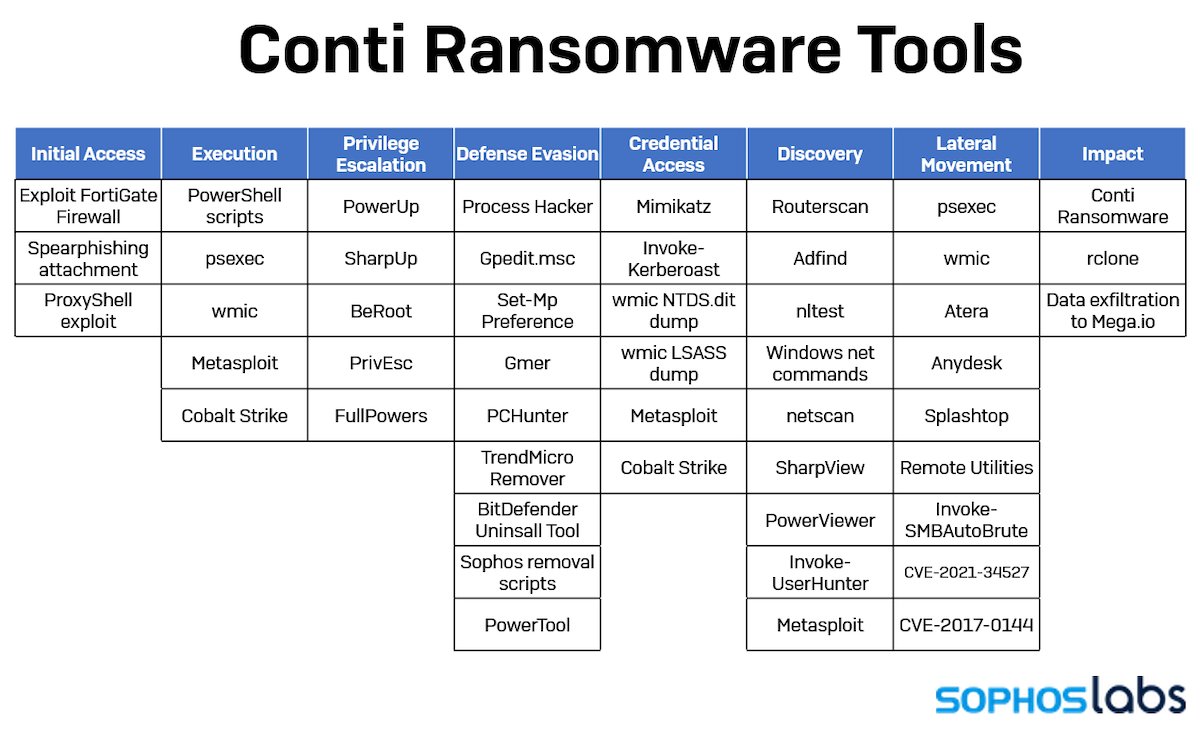
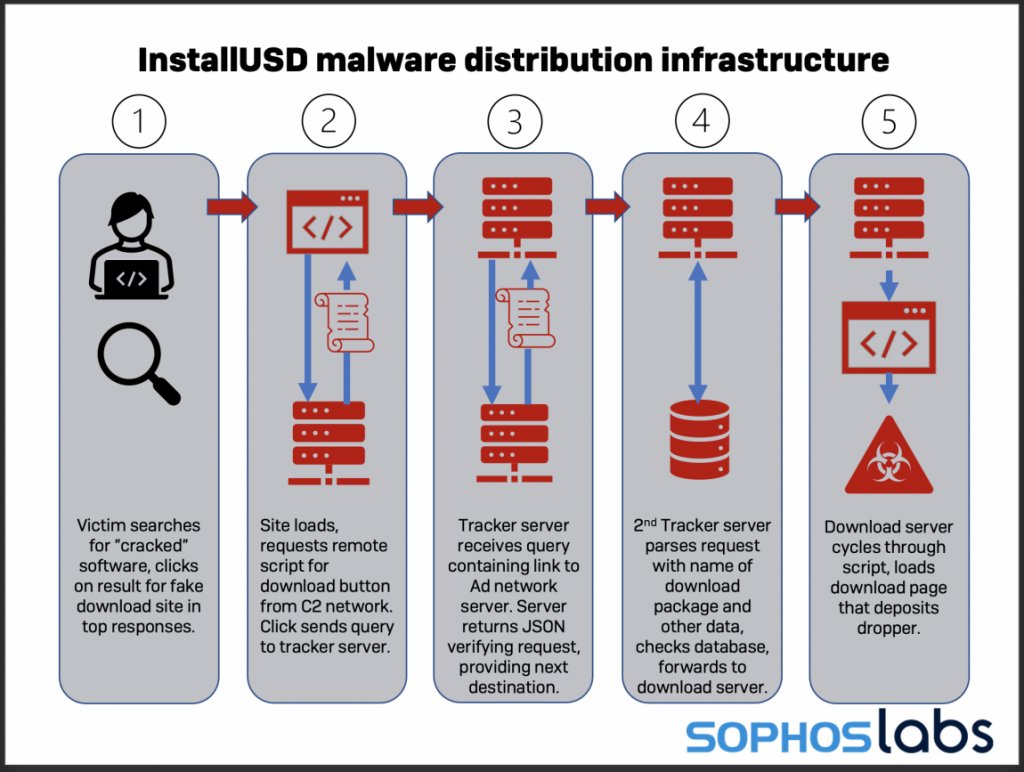
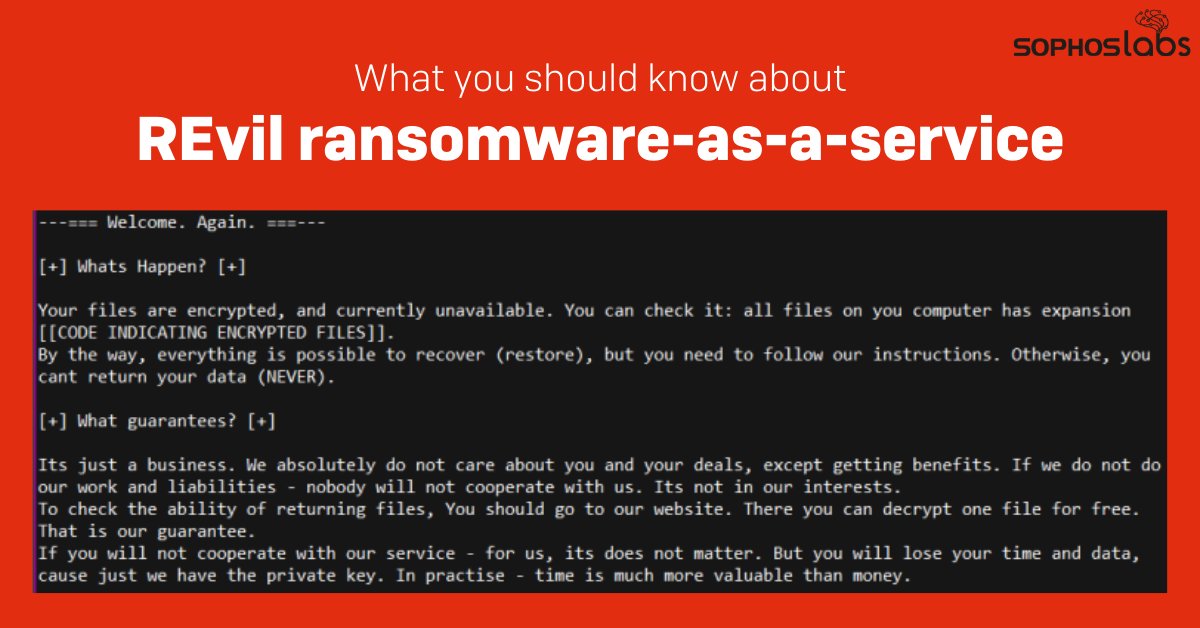
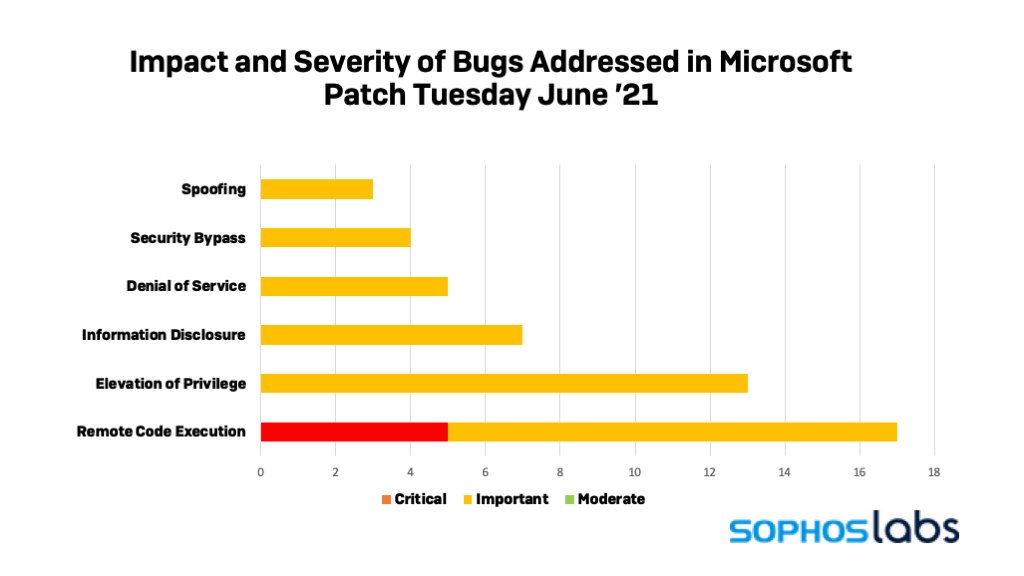
Hey everyone. @threatresearch here with a little news about how my day's been going.
Seems a lot of people are dealing with an outbreak of #BazarBackdoor that starts with an email that sounds like it's coming from someone who is annoyed you didn't report a complaint about you.
Seems a lot of people are dealing with an outbreak of #BazarBackdoor that starts with an email that sounds like it's coming from someone who is annoyed you didn't report a complaint about you.

We received a LOT of samples of the same-looking email from people who, correctly, recognized this as a phishy-looking spam. The "complaint" was purportedly linked in the email to a PDF.
Narrator: It wasn't a PDF
Narrator: It wasn't a PDF

Rather, the link leads to one of several pages hosted in Microsoft's cloud hosting space. The pages all looked like this one, with a link to download the "Preview PDF" but if you look closer at the link, you'll see it's an "ms-appinstaller:" link. That's new! 

Here's what I hadn't seen before: If you click the link, instead of downloading a more conventional .exe payload, the site delivers a Windows 10 AppXBundle file. This is the native format from the Windows App Store. Apparently, you can also get them by invoking the installer. 

In a test system, I (of course) clicked the Install button.
Please don't do this, yourself.
The browser downloads and immediately invokes AppInstaller on the Windows 10 system, which presents you with a very official-looking installer screen. It even has an Adobe logo-it's fake
Please don't do this, yourself.
The browser downloads and immediately invokes AppInstaller on the Windows 10 system, which presents you with a very official-looking installer screen. It even has an Adobe logo-it's fake

If, for any reason, you happen to click "Install," the AppInstaller component will run and, well, it's game over.
Really, please, don't do this, not unless you're intentionally getting an app directly from the Windows Store.
Really, please, don't do this, not unless you're intentionally getting an app directly from the Windows Store.

Here's what's happening behind the scenes:
First, the AppInstaller.exe component runs the contents of the .appxbundle file, which (to be fair) looks pretty innocuous at this stage.
First, the AppInstaller.exe component runs the contents of the .appxbundle file, which (to be fair) looks pretty innocuous at this stage.

AppInstaller then takes its cues from the contents of the .appxbundle file, which in this case instructs the system to drop a DLL into the %temp% directory and then register it using Regsvr32.exe. This really starts the ball rolling.
(Username's blocked to protect the victim)
(Username's blocked to protect the victim)

Here's where it starts to get weird.
That initial invocation of regsvr32 triggers the Windows command shell to run the same command, again, but this time it uses timeout.exe to pass the command to regsvr32, and it adds two alphabet-salad function names to the end of the commands
That initial invocation of regsvr32 triggers the Windows command shell to run the same command, again, but this time it uses timeout.exe to pass the command to regsvr32, and it adds two alphabet-salad function names to the end of the commands

And then it gets weirder.
The second iteration invokes regsvr32 a THIRD time, this time by passing the command through choice.exe. It also appends "& exit" to the end of the command line.
Oh, it's just getting warmed up.
The second iteration invokes regsvr32 a THIRD time, this time by passing the command through choice.exe. It also appends "& exit" to the end of the command line.
Oh, it's just getting warmed up.

So you can see there's a whole chain of child processes, spawned by the previous child process, which runs for a bit then terminates itself.
By the end of all of this, it has injected itself into the memory space of the Edge browser (msedge.exe)
By the end of all of this, it has injected itself into the memory space of the Edge browser (msedge.exe)

Once it's running hooked inside of an instance of Edge, it begins profiling the system by running a bunch of PowerShell commands. Remember, all this is happening behind the scenes.
Unless you were looking at your task manager you wouldn't notice it, probably even then.
Unless you were looking at your task manager you wouldn't notice it, probably even then.

The loader also invoked this pretty long PowerShell command to check one or more of the listed web addresses (at random) and use them to determine your public-facing IP address. This is too long for Process Explorer to show, so I pasted the command here so you can see it all. 



Here, it invoked PowerShell three more times to query the disk sizes of the hard drives, the motherboard manufacturer, and the physical RAM installed on the system. All were spawned as child processes of Edge, so I'm thinking it's pretty firmly wedged in there. 

The malware's c2 addresses all used the URI path /segment/billion in the sample I ran. Other folks in the industry shared that samples also used the URI paths of /recite/drink or /mission/revolt or /discreet/marble or /note/actual 

Some of the #BazarBackdoor c2 domains seen today:
kortynab[.]com
holygomar[.]com
hastrama[.]com
dfgerta[.]com
karatyvac[.]com
holygomar[.]com
There are probably more. These have been added to the SophosXL reputation service so they're blocked by endpoint and firewall.
kortynab[.]com
holygomar[.]com
hastrama[.]com
dfgerta[.]com
karatyvac[.]com
holygomar[.]com
There are probably more. These have been added to the SophosXL reputation service so they're blocked by endpoint and firewall.
Both the downloader and the backdoor components will be detected as Mem/Bazarld-c in our Intercept X endpoint product.
You know what also works, even if you don't have a Sophos product?
Don't click links that look like this.
/end
You know what also works, even if you don't have a Sophos product?
Don't click links that look like this.
/end

• • •
Missing some Tweet in this thread? You can try to
force a refresh