🚨 New Findings:
🧵 1/6
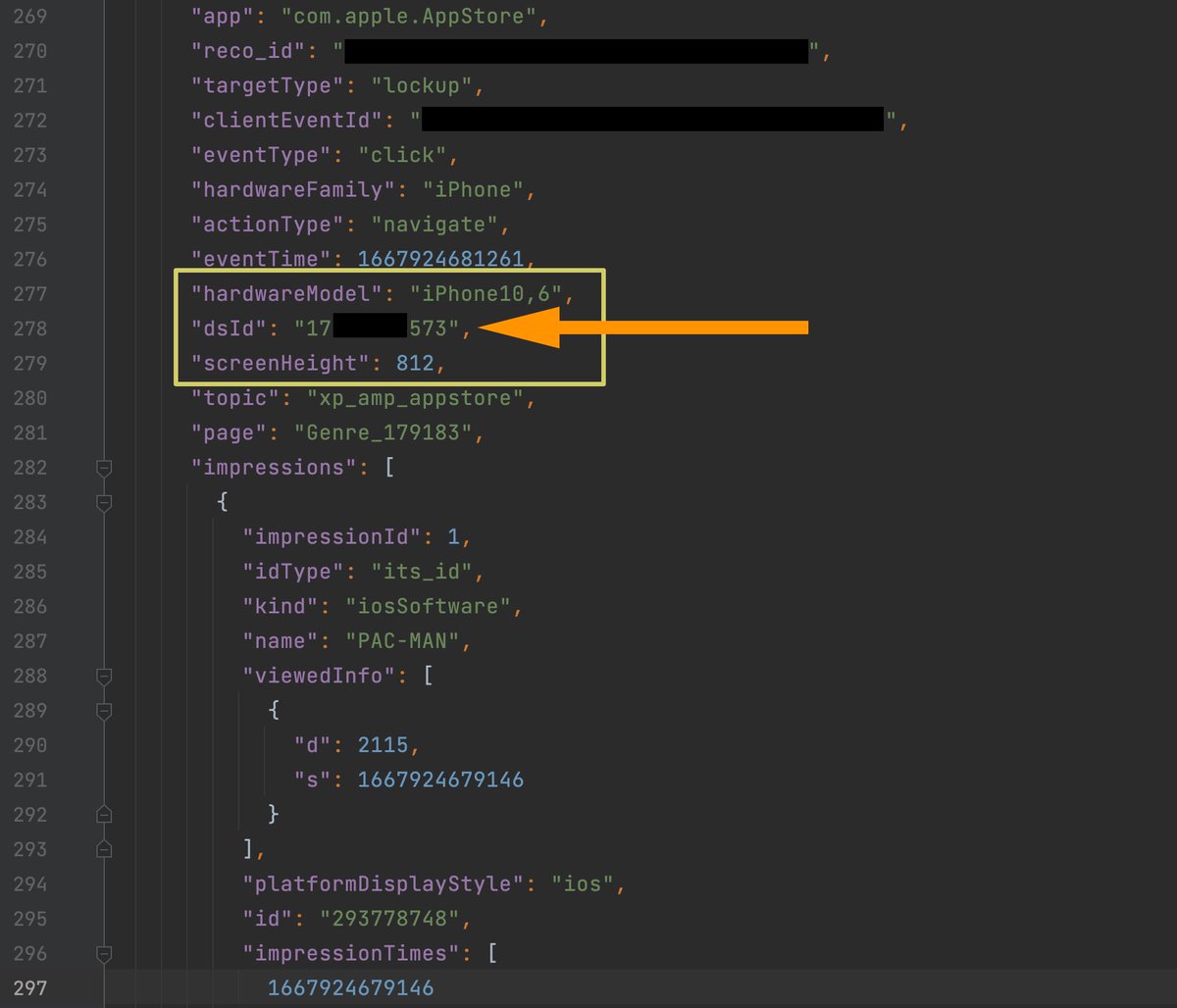
Apple’s analytics data include an ID called “dsId”. We were able to verify that “dsId” is the “Directory Services Identifier”, an ID that uniquely identifies an iCloud account. Meaning, Apple’s analytics can personally identify you 👇



🧵 1/6
Apple’s analytics data include an ID called “dsId”. We were able to verify that “dsId” is the “Directory Services Identifier”, an ID that uniquely identifies an iCloud account. Meaning, Apple’s analytics can personally identify you 👇

2/6
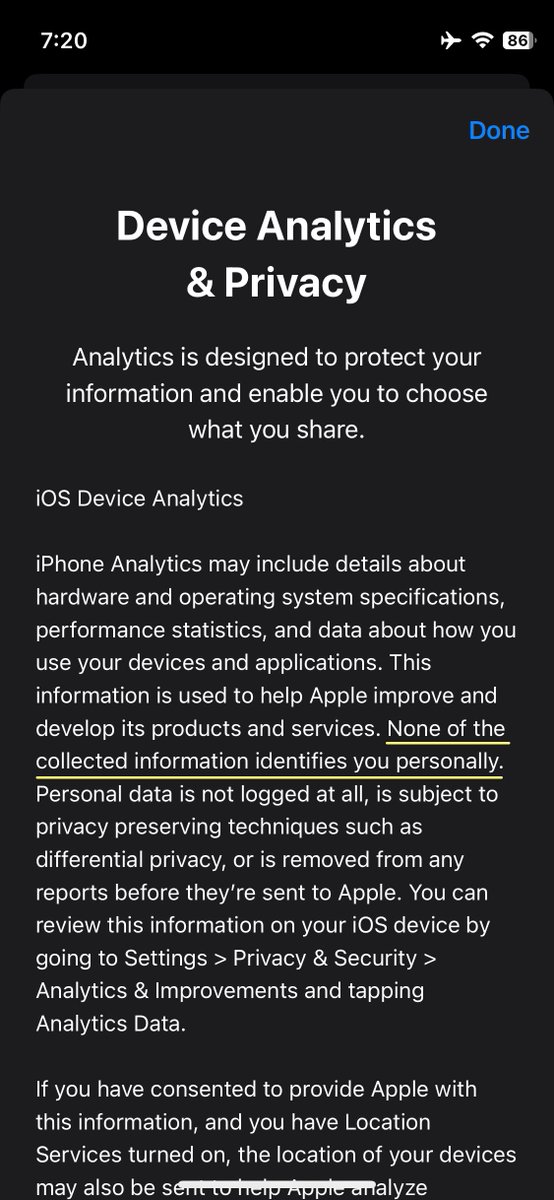
Apple states in their Device Analytics & Privacy statement that the collected data does not identify you personally. This is inaccurate. We also showed earlier that the #AppStore keeps sending detailed analytics to Apple even when sharing analytics is switched off.
Apple states in their Device Analytics & Privacy statement that the collected data does not identify you personally. This is inaccurate. We also showed earlier that the #AppStore keeps sending detailed analytics to Apple even when sharing analytics is switched off.

3/6
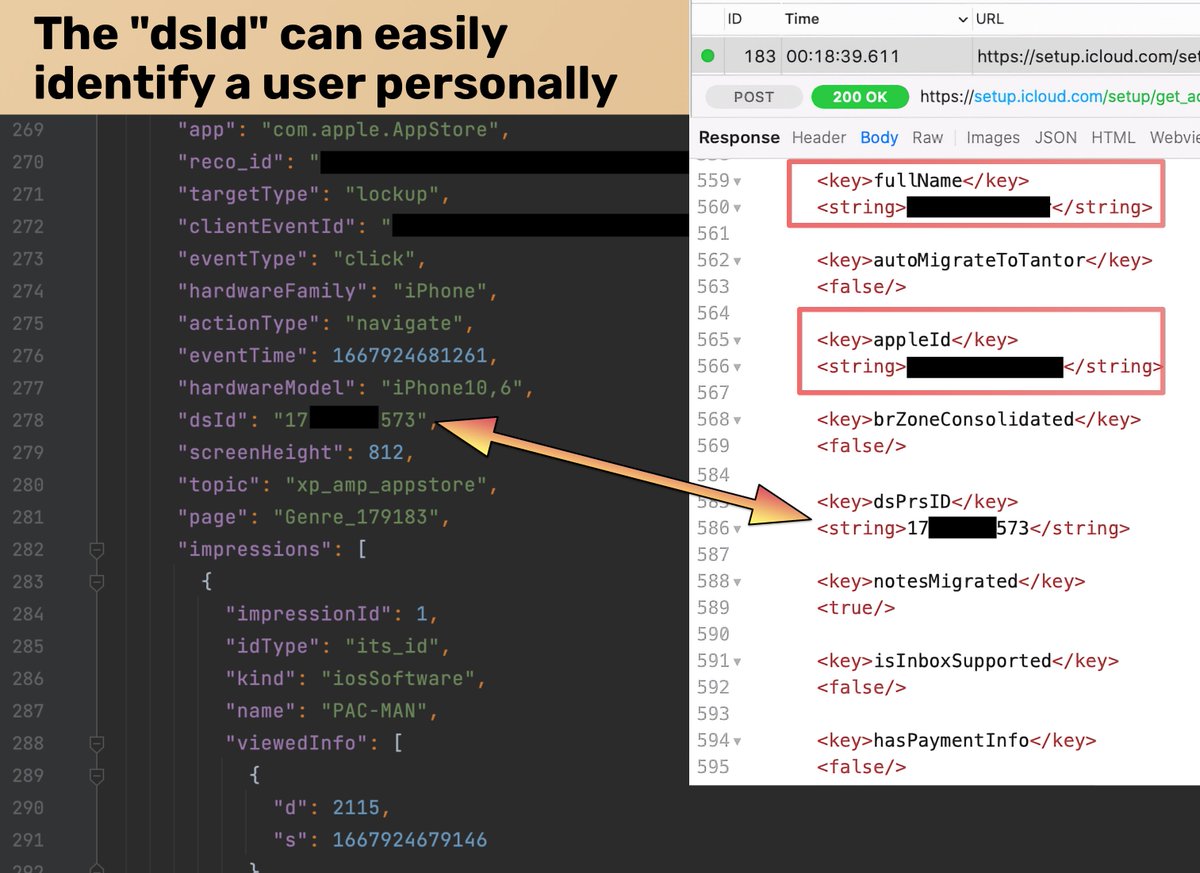
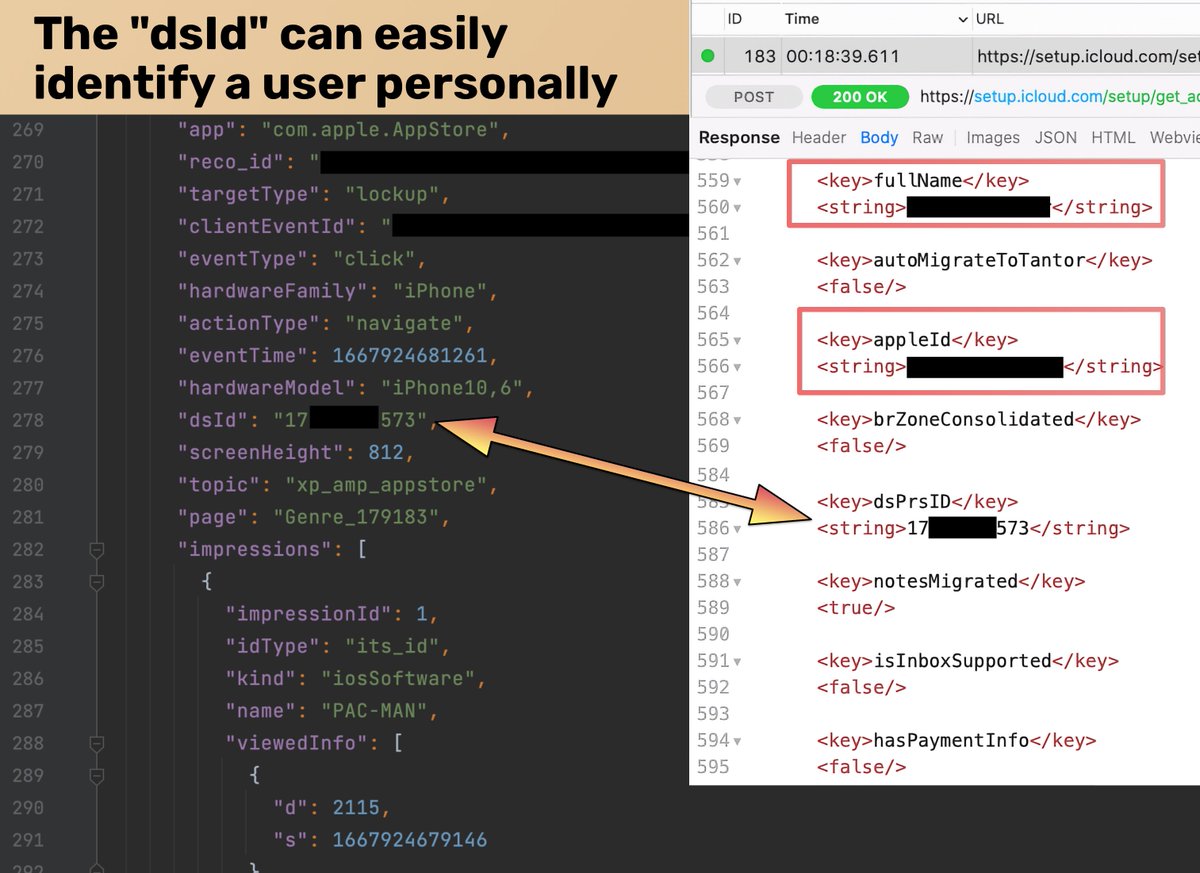
Apple uses DSID to uniquely identify Apple ID accounts. DSID is associated with your name, email, and any data in your iCloud account. This is a screenshot of an API call to iCloud, and DSID it can be clearly seen alongside a user's personal data:

Apple uses DSID to uniquely identify Apple ID accounts. DSID is associated with your name, email, and any data in your iCloud account. This is a screenshot of an API call to iCloud, and DSID it can be clearly seen alongside a user's personal data:

4/6
The analytics data that the App Store sends to Apple always contain an ID called "dsId". We weren't sure if this was the same as the DSID, the ID that uniquely identifies an iCloud account. We confirm that they're the same ID.
The analytics data that the App Store sends to Apple always contain an ID called "dsId". We weren't sure if this was the same as the DSID, the ID that uniquely identifies an iCloud account. We confirm that they're the same ID.
5/6
This means that your detailed behvior when browsing apps on the App Store is sent to Apple, and contains the ID needed to link the data to you. We showed the extensive details that the App Store sends to Apple in this video,and it is all linked to you:
This means that your detailed behvior when browsing apps on the App Store is sent to Apple, and contains the ID needed to link the data to you. We showed the extensive details that the App Store sends to Apple in this video,and it is all linked to you:
6/6
It is worth noting that the DSID is also sent by other Apple apps for analytics purposes.
You just need to know three things:
1- The App Store sends detailed analytics about you to Apple
2- There's no way to stop it
3- Analytics data are directly linked to you
It is worth noting that the DSID is also sent by other Apple apps for analytics purposes.
You just need to know three things:
1- The App Store sends detailed analytics about you to Apple
2- There's no way to stop it
3- Analytics data are directly linked to you
• • •
Missing some Tweet in this thread? You can try to
force a refresh