NEW: Fake pirated software sites serve up malware droppers as a service 🏴☠️
During our recent investigation into an ongoing Raccoon Stealer campaign, we found the malware was being distributed by a network of websites acting as a “dropper as a service,”... 1/00
During our recent investigation into an ongoing Raccoon Stealer campaign, we found the malware was being distributed by a network of websites acting as a “dropper as a service,”... 1/00
... serving up a variety of other malware packages—often bundling multiple unrelated malware together in a single dropper. These malware included an assortment of clickfraud bots, other information stealers, and even ransomware. 2/00 

While the Raccoon Stealer campaign we tracked on these sites took place between January and April, 2021, we continue to see malware and other malicious content distributed through the same network of sites. 3/00 

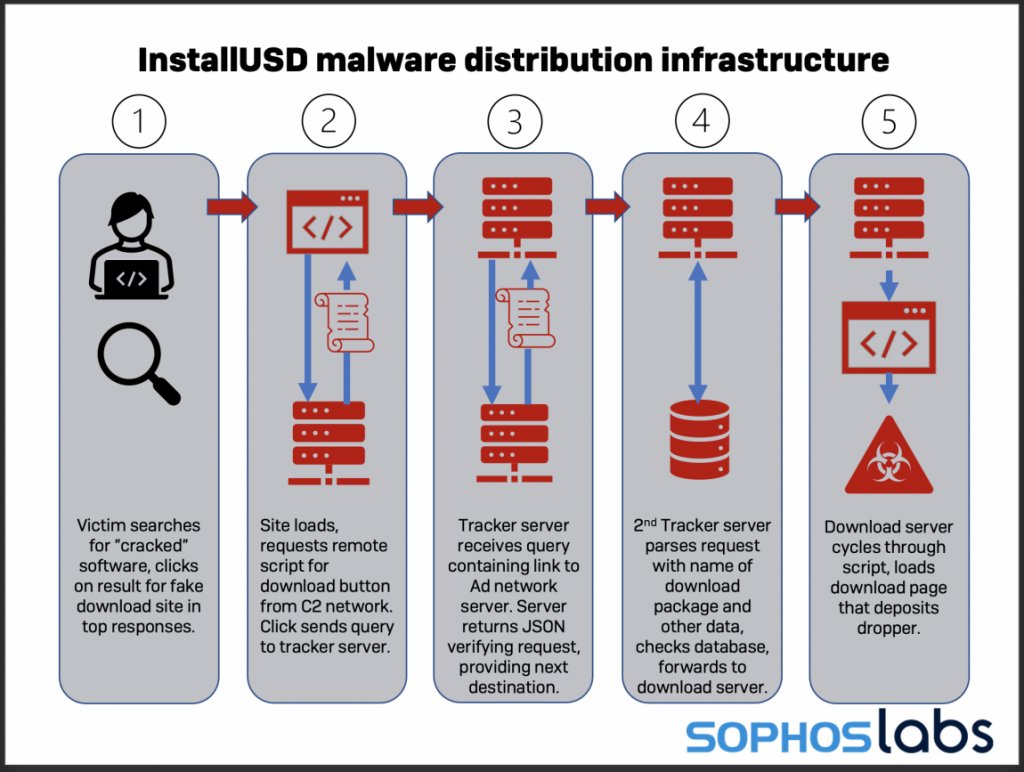
Multiple front-end websites targeting individuals seeking “cracked” versions of popular consumer and enterprise software packages link into a network of domains used to redirect the victim to the payload designed for their platform. 4/00 

We discovered multiple networks using the same basic tactics in our research. All of these networks use search engine optimization to put a “bait” webpage on the first page of results for search engine queries seeking “crack” versions of a variety of software products. 5/00
As we researched the Raccoon Stealer campaign, we discovered multiple other cases where some of these sites had been tied to other malware campaigns. 6/00
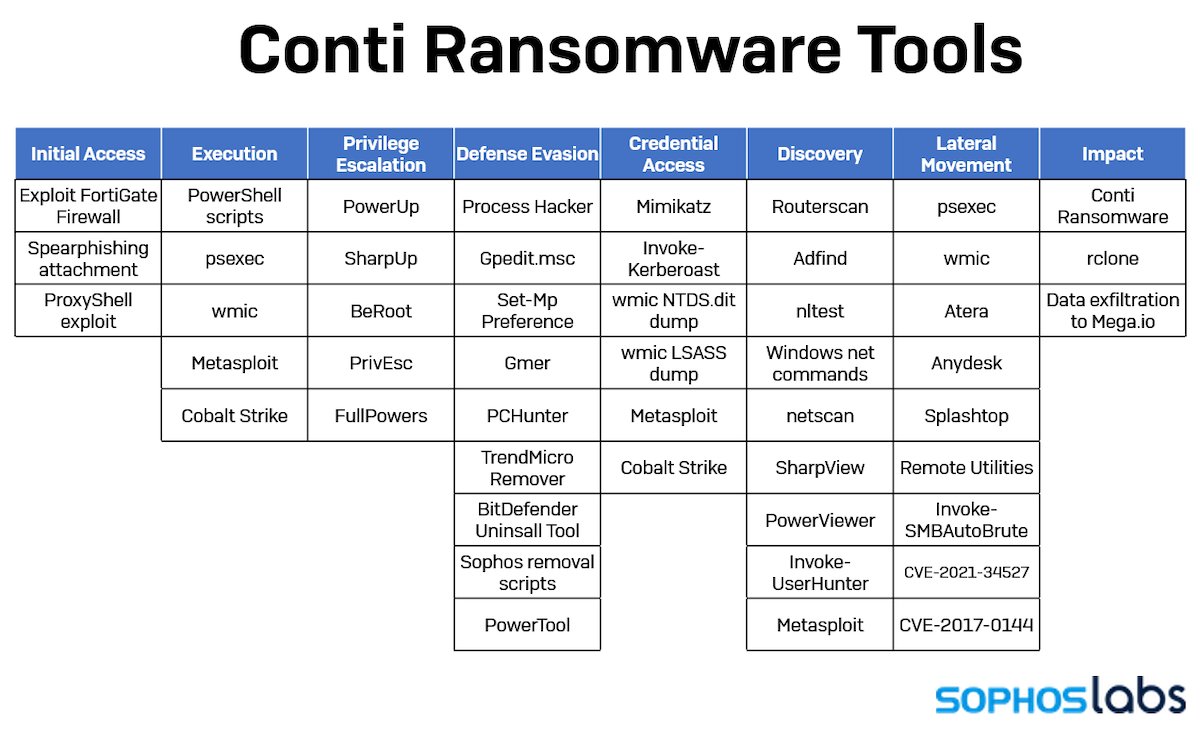
We found a variety of information stealers, clickfraud bots, and other malware delivered through the sites, including Conti and STOP ransomware.
So we began to investigate the networks behind the sites themselves... 7/00
So we began to investigate the networks behind the sites themselves... 7/00
Most of the bait pages we found are hosted on WordPress blog platforms.
Some clicks on bait pages are directed to a download site that hosts a packaged archive containing malware. Others steer to browser plugins or applications that fall in a potentially unwanted grey area. 8/00
Some clicks on bait pages are directed to a download site that hosts a packaged archive containing malware. Others steer to browser plugins or applications that fall in a potentially unwanted grey area. 8/00

Visitors who arrive on these sites are prompted to allow notifications; If they allow this to happen, the websites repeatedly issue false malware alerts. 9/00
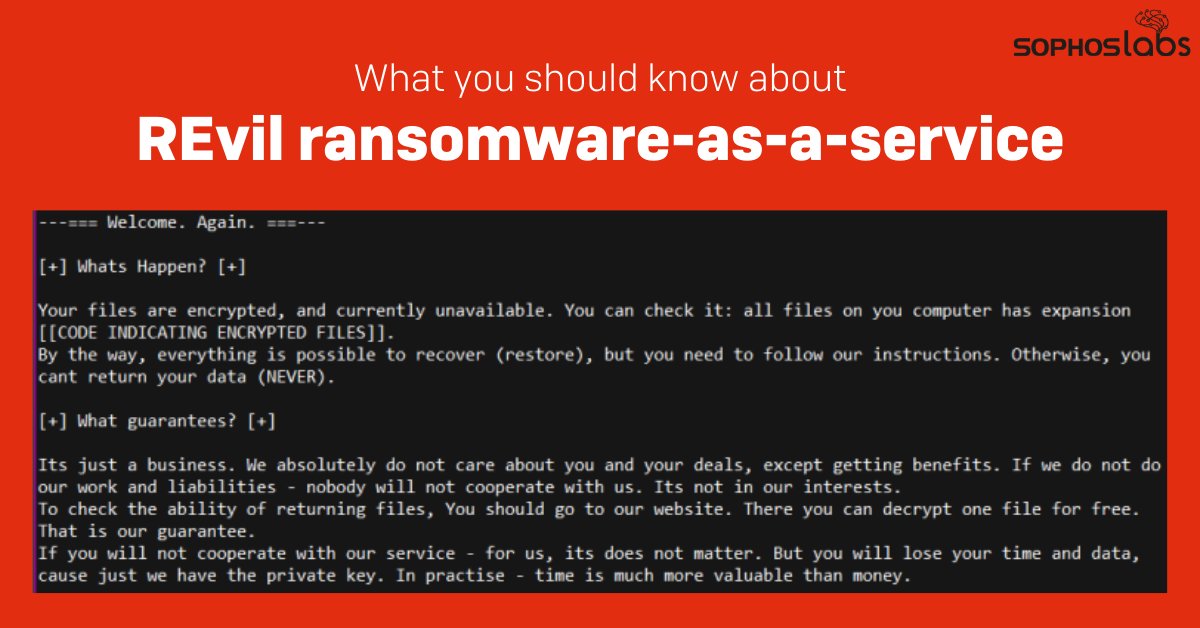
The downloads contained a variety of potentially unwanted applications and malware. We downloaded installers for Stop ransomware, the Glupteba backdoor, and a variety of malicious cryptocurrency miners (in addition to Raccoon Stealer). 10/00
In a bit of irony, many of these malware were delivered by downloads purporting to be installers for antivirus products, including 15 we examined that claimed to be licensing-bypassed versions of the Sophos-owned HitmanPro. 11/00
Almost all of these malware droppers are easily detectable, and all of them were detected either by signature or behavior by Sophos products. But because these packages are in encrypted archives, they do not get detected until they are unpacked. 12/00
Indicators of compromise relating to this research have been posted to the SophosLabs Github.
SophosLabs would like to thank Anand Ajjan and Andrew Brandt for their contributions to this report.
Read the full story from @thepacketrat and @yusufarslanp: news.sophos.com/en-us/2021/09/…
SophosLabs would like to thank Anand Ajjan and Andrew Brandt for their contributions to this report.
Read the full story from @thepacketrat and @yusufarslanp: news.sophos.com/en-us/2021/09/…
• • •
Missing some Tweet in this thread? You can try to
force a refresh