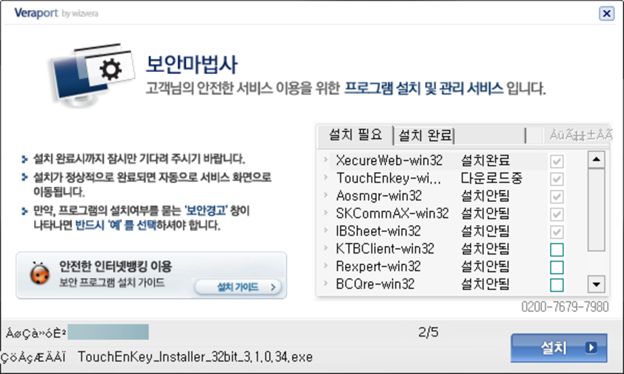
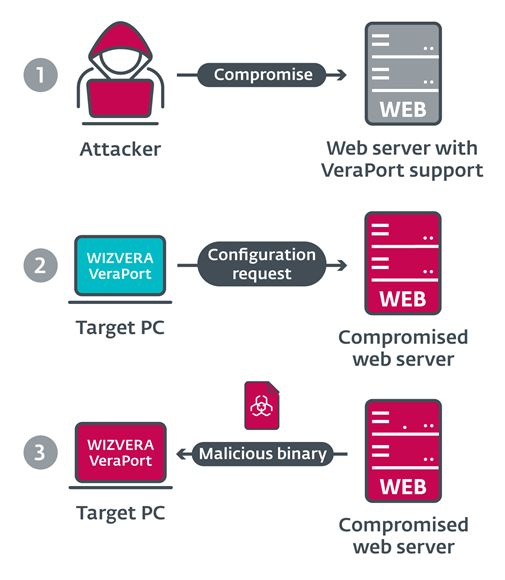
#ESETresearch discovered a trojanized IDA Pro installer, distributed by the #Lazarus APT group. Attackers bundled the original IDA Pro 7.5 software developed by @HexRaysSA with two malicious components. @cherepanov74 1/5 


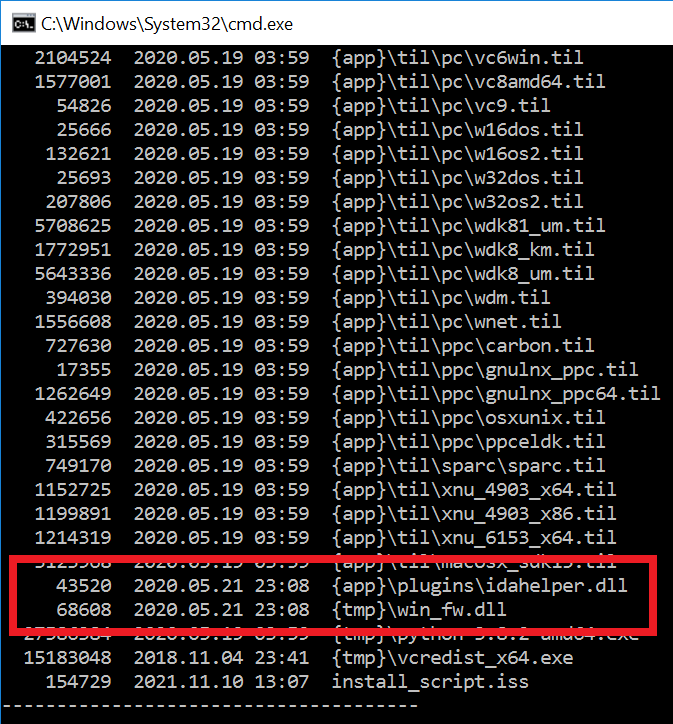
Attackers replaced win_fw.dll, an internal component that is executed during IDA Pro installation, with a malicious DLL. The malicious win_fw.dll creates a Windows scheduled task that starts a second malicious component, idahelper.dll, from the IDA plugins folder. 2/5 
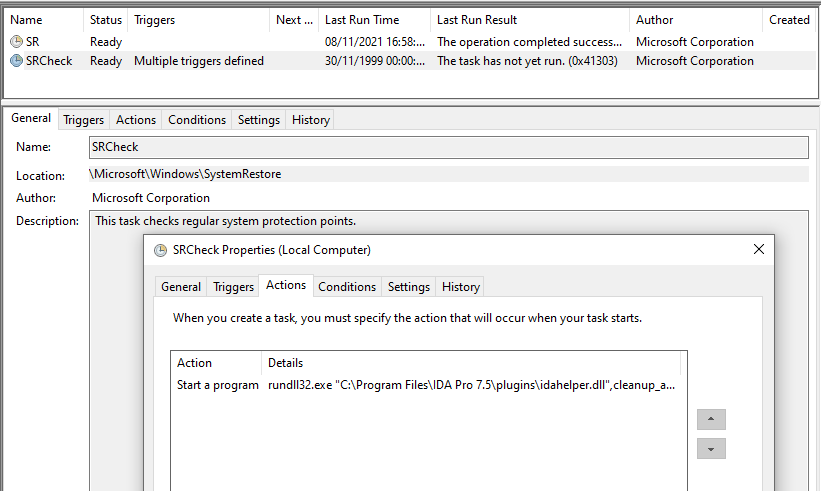
Once started, the idahelper.dll attempts to download and execute a next-stage payload from https://www[.]devguardmap[.]org/board/board_read.asp?boardid=01 3/5 

Based on the domain and trojanized application, we attribute this malware to known Lazarus activity, previously reported by Google’s Threat Analysis Group and Microsoft:
blog.google/threat-analysi…
microsoft.com/security/blog/…
4/5
blog.google/threat-analysi…
microsoft.com/security/blog/…
4/5
IoCs
📄:
win_fw.dll A8EF73CC67C794D5AA860538D66898868EE0BEC0
idahelper.dll DE0E23DB04A7A780A640C656293336F80040F387
🚨:
Win32/NukeSped.KZ
Win64/NukeSped.JS
🌐:
devguardmap[.]org
#ESETresearch 5/5
📄:
win_fw.dll A8EF73CC67C794D5AA860538D66898868EE0BEC0
idahelper.dll DE0E23DB04A7A780A640C656293336F80040F387
🚨:
Win32/NukeSped.KZ
Win64/NukeSped.JS
🌐:
devguardmap[.]org
#ESETresearch 5/5
• • •
Missing some Tweet in this thread? You can try to
force a refresh