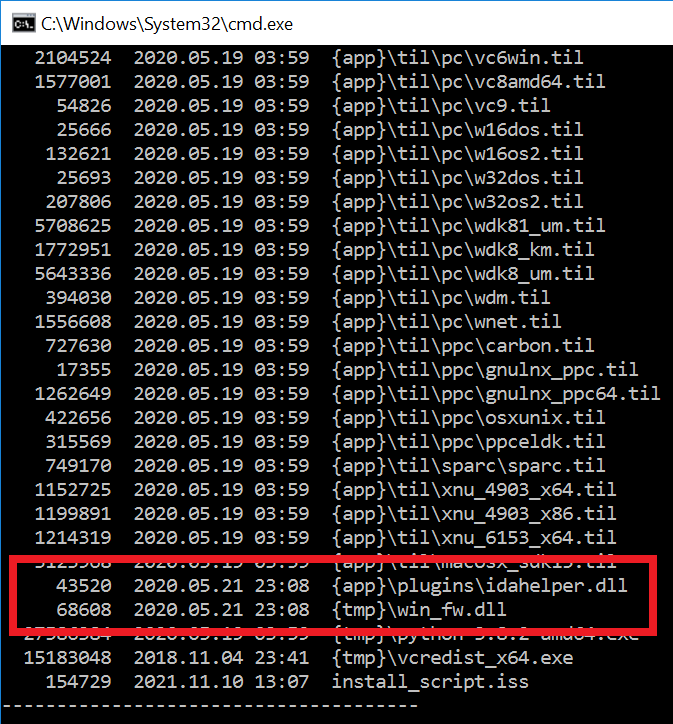
#ESETresearch identified malicious MS Excel documents automatically downloaded upon visiting the websites of cryptocurrencies #HotDoge, www.hotdogetoken[.]com, and #DonutCatBSC, www.donutcatbsc[.]com. Opening the document led to stealing the victim’s private information. 1/6 



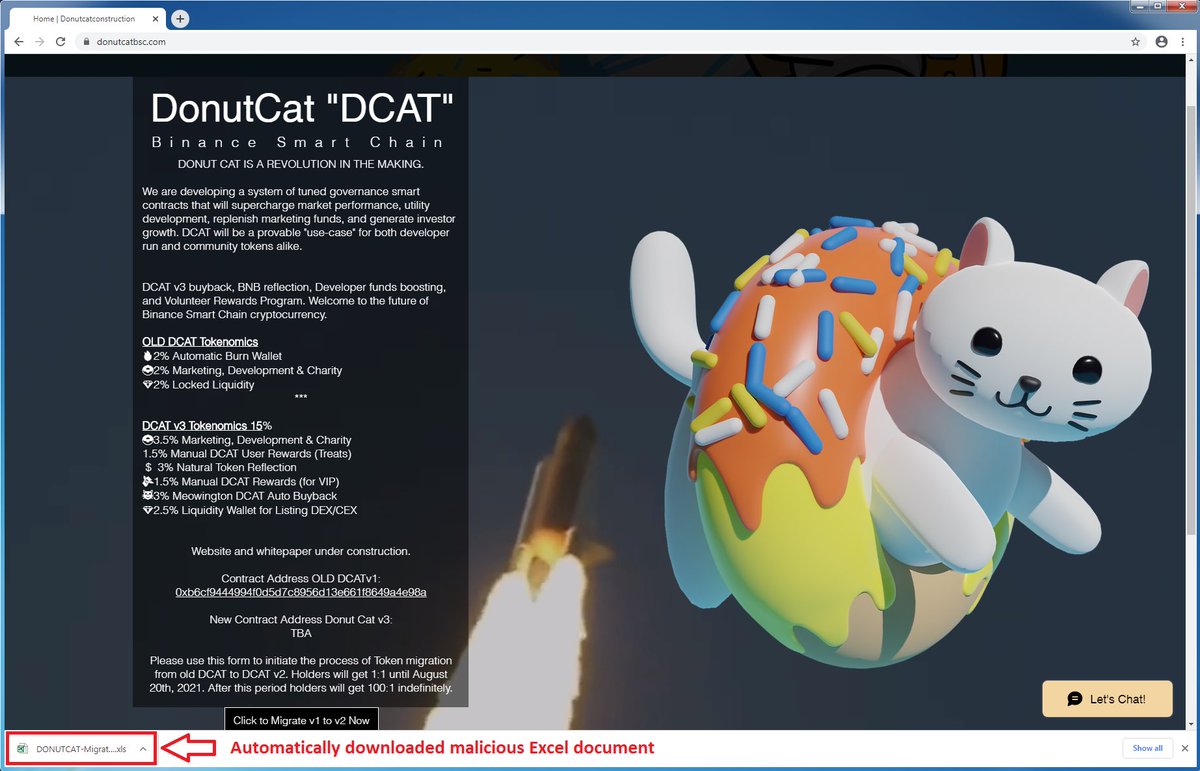



We contacted @HotDogeTokenBSC and provided them with the information to remediate the threat. They resolved the issue and the websites no longer serve the malicious documents. 2/6
We attribute this campaign to the 🇰🇵North Korea-linked APT group #Kimsuky. The Excel document contains a malicious Excel V4.0 macro that uses the #Squiblydoo technique to download and execute an XML file with a VBS scriptlet. 3/6
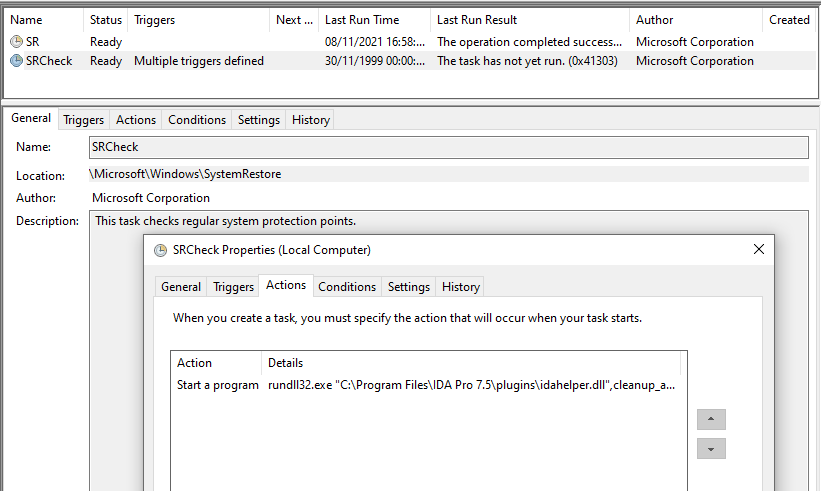
The VBS scriptlet ensures persistence on the compromised machine by creating a registry entry HKCU\Software\Microsoft\Command Processor\AutoRun that, upon execution, again takes advantage of #Squiblydoo technique to download & execute another XML file with a VBS scriptlet. 4/6
We have observed two versions of the next VBS scriptlet. The first one just sends information about the Windows version on the compromised machine to the C&C server. The second one downloads and executes #QuasarRAT. 5/6
The attackers used #QuasarRAT for stealing browser credentials and cookies, making screenshots, and listing particular folders. IoCs related to the case are available on our Github: github.com/eset/malware-i… #ESETresearch 6/6
• • •
Missing some Tweet in this thread? You can try to
force a refresh