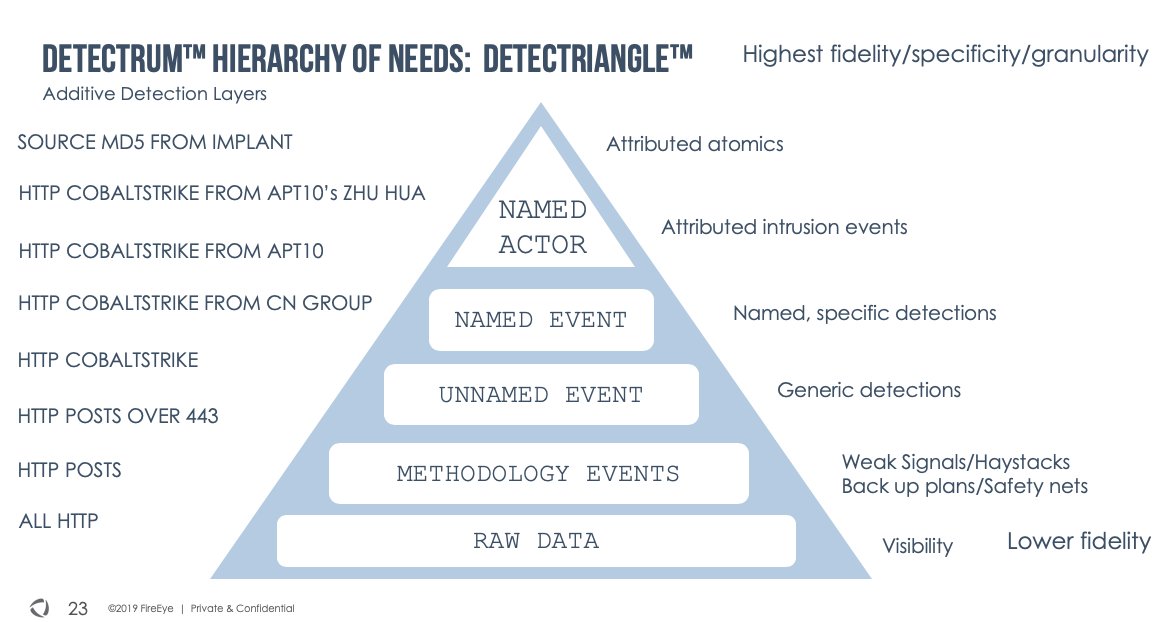
Everyone has diff vernacular for their models and ideas, but I define detection on a spectrum, where logic for the purpose of finding evil is measured by output fidelity, result set size, time/expertise requirements for review, and most importantly, “threat density.” #detectrum
The #detectrum is just a mental model for me, a way to explain the different intents and purposes for all sorts of logic and technologies and haystacks that help us find and attribute intrusion activity.
It’s not novel or special, but the detectrum can be helpful when you are examining the complex systems (people, processes, myriads of technologies) within a large intelligence apparatus.
Detection includes attribution. Attribution is a peak form of detection. Why do I think this? Before you laugh and mute me and move on, let me try to explain.
In the concept of detectrum, any given activity can be explained on a scale of specificity. Logic at its absolute widest will create massive haystacks of data relating to particular tech or TTPs. Let’s say you have logic or systems that extract host commands to help find badness.
You may have several pieces of logic for extracting host commands, but the widest one gets everything. This haystack is not threat dense and is not very specific in its designation of what is and is not in this giant haystack. This rule is on the far right of the detectrum.
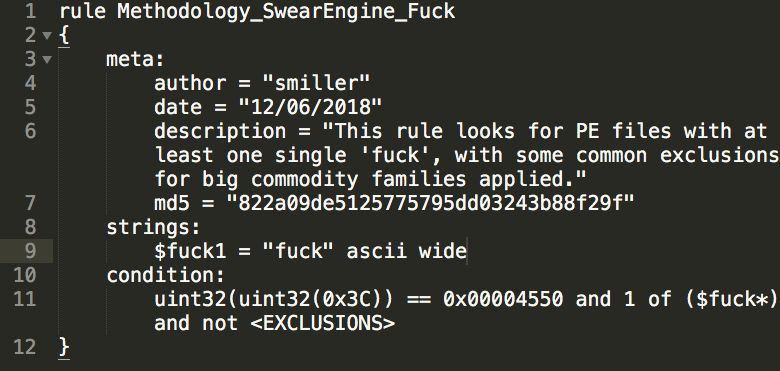
Moving left, a bit more specific, a better piece of logic looks for all host commands with arguments for PuTTY Link (PLINK) tunneling. It’s a methodology, and not always malicious. But it is a much smaller haystack and significantly threat dense.
Now even more specific, say you have another host cmd rule that looks for PLINK tunneling with a structure that is common to APT34.CATE operators. They have a particular style of how they do the flags and maybe a regex of their favorite keyboard runs for passwords.
At its most specific, a rule logic for all of the above but also has an exact password match for a tracked operator and a fqdn for a known attributed APT34 C2 server. This is a very specific, precise piece of logic that now offers *attribution* to a host event.
In my head, the detectrum shows how events or data can build up. Simple telemetry, to haystacks by TTP, to generic malicious, to specific malicious. With data from layers of logic, in grades of specificity, you can move from across the spectrum from what, onto _who_
Imagine yourself a buyer of detection. Or any analyst receiving an alert or interpreting data. Which of these events would you prefer?
1) Generic.Mal
2) APT.SIXPLUS
3) SIXPLUS (unc2157)
4) SIXPLUS (APT29, operator Pavel)
Each of these can be delivered by different rule logic.
1) Generic.Mal
2) APT.SIXPLUS
3) SIXPLUS (unc2157)
4) SIXPLUS (APT29, operator Pavel)
Each of these can be delivered by different rule logic.
These are my coffee thoughts. Back to work!
• • •
Missing some Tweet in this thread? You can try to
force a refresh