How do @Mandiant UNC clusters get formed, merged, and graduate to APT groups or even personas? Look at serial crimes and sprees in meatspace. Multiple crimes on multiple victim systems, multiple places. It takes forensic evidence to tie the cases together. It's the same process.
Foot impression from the crime scene. Is it unique? What shoe is it, where was it sold? How many made in that size? You have to know if the evidence is unique. All the casings, latents, entry toolmarks. Technical evidence is how we group crimes together and move towards an actor.
TTPs and MOs and methodologies and victimologies are important too, but these don't help you get attribution alone. Technical links, grounded in substantiated evidence is the only way.
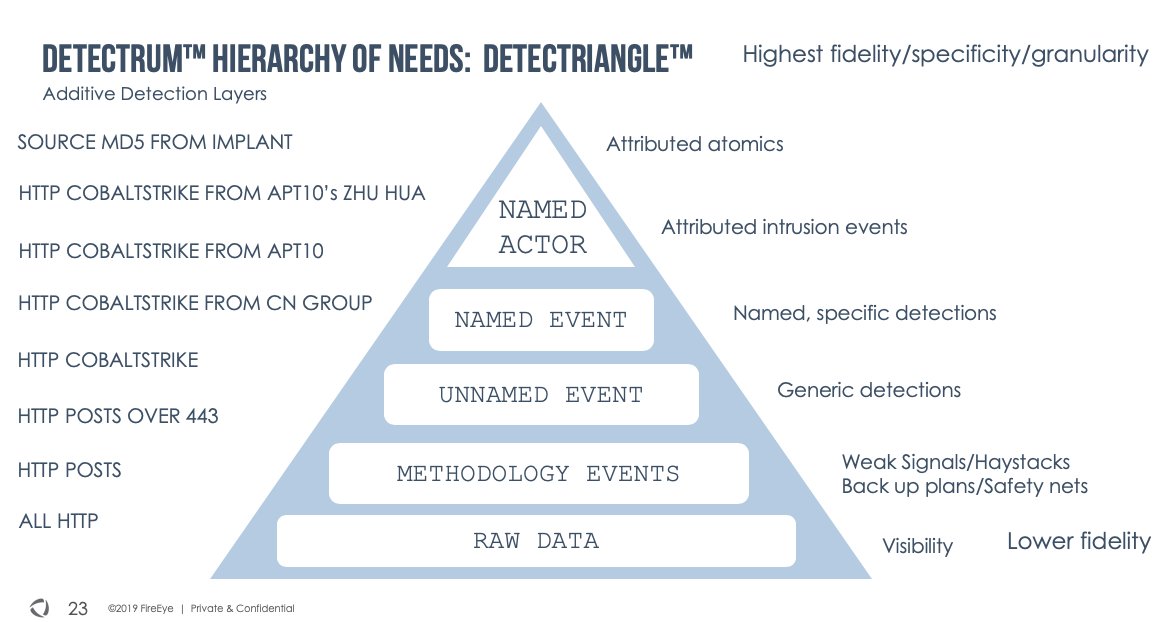
"But, but, attribution is a spectrum! And it has different purposes and different consumers and different levels of fidelity, specificity, granularity and all that!"
Yep. Burden of proof, confidence varies. This is why we have a model/process for UNC > APT > Personas > People
Yep. Burden of proof, confidence varies. This is why we have a model/process for UNC > APT > Personas > People
"But, but, look at the thing, I KNOW it's APT10."
That's great! Maybe it is. Make your case. Show an evidence-based technical linkage to that claim and we can help grow the cluster with an attribution on new data. We curate thousands of clusters/groups over many years.
That's great! Maybe it is. Make your case. Show an evidence-based technical linkage to that claim and we can help grow the cluster with an attribution on new data. We curate thousands of clusters/groups over many years.
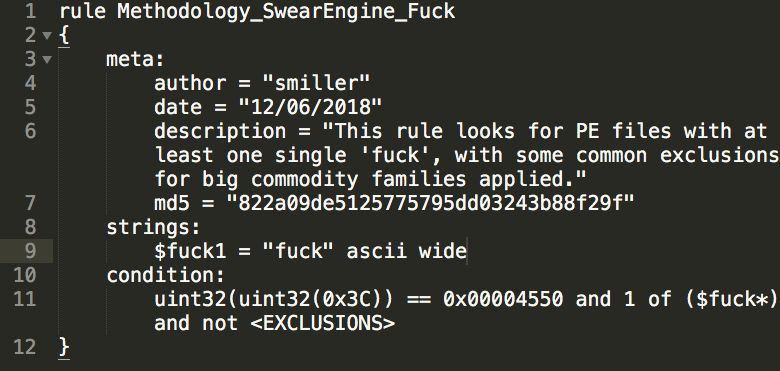
There are also situations where technical evidence linkages aren't sufficient for an attribution. Lots of them, such as with IP addresses and FQDNs. Malware families. Even individual samples. These alone do not define an actor.
I see a new wave of METALJACK C2 activity and I know deep in my heart it is probably APT32, but I can't get to the attrib. It is even to an IP that APT32 has used before. But the link is not strong. This becomes a *new* UNC group that is a low confidence, _suspected_ APT32.
Not getting an attrib is not a bad thing. While it may seem like an art, attribution is (or can be) a scientific discipline where a null result is acceptable. If the evidence isn't there, we cluster and move on.
If one day that UNC grows and starts to overlap in meaningful ways, maybe we can merge it in to APT32. Until then we can summarize it and operate on the technical cluster as its own thing. We exploit the data, we gain knowledge, we pivot and hunt and respond with the UNC.
I don't know that there is a great analogy for an UNC in the physical world. Is it more like a "profile" of a serial killer? Maybe we don't know the actual person just yet, but we have a cluster of technical data and TTPs adding up. Maybe we will find out who dun it someday.
This is what happens when I drink coffee after 1pm.
Are detection and attribution on *the same spectrum?* <mind blowing noise>
https://twitter.com/stvemillertime/status/1231328008788750337
Whether UNC1878 or UNC2452 you should know that these groups are built on a giant pile of technical data and the higher you pile the technical links, the closer you get to actual humans behind an attack. You can go from total unknown > geo alignment > group > people over time.
One thing that is often overlooked, is that intrusion sets (esp for hifi attribs) must have qualified crime scenes. Not just connected data points floating in space, but the data must be grounded in compromised assets, or seen at positively identified victims of intrusion crimes.
Because many in the industry buy, sell and share threat data, we take for granted that we get it without much (if any) context of the true victims. To protect the victims, most data is disassociated from crime scenes. This makes it harder for you to use for attribution.
Imo, this is why companies and gov orgs that do incident response (or maybe AV + EDR) hold the keys to the attribution kingdom. They can observe victimology and connect organic *and* third party threat data to actual crime scenes, to host level, across thousands of global orgs.
• • •
Missing some Tweet in this thread? You can try to
force a refresh