to 'cyber Pearl Harbor'
* Mike Pompeo on Friday became first official to attribute breach to Russia
* Colorado congressman compares SUNBURST attack to 'cyber Pearl Harbor'
57)
* Microsoft president says the attack is a 'moment of reckoning' for America
* Suspected Russian hackers breached key government agencies and companies
* Officials warn that hackers had ample opportunity to set up secret backdoors
* Microsoft president says the attack is a 'moment of reckoning' for America
* Suspected Russian hackers breached key government agencies and companies
* Officials warn that hackers had ample opportunity to set up secret backdoors
58)
* Breach went undetected for nine months giving hackers free reign in systems
* Experts say infected networks may need to be 'burned to the ground' and rebuilt
*Hackers conducted a 'dry run' of the attack more than a year ago
* Breach went undetected for nine months giving hackers free reign in systems
* Experts say infected networks may need to be 'burned to the ground' and rebuilt
*Hackers conducted a 'dry run' of the attack more than a year ago
59) Last bullet point:
* Apparent espionage campaign has been called the largest breach in US history
Who knew, friends? That cyberwar is announced in such a soft voice, almost impossible to hear if you don't lean forward and study every little detail and link?
* Apparent espionage campaign has been called the largest breach in US history
Who knew, friends? That cyberwar is announced in such a soft voice, almost impossible to hear if you don't lean forward and study every little detail and link?
60) A single quote:
"Experts say there simply are not enough skilled threat-hunting teams to properly identify all the government and private-sector systems that may have been hacked, and warn infected networks may have to be 'burned to the ground' and rebuilt from scratch.
"Experts say there simply are not enough skilled threat-hunting teams to properly identify all the government and private-sector systems that may have been hacked, and warn infected networks may have to be 'burned to the ground' and rebuilt from scratch.
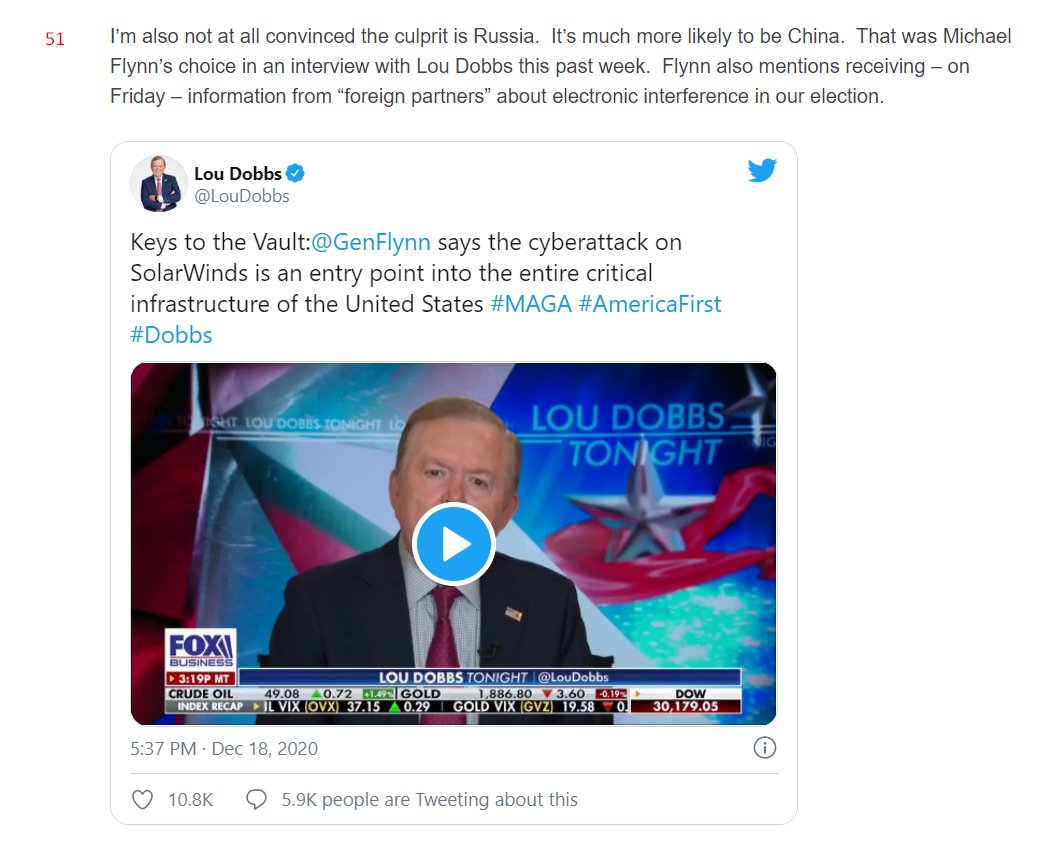
64) Keys to the Vault: @GenFlynn says the cyberattack on SolarWinds is an entry point into the entire critical infrastructure of the United States."
https://twitter.com/LouDobbs/status/1340063686237573123?s=20
65) Surely you MUST watch all 7 minutes of @GenFlynn's interview. I will again, right now.
Flynn's 1st point is that these attacks are from Foreign Influencers.
See yesterday's discussion of E.O. 13848. That it was done in concert with traitors here does not negate this.
Flynn's 1st point is that these attacks are from Foreign Influencers.
See yesterday's discussion of E.O. 13848. That it was done in concert with traitors here does not negate this.
66) You're inside our home, able to do anything. A very serious attack. This is all part of our Election security. Direct evidence of foreign influence, reiterated.
At about 2:20, foreign allies saw this, and will provide the data. That is HUGE!
At about 2:20, foreign allies saw this, and will provide the data. That is HUGE!
67) Lou tells us we have simply lost control of our own agencies in our government.
At about 3:40 Flynn tells us we're in an Information War, and the principle nemesis is China. They are masters. We're good, but bigger decisions are required.
At about 3:40 Flynn tells us we're in an Information War, and the principle nemesis is China. They are masters. We're good, but bigger decisions are required.
68) Lou emphasizes that the government cannot establish the extent of the damage, or the infiltration.
This is the act of an ENEMY threatening our national security.
Flynn names them: Adversaries that want to dominate our nation with their ideologies.
This is the act of an ENEMY threatening our national security.
Flynn names them: Adversaries that want to dominate our nation with their ideologies.
69) Slide 23
"Meanwhile, Trump’s assertion that “everything is well under control” should make people laugh, if for different reasons. Those whose cognitive facilities are deranged by him will find the statement mind-blowing."
"Meanwhile, Trump’s assertion that “everything is well under control” should make people laugh, if for different reasons. Those whose cognitive facilities are deranged by him will find the statement mind-blowing."
70) "Others, who may be on a spectrum of indifference to hero worship as regards Trump personally, recognize that Trump never tweets in vain....His track record of being right about these tweet assertions...is considerably better than the media’s."
71) We have a final slide with which to wrap up momentarily. We will also review the relationship between how this Key Supporting effort is both clarifying itself, and its relationship to the Main Effort. That, after all, has been the real driving point here.
72) I have to imagine your minds are all as exhausted as my own. I push on, though, for the following single motivation. My constant question, since the morning of November 4, 2020, has been simply and solely: what do we need to understand to #StopTheSteal? But it has morphed.
73) As you realize, I've come to see this #2020ElectionSteal as but a theater in the Great 2019 War With China. they declared this war. We still haven't declared war back.
It's 12:30 PM. We've been at this for hours. One more break, and then we'll finish up.
It's 12:30 PM. We've been at this for hours. One more break, and then we'll finish up.
74) Slide 24
In P57 J.E. states that this Key Supporting Effort is more than just clarifying itself, it's revealing just how large its scope truly is. Here again, I think she understates her case.
In P57 J.E. states that this Key Supporting Effort is more than just clarifying itself, it's revealing just how large its scope truly is. Here again, I think she understates her case.
75) Stating the case as fully as possible is our last task for today. Should we capitulate and allow Biden his stolen post as Commander In Chief, how can we do anything other than prepare for defeat in this war? The Cyberwar of 2020 won by China, what happens here, then?
76) In a word, we must foresee our own provincialization. We must anticipate the rise of the ACP, the American Communist Party, as the sole governing power in the newly minted People's' Republic of America. We have already observed the Propaganda Arm already in place.
77) We have already seen, dating back to Bush 41's administration, how our economy may be packaged up and crated off to China. Since Clinton 41 we've seen how our Intelligence may be transferred to China with full sanction of the Oval Office.
78) With Bush 43, we saw how China can be granted Most Favored Nation status upon entry - the 1st Communist nation so honored - into the WTO, granting it every right of every trade deal under WTO auspices. What was the tie to China in 2008/2009 financial collapse?
79) If in no other way, we know that China gained growing power over us by our becoming a debtor nation, owing more money to China than we'd ever owed to any nation before.
80) As there was an Axis of Evil under Reagan whom we fought, there were also Axes of alliances in both WWI and WWII, of course. Under Obama we can see the Axe of alliance between China, Cuba, and Venezuela attaining perfect symbiosis. It gets worse.
81) Under Obama, as we decimated our military might and preparedness, China exploded its own, extending its territory far into the Pacific Ocean with new island formation and instant militarization. And then there was its Belt and Road Initiative.
82) With vast hordes of cash stolen from America's middle class as it was hollowed out, China began the most aggressive foreign infrastructure project in human history. You'd have to reach back to Rome and its famed roads, all of which led to Rome, for a comparison.
83) In American history, it would be the Marshall Plan, but it pales in comparison. China already holds claim to the greatest colonial enterprise since the creation of the British Empire. Its Belt and Road Initiative has nothing less than the complete colonization of Africa.
84) This occurred with Obama's full blessing. How can I say that? He simply did nothing to oppose it. And what does J.E. teach us about the present moment? That rogue/traitor factions replete throughout our government are in bed with China to steal Election 2020.
85) If you ask any military sci-fi author what will be the main route into the US were China to physically invade? The answer is our Southern Border. So, should we capitulate and surrender the Oval Office to its thief, we can expect to see our Border Wall torn down immediately.
86) My fear is worse than that. My fear is that no physical invasion will ever be necessary at all. Why confiscate Fort Knox's gold if you have an American Government ready to pack it up and ship it to you for the asking?
87) Look back again. Who runs South America? There can be no question that the Drug Cartels have more power than any of the formal Governments. From the presence of the Calabrian Ndrangheta, to of course the Columbian Cartel, whichever flavor the day, they are lord and master.
88) Not enjoying our middle class's stolen wealth happily enough, China joined forces with these Global Drug Empires to pour fentanyl and oxycodone into every town and hamlet in America. It was direct reach to the true heartland of America they sought and gained.
89) Can you doubt that MS13 and China build strategy and plans together? Reach forward from there into every state penitentiary in America, and every gang and drug logistics crime outfit. Not enough yet? Hell no. Look to our universities and their Confucius Institutes.
90) Enough yet? Not a chance. Who owns the greatest power over Hollywood? And then, we have Big Tech. Google and Apple are but Chinese lap dogs. Shih Tzus, I picture them. Well trained. Obedient. They bow and step backwards as they depart the Emperor's Throne Room. They kowtow.
91) Finally, even I grow tired. I can only feel for you reading all this horror and terror. Yet even I cannot express the dire nature of the threat we face But as J.E. tells us, it all comes down to the mechanisms of this election's theft and Trump's strategy to cure it.
92) And with that, I turn to a positive vision. I purposefully left the alliance between America's Pharmaceutical Industry and China out of our list of horrors above. Here's why. If we hold fast, as J.E. tells us to do, Trump is well on the path toward fixing that ill already.
93) We should elevate the two words Supply Chain to sacred status. As Trump led us to Energy Independence, he will lead us to Supply Chain independence. We will provide security to our Supply Chain so it may NEVER be threatened by any foreign power, ever again.
94) What better place to begin than with antibiotics? If we protect Trump's coming four years, already won by a landslide, we will manufacture every bit of our own medical supply chain. How do you think that looks under a Biden administration? We'll manufacture even less.
95) By this point long ago, the great @marklevinshow would have waved his hand, saying, 'That's it."
The Cyberwar rages. You know it. It is on us to win it. And the only way to do that is safeguarding Trump's coming four years.
The Cyberwar rages. You know it. It is on us to win it. And the only way to do that is safeguarding Trump's coming four years.
Both this thread, today AND our extended J.E. Dyer opus end now at #95.
We may do a Table Of Contents style post on it tomorrow, but we have actually completed our analytical mission here. Our work is done.
For now.
We may do a Table Of Contents style post on it tomorrow, but we have actually completed our analytical mission here. Our work is done.
For now.
• • •
Missing some Tweet in this thread? You can try to
force a refresh