Over 48hrs I captured tweets on tags #郭文贵 & #milesguo. This THREAD is an #OSINT analysis of how the network operates 🤖👇🤖
cc: @TwitterSafety
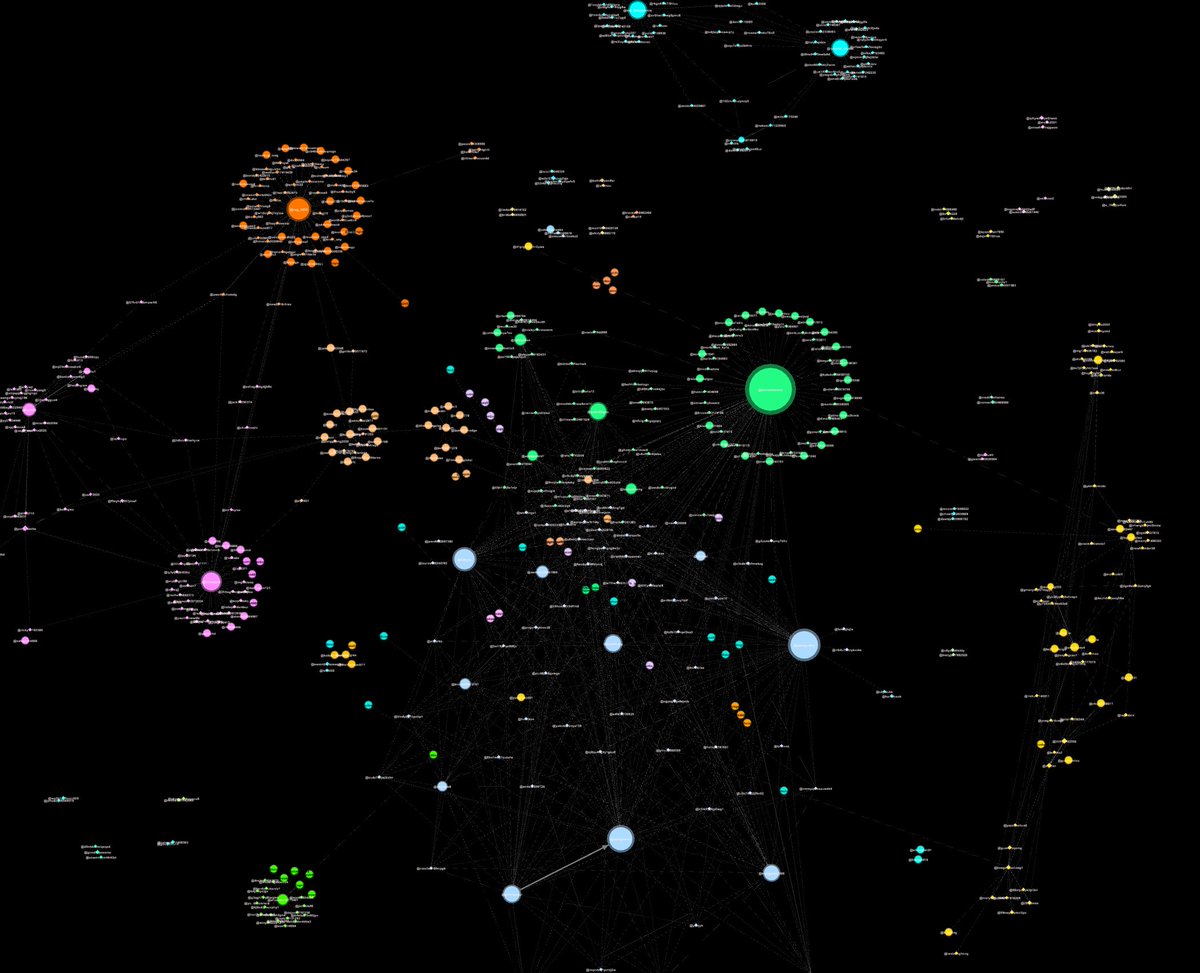

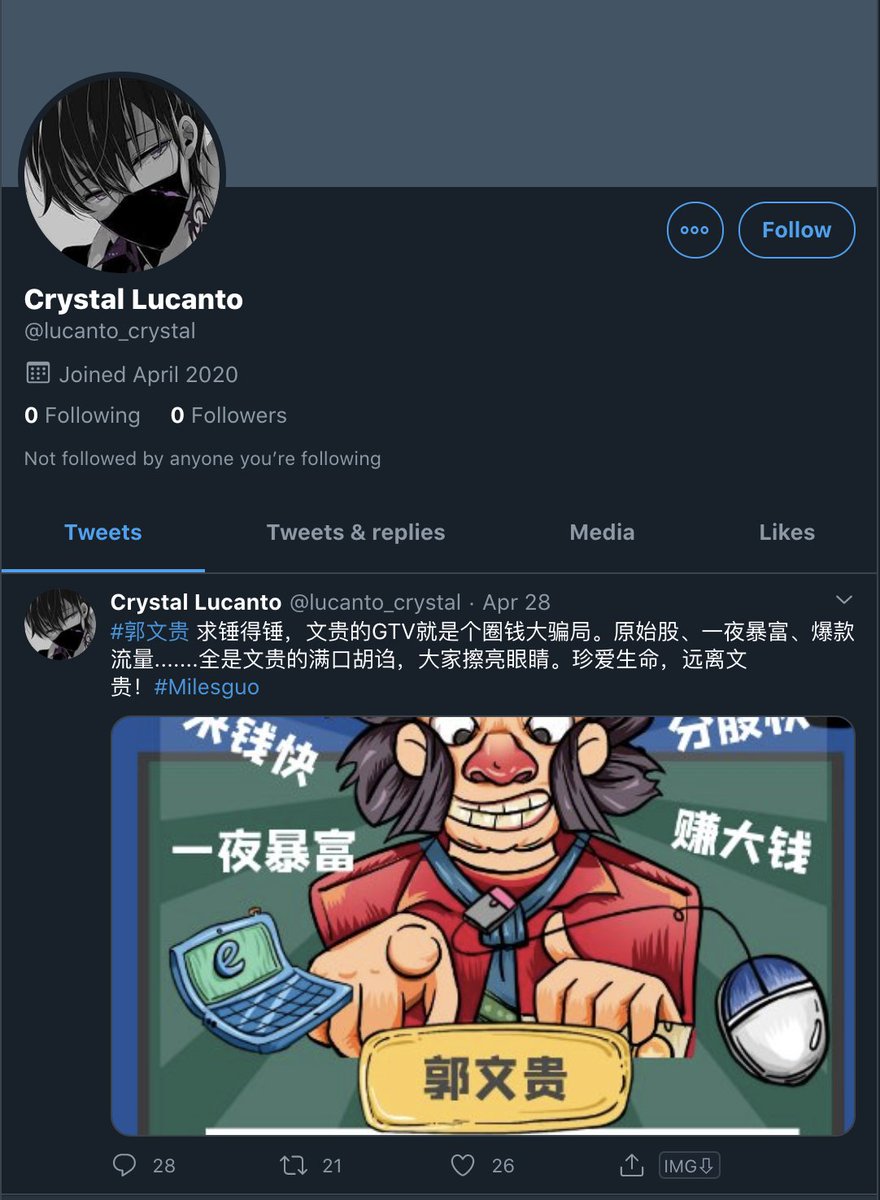
The findings were no surprise 🤖🤖🤖
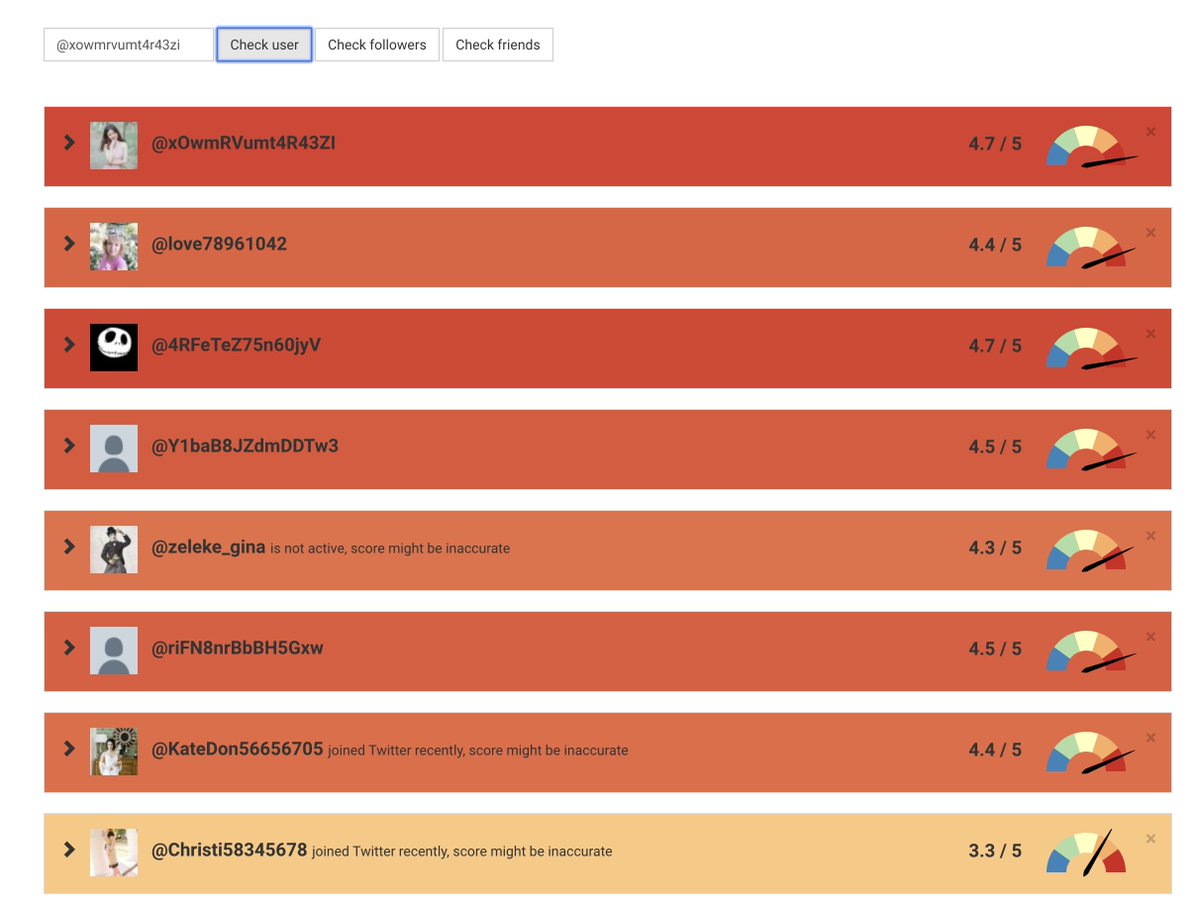
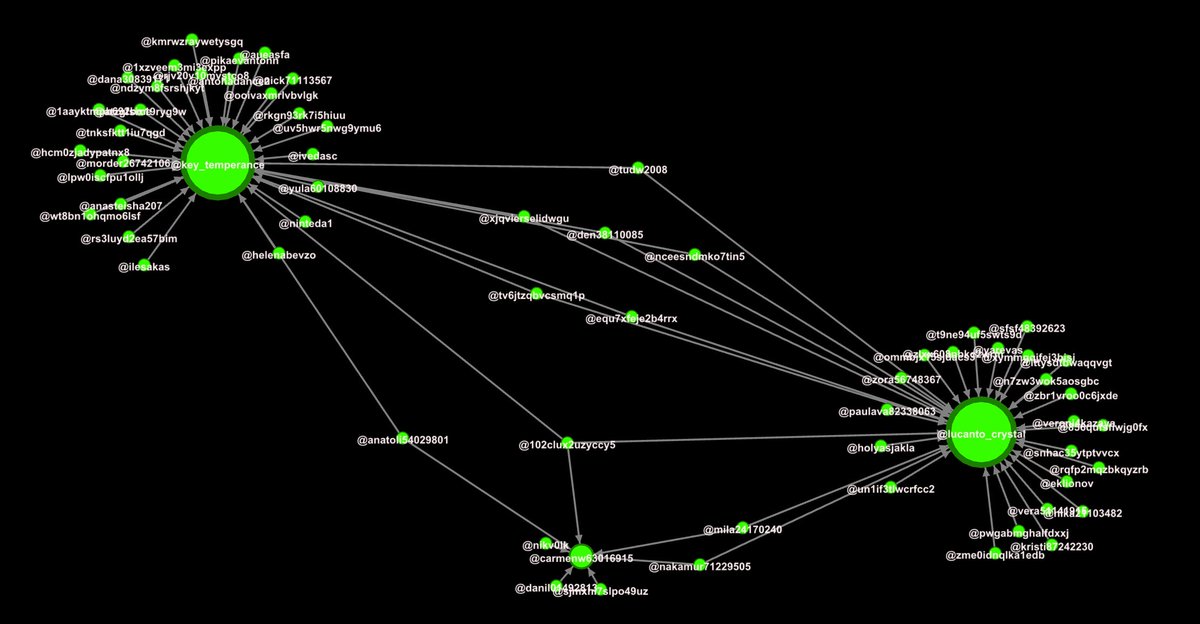
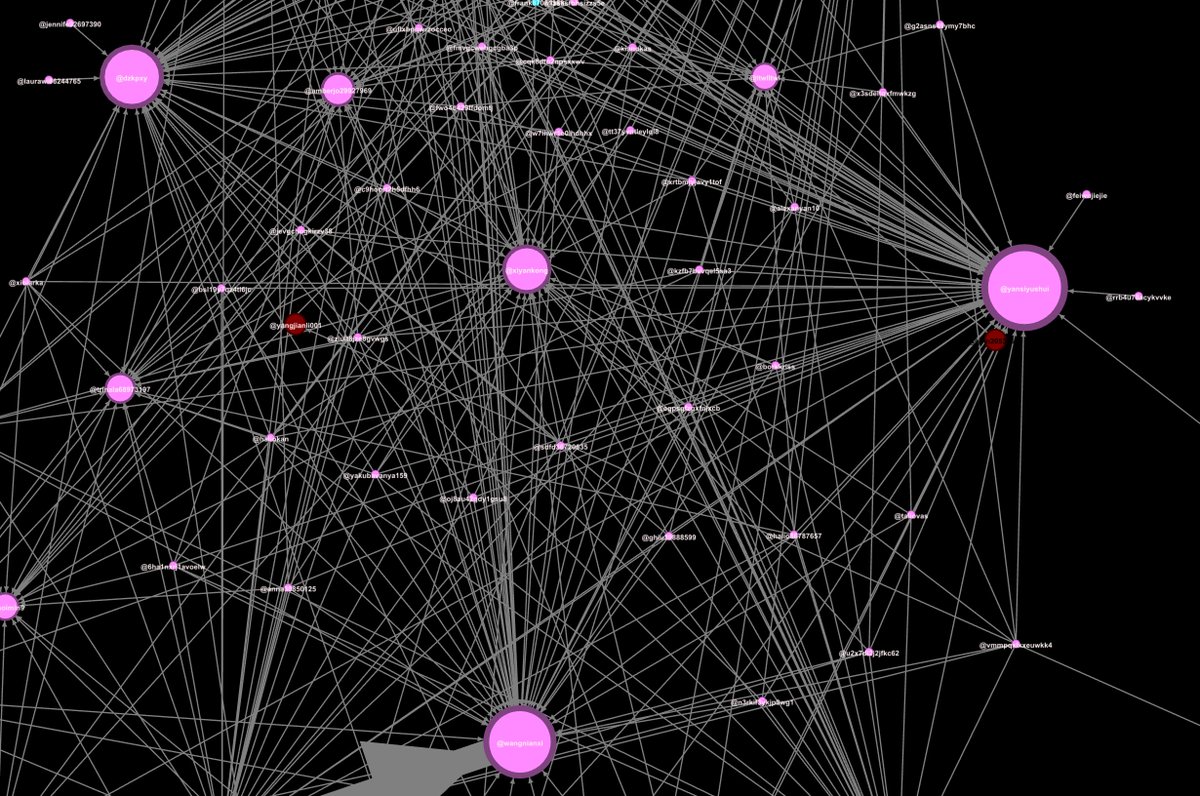
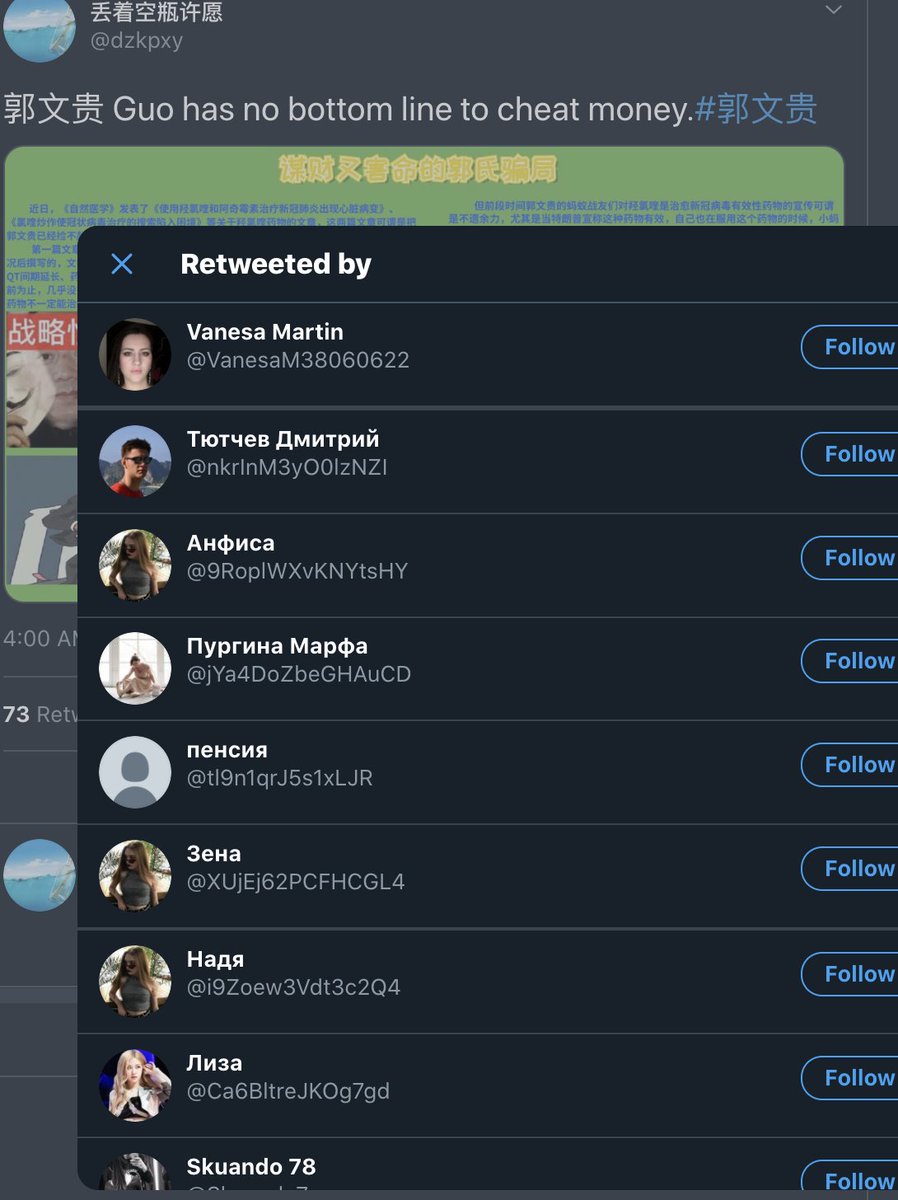
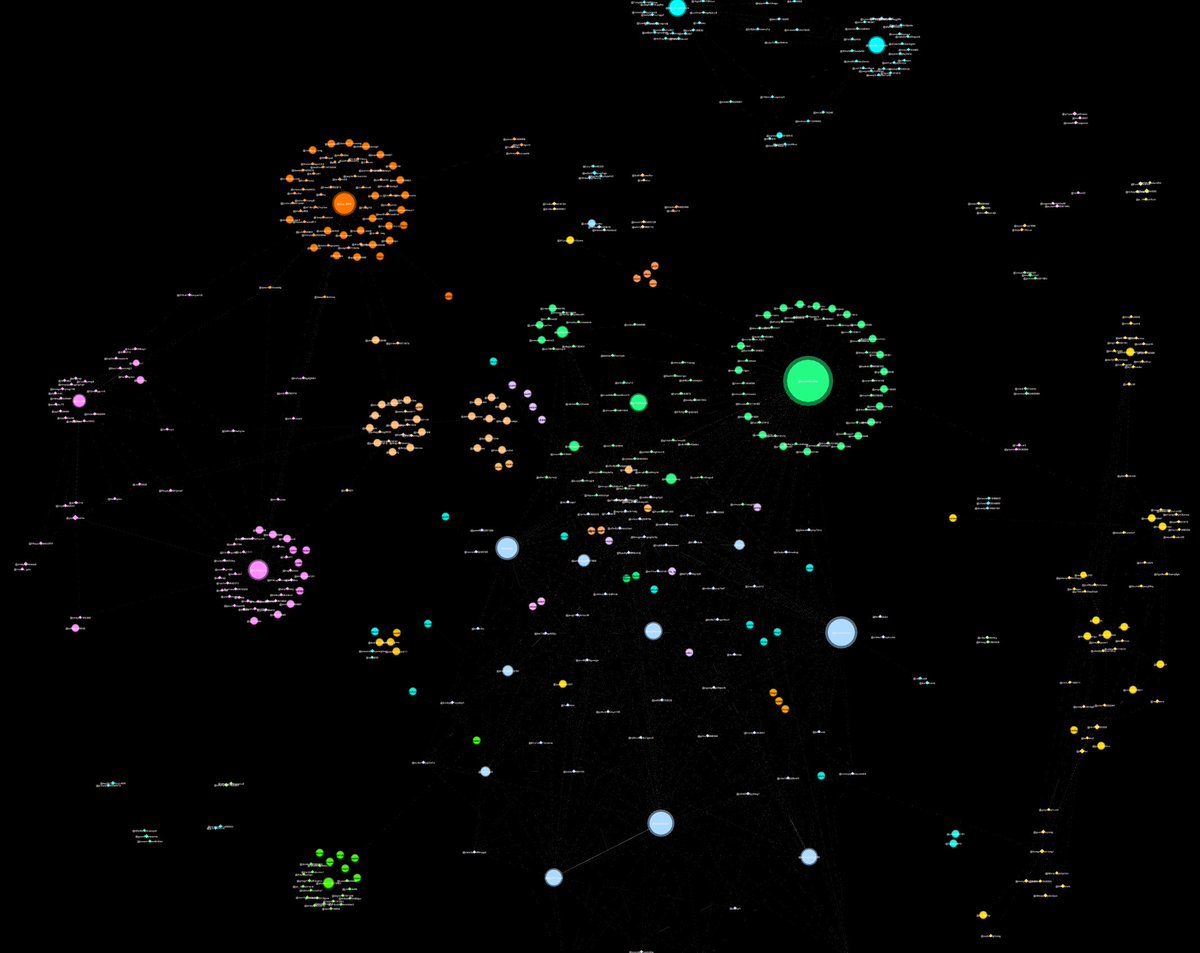
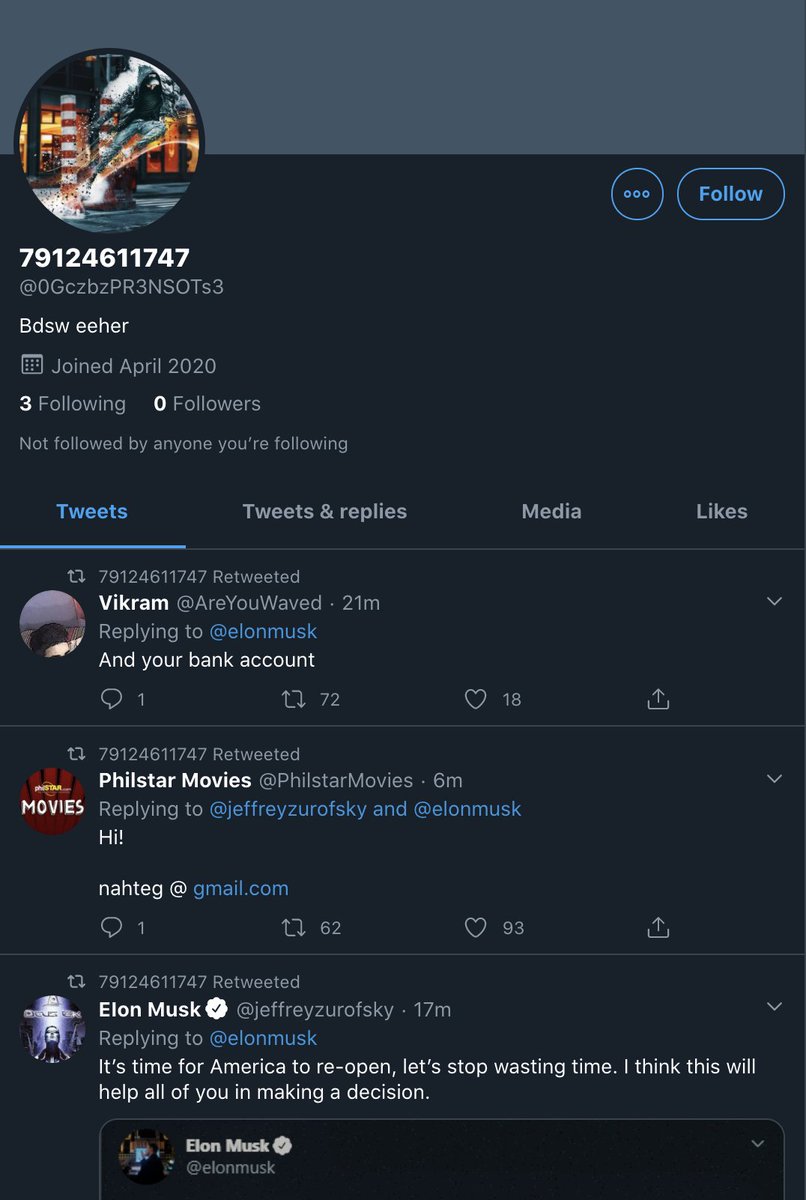
Well there's a concentrated inauthentic use of @Twitter by creating a large number of accounts (again, the sample data is only from 48hrs) to promote an agenda and maintain an information operation.
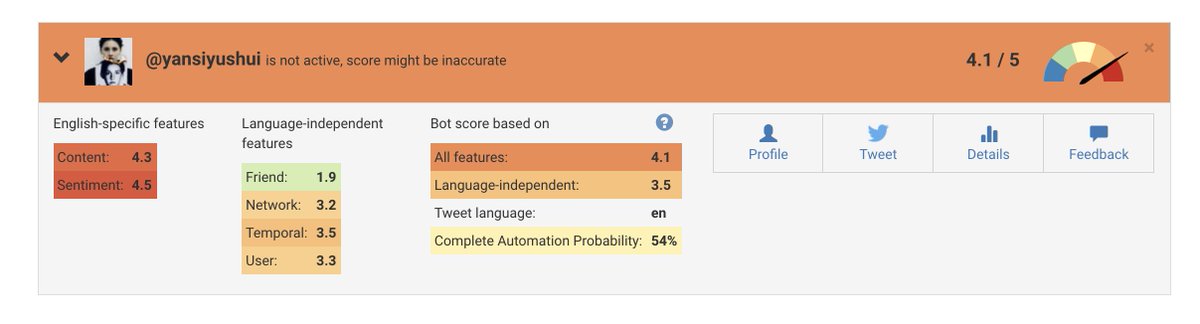
Oh, and they smell of botlike activity.
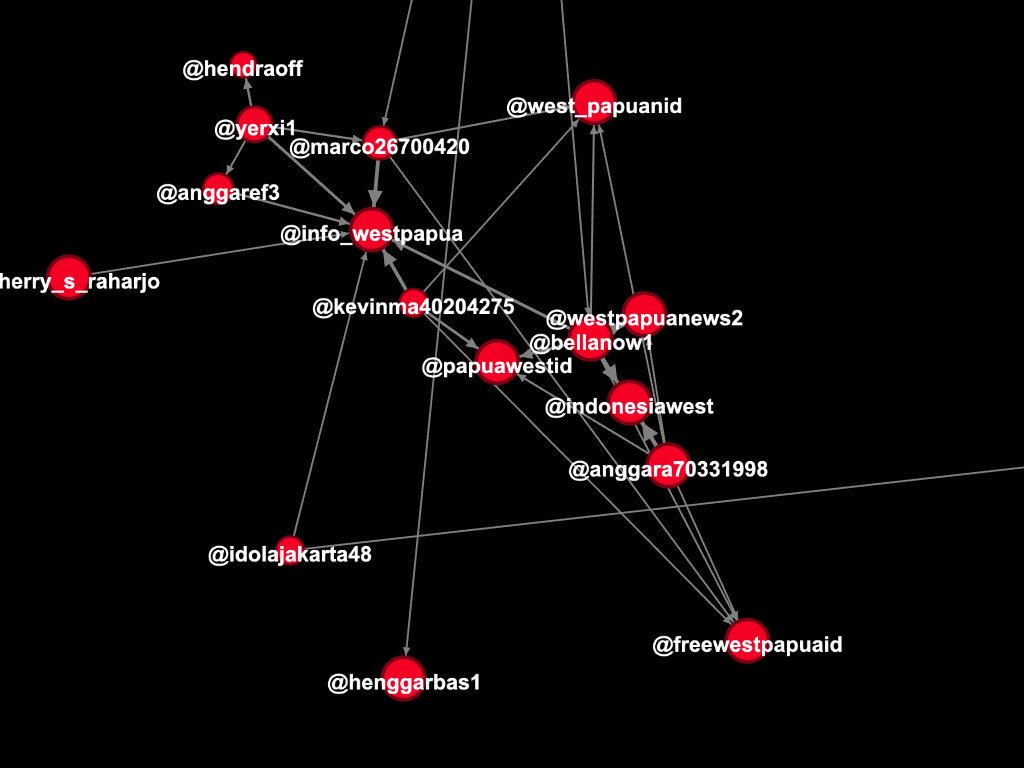
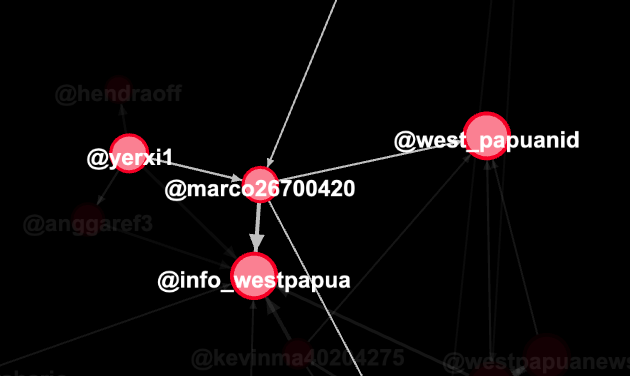
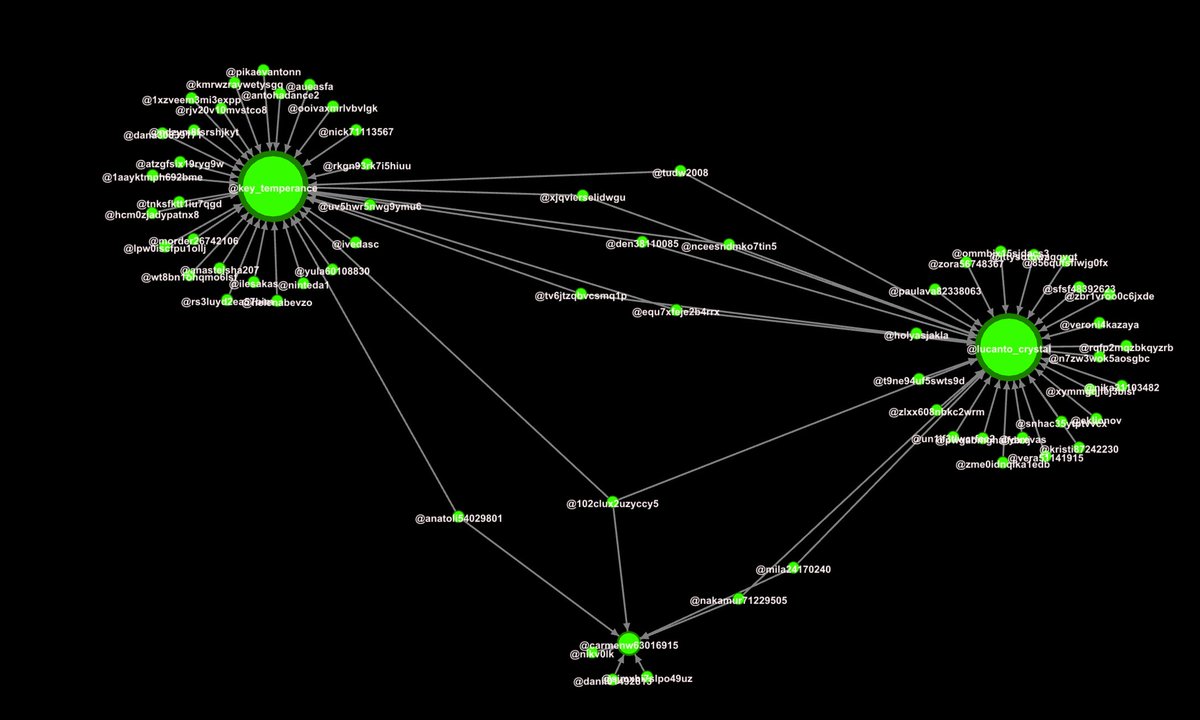
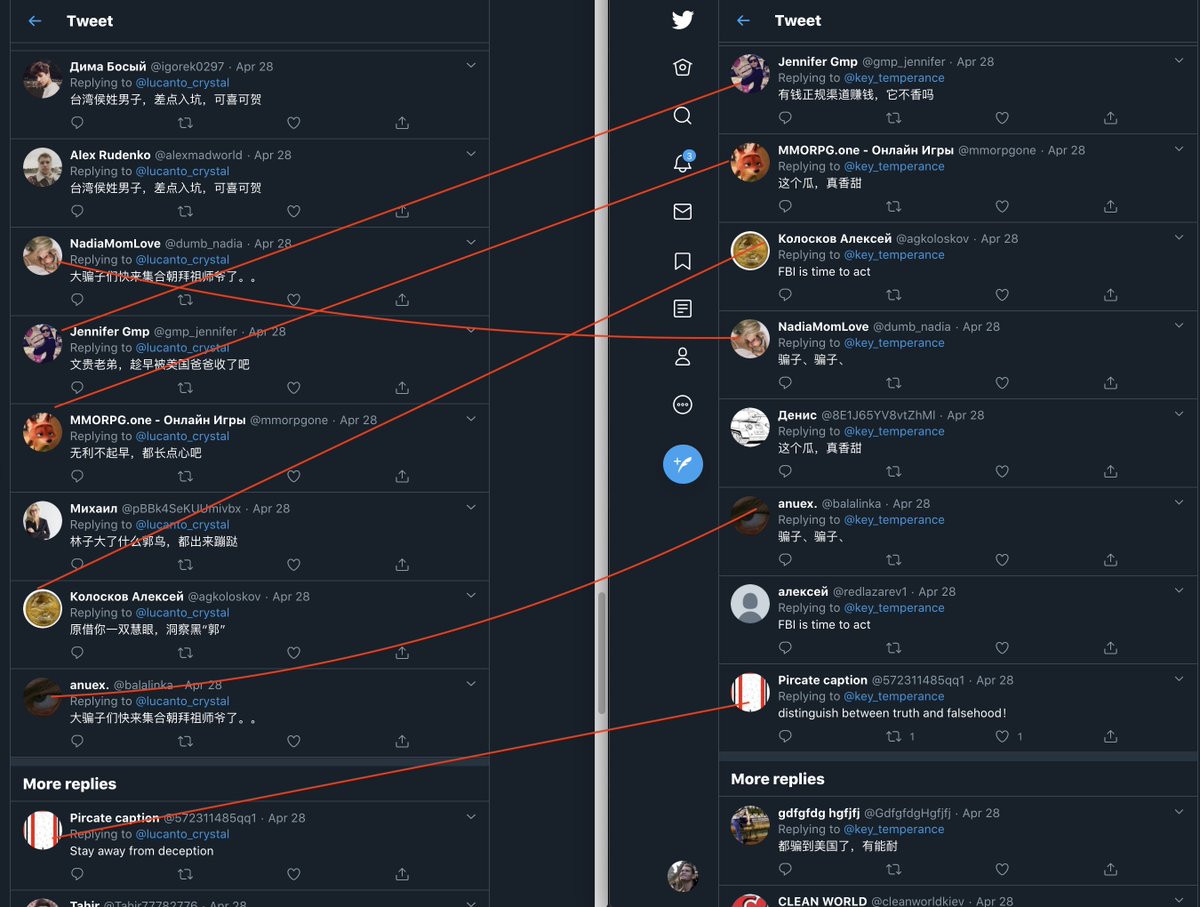
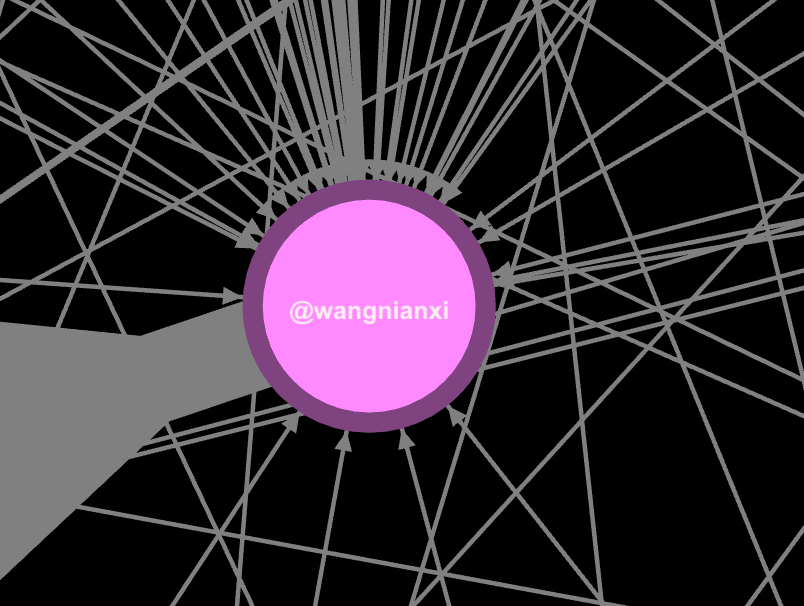
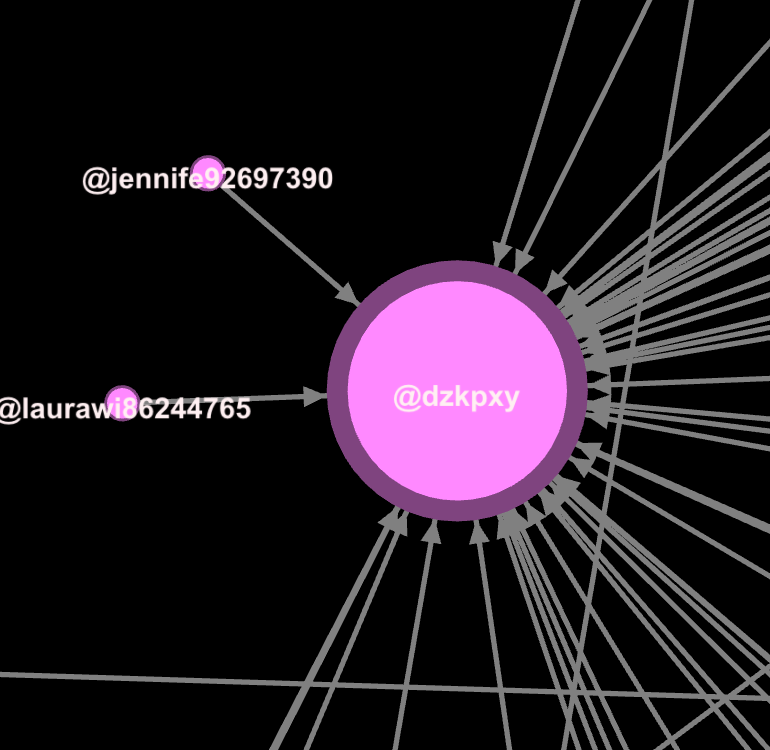
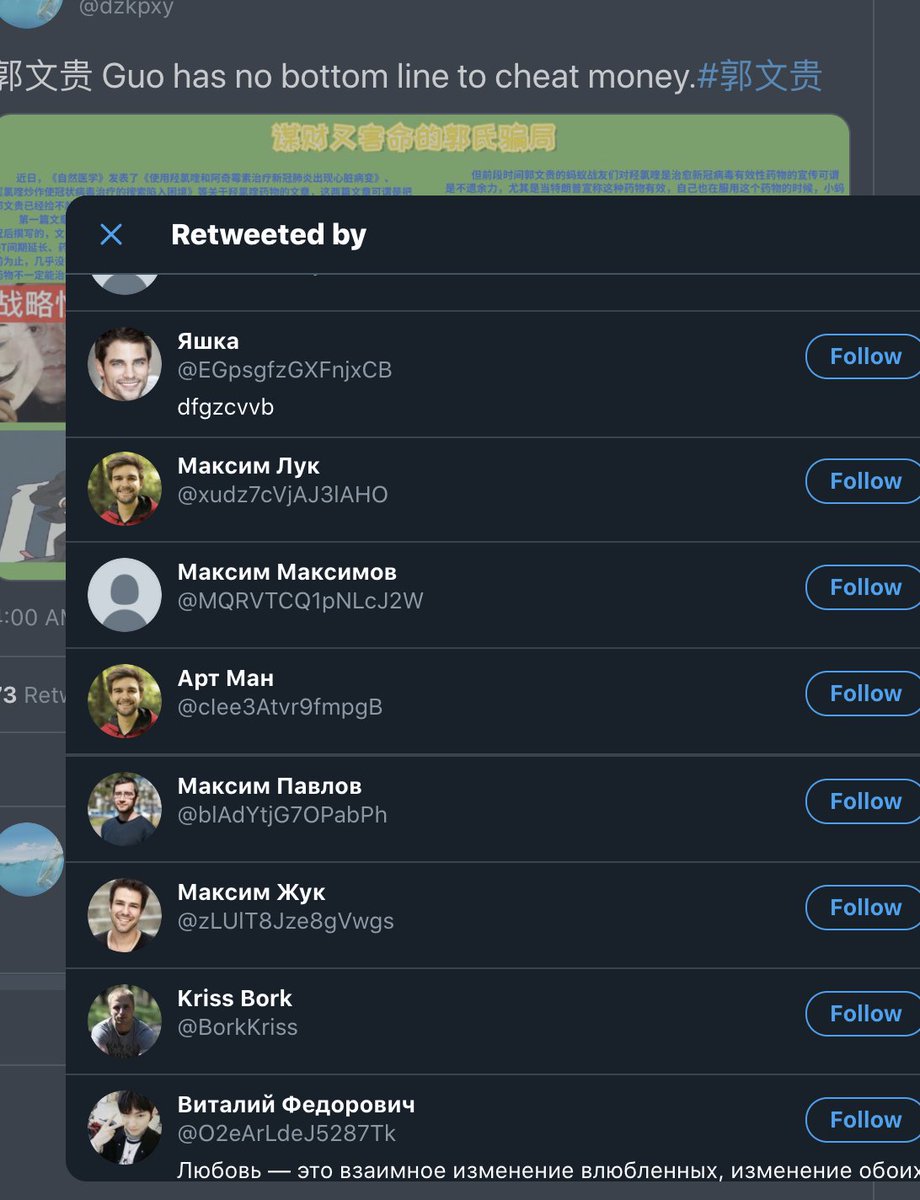
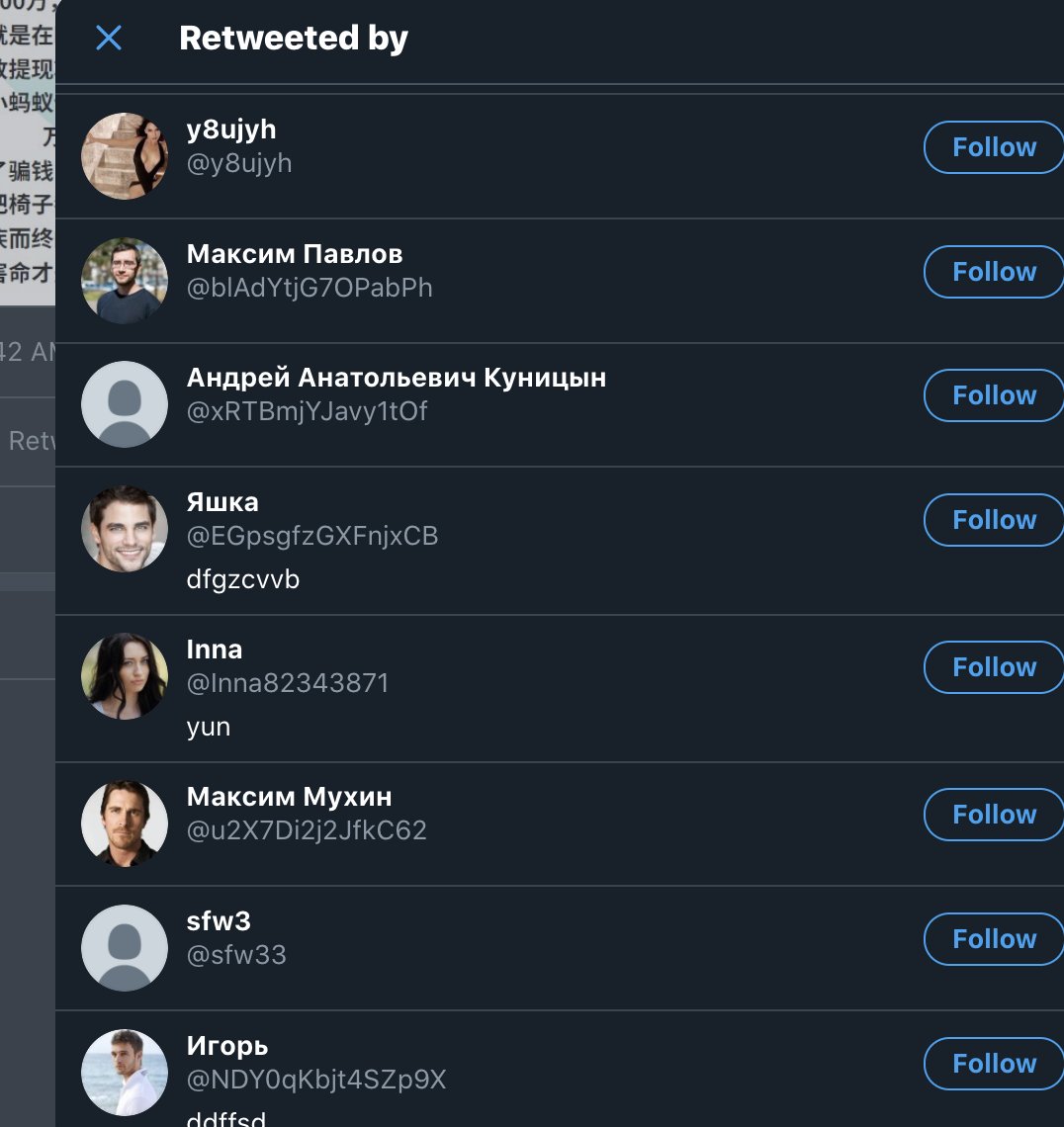
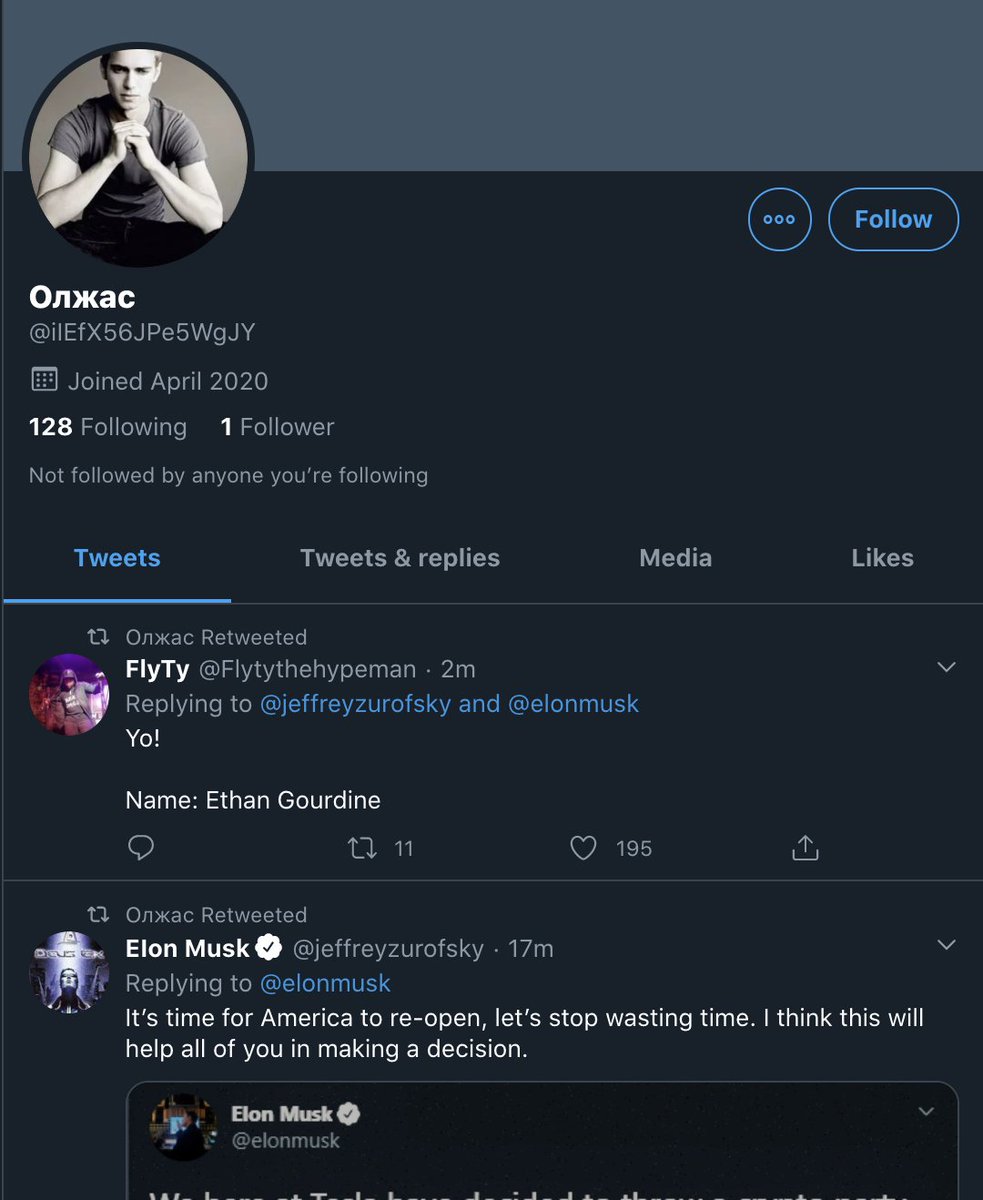
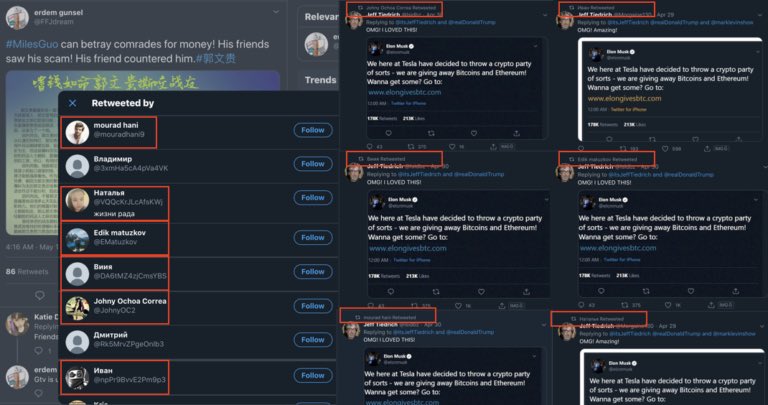
look 'linked'. Take a look at the relationship between the two posts, it shows the same style of post, comments, and almost the exact same accounts commenting.
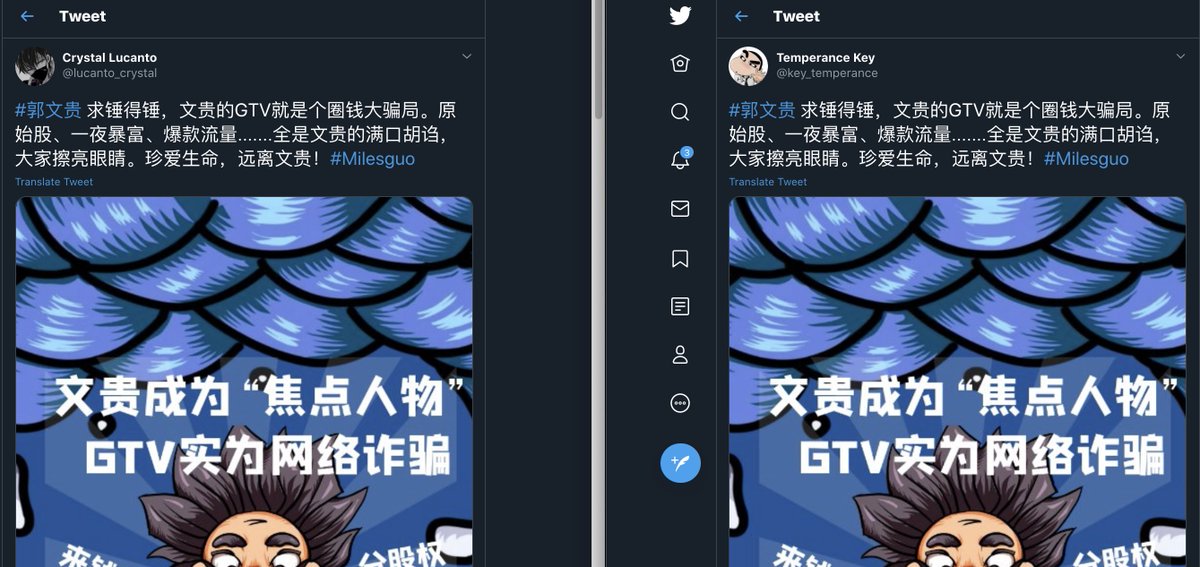
@yansiyushui
@wangnianxi
@dzkpxy
@xiyankong
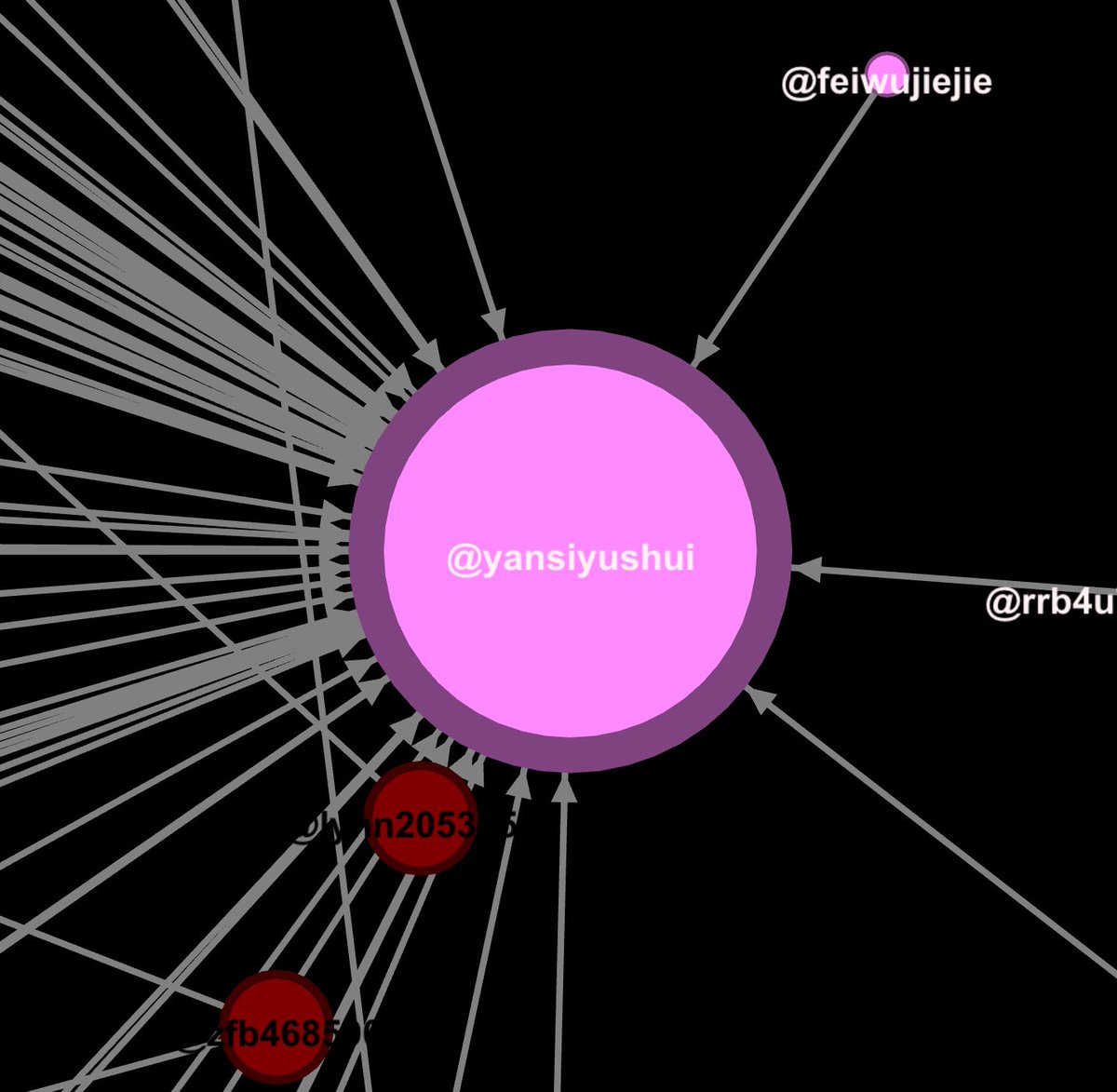
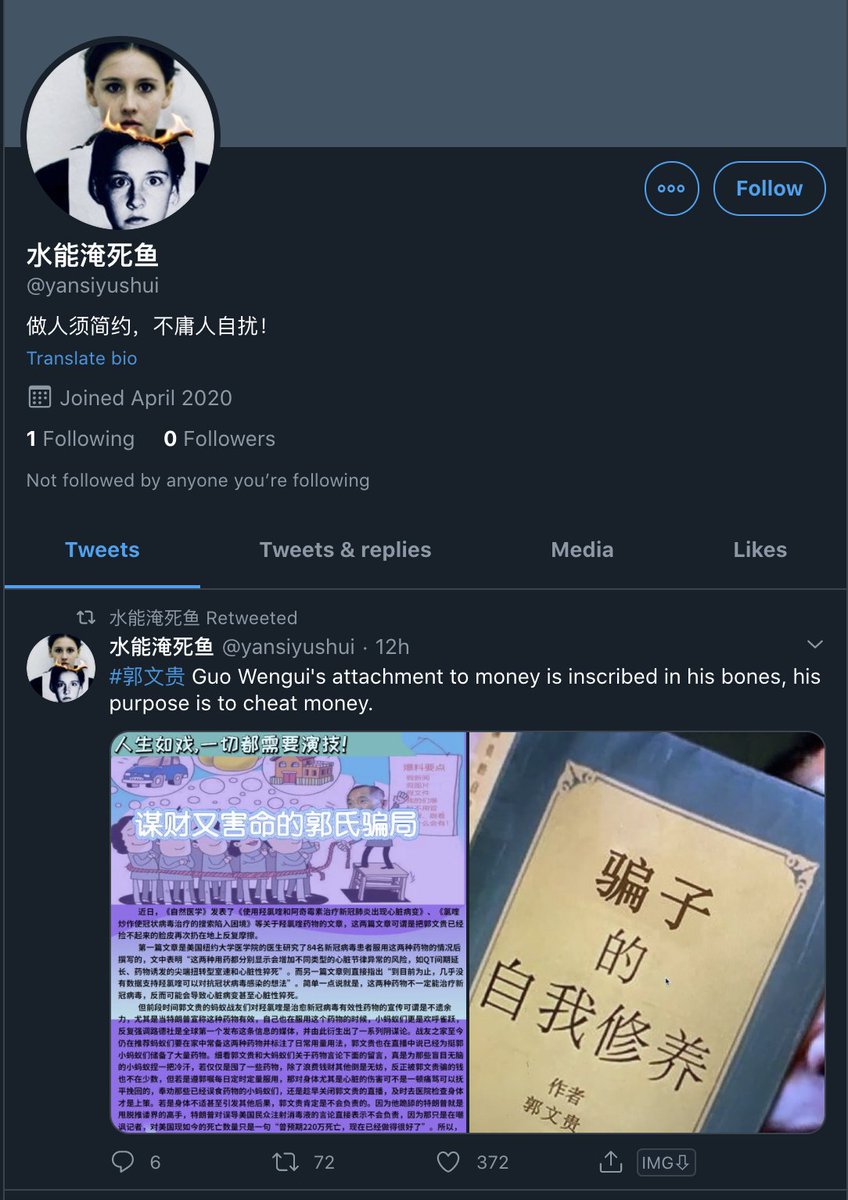
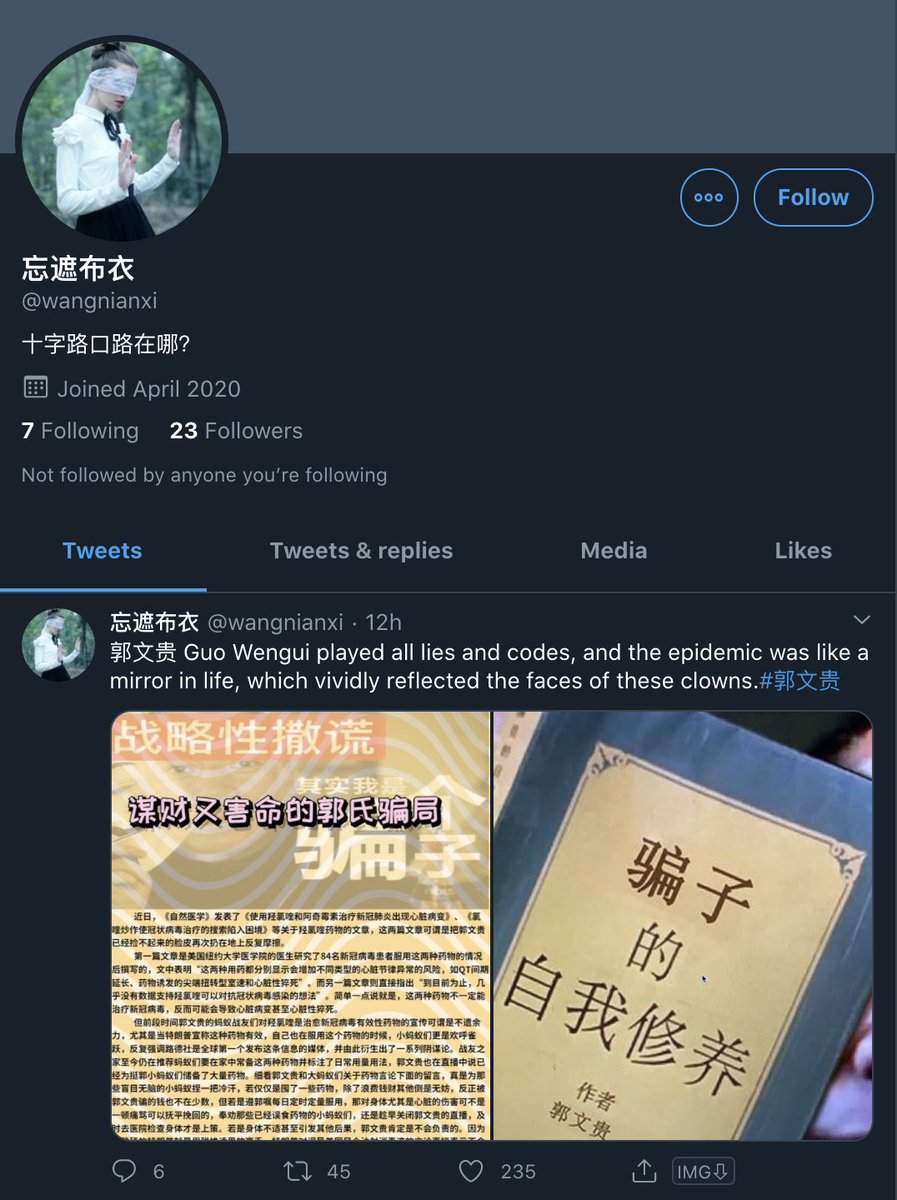

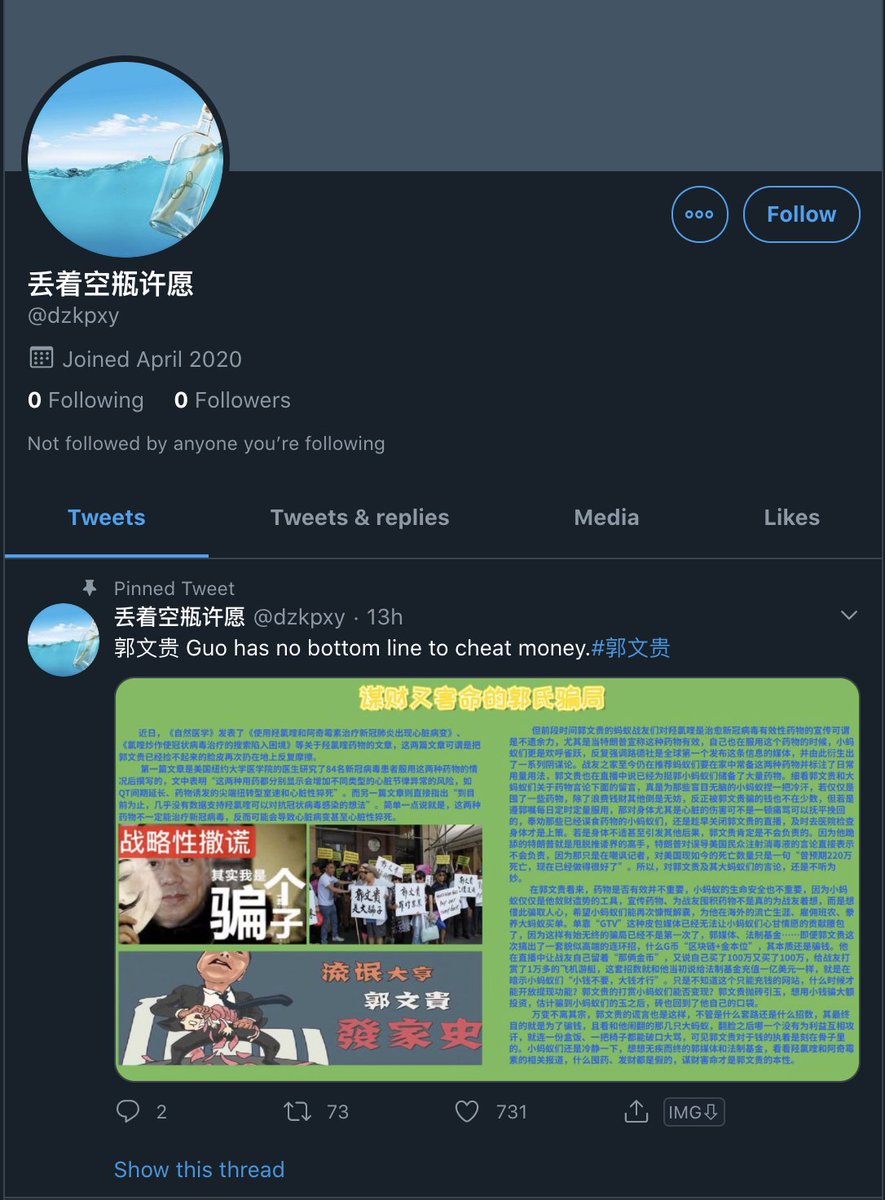
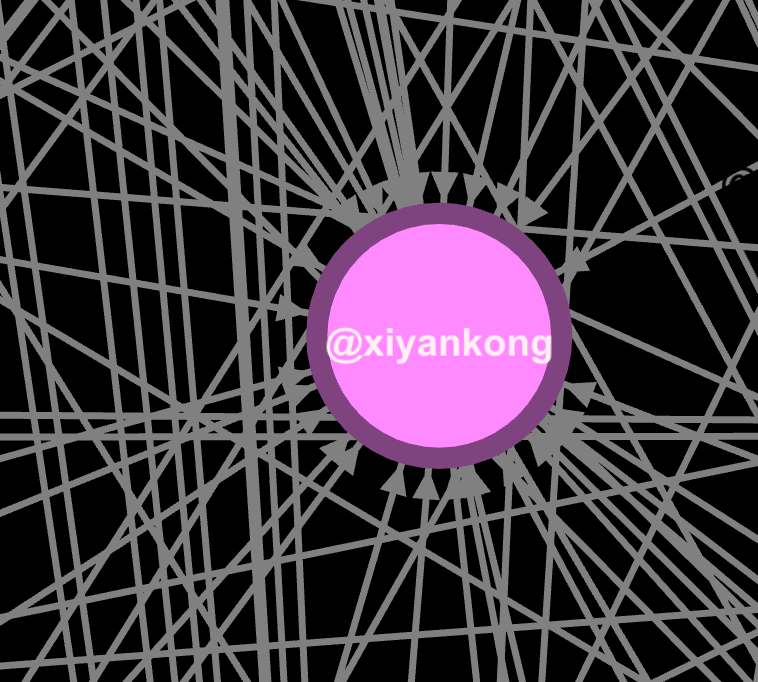
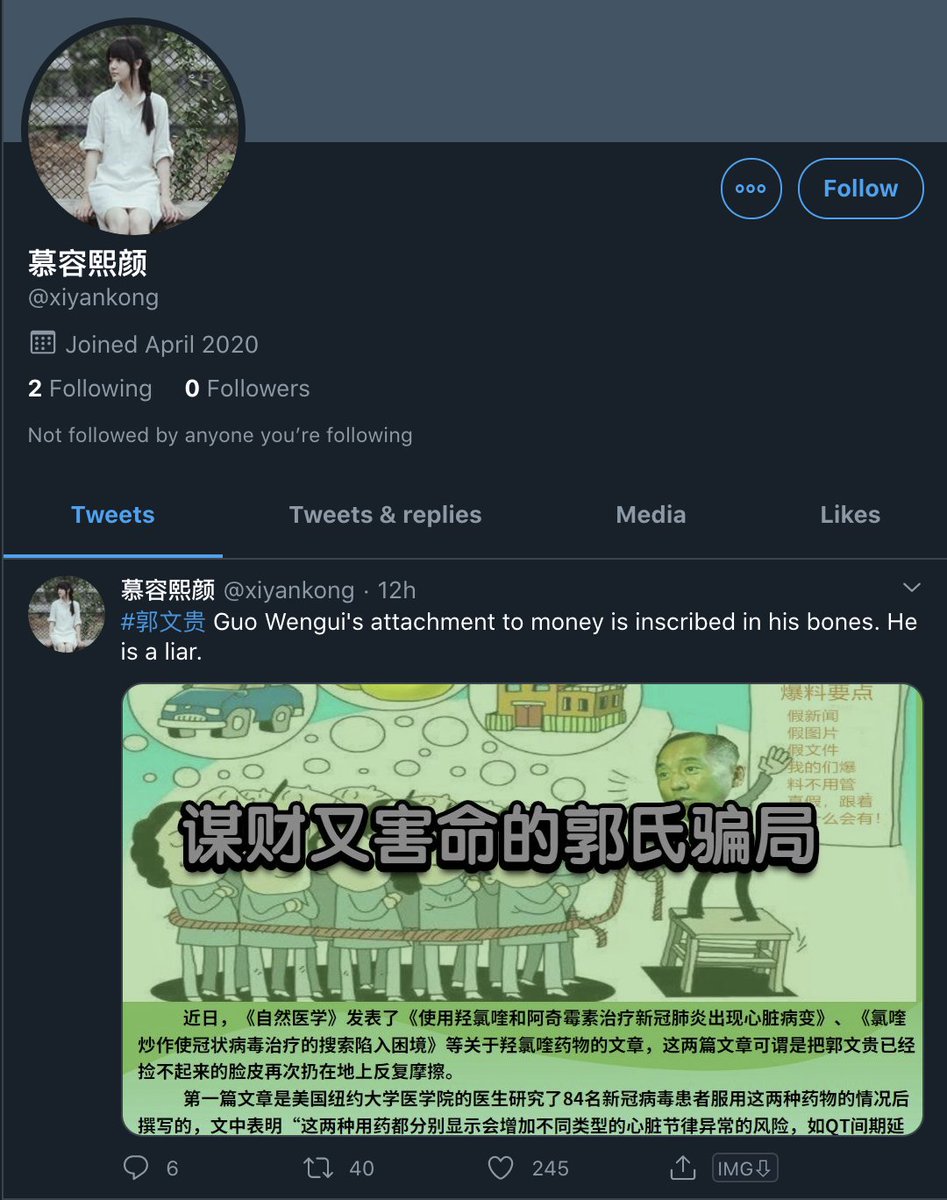
The only cool thing about this is one of them uses Batman as a profile pic.
Otherwise, it's a coordinated attempt to target certain issues. @TwitterSafety
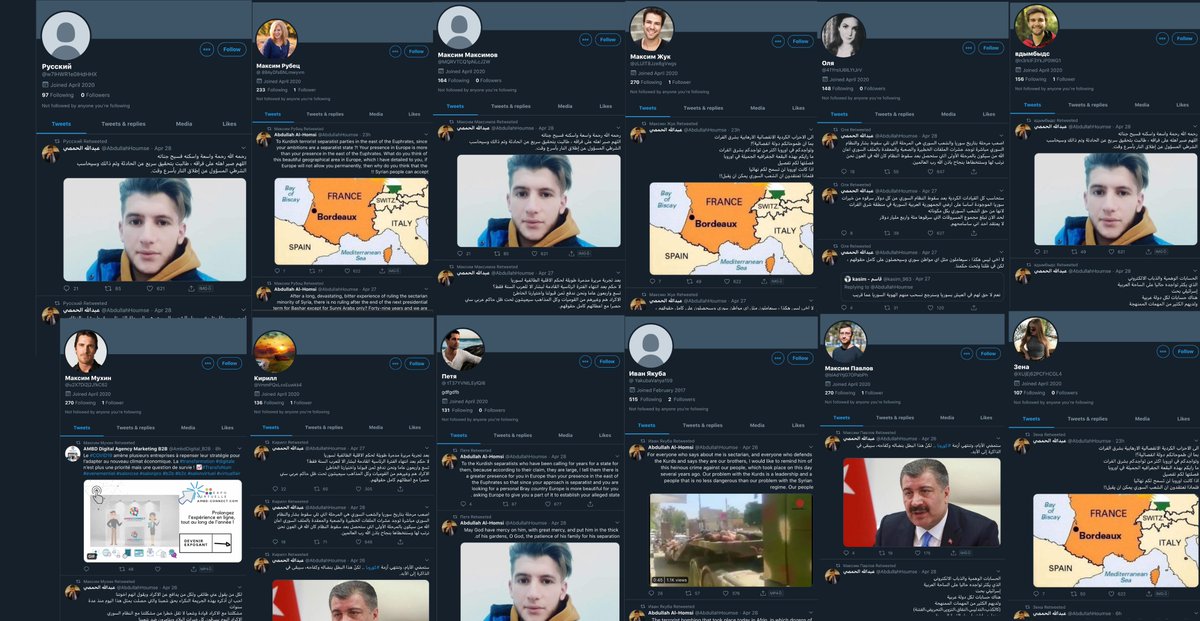
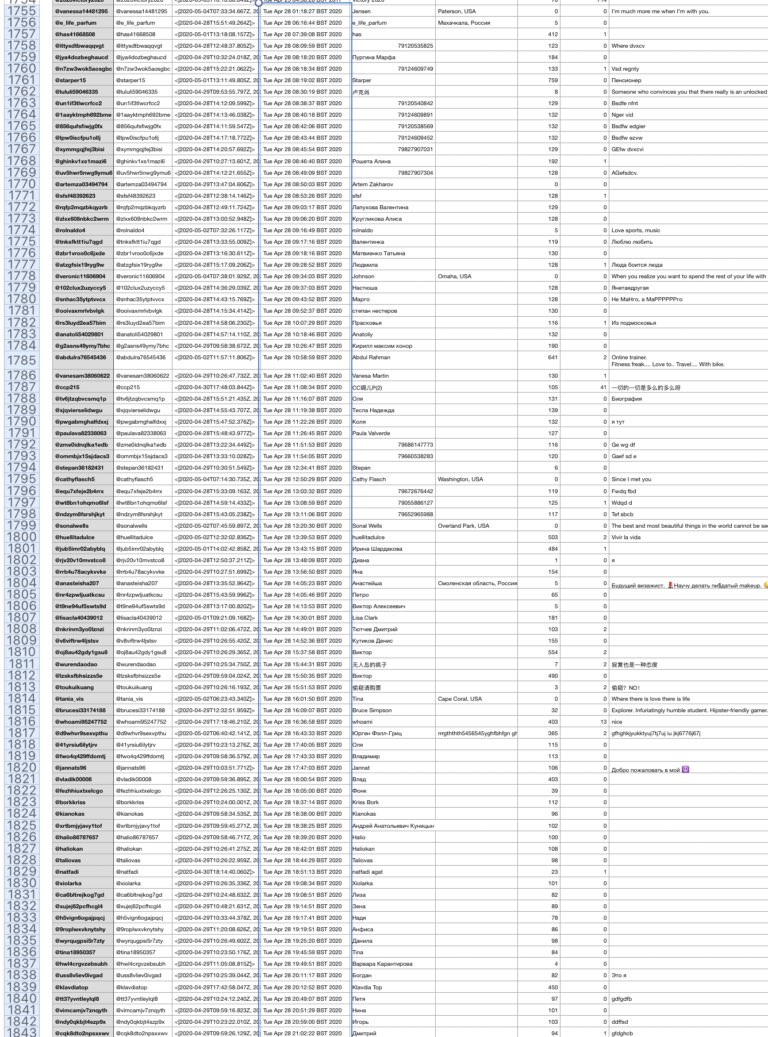
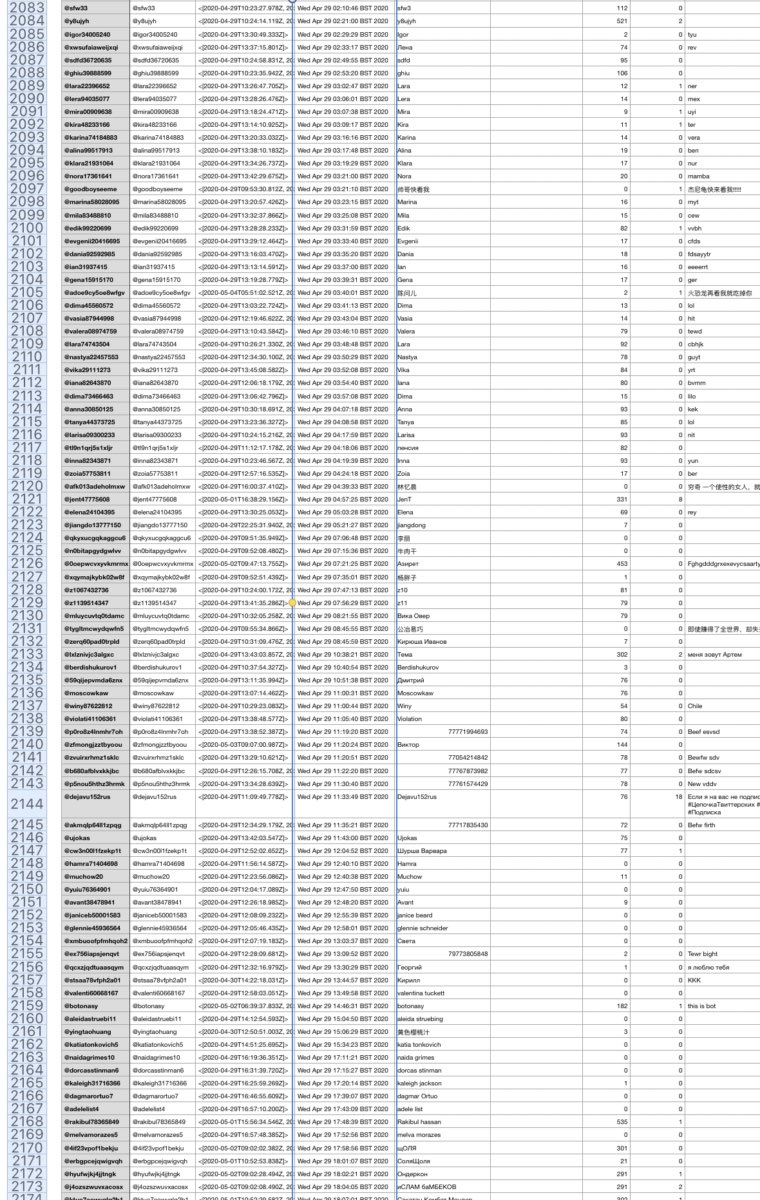
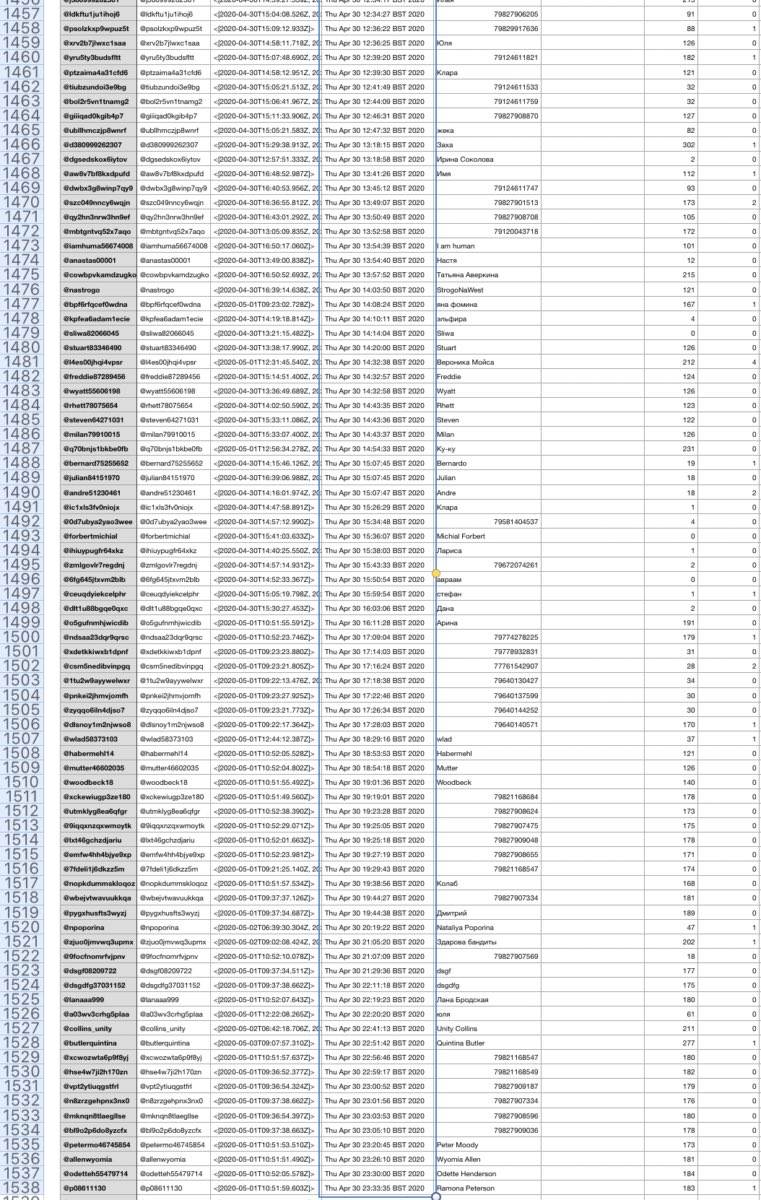
Between 1000 & 1500 today (April 30) 50+ accounts were created in network.
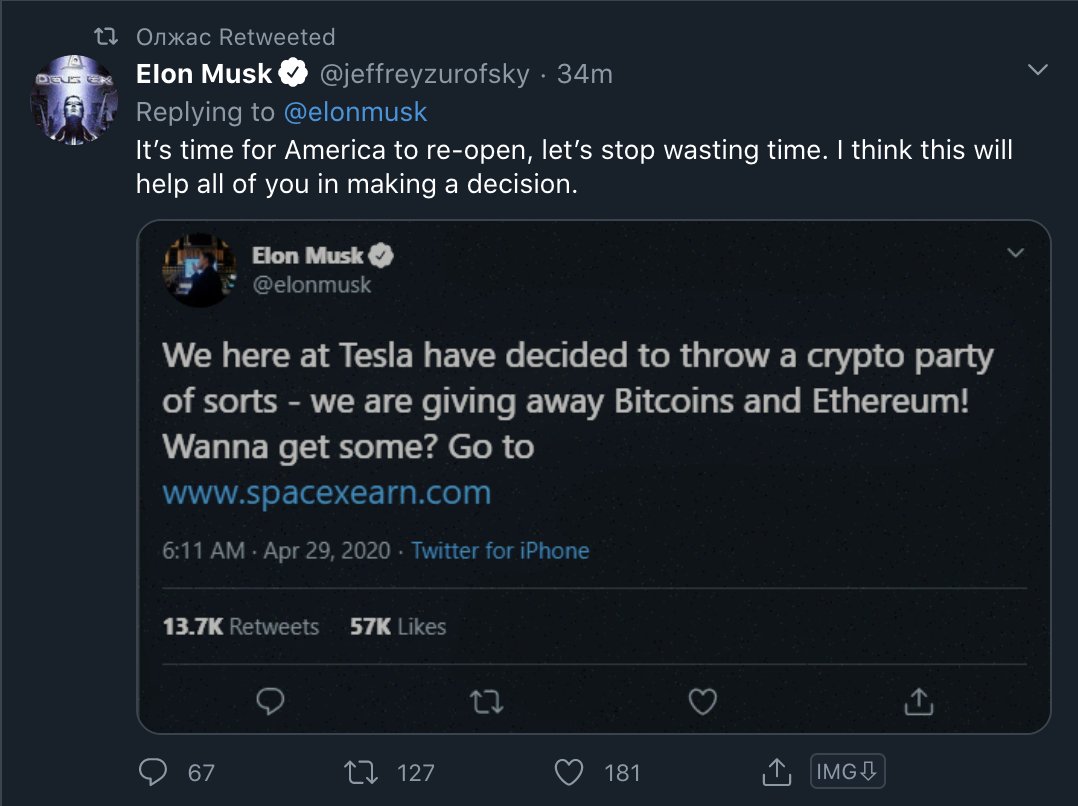
Accounts now retweet VERIFIED account pretending to be Elon Musk (@jeffreyzurofsky - likely hacked), calling for end to US to re-open
@TwitterSafety
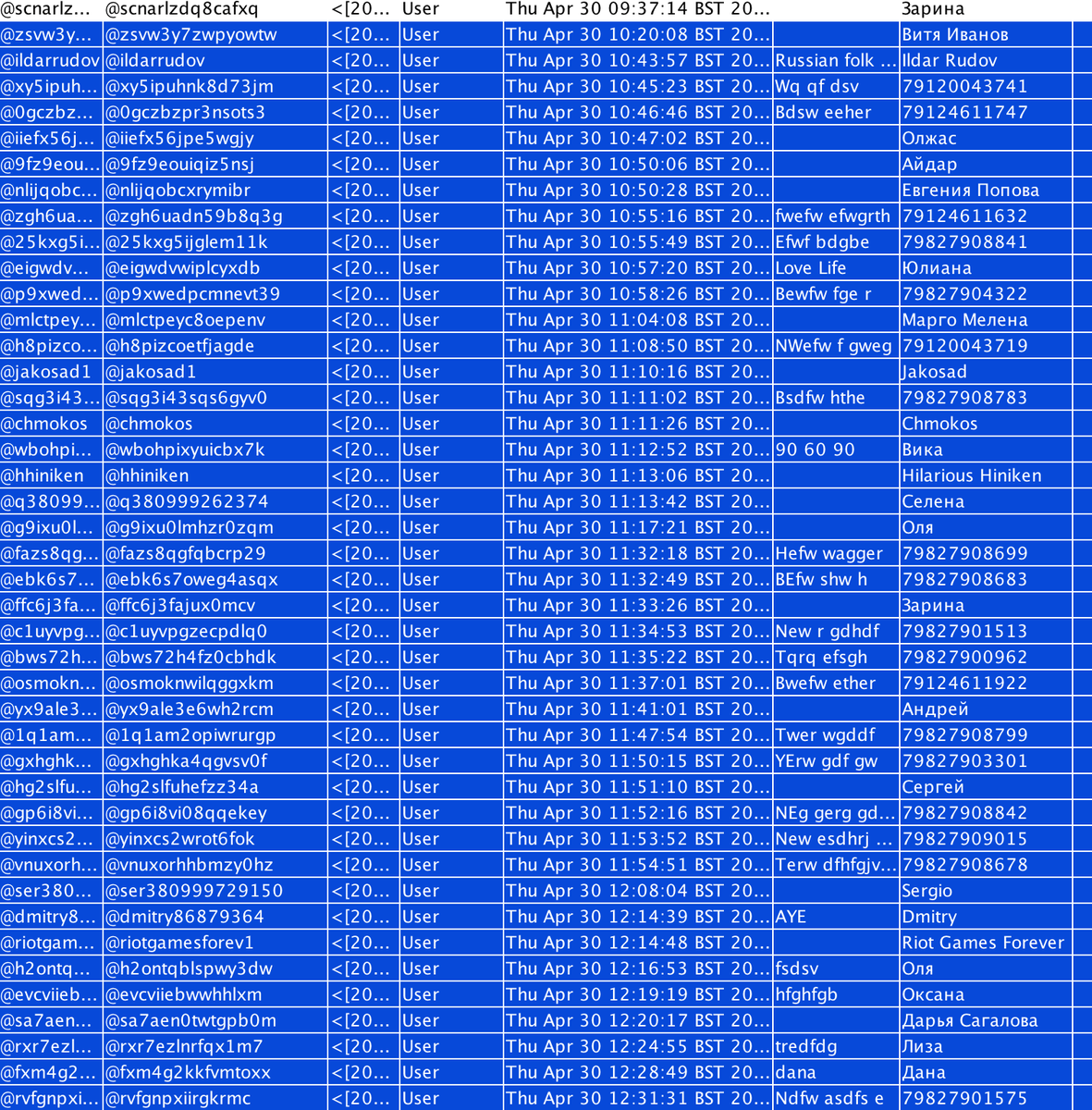
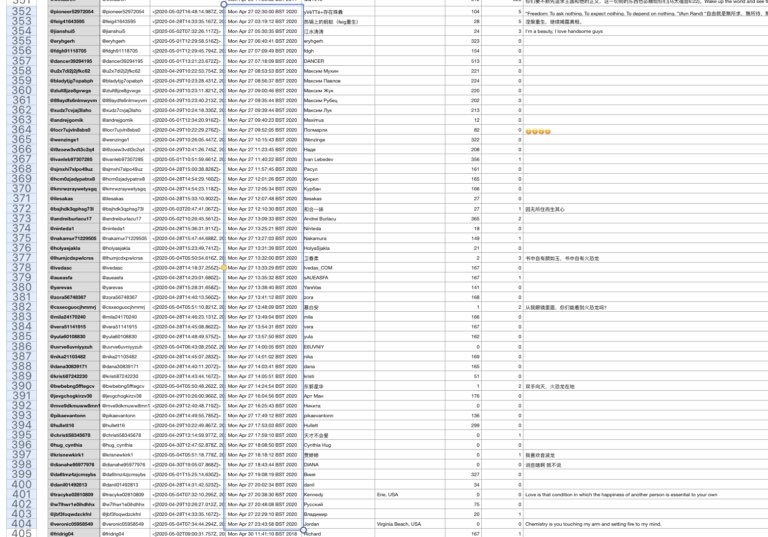
April 27, 2020: 52 accounts
April 28, 2020: 97 accounts
April 29, 2020: 109 accounts
April 30, 2020: 151 accounts
These can viewed in screenshots of the dataset I made below.
Post below is an example. I linked it to show how same amplifiers of one MilesGuo post amplified crypto content.
For a more detailed report, please refer to analysis on @bellingcat bellingcat.com/news/2020/05/0…