#ESETresearch confirms in-the-wild use of the PRIVATELOG/STASHLOG malware reported by @Int2e_ and @MalwareMechanic from @FireEye earlier this week. Findings 👇 @0xfmz 1/11 fireeye.com/blog/threat-re…
We saw this malware family used in a targeted attack against a high profile company in 🇯🇵 Japan in May 2021. We recovered 2 samples that match FireEye's description of PRIVATELOG and STASHLOG, along with a previously unknown sample we call SPARKLOG 2/11
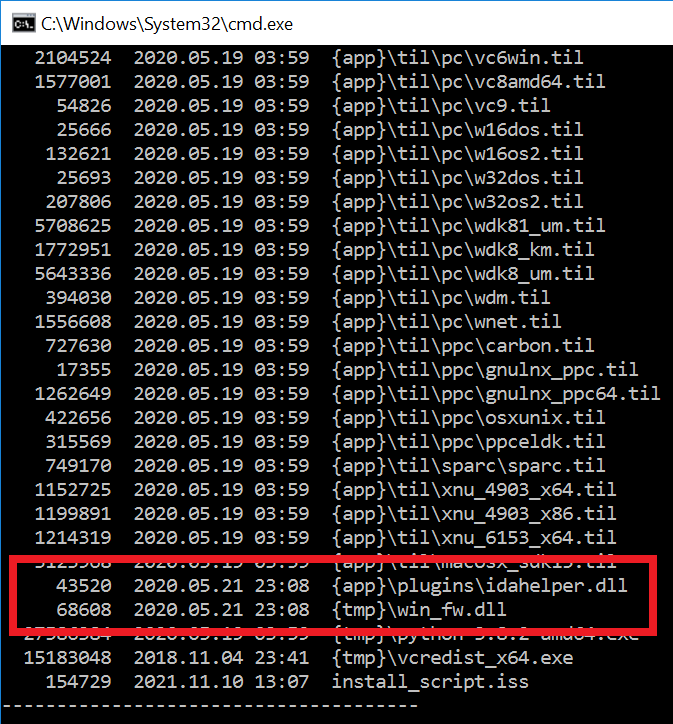
With STASHLOG being the installer and PRIVATELOG a loader, SPARKLOG is the launcher component for PRIVATELOG. Its main purpose is to retrieve PRIVATELOG from the log file, decrypt it, and get it loaded into legitimate service which varies from one OS version to another. 3/11
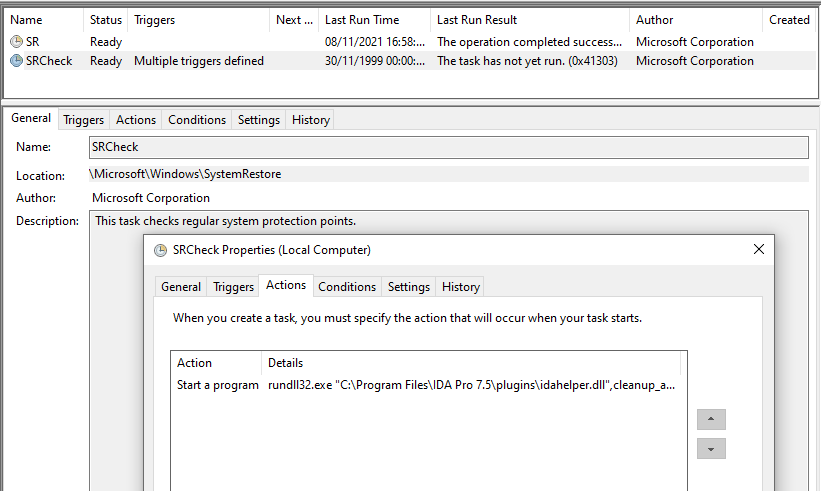
From Windows Server 2012 to Windows 10, SPARKLOG drops PRIVATELOG as %SYSTEM32%\spool\drivers\x64\3\prntvpt.dll (mimicking a legitimate Windows DLL) then stops and starts an existing PrintNotify service to load the DLL. PrintNotify is a legitimate Windows service. 4/11 
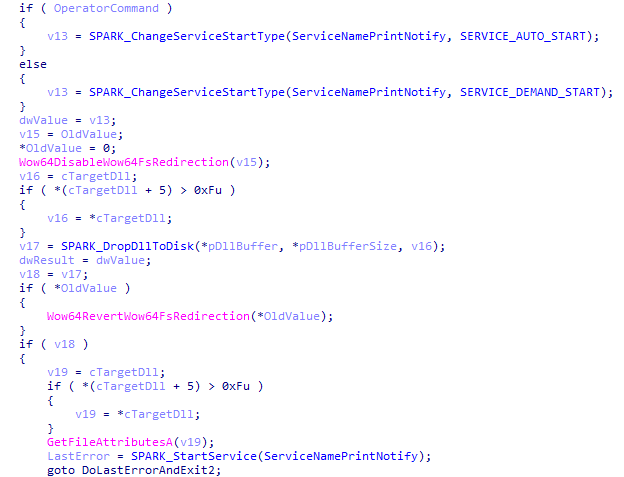
From Windows Vista to Windows 7, SPARKLOG uses a well-known DLL hijacking technique that involves dropping PRIVATELOG as %SYSTEM32%\WindowsPowershell\v1.0\wlbsctrl.dll, then stops and starts the legitimate Windows’ IKEEXT service to load it. 5/11 
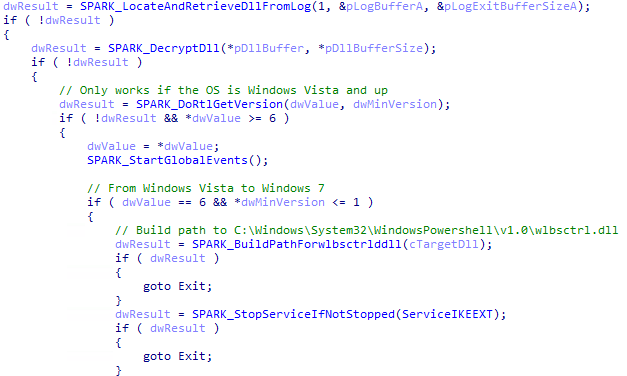
Depending on the command line, unlike with printpvt.dll, the file is wiped if the service is started successfully. 6/11
We believe that there should exist a version of PRIVATELOG that, as in the case of prntvpt.dll, mimics or attempts to look as wlbsctrl.dll, another legitimate Windows DLL. 7/11
Interestingly, SPARKLOG executable contains an icon (doesn’t seem to belong to a specific software), and it creates a non-visible window to which it posts a message that triggers the execution of a thread to launch PRIVATELOG. 8/11 



We are sharing the following IoCs in hope that the community can use them to continue to research and find the missing components of the malware: 9/11
SPARKLOG F8D46895E738254238473D650D99BDC92C34EE44
PRIVATELOG 9267FE0BB6D367FC9186E89EA65B13BAA7418D87
STASHLOG BB93AE0FEE817FE56C31BDC997F3F7D57A48C187
10/11
PRIVATELOG 9267FE0BB6D367FC9186E89EA65B13BAA7418D87
STASHLOG BB93AE0FEE817FE56C31BDC997F3F7D57A48C187
10/11
Seen:
C:\Windows\apppatch\Custom\Custom64\Spark.exe
C:\Windows\AppPatch\Custom\Custom64\Shiver.exe
C:\Windows\system32\spool\drivers\x64\3\prntvpt.dll
Probable:
C:\Windows\system32\spool\drivers\w32x86\3\prntvpt.dll
C:\Windows\system32\WindowsPowershell\v1.0\wlbsctrl.dll
11/11
C:\Windows\apppatch\Custom\Custom64\Spark.exe
C:\Windows\AppPatch\Custom\Custom64\Shiver.exe
C:\Windows\system32\spool\drivers\x64\3\prntvpt.dll
Probable:
C:\Windows\system32\spool\drivers\w32x86\3\prntvpt.dll
C:\Windows\system32\WindowsPowershell\v1.0\wlbsctrl.dll
11/11
• • •
Missing some Tweet in this thread? You can try to
force a refresh