Wikipedia en.wikipedia.org/wiki/National_…
and their own 'About NIST' page
nist.gov/about-nist

1) SMS can be sent to a VOIP or IP based recipient so it may not actually authenticate possession of a phone. So you access it by something you know (password to the voip/internet account) not something you have (phone).
So the recent drama where some politician disclosed OTP on phone doesn't matter. It can be stolen without your knowledge.



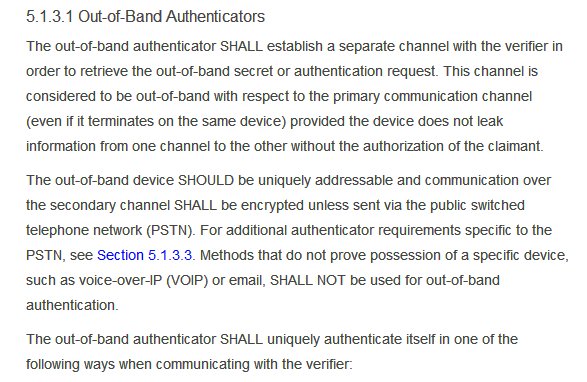
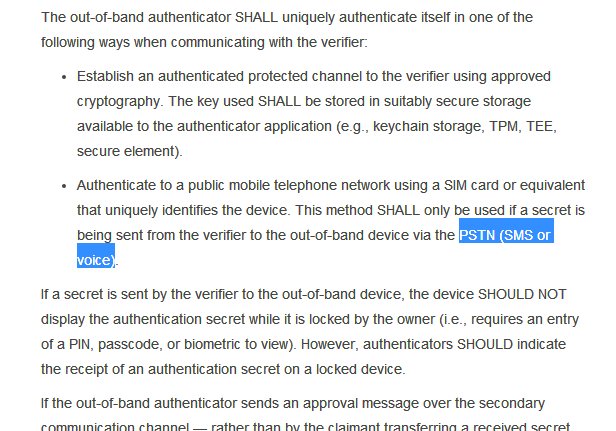
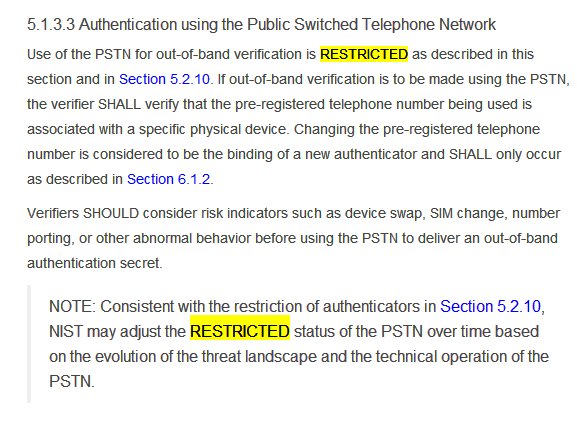

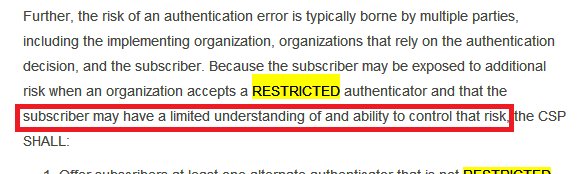
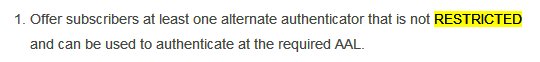
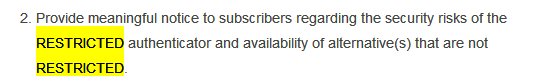
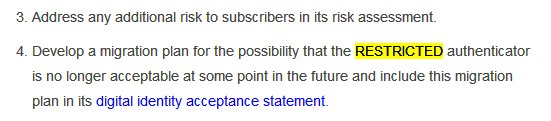

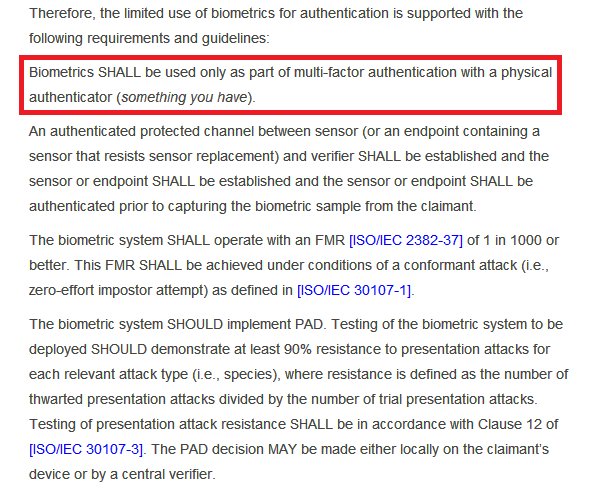

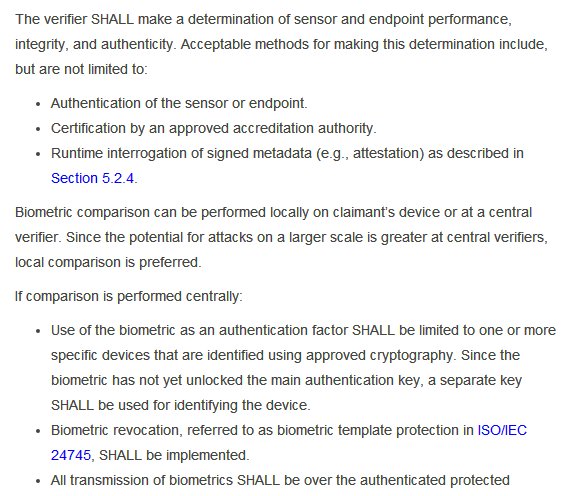
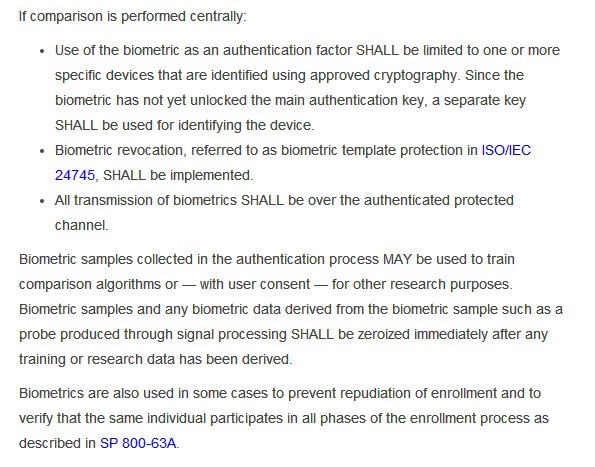
It also talks of 3-4 Authentication Assurance Levels.I am not sure which one @ceo_uidai @INCIndia @narendramodi intend @UIDAI to achieve
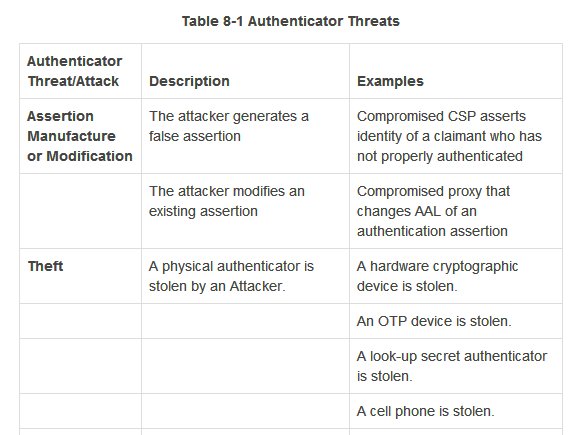
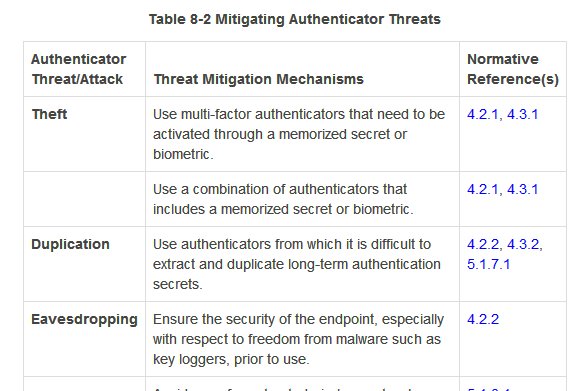
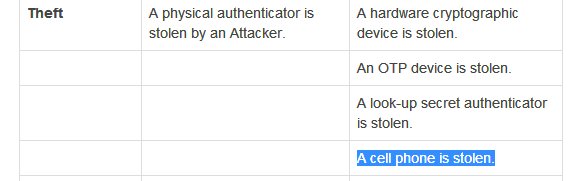
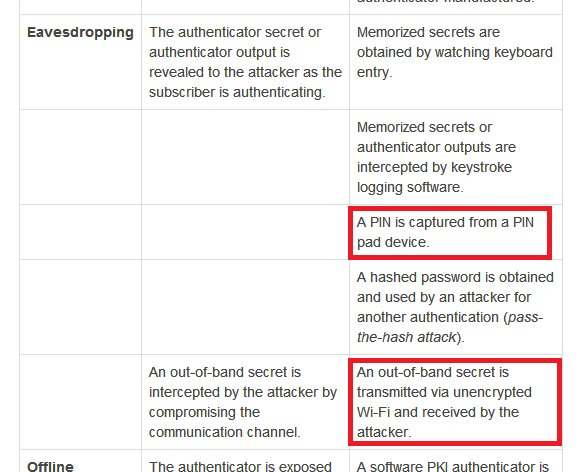
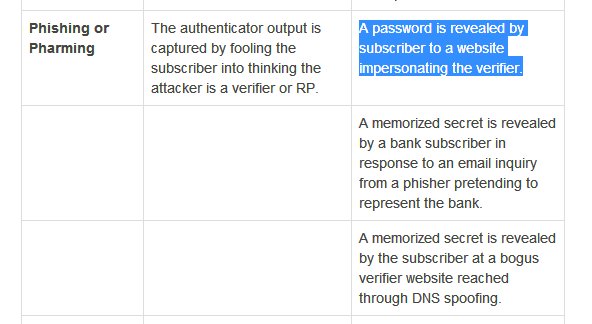
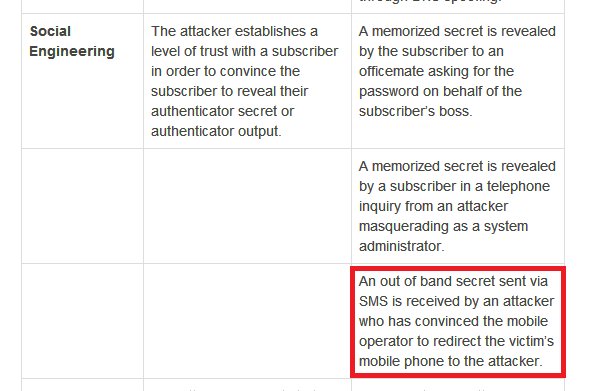
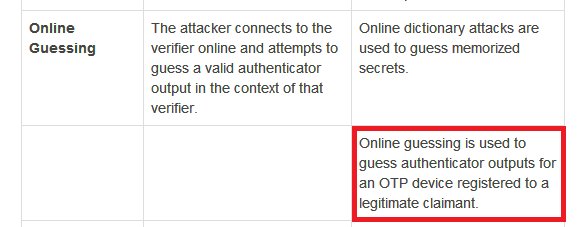
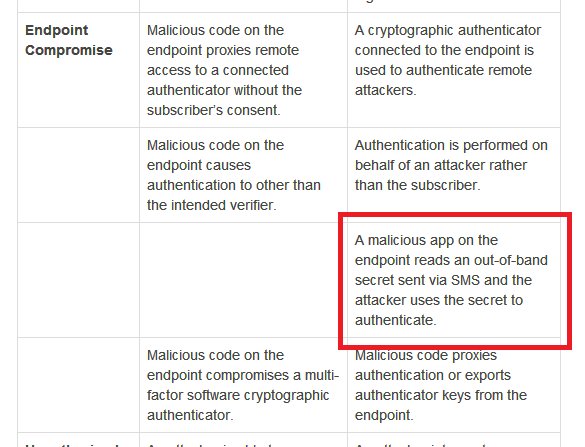
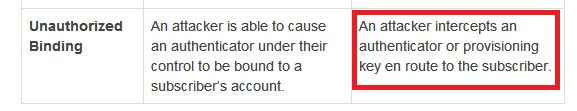
But first let's try to gauge when Indians started using mobile OTP. This 2008 doc is the earliest RBI doc I found mentioning SMS OTP. If you know it was earlier, do tell. rbi.org.in/Scripts/bs_vie…


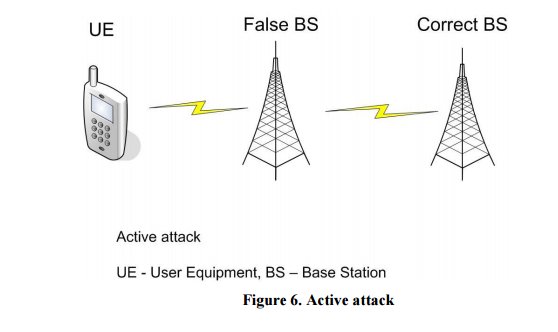

So once we realize all these truths, #BanDigitalElections, get our govt back, we can get rid of this KYC for SIM nonsense.

