The Linux🐧 commands you should NEVER use.
Disclaimer DON'T🚫 run these commands.
A thread🧵👇
#CyberSecurity #infosec #Linux
Disclaimer DON'T🚫 run these commands.
A thread🧵👇
#CyberSecurity #infosec #Linux

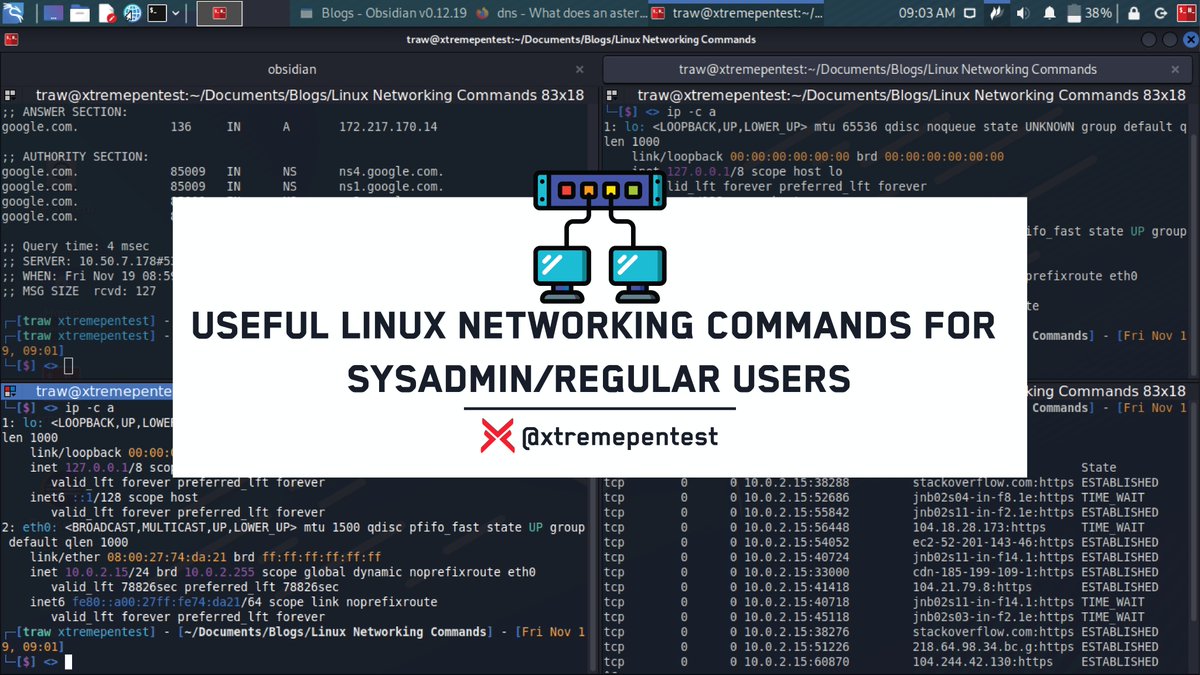
1. Recursive Deletion🔁🗑️
This is one of the most dangerous commands. Once this command is run, it deletes all the content of the root directory forcefully and recursively. Thus, all your directories and subdirectories will be deleted and the data will be lost.
This is one of the most dangerous commands. Once this command is run, it deletes all the content of the root directory forcefully and recursively. Thus, all your directories and subdirectories will be deleted and the data will be lost.

2. Fork Bomb🍴💣
My personal best😄,this is a simple bash recursive function which once executed creates copies of itself which in turn creates another set of copies of itself. This consumes the CPU time and memory. Thus, it runs recursively until the system freezes.
My personal best😄,this is a simple bash recursive function which once executed creates copies of itself which in turn creates another set of copies of itself. This consumes the CPU time and memory. Thus, it runs recursively until the system freezes.

3. Overwrite Hard Drive✍️💿
This command writes raw data (output of the command) to the specified partition. This results in data loss in the hard drive or mentioned partition.
command - this could be any command.
This command writes raw data (output of the command) to the specified partition. This results in data loss in the hard drive or mentioned partition.
command - this could be any command.

4. Implode Hard Drive🕳️
These commands will move all the data to a special location in Linux called the black hole (/dev/null). Anything moved to this location is destroyed. Thus if you accidentally move your data to this folder, your data is not going to be recovered anyway.

These commands will move all the data to a special location in Linux called the black hole (/dev/null). Anything moved to this location is destroyed. Thus if you accidentally move your data to this folder, your data is not going to be recovered anyway.


5. Download and Execute Malicious Script☠️📜
Wget is a very useful Linux command for fetching/downloading files from the internet. But this command can be dangerous if we blindly download and execute a malicious script.
Wget is a very useful Linux command for fetching/downloading files from the internet. But this command can be dangerous if we blindly download and execute a malicious script.

6. Format Hard Drive🧹📀
This command will wipe out your hard drive and makes it new. These should only be used in instances when you have either have your data backup on the cloud or external device.
This command will wipe out your hard drive and makes it new. These should only be used in instances when you have either have your data backup on the cloud or external device.

7. Write Random Junk to Hard Drive🈳📀
This command will write random junk data into your drive. The after effects of this command are that your system will not be recovered.
This command will write random junk data into your drive. The after effects of this command are that your system will not be recovered.

8. Breach the System🔓
This cmd doesn’t physically affect your system like the other commands do, but this provides a security breach on the system. By executing this command, you are providing all the users of the system to be able to read, write and execute data on your system.
This cmd doesn’t physically affect your system like the other commands do, but this provides a security breach on the system. By executing this command, you are providing all the users of the system to be able to read, write and execute data on your system.

9. The Hidden (rm -rf /)
The below command is nothing but the rm -rf / command above. Here the codes are hidden in hex so that an ignorant user may be fooled. Running the below code in your terminal will wipe your root partition.
The below command is nothing but the rm -rf / command above. Here the codes are hidden in hex so that an ignorant user may be fooled. Running the below code in your terminal will wipe your root partition.

Please DON'T execute any of the above commands in your Linux terminal or shell or of your friend or school computer. If you want to test them, run them in virtual machine. Any in-consistence or data loss, due to the execution of above command will break your system down.
That's it! Thank you for reading today's thread😇. If you have other DON'T run commands I have missed, feel free to add them in the comments. Would love to know them as well. And be sure to rt🔁, like💌 and follow me (@xtremepentest) for more future Linux content.
• • •
Missing some Tweet in this thread? You can try to
force a refresh