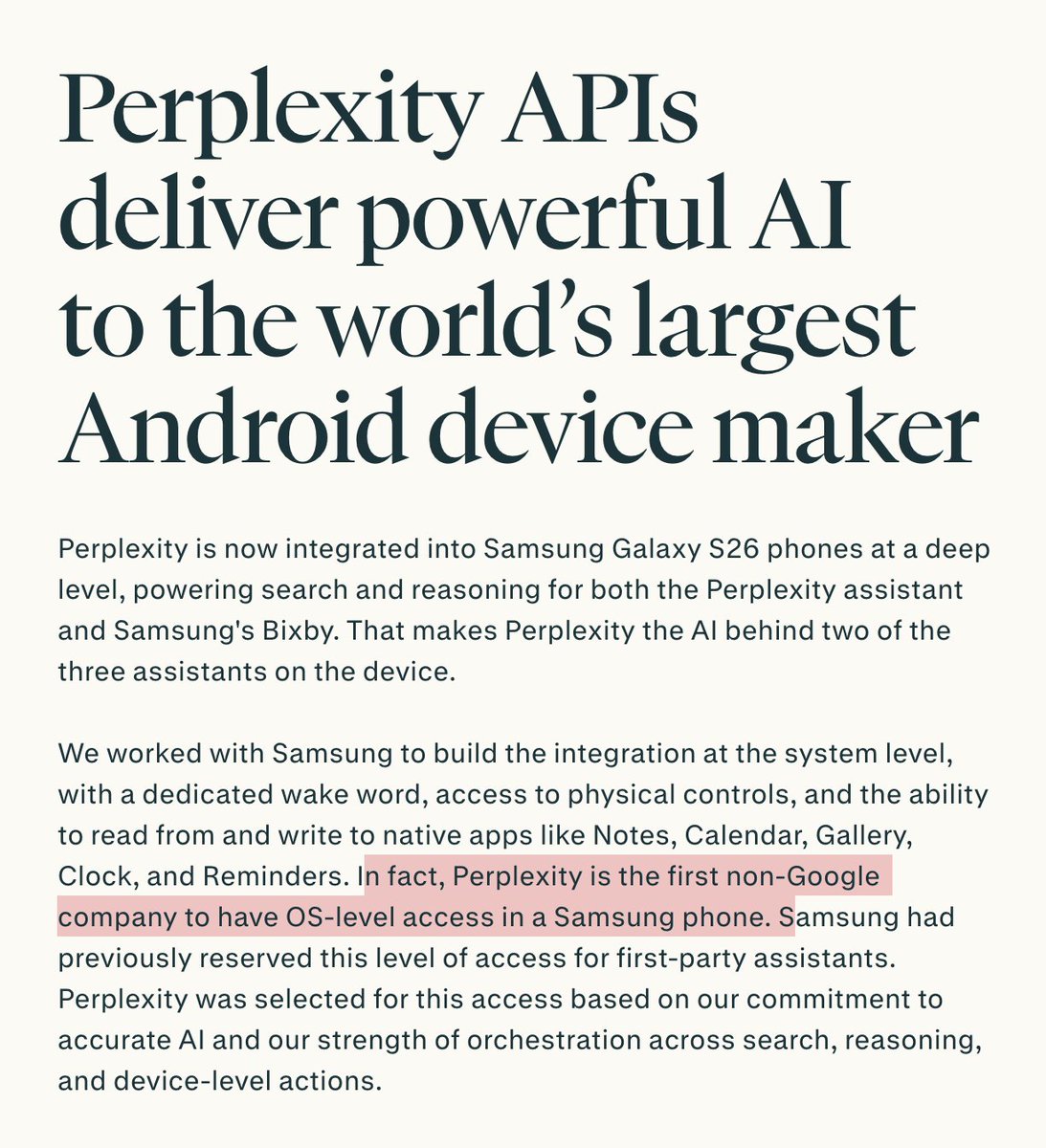
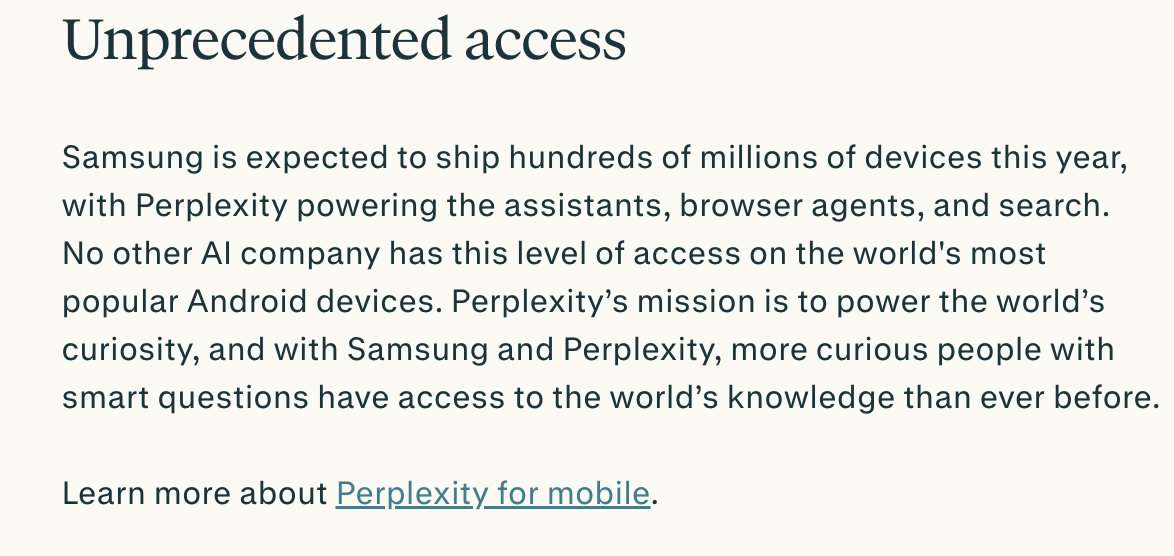
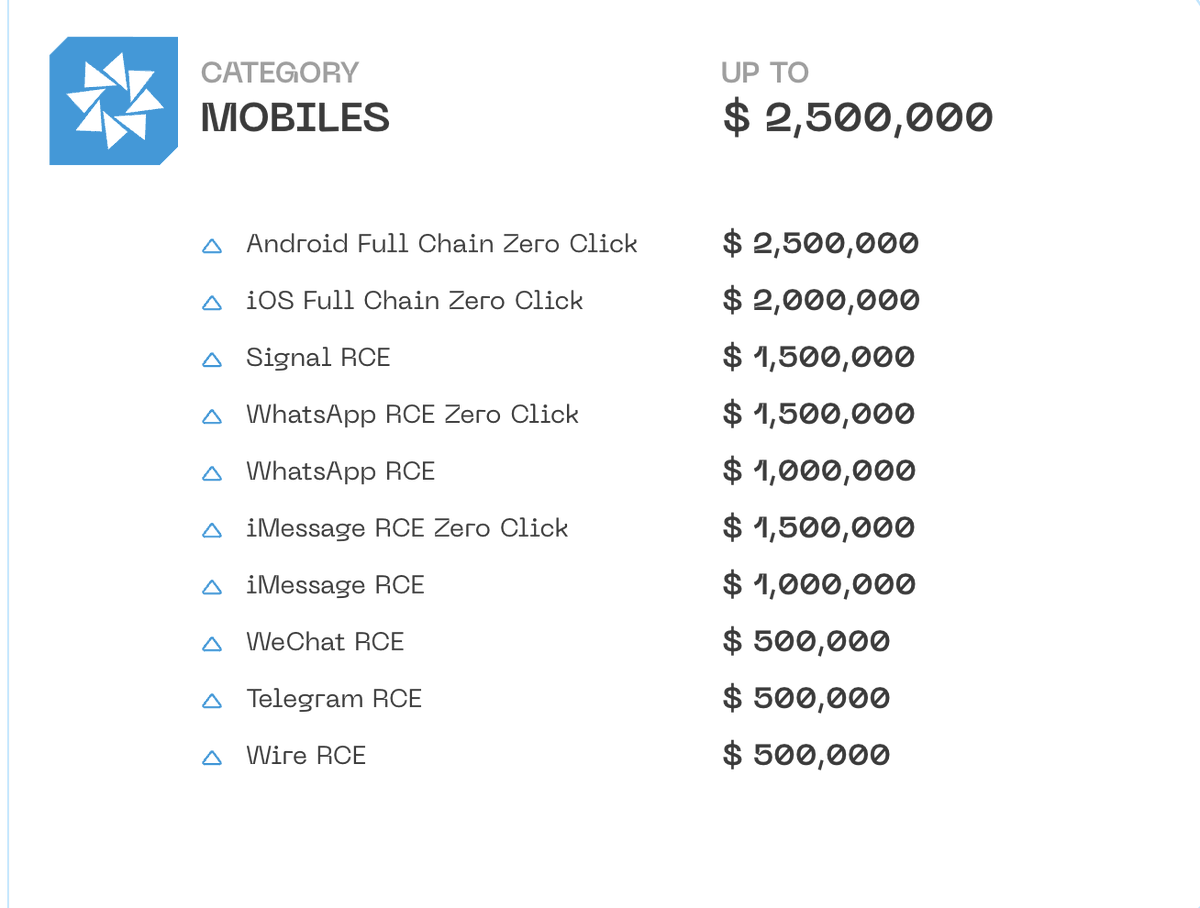
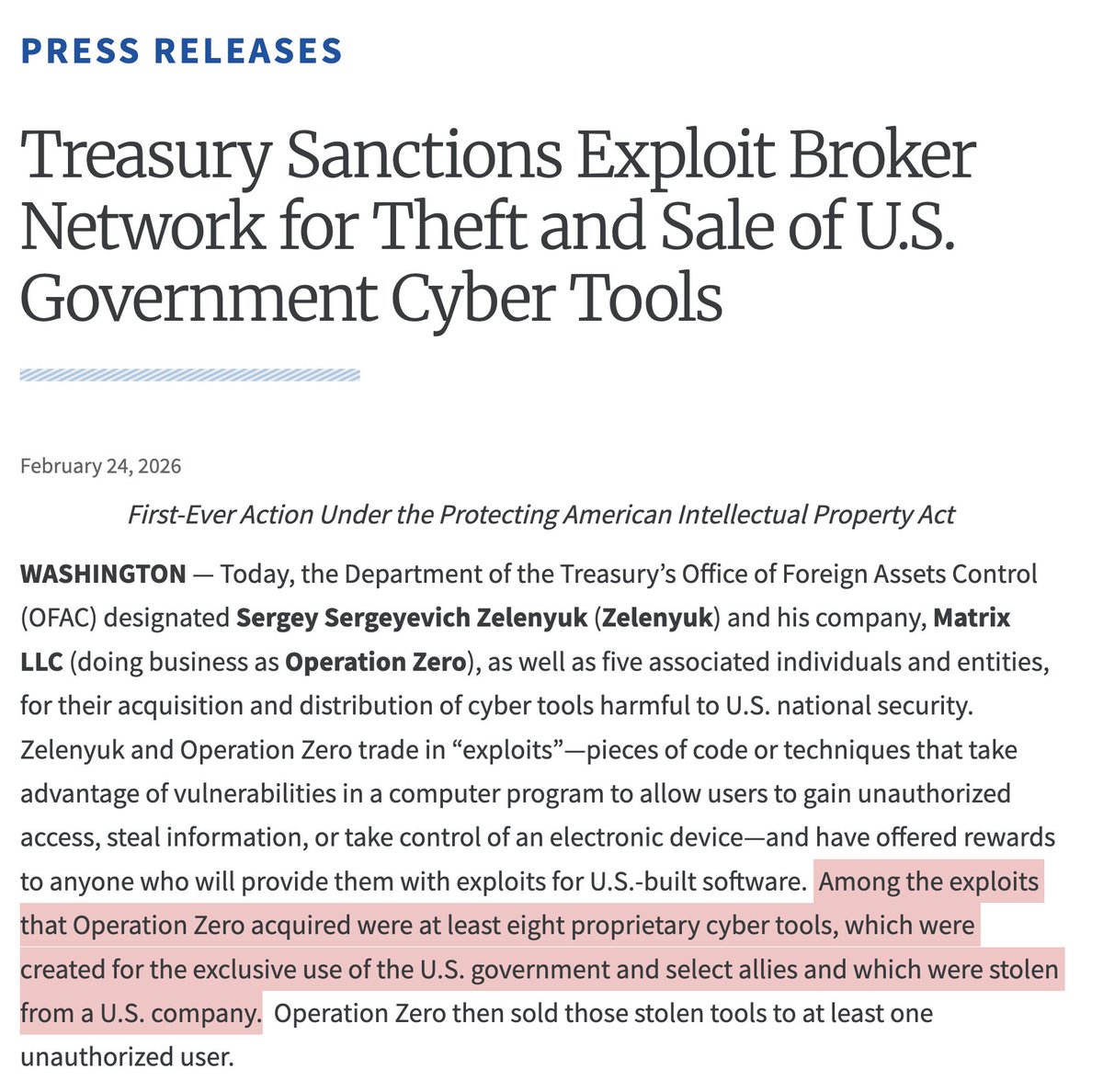
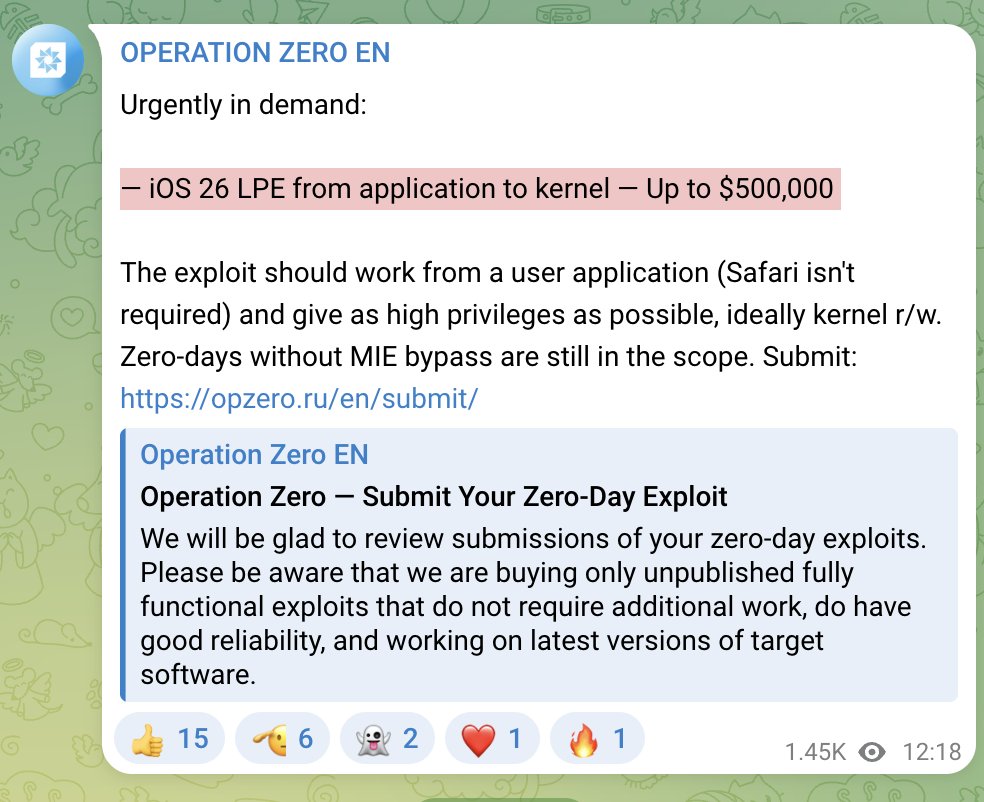
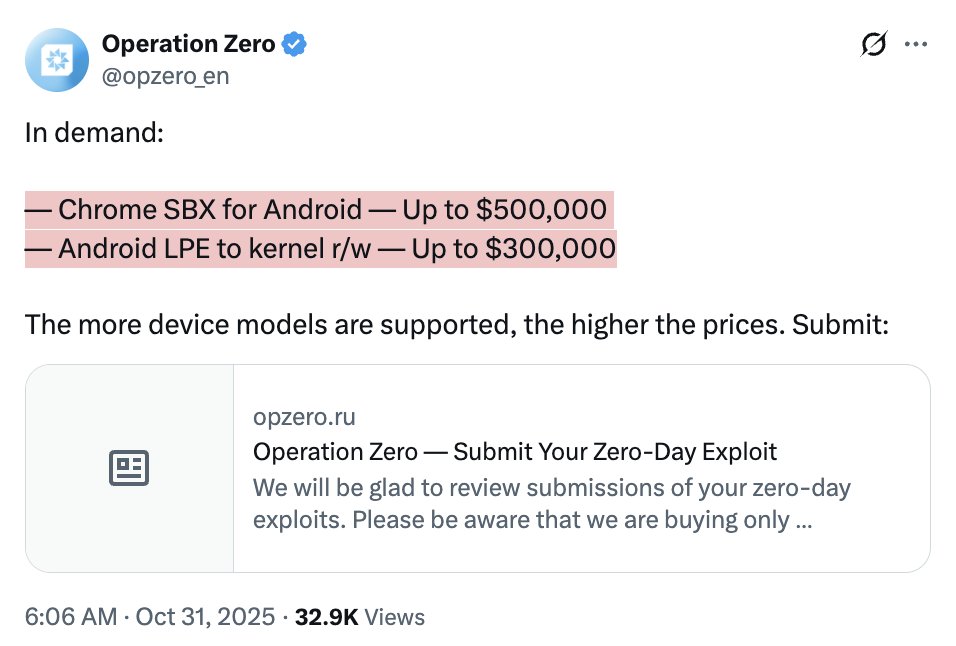
BREAKING: massive, global leak of the targets of NSO Group's Pegasus spyware. *huge deal.*
Forensic investigation by @AmnestyTech
in collaboration with @FbdnStories reporters.
We @citizenlab conducted peer review.
Here's an explainer THREAD.
washingtonpost.com/investigations…
Forensic investigation by @AmnestyTech
in collaboration with @FbdnStories reporters.
We @citizenlab conducted peer review.
Here's an explainer THREAD.
washingtonpost.com/investigations…

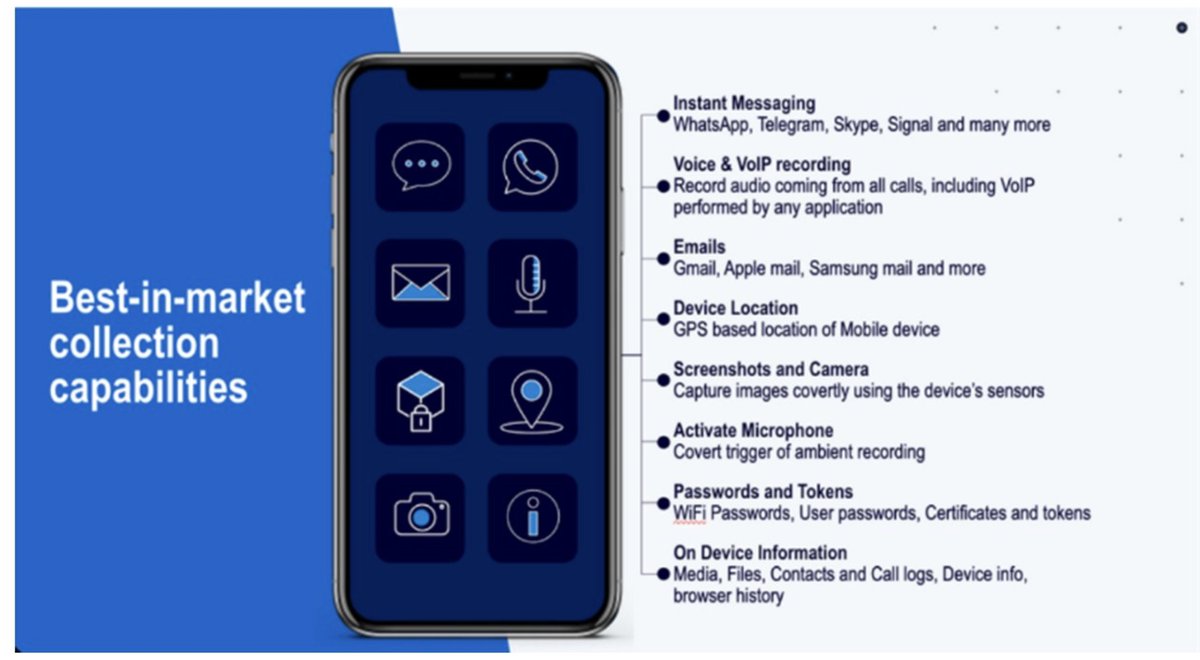
2. Background: the already-notorious NSO Group makes mercenary spyware to silently & remotely hack iPhones & Androids.
Many of their government customers are authoritarians.
Most cannot resist the temptation to target their critics, reporters, human rights groups etc.
Many of their government customers are authoritarians.
Most cannot resist the temptation to target their critics, reporters, human rights groups etc.
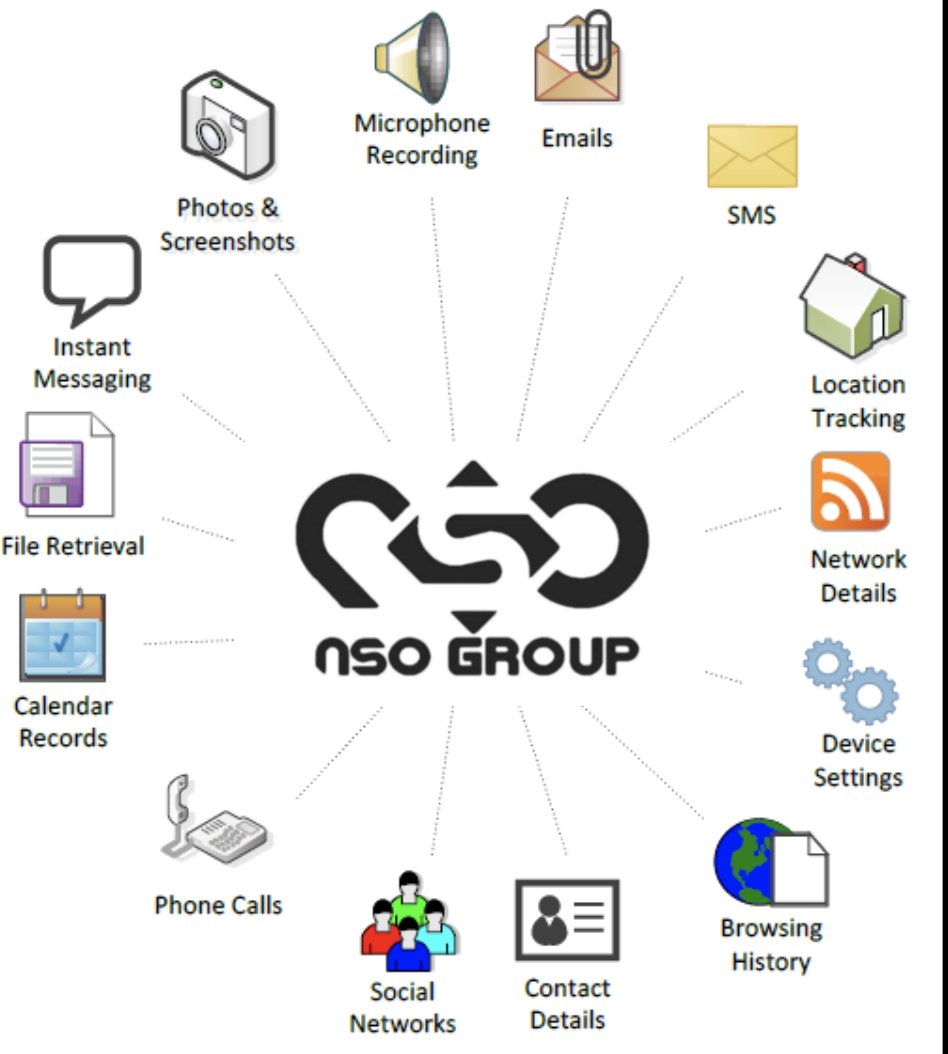
3. More about leaked numbers & targets in a sec, but first you need to know:
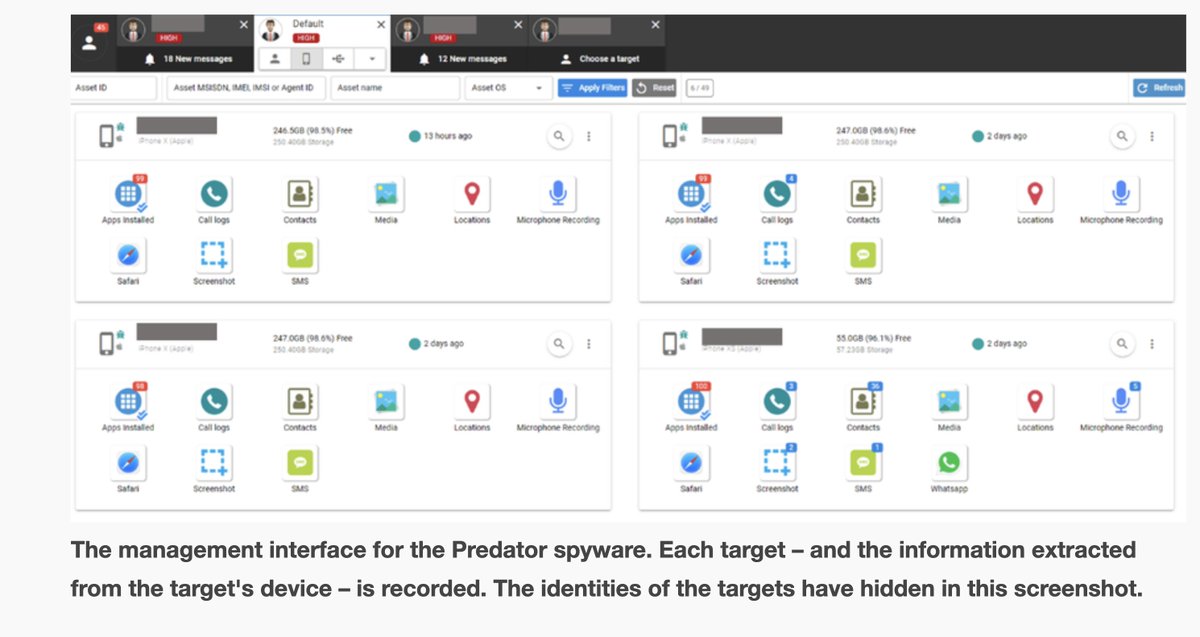
@AmnestyTech just released a report with technical analysis of NSO's infrastructure... & analysis validating w/forensics that some phones were infected with Pegasus.
amnesty.org/en/latest/rese…
@AmnestyTech just released a report with technical analysis of NSO's infrastructure... & analysis validating w/forensics that some phones were infected with Pegasus.
amnesty.org/en/latest/rese…
4. We @citizenlab independently peer reviewed @AmnestyTech's forensic methodology, including how they identify an infected phone.
Our review, led by my colleague @billmarczak, judged their forensics & research methodology to be SOUND.
citizenlab.ca/2021/07/amnest…
Our review, led by my colleague @billmarczak, judged their forensics & research methodology to be SOUND.
citizenlab.ca/2021/07/amnest…

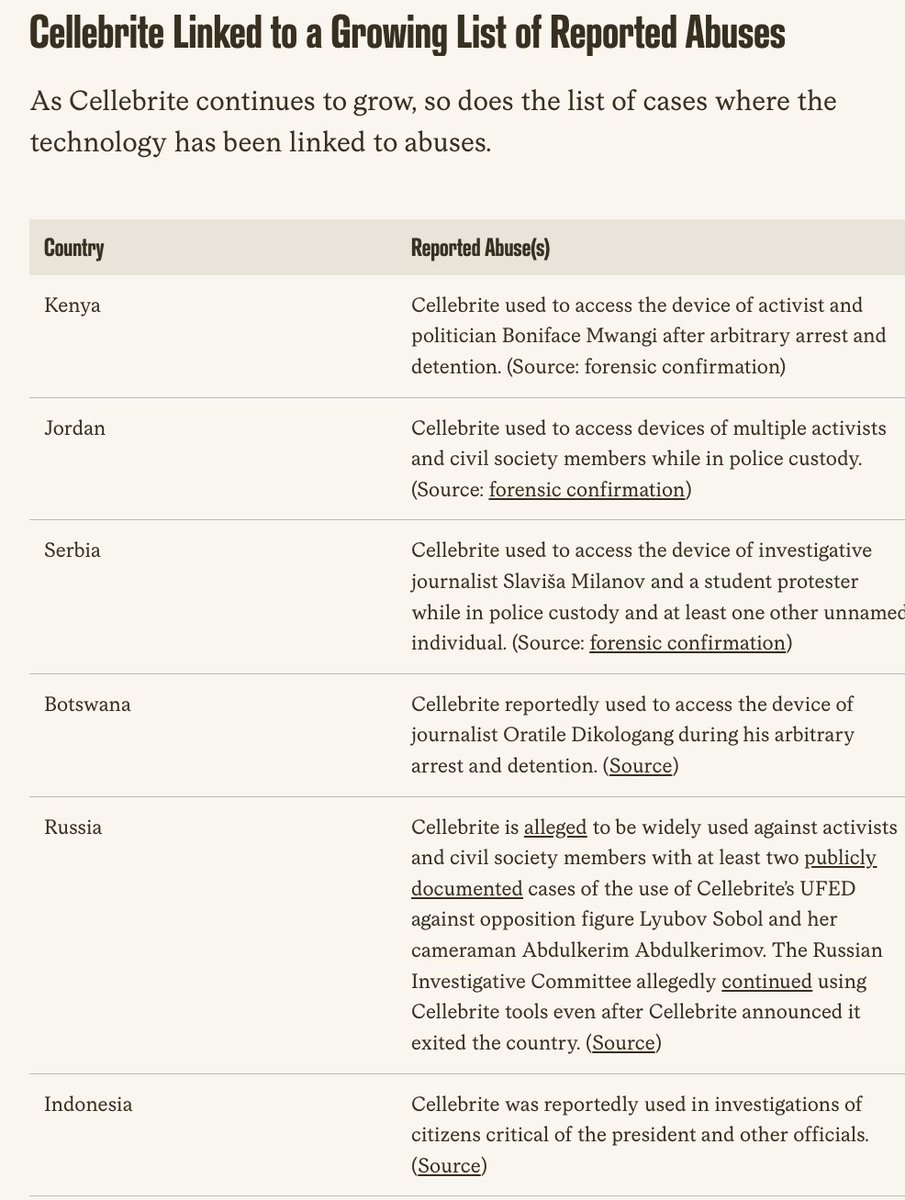
5. Now, to the findings: >50k numbers were leaked that are reportedly part of the infection & targeting workflow with Pegasus.
To help validate the relationship between these numbers & infections @AmnestyTech got consent to forensically examine a subset of the devices.
To help validate the relationship between these numbers & infections @AmnestyTech got consent to forensically examine a subset of the devices.

6. The @FbdnStories consortium worked w/the leaked phone numbers... what they found reveals 10 of NSO Group's customers insatiable intent to snoop.
And the massive scale of the operation.
- Mexico customer > 15,000
- Morocco > 10,000
- UAE > 10,00
Etc.
And the massive scale of the operation.
- Mexico customer > 15,000
- Morocco > 10,000
- UAE > 10,00
Etc.

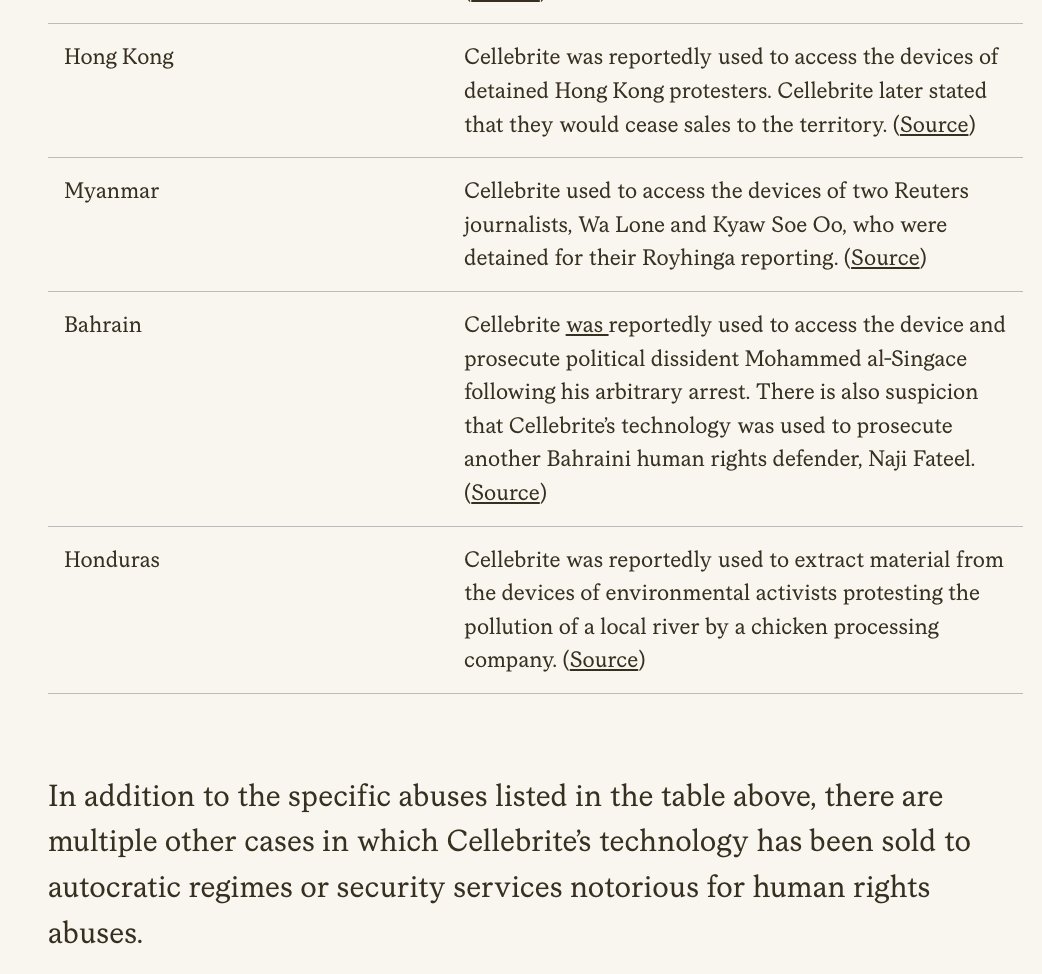
7. #SaudiArabia 🇸🇦 murdered & dismembered Jamal Khashoggi.
Jamal's wife was targeted with Pegasus spyware before the killing...
Then his fiancee was hacked multiple times just days after.
@citizenlab independently confirmed findings.
#PegasusProject
washingtonpost.com/investigations…



Jamal's wife was targeted with Pegasus spyware before the killing...
Then his fiancee was hacked multiple times just days after.
@citizenlab independently confirmed findings.
#PegasusProject
washingtonpost.com/investigations…




8. #HUNGARY 🇭🇺
Ask the government for comment... get hacked.
Hungary's far-right PM Viktor Orbán is using Pegasus spyware to surveil & attack Hungary's independent media, like @direkt36, @panyiszabolcs, and many more.
Story: @shaunwalker7 theguardian.com/news/2021/jul/…



Ask the government for comment... get hacked.
Hungary's far-right PM Viktor Orbán is using Pegasus spyware to surveil & attack Hungary's independent media, like @direkt36, @panyiszabolcs, and many more.
Story: @shaunwalker7 theguardian.com/news/2021/jul/…




9. #INDIA🇮🇳 Over 40 reporters, major opposition figures, serving ministers in the #Modi government, members of the security services and beyond are in the list.
Story to watch as the scandal unfolds there.
Story @svaradarajan @thewire_in
thewire.in/government/pro…
Story to watch as the scandal unfolds there.
Story @svaradarajan @thewire_in
thewire.in/government/pro…

10. HUNDREDS of journalists around the globe are on the #PegasusProject list.
NSO Group's role in fueling the authoritarian assault on democratic values (like a free press) is coming into sharp focus
theguardian.com/world/2021/jul…



NSO Group's role in fueling the authoritarian assault on democratic values (like a free press) is coming into sharp focus
theguardian.com/world/2021/jul…




11. NSO Group puts up a facade of caring about human rights, doing due diligence, etc.
This leak exposes the farce of that performance.
When your customers are dictators... they will do bad things. NSO knows this. We know it.
Now everybody knows it.
This leak exposes the farce of that performance.
When your customers are dictators... they will do bad things. NSO knows this. We know it.
Now everybody knows it.

12. Continuing with cases.... in #FRANCE 🇫🇷
#PegasusProject list includes @edwyplenel, founder of independent news site @Mediapart, a reporter from @lemondefr, etc..
Story lemonde.fr/projet-pegasus…
#PegasusProject list includes @edwyplenel, founder of independent news site @Mediapart, a reporter from @lemondefr, etc..
Story lemonde.fr/projet-pegasus…

13. in #Mexico 🇲🇽 Journalist Cecilio Pineda Birto was getting death threats for reporting on official collusion with a cartel capo...
...then his number showed up on the #PegasusProject list.
Then he was assassinated.
theguardian.com/news/2021/jul/…



...then his number showed up on the #PegasusProject list.
Then he was assassinated.
theguardian.com/news/2021/jul/…




14. Bookmark this thread. Things are only getting started.
I'll be updating it with more cases & context as #PegasusProject revelations keep dropping.
I'll be updating it with more cases & context as #PegasusProject revelations keep dropping.
15. REASON TO CARE #1
So, you didn't know today's #PegasusProject hacking victims personally.
But tomorrow? Who knows. You don't.
#NSOGROUP is aggressively pitching *local* cops, including in USA 🇺🇸
Pause. Think about the oversight at your local PD.
vice.com/en/article/889…



So, you didn't know today's #PegasusProject hacking victims personally.
But tomorrow? Who knows. You don't.
#NSOGROUP is aggressively pitching *local* cops, including in USA 🇺🇸
Pause. Think about the oversight at your local PD.
vice.com/en/article/889…




16. REASON TO CARE #2:
Since all phones are vulnerable, #Pegasus spyware lets its autocrat-users *export fear*
They want want *you* to be afraid to criticize them.
Yes, you. A continent away. In a democracy.
Think about the implications.
Since all phones are vulnerable, #Pegasus spyware lets its autocrat-users *export fear*
They want want *you* to be afraid to criticize them.
Yes, you. A continent away. In a democracy.
Think about the implications.
7. REASON TO CARE #3:
Think only human rights defenders & journalists get hacked with #Pegasus?
Wrong.
Good chance officials responsible for the national security of YOUR country have been / will be targeted.
Example pic: 2019 #NSOGroup WhatsApp hack.
reuters.com/article/us-fac…
Think only human rights defenders & journalists get hacked with #Pegasus?
Wrong.
Good chance officials responsible for the national security of YOUR country have been / will be targeted.
Example pic: 2019 #NSOGroup WhatsApp hack.
reuters.com/article/us-fac…

18. Know who else is saying #NSOGroup must be stopped?
Big tech.
These days they are hitting back hard against the mercenary spyware industry for hacking their products & users.
E.g. this thread by @wcathcart @WhatsApp's CEO.👇
Big tech.
These days they are hitting back hard against the mercenary spyware industry for hacking their products & users.
E.g. this thread by @wcathcart @WhatsApp's CEO.👇
https://twitter.com/wcathcart/status/1416794901438554112
19. #INDIA🇮🇳 (2/)
She accused the Chief Justice of India’s Supreme Court of sexual harassment.
Just days later:
Her phone. Her husband's phone. Their family members..
11 in total then showed up on the #PegasusProject list.
thewire.in/rights/ranjan-…


She accused the Chief Justice of India’s Supreme Court of sexual harassment.
Just days later:
Her phone. Her husband's phone. Their family members..
11 in total then showed up on the #PegasusProject list.
thewire.in/rights/ranjan-…



20. #FRANCE 🇫🇷 Claude Mangin is campaigning for the release of her husband, a political activist, from a #moroccan prison.
She's in France.
Last month her iPhone 11 was silently hacked w/#Pegasus spyware. A second iPhone she borrowed? Also infected.
washingtonpost.com/technology/202…


She's in France.
Last month her iPhone 11 was silently hacked w/#Pegasus spyware. A second iPhone she borrowed? Also infected.
washingtonpost.com/technology/202…



21. BREAKING: Americans 🇺🇸 including US. Gov. officials are on the #PegasusProject list...
...even the #Biden administration's lead Iran negotiator Robert Malley!
#NSOGroup is an urgent national security problem for the United States.
washingtonpost.com//national-secu…
...even the #Biden administration's lead Iran negotiator Robert Malley!
#NSOGroup is an urgent national security problem for the United States.
washingtonpost.com//national-secu…

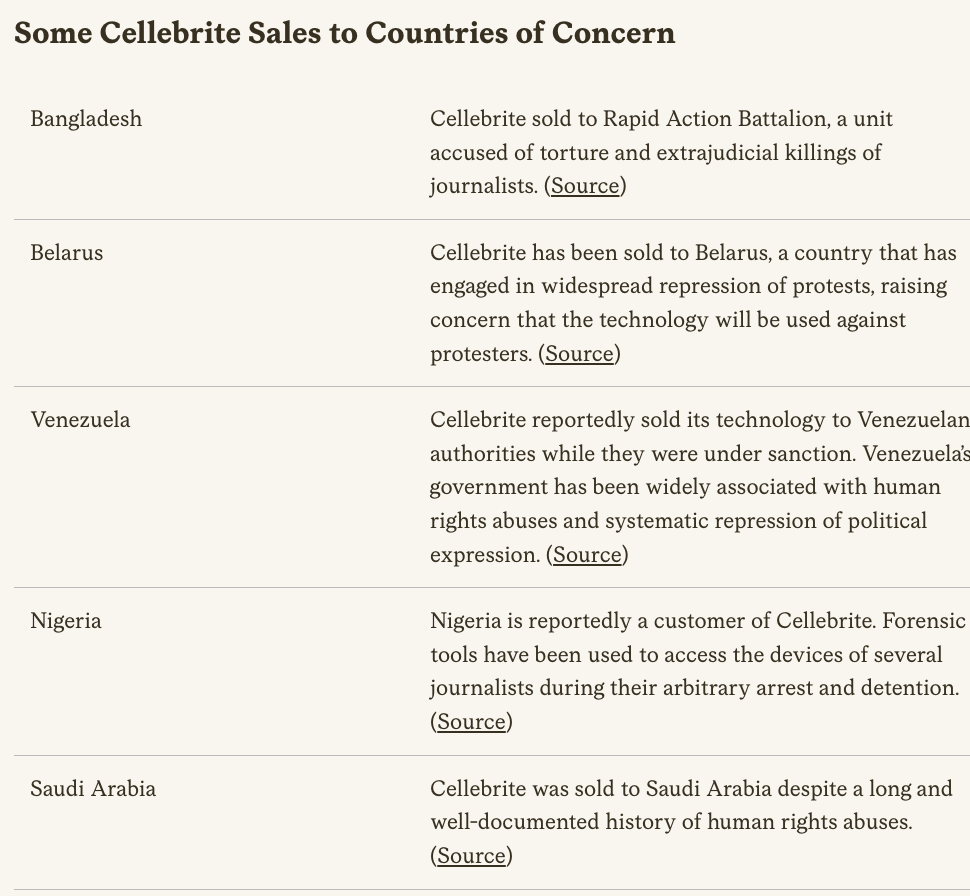
22. #MEXICO 🇲🇽: At least *50 people* close to the president ... are on the #PegasusProject spyware list.
They were put there while he was campaigning.
-His wife
-Family members, drivers, doctor
-Aides, chief of staff
-Doctor...
#PegasusProject
Story theguardian.com/news/2021/jul/…

They were put there while he was campaigning.
-His wife
-Family members, drivers, doctor
-Aides, chief of staff
-Doctor...
#PegasusProject
Story theguardian.com/news/2021/jul/…


23. Paul Rusesabagina inspired Hotel #Rwanda 🇷🇼
He's become a critic of the gov., and was recently thrown in jail.
His American 🇺🇸 daughter, while advocating for his release, has been incessantly surveilled w/ #Pegasus.
#PegasusProject
By @skirchy theguardian.com/news/2021/jul/…


He's become a critic of the gov., and was recently thrown in jail.
His American 🇺🇸 daughter, while advocating for his release, has been incessantly surveilled w/ #Pegasus.
#PegasusProject
By @skirchy theguardian.com/news/2021/jul/…



24. Policies to stop the global spyware catastrophe?
Experts @davidakaye & @MarietjeSchaake say:
- Immediate moratorium on sale & transfer
-Rule-of-law requirements on users
-Victims must be able to sue
-Global principles of conduct
#PegasusProject
washingtonpost.com/opinions/2021/…



Experts @davidakaye & @MarietjeSchaake say:
- Immediate moratorium on sale & transfer
-Rule-of-law requirements on users
-Victims must be able to sue
-Global principles of conduct
#PegasusProject
washingtonpost.com/opinions/2021/…




25. #INDIA 🇮🇳 (3/) Rahul Gandhi was Prime Minister #Modi's main opponent in the 2019 nat'l elections.
During the campaign, 2 of his phones were put on the #PegasusProject list, and 5 of his friends & fellow Congress party officials.
theguardian.com/news/2021/jul/…
During the campaign, 2 of his phones were put on the #PegasusProject list, and 5 of his friends & fellow Congress party officials.
theguardian.com/news/2021/jul/…

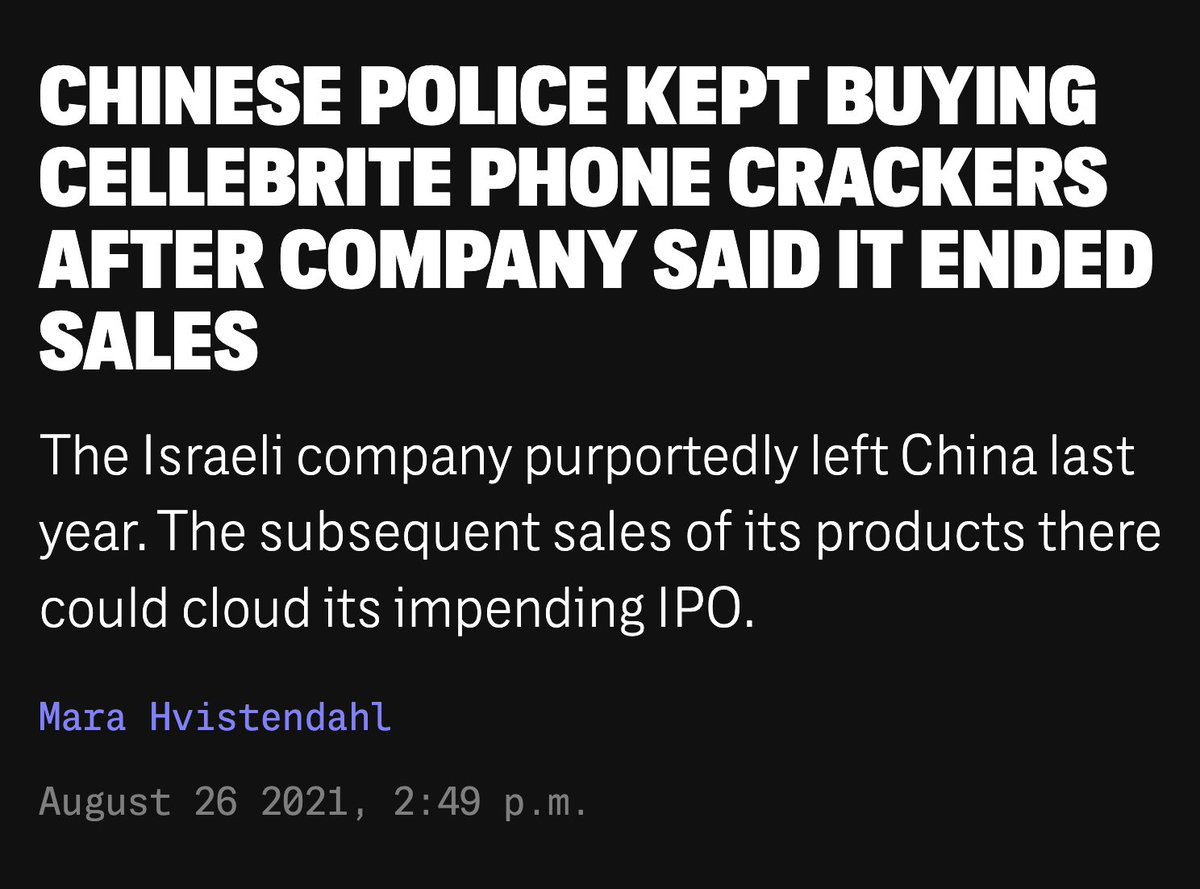
26. #NSOGroup & #Pegasus spyware customers are issuing panicky, fairy-tale denials.
Here's my take.
#PegasusProject
Here's my take.
#PegasusProject
27. BREAKING: 10 prime ministers, 3 presidents & a king on the #PegasusProject spyware list.
Included, French president @EmmanuelMacron
🇫🇷
Crystal clear: #NSOGroup is a global national security threat.
Story: washingtonpost.com/world/2021/07/…
Included, French president @EmmanuelMacron
🇫🇷
Crystal clear: #NSOGroup is a global national security threat.
Story: washingtonpost.com/world/2021/07/…

28. #NSOGroup, after courting a lot of press, is suddenly not interested in talking....
So begins the hope-this-dies-down phase of crisis management?
#PegasusProject
So begins the hope-this-dies-down phase of crisis management?
#PegasusProject
https://twitter.com/kifleswing/status/1417857420425007107
29. NEW "there's gotta be some accountability for spies-for-hire"
Senator @RonWyden to Senate Intelligence Committee yesterday in light of #PegasusProject revelations about #NSOGroup spyware.
Full:
Senator @RonWyden to Senate Intelligence Committee yesterday in light of #PegasusProject revelations about #NSOGroup spyware.
Full:
30. NEW: 1st legal complaint from #Pegasus victims over latest spyware revelations has landed in France 🇫🇷
Brought by 2 journalists, supported by press freedom org @RSF_inter
Their statement says more complaints inbound.
#PegasusProject
rsf.org/en/news/after-…


Brought by 2 journalists, supported by press freedom org @RSF_inter
Their statement says more complaints inbound.
#PegasusProject
rsf.org/en/news/after-…


31. NEW: Dalai Lama's inner circle on the #PegasusProject list. (He's not thought to carry a phone)
Happened in period before & after a private meeting with @BarackObama.
#India🇮🇳 suspected as #NSOGroup #spyware client responsible.
Report: theguardian.com/news/2021/jul/…



Happened in period before & after a private meeting with @BarackObama.
#India🇮🇳 suspected as #NSOGroup #spyware client responsible.
Report: theguardian.com/news/2021/jul/…




32. NEW: While #NSOGroup is trying to distract you with a counter narrative...
Here are #Indian 🇮🇳 Police barging into the offices of one of the #PegasusProject media outlets. 👇
Here are #Indian 🇮🇳 Police barging into the offices of one of the #PegasusProject media outlets. 👇
https://twitter.com/svaradarajan/status/1418513671764865024
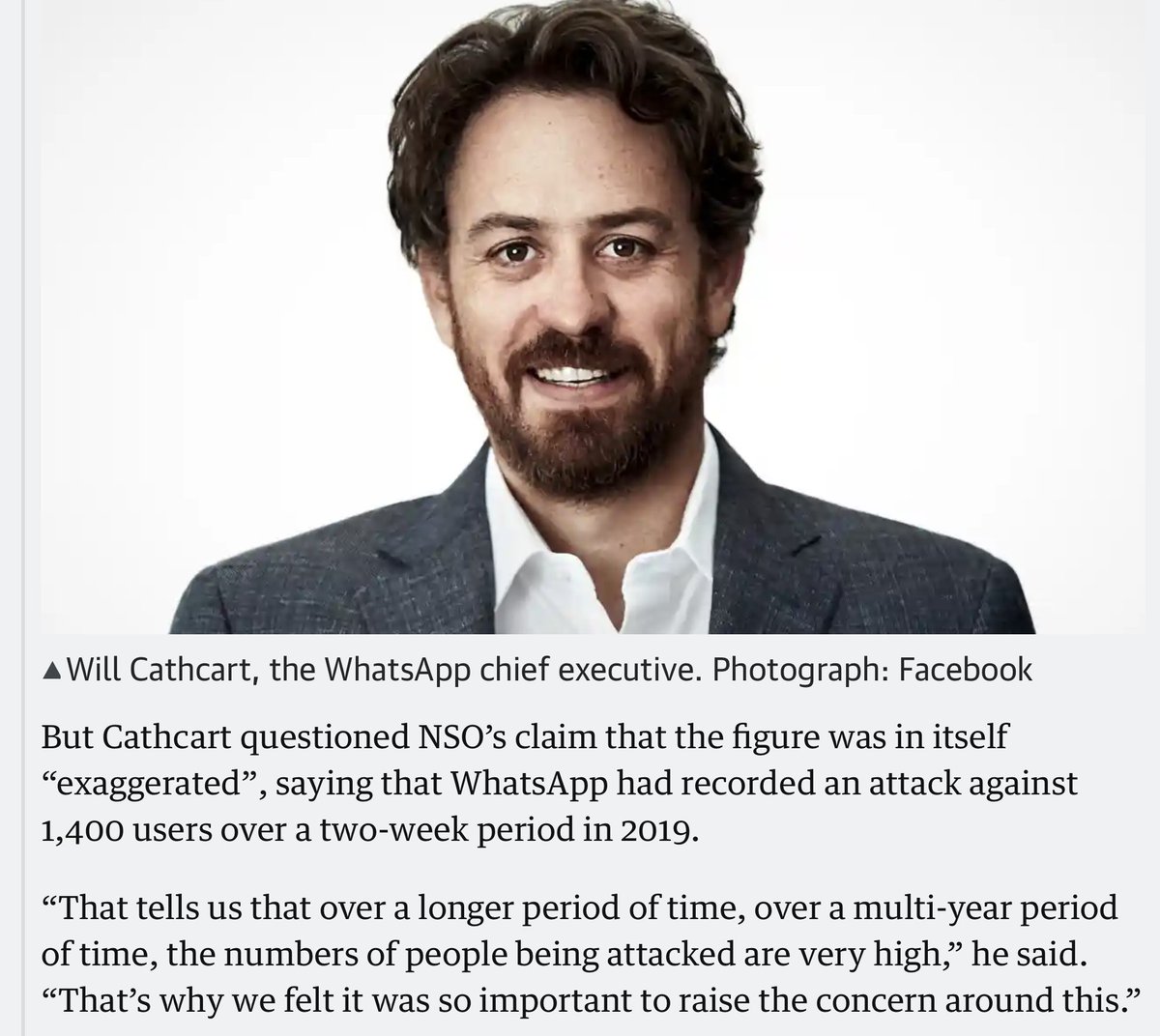
35. TODAY: @WhatsApp CEO @wcathcart rubbishes #NSOGroup's denials:
- #PegasusProject reporting consistent w/targeting in #NSOGroup's 2019 attack on WhatsApp users.
- Points out: in *only* 2 weeks 1.4k numbers were confirmed targeted in 2019. Do the math.
theguardian.com/technology/202…

- #PegasusProject reporting consistent w/targeting in #NSOGroup's 2019 attack on WhatsApp users.
- Points out: in *only* 2 weeks 1.4k numbers were confirmed targeted in 2019. Do the math.
theguardian.com/technology/202…

36. BIG DEAL: today @WhatsApp CEO @wcathcart *publicly confirmed* that senior national security officials of US allies🇺🇸 were targeted with #Pegasus spyware in 2019.
Clear message: #NSOGroup spyware is a national security threat.
By @skirchy theguardian.com/technology/202…
Clear message: #NSOGroup spyware is a national security threat.
By @skirchy theguardian.com/technology/202…

37. Taking #NSOGroup's denials at face value?
CEO: "you won't reach 50,000 #Pegasus targets since the company was founded"
FACT: there were >1,400 *confirmed* targets in just 2 weeks in 2019 per @WhatsApp.
At this rate NSO would have easily reached 50k+
calcalistech.com/ctech/articles…
CEO: "you won't reach 50,000 #Pegasus targets since the company was founded"
FACT: there were >1,400 *confirmed* targets in just 2 weeks in 2019 per @WhatsApp.
At this rate NSO would have easily reached 50k+
calcalistech.com/ctech/articles…

38. Not familiar with the 2019 #NSOGroup attack on @WhatsApp?
#Pegasus spyware was used to target people via WhatsApp in 2019. WhatsApp spotted it, quickly shut it down, notified all targets...and then *sued* NSO.
We @citizenlab helped investigate.
washingtonpost.com/opinions/2019/…
#Pegasus spyware was used to target people via WhatsApp in 2019. WhatsApp spotted it, quickly shut it down, notified all targets...and then *sued* NSO.
We @citizenlab helped investigate.
washingtonpost.com/opinions/2019/…
39. "A.Q. Khans of the cyber world"
🇺🇸 US lawmakers just came out swinging against mercenary hacking company #NSOGroup.
Statement: US Gov must impose consequences in light of latest revelations of spyware misuse.
Reps @Malinowski @RepKatiePorter @JoaquinCastrotx @RepAnnaEshoo


🇺🇸 US lawmakers just came out swinging against mercenary hacking company #NSOGroup.
Statement: US Gov must impose consequences in light of latest revelations of spyware misuse.
Reps @Malinowski @RepKatiePorter @JoaquinCastrotx @RepAnnaEshoo



• • •
Missing some Tweet in this thread? You can try to
force a refresh