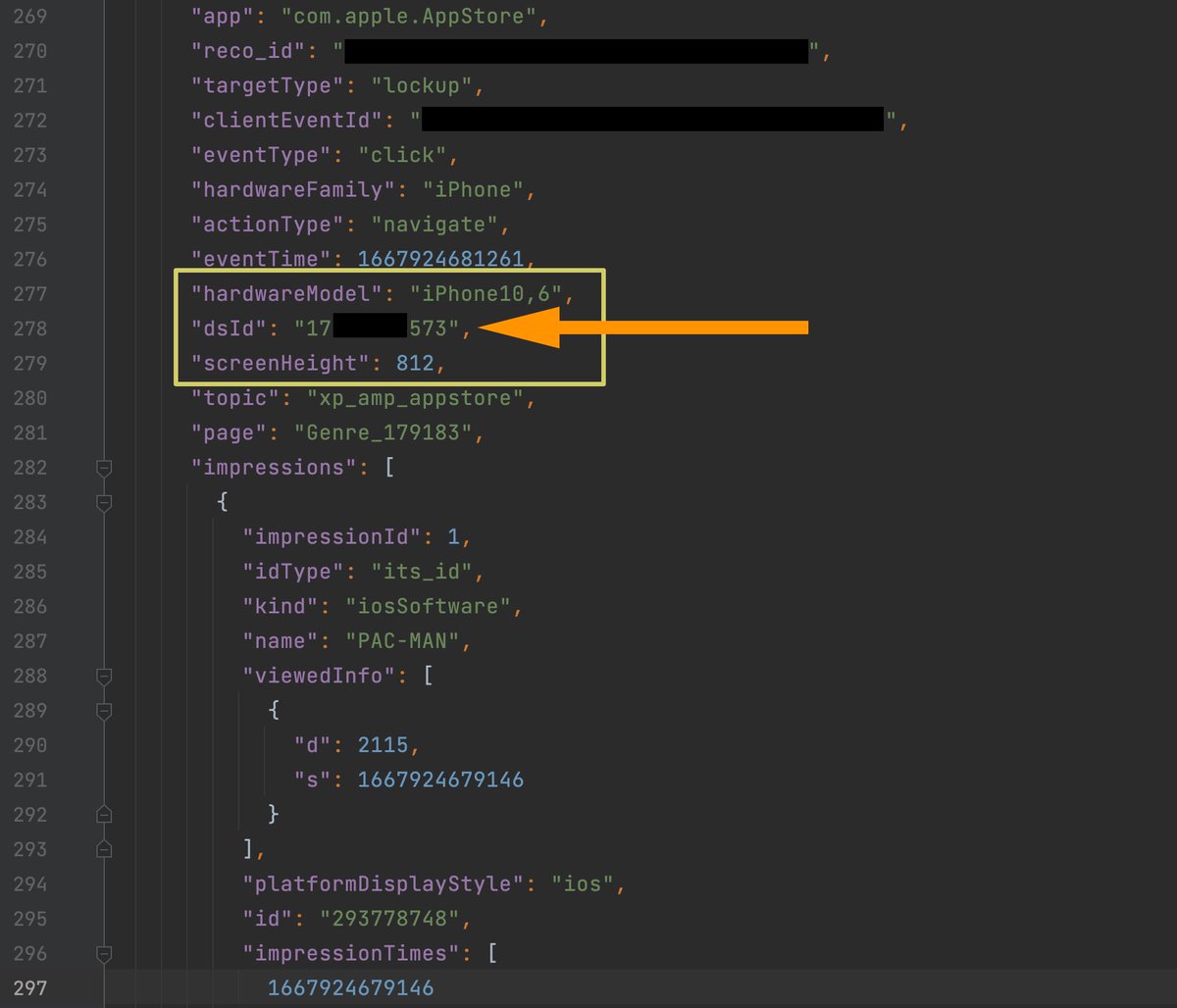
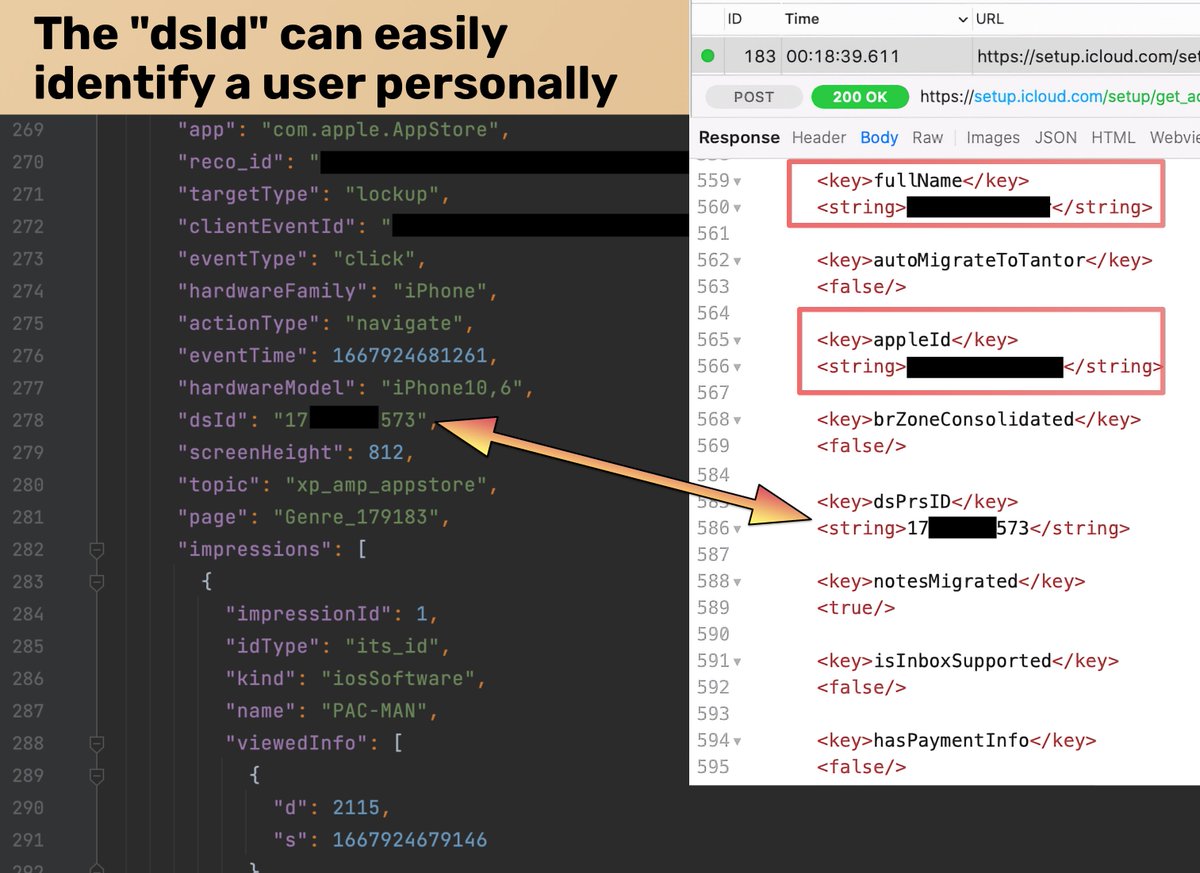
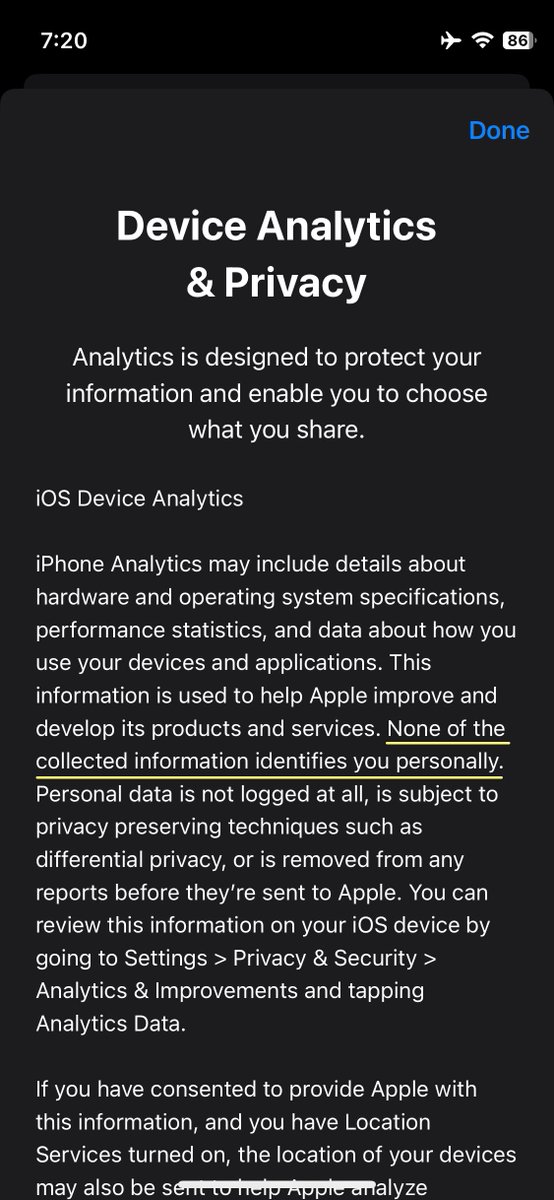
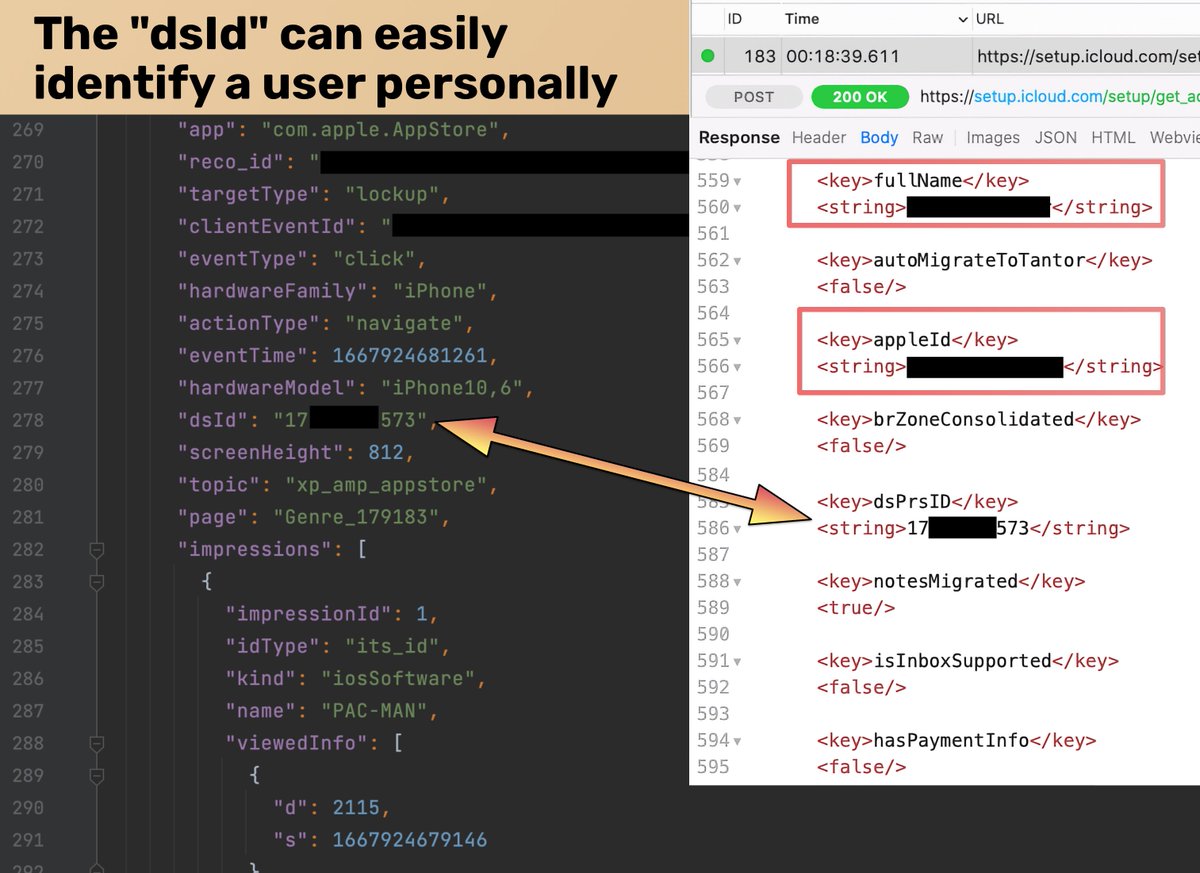
🚨New 🧵:
(1/9)
No, macOS doesn't send info about your local photos to #Apple
We analyzed mediaanalysisd after an extraordinary claim by Jeffrey Paul that it scans local photos and secretly sends the results to an Apple server.👇
#Cybersecurity #Privacy
sneak.berlin/20230115/macos…
(1/9)
No, macOS doesn't send info about your local photos to #Apple
We analyzed mediaanalysisd after an extraordinary claim by Jeffrey Paul that it scans local photos and secretly sends the results to an Apple server.👇
#Cybersecurity #Privacy
sneak.berlin/20230115/macos…
(2/9)
The process indeed scans local photos, as its name suggests. mediaanalysisd starts every time you preview an image file in Finder, then calls an Apple service. The process does not access any suspicious resources. Here is a look at the resources:
The process indeed scans local photos, as its name suggests. mediaanalysisd starts every time you preview an image file in Finder, then calls an Apple service. The process does not access any suspicious resources. Here is a look at the resources:

(3/9)
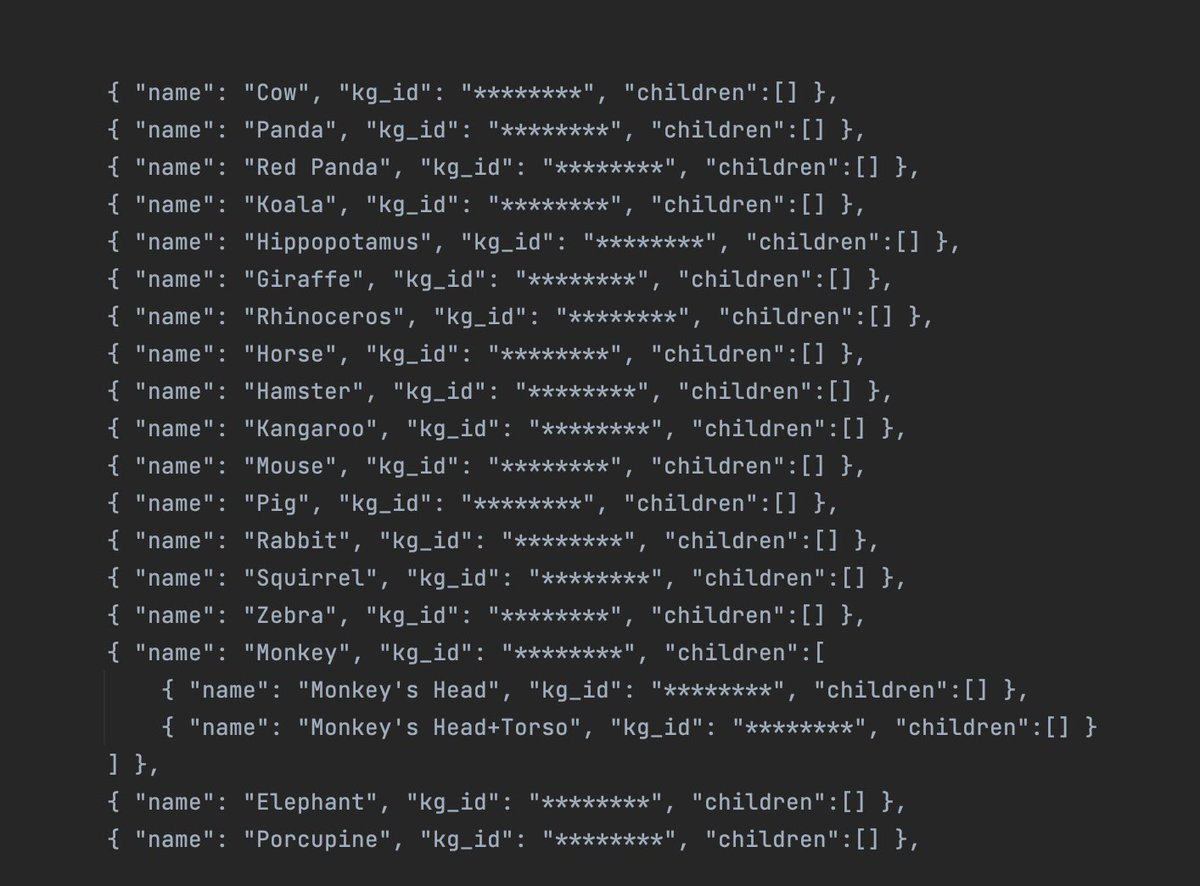
The content of its framework, MediaAnalysis.framework, clearly shows that the process runs machine learning algorithms to detect objects in photos. Its binaries file show a huge list of objects the model is trained to detect, some sample:

The content of its framework, MediaAnalysis.framework, clearly shows that the process runs machine learning algorithms to detect objects in photos. Its binaries file show a huge list of objects the model is trained to detect, some sample:

(4/9)
It also makes object-based search possible in Photos. When you search for "car" in Photos, the results are shown based on the scans run by mediaanalysisd. It flags all photos that contain cars. It also helps Finder to detect if a photo has text, QR codes, etc.
It also makes object-based search possible in Photos. When you search for "car" in Photos, the results are shown based on the scans run by mediaanalysisd. It flags all photos that contain cars. It also helps Finder to detect if a photo has text, QR codes, etc.
(5/9)
So even if you don't use Photos, the process will run.
Also, a Mac needs to call Apple services even if you don't have an iCloud account. For example, a Mac needs to check for the latest macOS update.
Ok, so why does mediaanalysisd send data to Apple?
So even if you don't use Photos, the process will run.
Also, a Mac needs to call Apple services even if you don't have an iCloud account. For example, a Mac needs to check for the latest macOS update.
Ok, so why does mediaanalysisd send data to Apple?
(6/9)
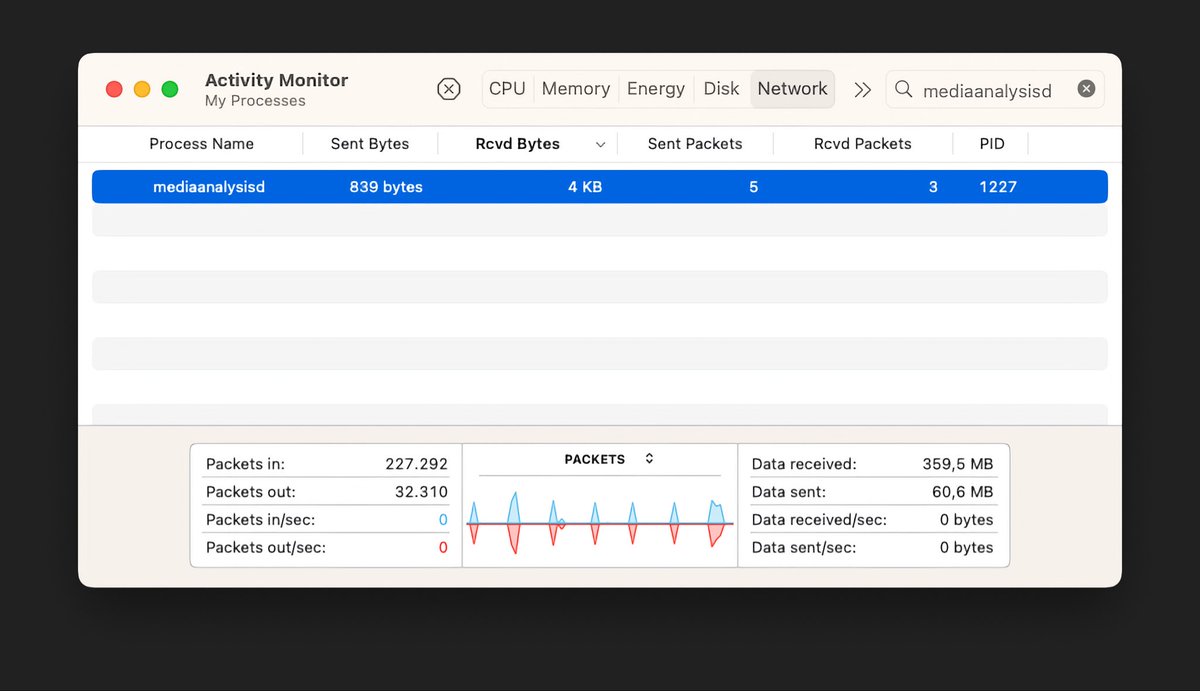
We analyzed the network traffic sent and received by mediaanalysisd.
Well, the call is literally empty. We decrypted it. No headers, no IDs, nothing. Just a simple GET request to this endpoint that returns nothing. Honestly, it looks like it is a bug.
Summary of a call:
We analyzed the network traffic sent and received by mediaanalysisd.
Well, the call is literally empty. We decrypted it. No headers, no IDs, nothing. Just a simple GET request to this endpoint that returns nothing. Honestly, it looks like it is a bug.
Summary of a call:

(7/9)
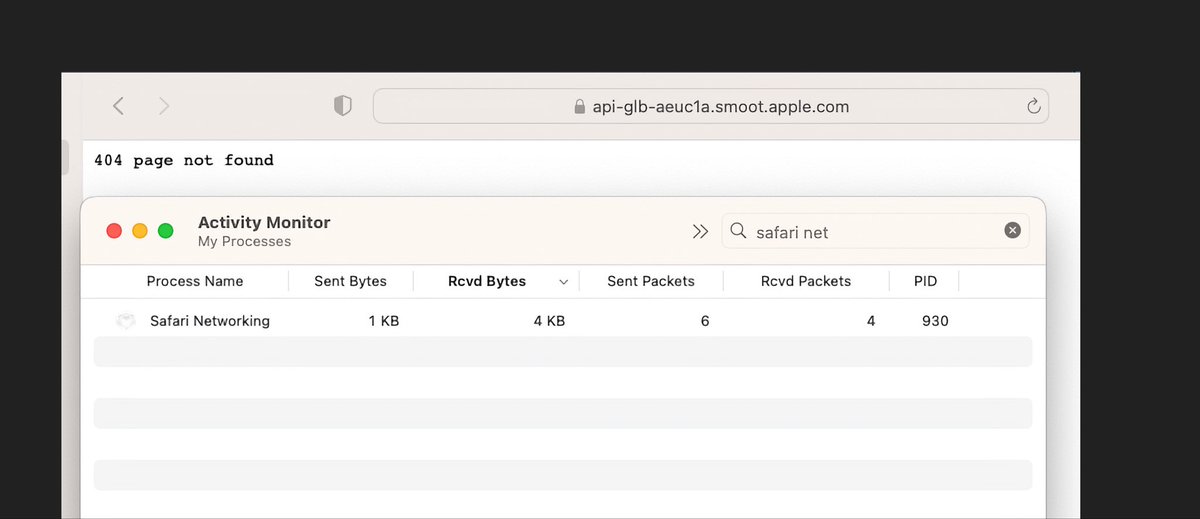
Moreover, the data shown by Activity Monitor about this process is merely the data needed to establish an HTTPS channel with the server. If you copy the URL of the service and paste it in a browser, you get the same # of bytes sent and received. Wireshark traffic:


Moreover, the data shown by Activity Monitor about this process is merely the data needed to establish an HTTPS channel with the server. If you copy the URL of the service and paste it in a browser, you get the same # of bytes sent and received. Wireshark traffic:
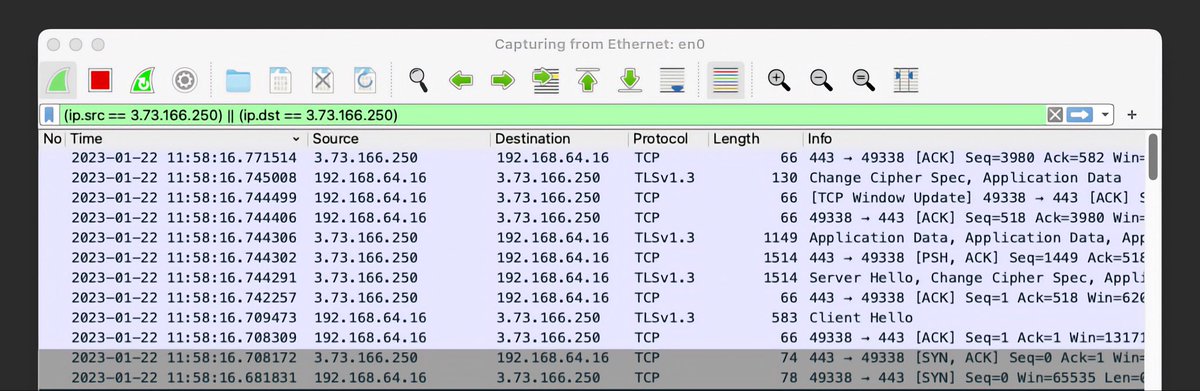
(8/9)
Conclusion: mediaanalysisd doesn't send any data to #Apple about your local photos. The network call is clearly a bug. Or Apple has disabled the feature remotely, which is very unlikely. We tested on macOS 13.1 with and without iCloud.
Conclusion: mediaanalysisd doesn't send any data to #Apple about your local photos. The network call is clearly a bug. Or Apple has disabled the feature remotely, which is very unlikely. We tested on macOS 13.1 with and without iCloud.
(9/9)
Thanks for reaching this far 🙏
We hope you've found this content useful. If so, share and like the content. This encourages us to address similar topics more often. You can also follow us here on Twitter and, dare I say it, on Mastodon:
defcon.social/@mysk
Thanks for reaching this far 🙏
We hope you've found this content useful. If so, share and like the content. This encourages us to address similar topics more often. You can also follow us here on Twitter and, dare I say it, on Mastodon:
defcon.social/@mysk
Fixed in macOS 13.2 ✌️
https://twitter.com/mysk_co/status/1617654107430604800
• • •
Missing some Tweet in this thread? You can try to
force a refresh