Useful Linux🐧 Networking🌐 Commands📜 for Sysadmins/Regular Users🧑💻
A thread🧵
Hello everyone👋, Today I'll be doing another quick, easy to follow thread🧵 on some of the most used command-line tools and utilities for network management in Linux
#infosec #CyberSecurity #Linux
A thread🧵
Hello everyone👋, Today I'll be doing another quick, easy to follow thread🧵 on some of the most used command-line tools and utilities for network management in Linux
#infosec #CyberSecurity #Linux
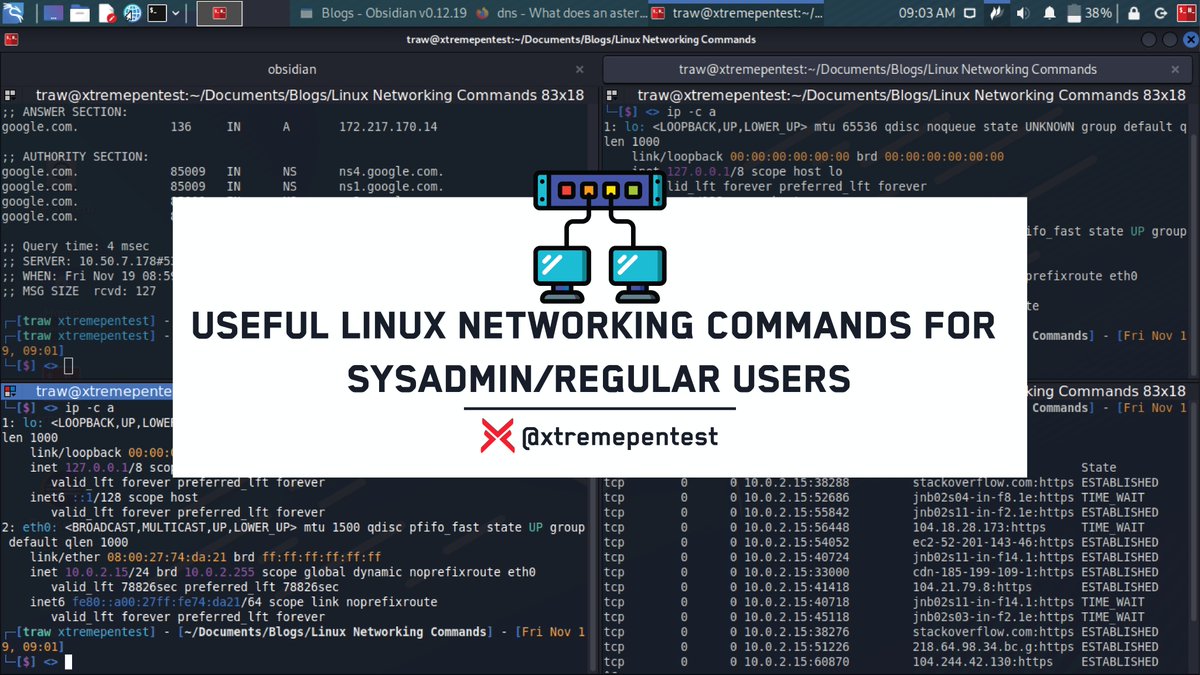
1. Ifconfig🌐
Ifconfig stands for Interface Configurator, it is one of the most used commands for finding network details, nitialize an interface, assign IP address, enable or disable an interface. It also display route and network interface.
Ifconfig stands for Interface Configurator, it is one of the most used commands for finding network details, nitialize an interface, assign IP address, enable or disable an interface. It also display route and network interface.
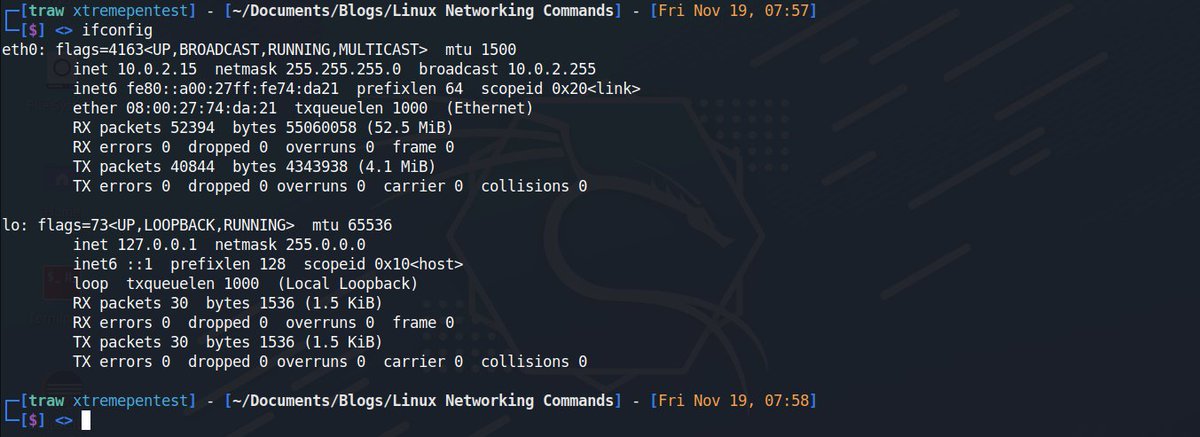
2. Ip🌐
ip command is the latest version of ifconfig. It is more powerful than ifconfig command as it can perform several other tasks that the ifconfig cannot do. The utility is used for displaying and manipulating routing, network devices, interfaces.
ip command is the latest version of ifconfig. It is more powerful than ifconfig command as it can perform several other tasks that the ifconfig cannot do. The utility is used for displaying and manipulating routing, network devices, interfaces.

3. Traceroute🌐
Traceroute - network troubleshooting utility for tracing the full path/route of packet from your local system to another network system.
Traceroute - network troubleshooting utility for tracing the full path/route of packet from your local system to another network system.

On the above output traceroute was only displaying asterisks, here is how the issue is fixed.
1. unix.stackexchange.com/questions/1270…
2. webmasters.stackexchange.com/questions/1779…
1. unix.stackexchange.com/questions/1270…
2. webmasters.stackexchange.com/questions/1779…
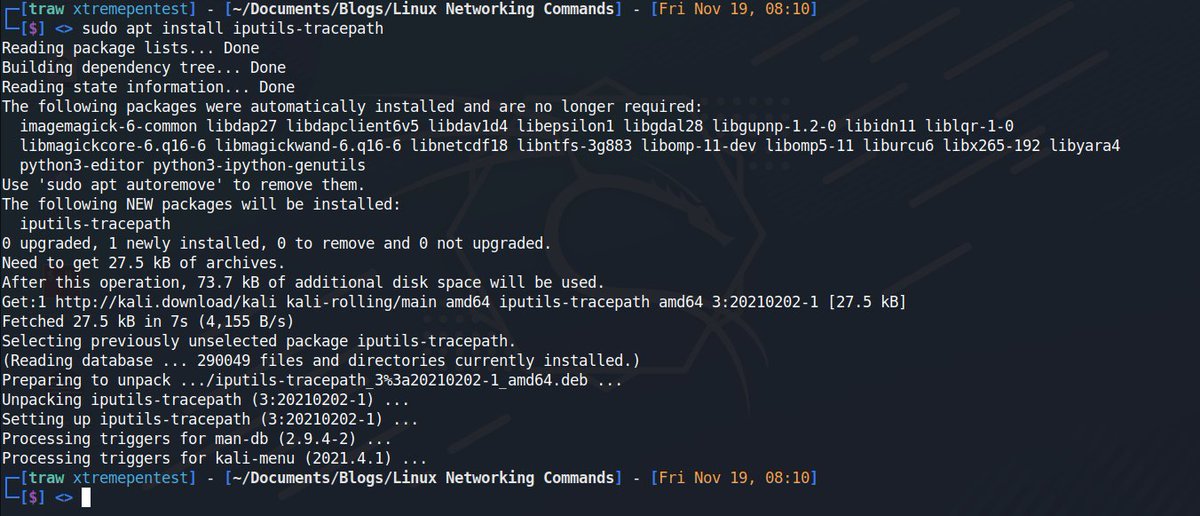
4. Tracepath🌐
It is similar to traceroute command, but it doesn't require root privileges. By default, it is installed in Ubuntu. If it's not found in your system you have to install using the below easy to follow procedure.
It is similar to traceroute command, but it doesn't require root privileges. By default, it is installed in Ubuntu. If it's not found in your system you have to install using the below easy to follow procedure.
Tracepath traces the network path of the specified destination and reports each hop along the path. If you have a slow network then tracepath will show you where your network is weak. 

5. Ping🌐
Packet Internet Gropper (Ping) - it is used to check the connectivity between two hosts/nodes on a Local Area Network or Wide Area Network. It makes use of the ICMPs (Internet Control Message Protocol) to make communicate with end nodes.
Packet Internet Gropper (Ping) - it is used to check the connectivity between two hosts/nodes on a Local Area Network or Wide Area Network. It makes use of the ICMPs (Internet Control Message Protocol) to make communicate with end nodes.

6. Netstat🌐
Netstat command stands for Network statistics . It displays information about different interface statistics, including open sockets, routing tables, and connection information. Here is an example of displaying all network connections.
Netstat command stands for Network statistics . It displays information about different interface statistics, including open sockets, routing tables, and connection information. Here is an example of displaying all network connections.

The netstat command supports various command-line options, few free to check netstat man pages.
7. ss🌐
The ss command is a replacement for netstat command. This command gives more information in comparison to the netstat. It is also faster than netstat as it gets all information from kernel userspace.
Here is a full thread on the ss command.
The ss command is a replacement for netstat command. This command gives more information in comparison to the netstat. It is also faster than netstat as it gets all information from kernel userspace.
Here is a full thread on the ss command.
https://twitter.com/xtremepentest/status/1446562881504522246?s=20
8. dig🌐
Dig stands for domain internet gropper is ar simple DNS lookup utility, that is used to query DNS related information such as A Record, CNAME, MX Record etc. It mainly deals with troubleshooting DNS related problems.
Dig stands for domain internet gropper is ar simple DNS lookup utility, that is used to query DNS related information such as A Record, CNAME, MX Record etc. It mainly deals with troubleshooting DNS related problems.

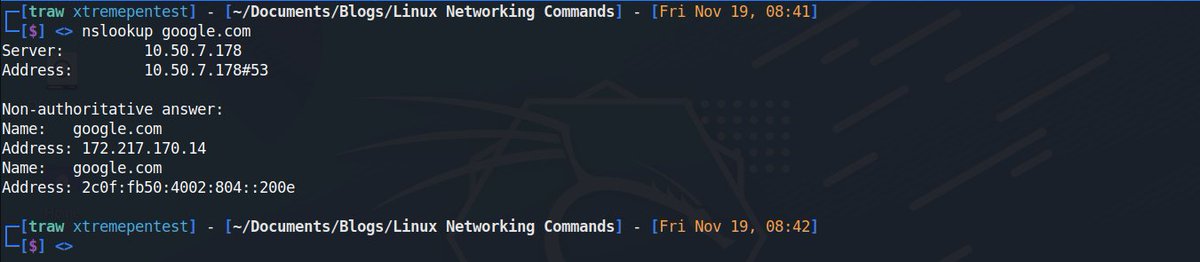
9. Nslookup🌐
This is also another command-line utility to query DNS servers both interactively and non-interactively. It is used to query DNS resource records (RR). You can find out the “A” record (IP address) of a domain.
This is also another command-line utility to query DNS servers both interactively and non-interactively. It is used to query DNS resource records (RR). You can find out the “A” record (IP address) of a domain.
11. host🌐
the host command displays domain name for given IP address or vice-versa. It also performs DNS lookups related to the DNS query.
the host command displays domain name for given IP address or vice-versa. It also performs DNS lookups related to the DNS query.

12. arp🌐
The command arp stands for Address Resoslution Protocol. It allows us to view or add content into kernel's ARP table.
The command arp stands for Address Resoslution Protocol. It allows us to view or add content into kernel's ARP table.

13. iwconfig🌐
The command iwconfig configures a wireless network interface. You can view and set basic wi-fi details like SSID and encryption. For more details on this command please refer man page of iwconfig.
The command iwconfig configures a wireless network interface. You can view and set basic wi-fi details like SSID and encryption. For more details on this command please refer man page of iwconfig.

14. Hostname🌐
the hostname command allows us to set and view /show system's hostname. A hostname is the name of any computer that is connected to a network that is uniquely identified over a network.
the hostname command allows us to set and view /show system's hostname. A hostname is the name of any computer that is connected to a network that is uniquely identified over a network.

15. Whois🌐
The whois command displays information about a website's record. You may get all the information about a website regarding its registration and owner's information.
The whois command displays information about a website's record. You may get all the information about a website regarding its registration and owner's information.

That's it for today's thread! Thank💌 you for reading📚If you liked the thread and found it useful, give me a follow (@xtremepentest) for future Linux, Networking and Security content!. Be sure to also add some commands for text manipulation, would love to know them as well.😇
• • •
Missing some Tweet in this thread? You can try to
force a refresh