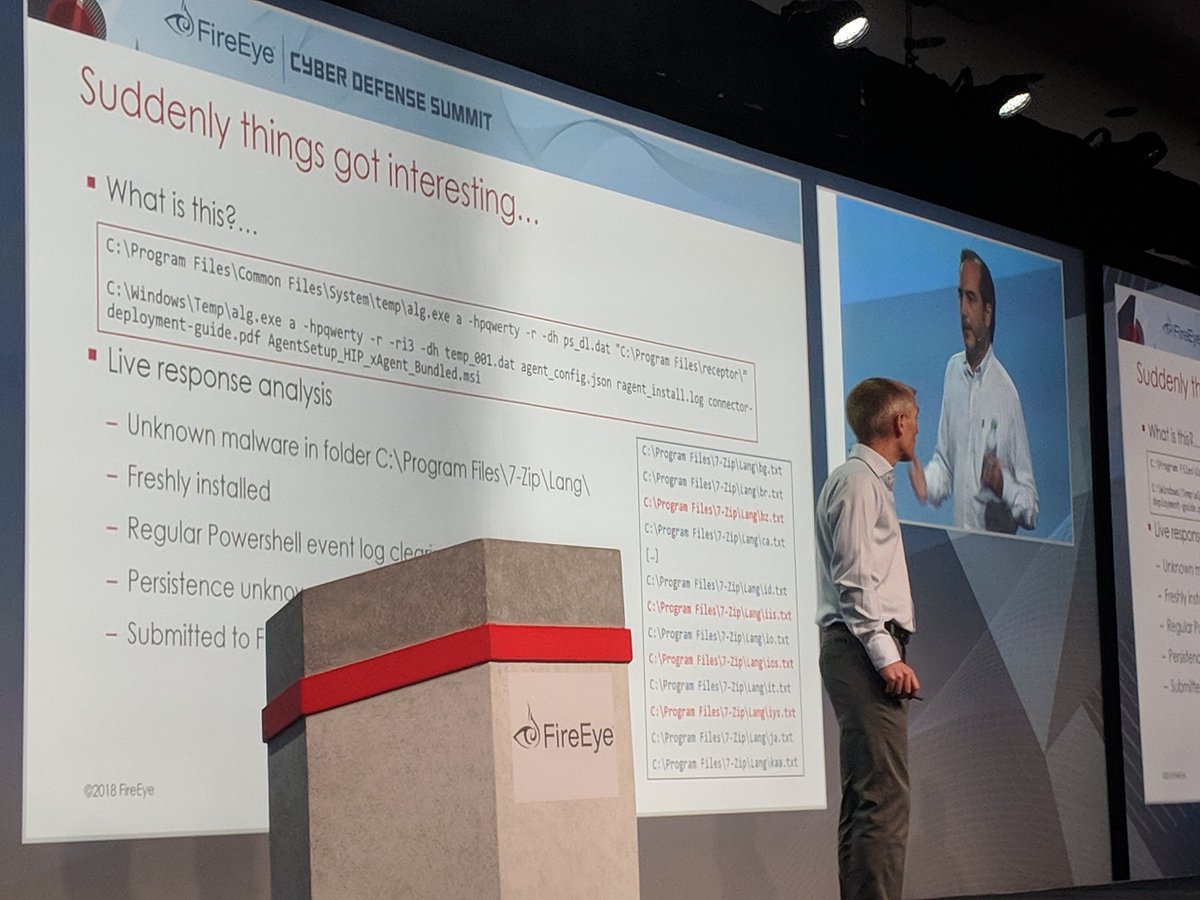
Thread 1/n
0433aeff0ed2cdf5776856f2c37be975
PDB: D:\codes\WinHexCalc\Release\hexcalc.pdb
This led me to search for the original (shady) project from Github: github.com/azlan/WinHexCa…
and this indeed contains this initial hexcalc.exe
2/n
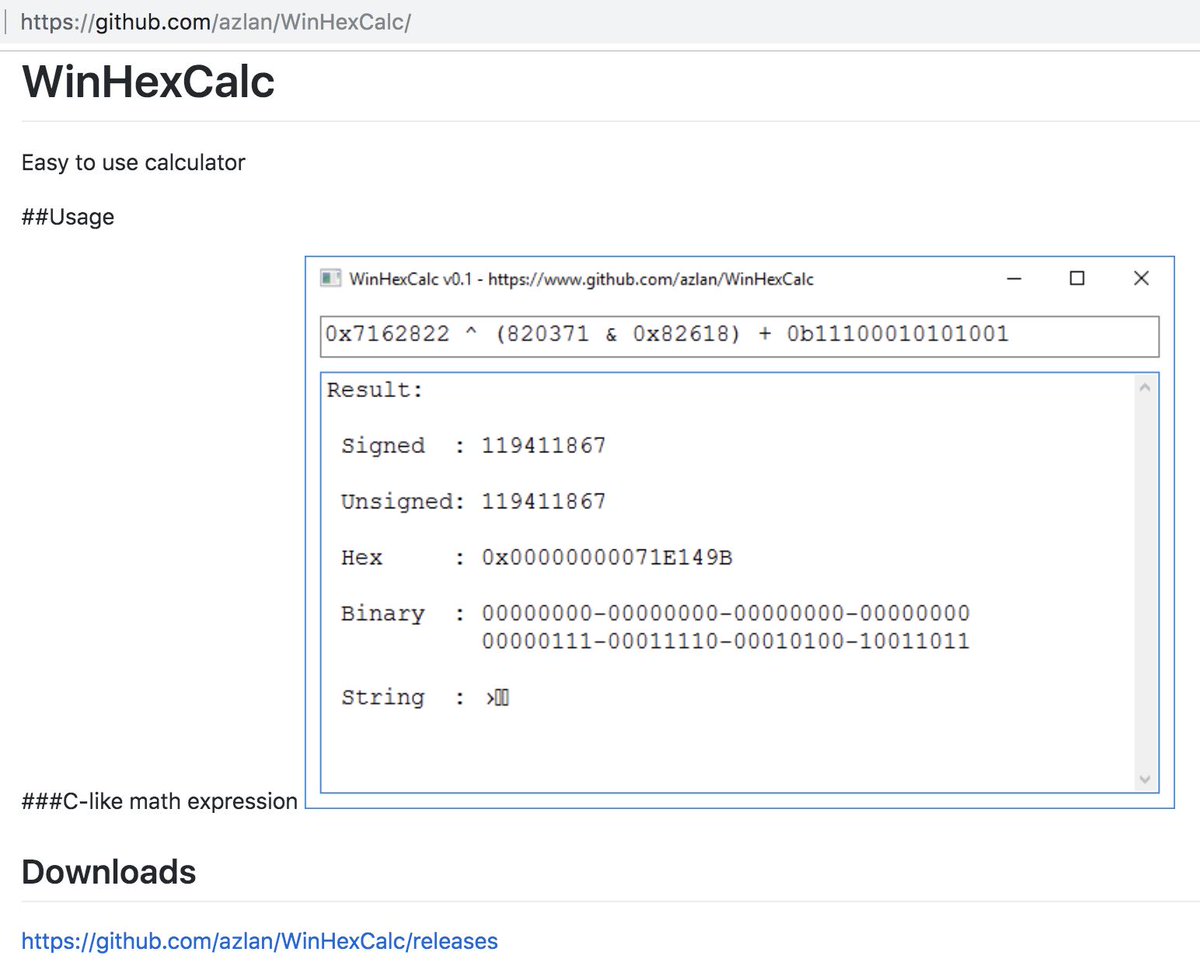
ae73fe66415edbfd5669ab567793536b
d7c7c9ef1c1725f497ef5feaa654fc2e
7feaa6255459dcba370252e8905a9a4a
ddc442bd5e5d157011ae79c48ee2189a
PDB: F:\Devel\WinHexCalc-master\Release\hexcalc.pdb
3/n
^this captures all of these files, it is further discussed here:
4/n
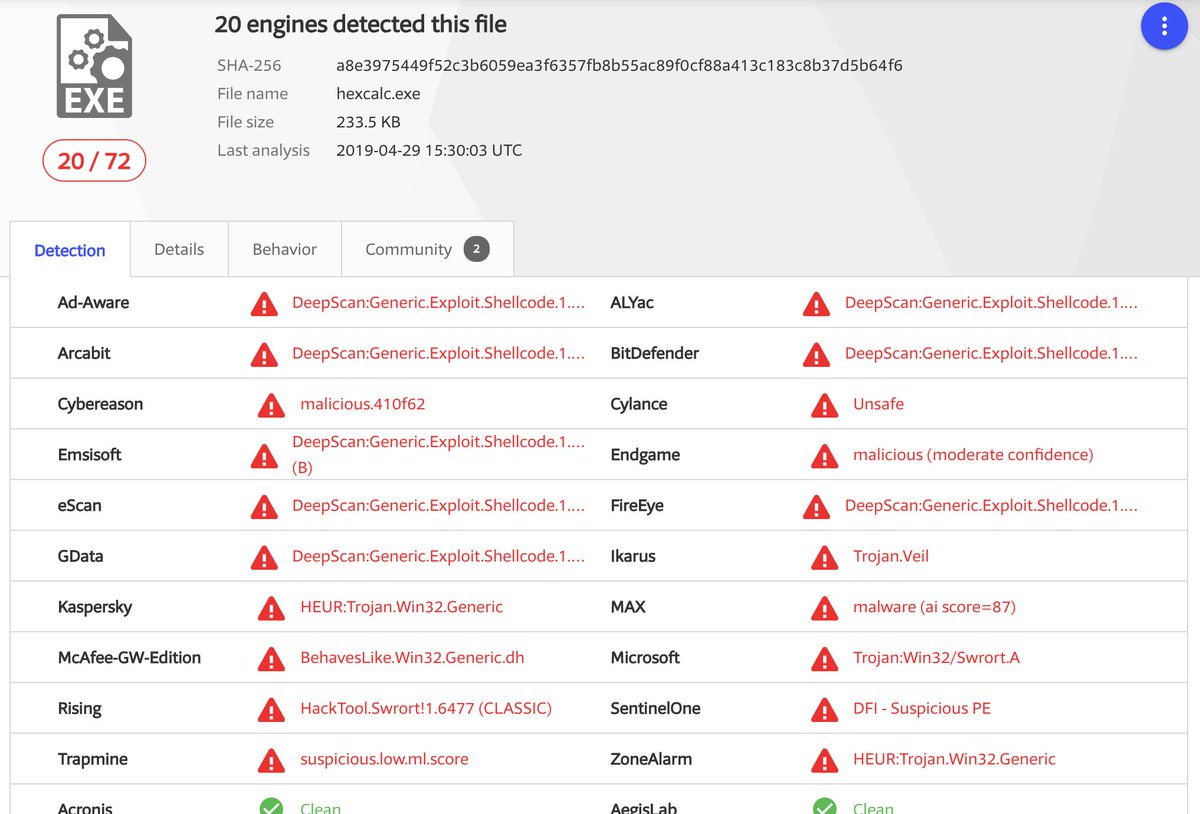
e48e566410f6238647eb5ed24cbd6910
Same attacker PDB: F:\Devel\WinHexCalc-master\Release\hexcalc.pdb
Higher detection rate on non-PS1 shellcode: virustotal.com/#/file/a8e3975…
5/n
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0)
Refresher on specifying User-Agent when grabbing the payloads:
6/n
7/n
8/n
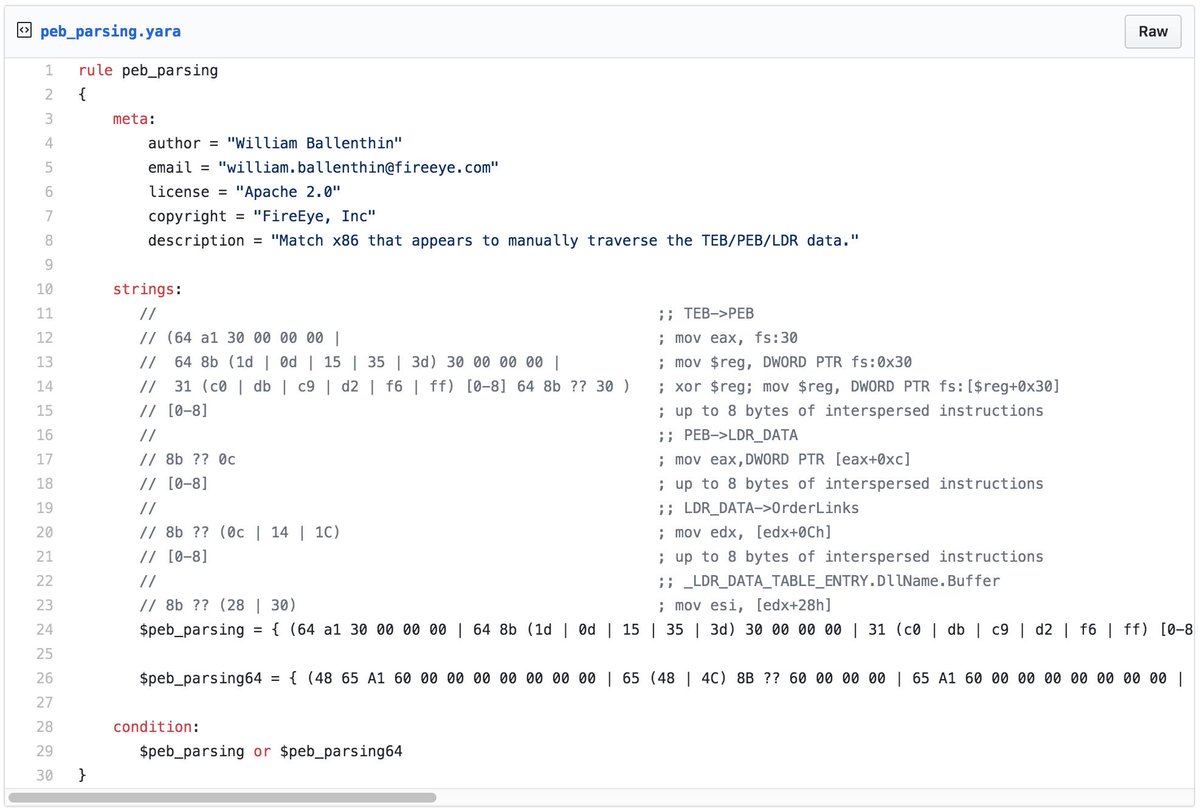
but the techniques used to detect, understand, and cluster/link this activity together work on real important stuff too -- we just can't always share that on Twitter.
Now go use the referenced #yara hunting rules. 😉
9/9