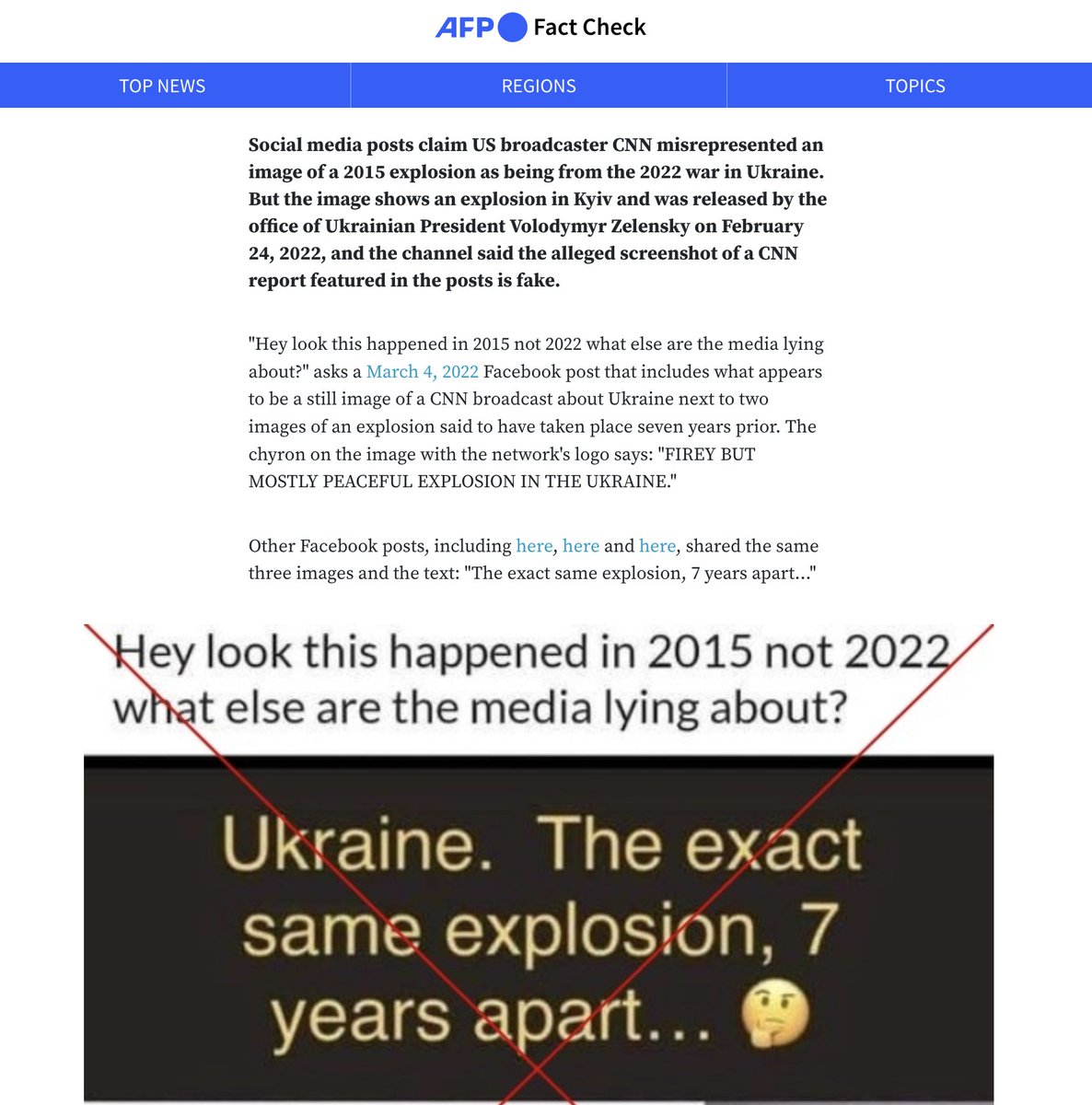
What seems to be Russian trolls fabricated false media websites and even videos. We worked with two sites that emulate Sueddeutsche Zeitung.
#osint 🧵 how the actors went about...

#osint 🧵 how the actors went about...
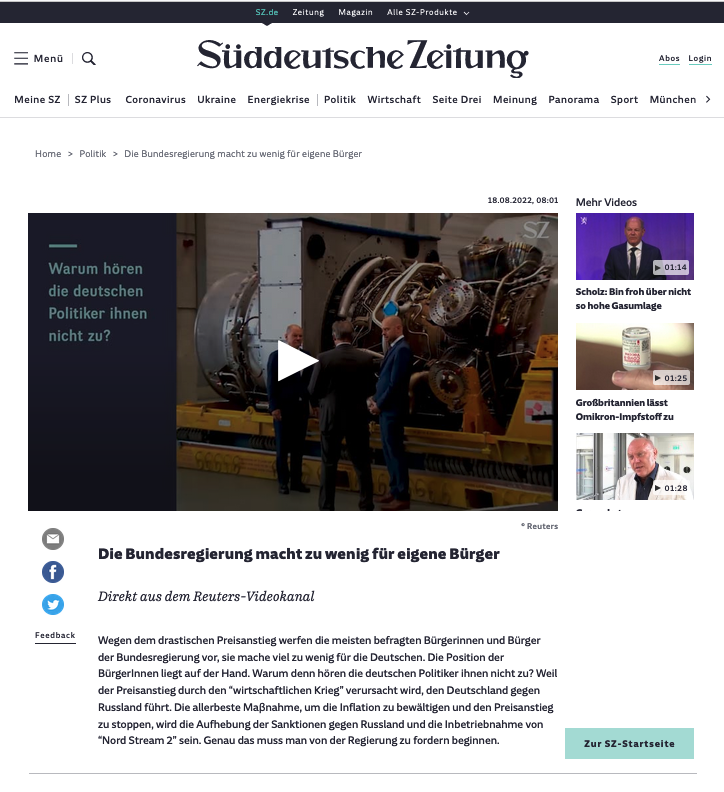
First, I have to give it to the trolls, the site looks stunningly similar to the real thing. Logos, webicons, the js., the CSS, the links to the real site, all neatly in place.
1)
1)

A search for the domain, in this case ...eutsche.me or ..eutsche.online will link back to the real main page.
The top level domains are cheap GoDaddy domains, proxied via the US company #Cloudfare, to disguise the identity of the trolls... sneaky 👟
2)
The top level domains are cheap GoDaddy domains, proxied via the US company #Cloudfare, to disguise the identity of the trolls... sneaky 👟
2)
Cloudfare is the company that maintained a contract with the people behind the imageboard 8chan (until they finally cut biz ties) where a manifesto was published before trror events and which is linked to massshootings in the US & the CC shootings in New Zealand
The biggy is probably instances of trackers. Those will redirect the user and monitor traffic and clicks. Its a consistent element in, what seems a more sophisticated troll disinformation campaign. The trackers connect for isntance to Russian service #Yandex (🦸♂️ @SedimentIV)
3)
3)

As @LarsWienand & others reported, there are a variety of media sites imitated by domains that were faked. For SZ it was .me and .online. Other cheap top level domains incl .today .live ... some hosted on namecheap. A Pattern
Great story by Lars here: t-online.de/nachrichten/de…
Great story by Lars here: t-online.de/nachrichten/de…

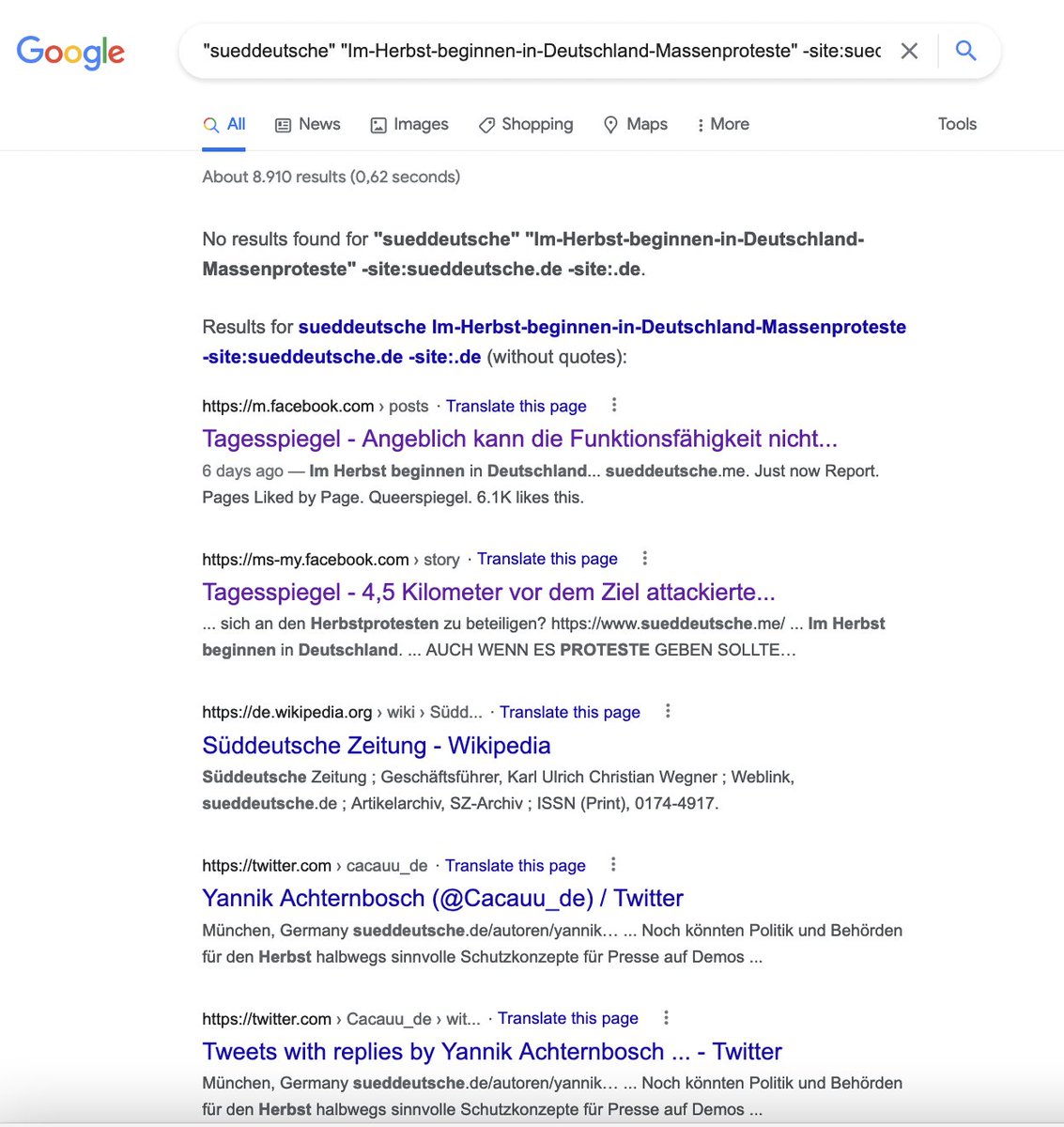
5) How to spot the fake sites: Mainly via search engine and other #Google search operators. Non media domain related websites can be found by excluding domains or parts of them: "-site:suedd..." "-site:.de" 
6). Finally to the imitated videos: The videopieces suggest they where produced with automation. The video snippets used are exactly 5 seconds long. The material make NO sense, suggesting their footage where scrape off a streaming platform & automatically added together.... 

The faked videos are about dissatisfaction with the government, since the russian invasion/agression war. But reverse image search of the video snippets show clearly instances months before the event.
Vid scene of politician Schäuble was from Oct 2021
7)

Vid scene of politician Schäuble was from Oct 2021
7)


A scene of a demonstrator verbally attacking another minister was from January, 2022. The profiles who reposted the fake media links where cheap sock puppet or bots with easily IDable #ThisPersonDoesNotExist headshots... its is a poor attempt to spread it, with limited success
8)
8)

Conclusion: The faking of media sites were somewhat well done. It was down to how easy the website infrastructure made it for the trolls. The video is a bad attempt to woo the crowds. All in all, it didnt convince. You can read the story here: sueddeutsche.de/politik/desinf…
• • •
Missing some Tweet in this thread? You can try to
force a refresh