Every day or two, they'd move to 10 new systems, dropping SEADADDY on 9 of them.
35/n
For Python fans specifically, @byt3bl33d3r released #SilentTrinity last year: github.com/byt3bl33d3r/SI…
36/n
37/n
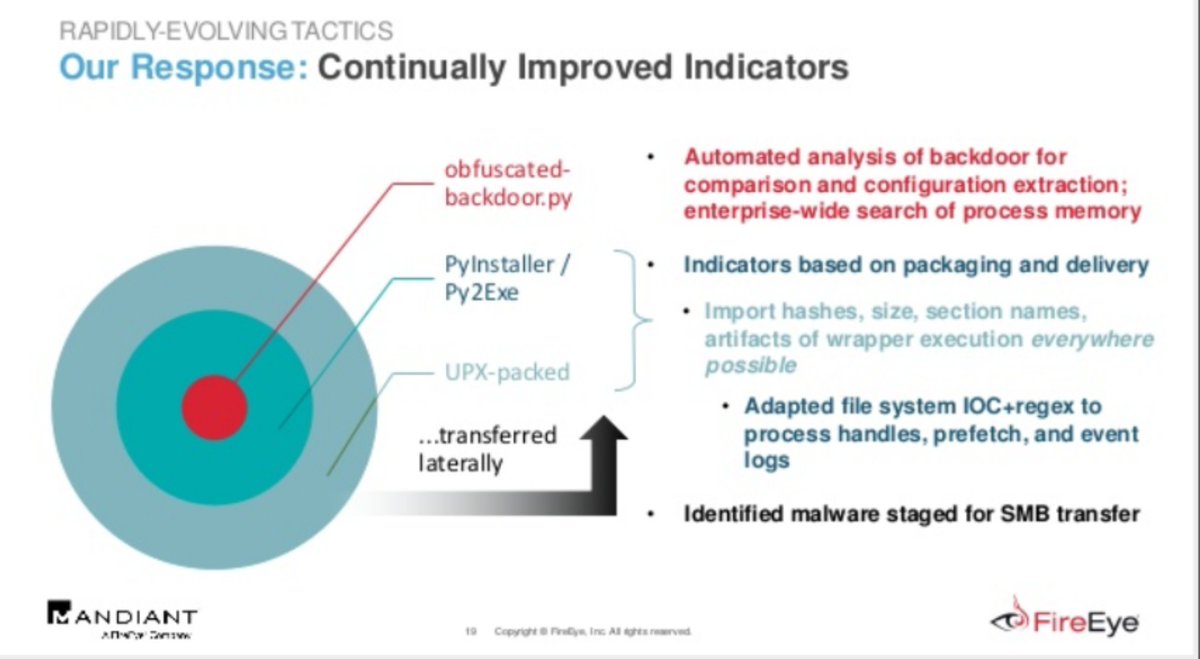
We watched APT29 actively develop the underlying Python within those ~9 new SEADADDY samples-per-day.
Weekly tweaks, 3 major revisions.
7 persistence mechanisms.
38/n
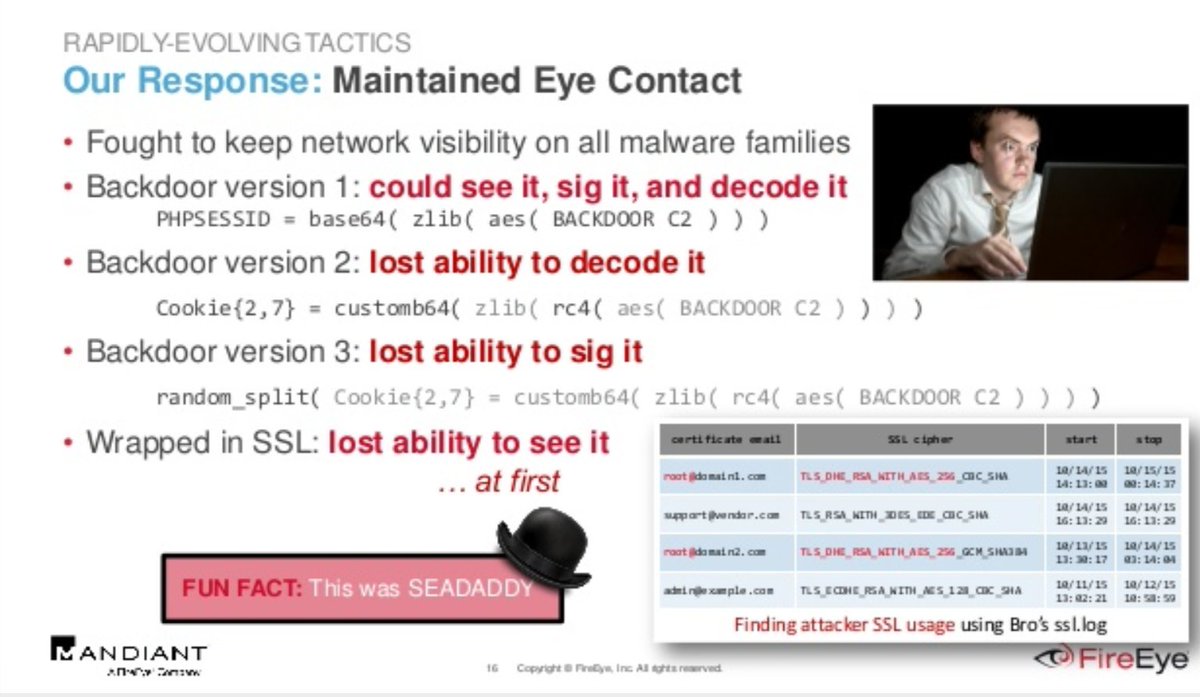
When #APT29 built SSL into SEADADDY's comms to compromised C2, we lost them. Until we found new ways to profile x509 w/ Bro & track Python-initiated SSL (early TLS fingerprinting).
39/n
👀 DETAILS:
40/n