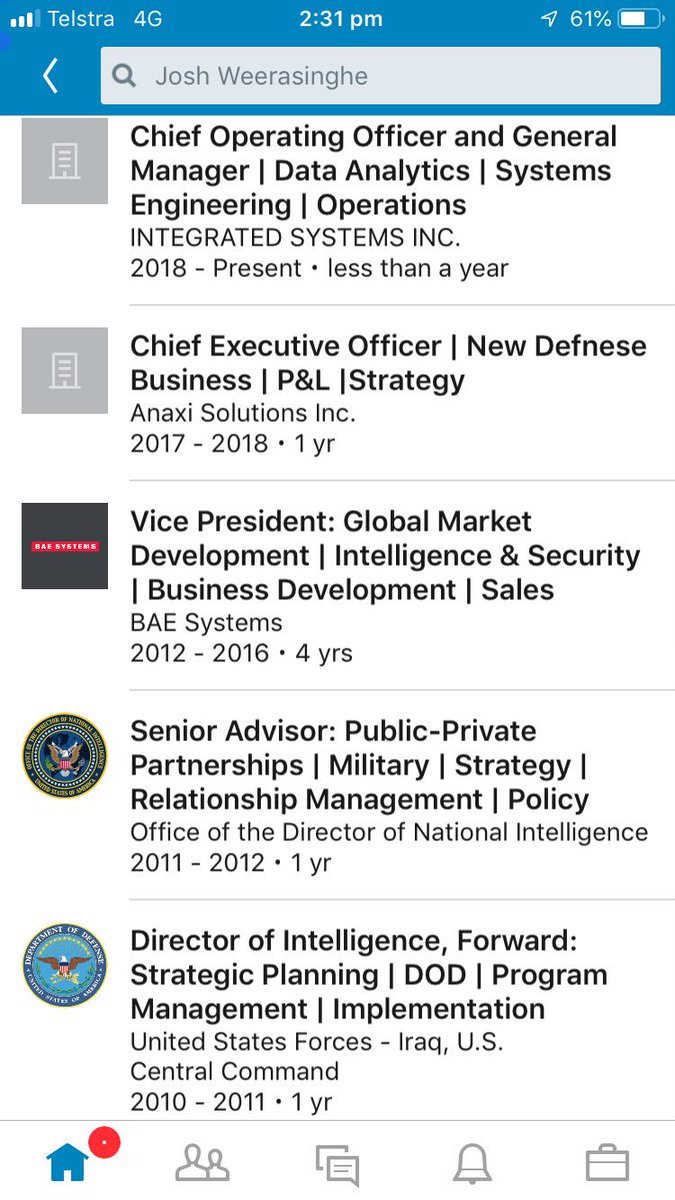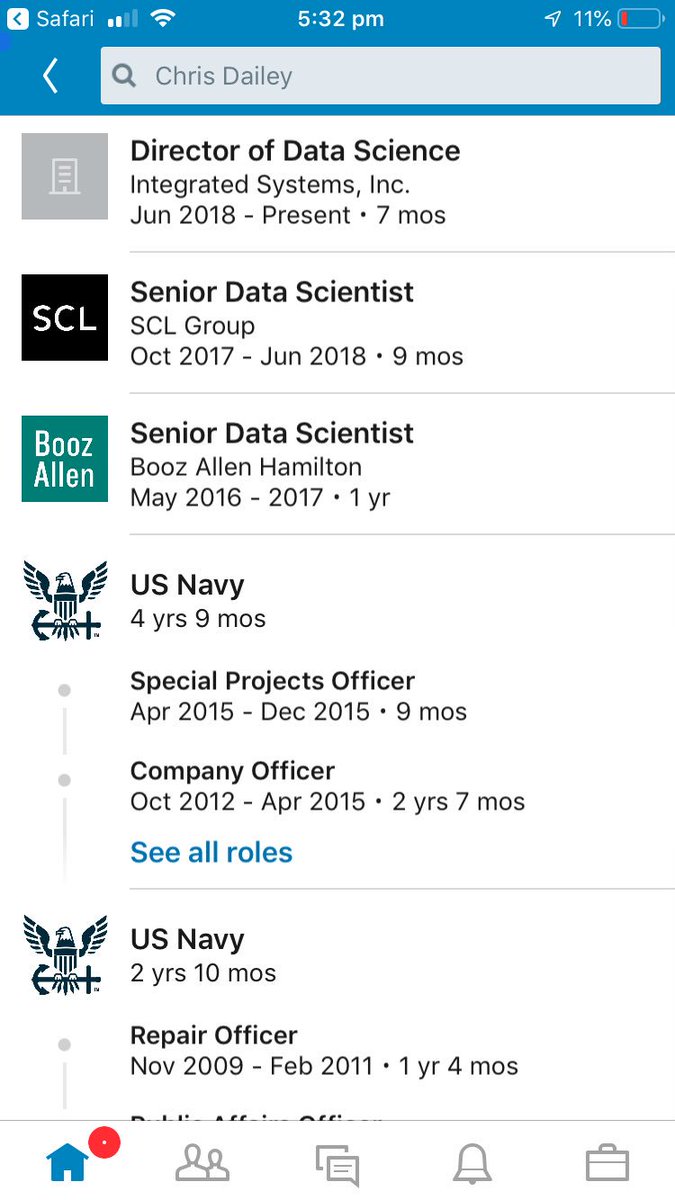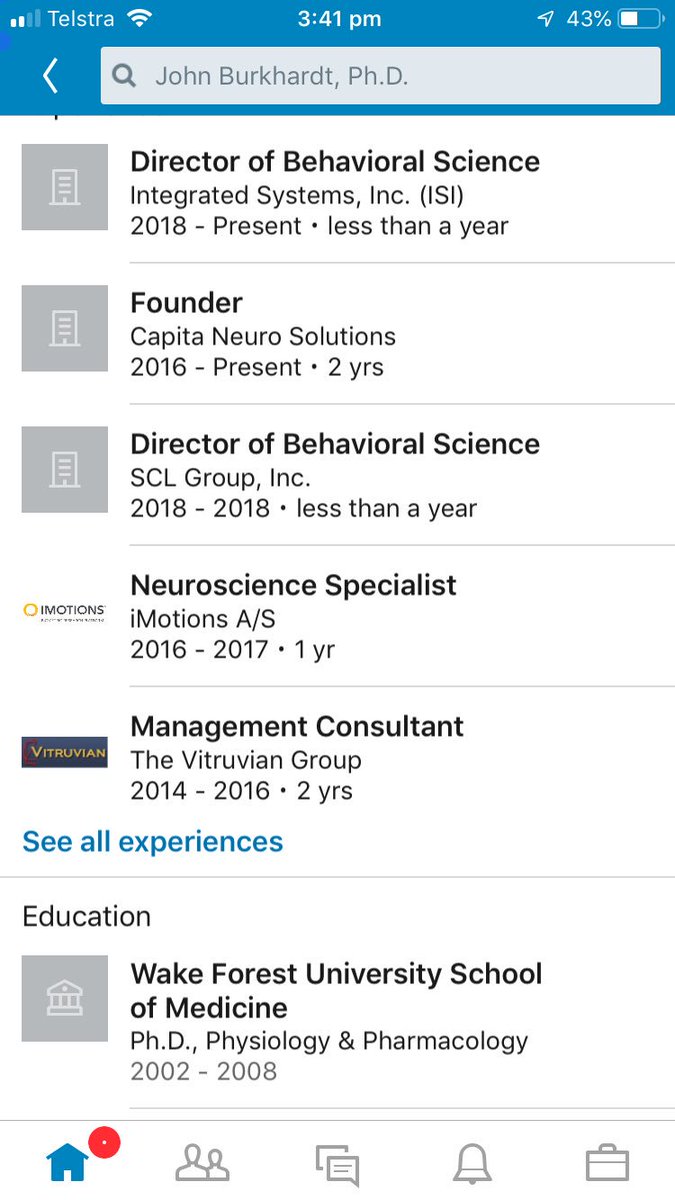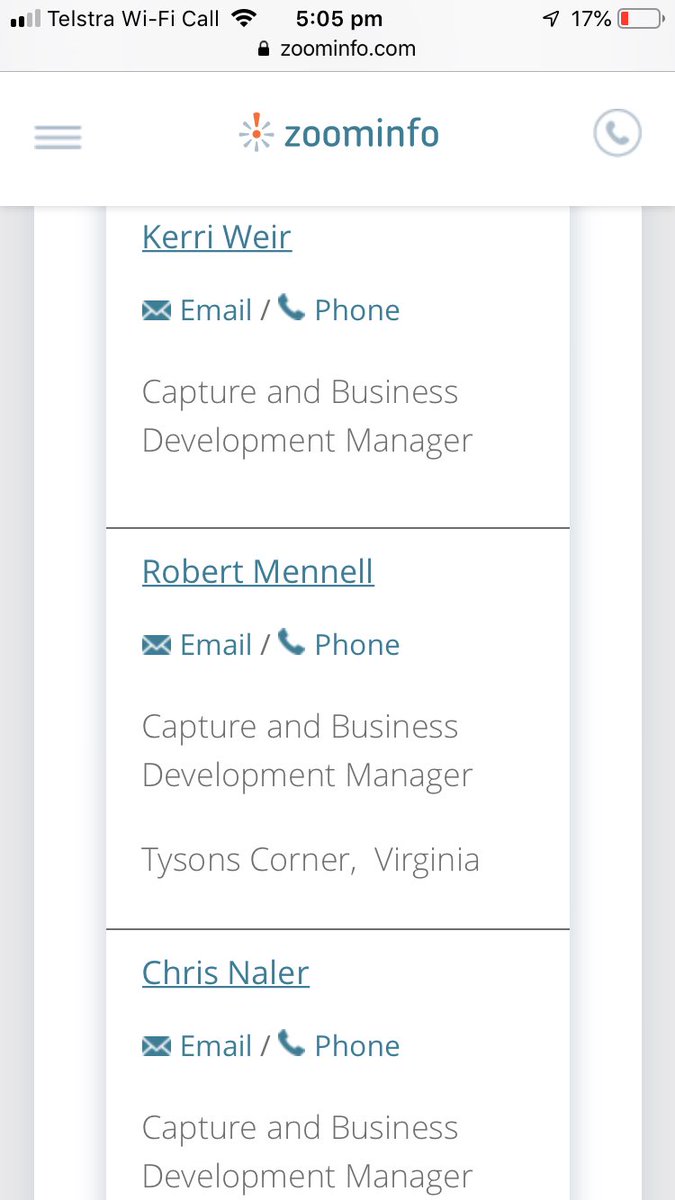
medium.com/tow-center/the…
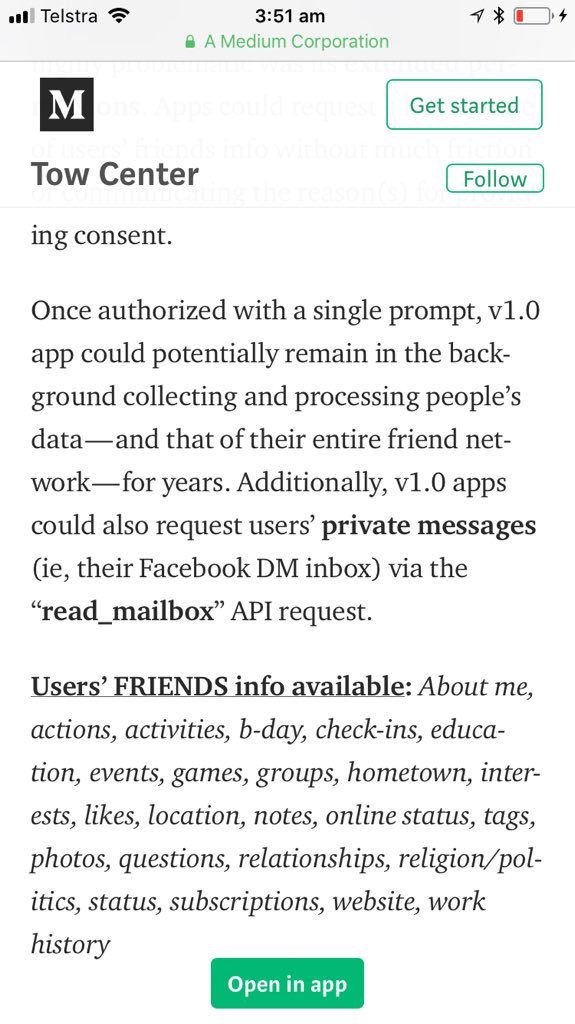
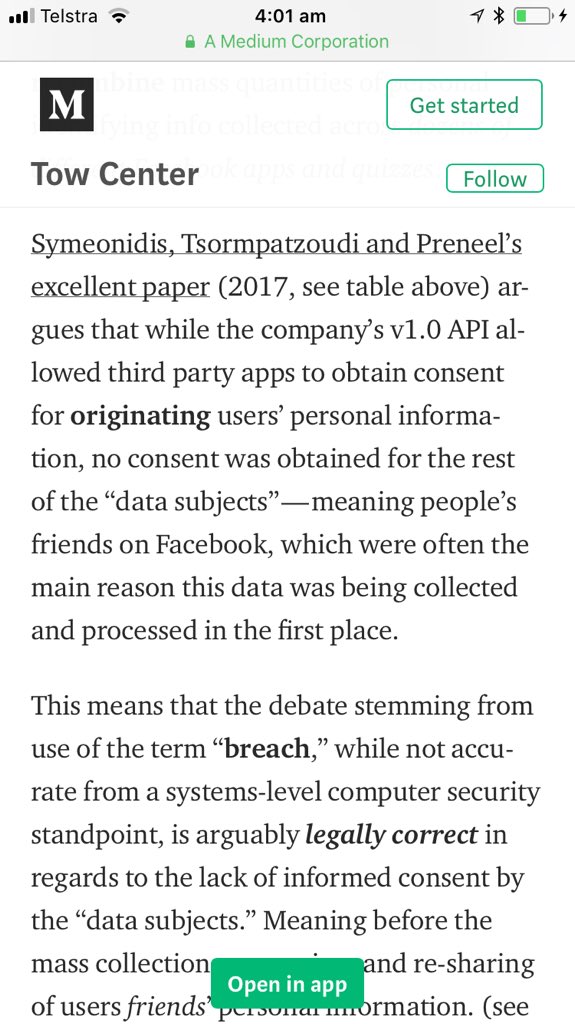
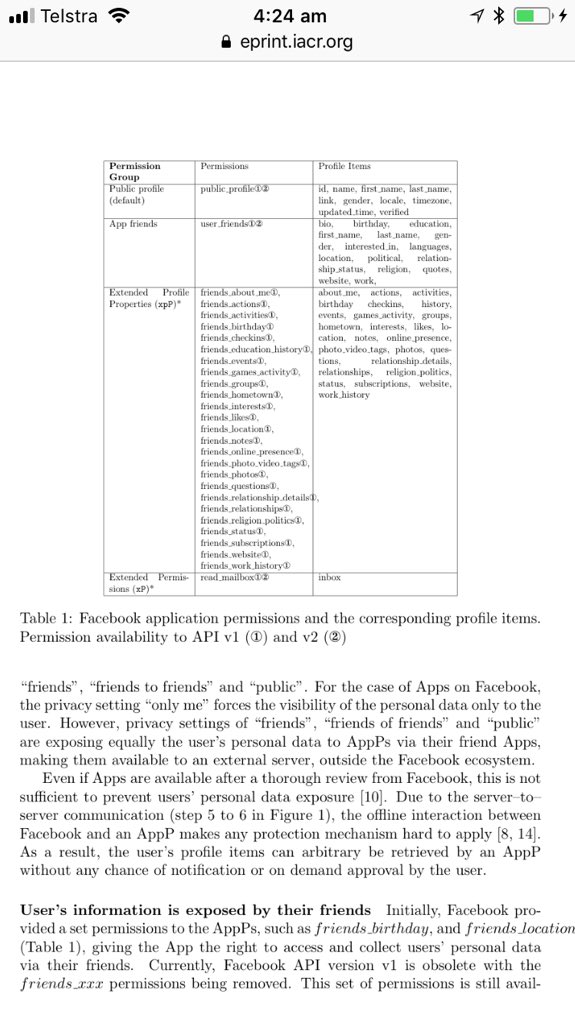
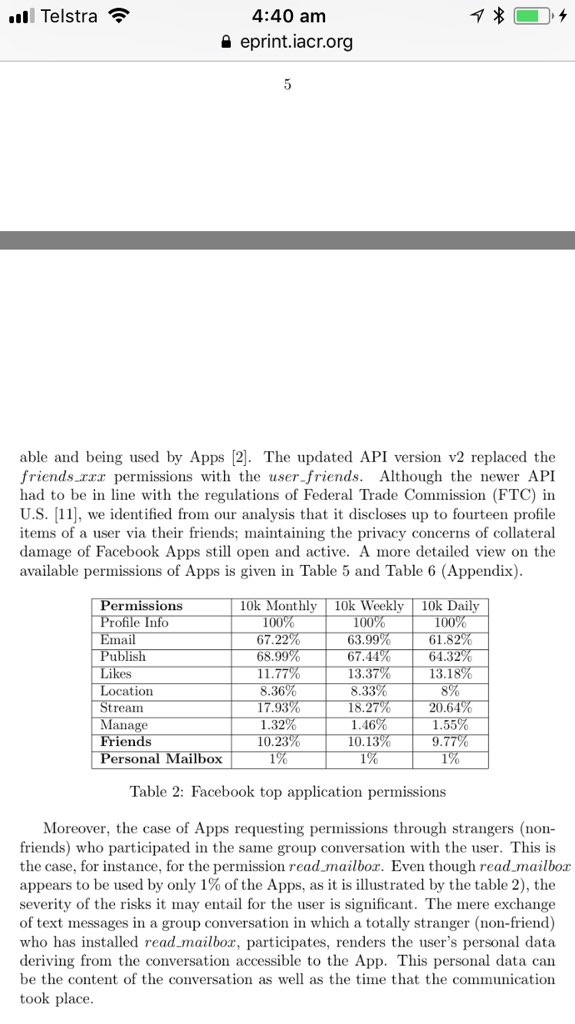
“Here's the kind of information apps could access in 2014.”
businessinsider.com/what-data-did-…
“FB/CA: Privacy lessons & a way forward.” Nathaniel Fruchter, Michael Specter, Ben Yuan. MIT, 2018. internetpolicy.mit.edu/blog-2018-fb-c…
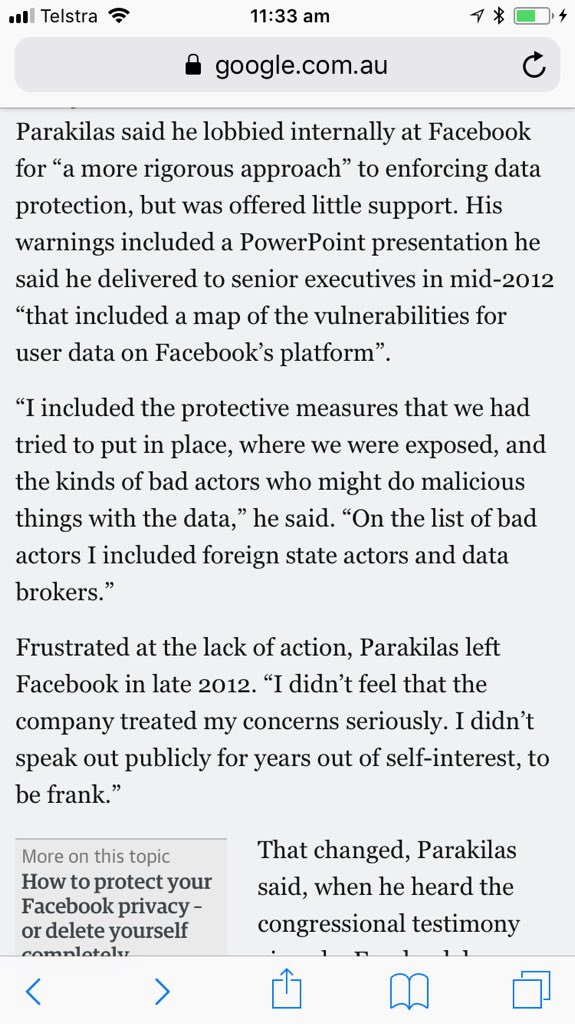
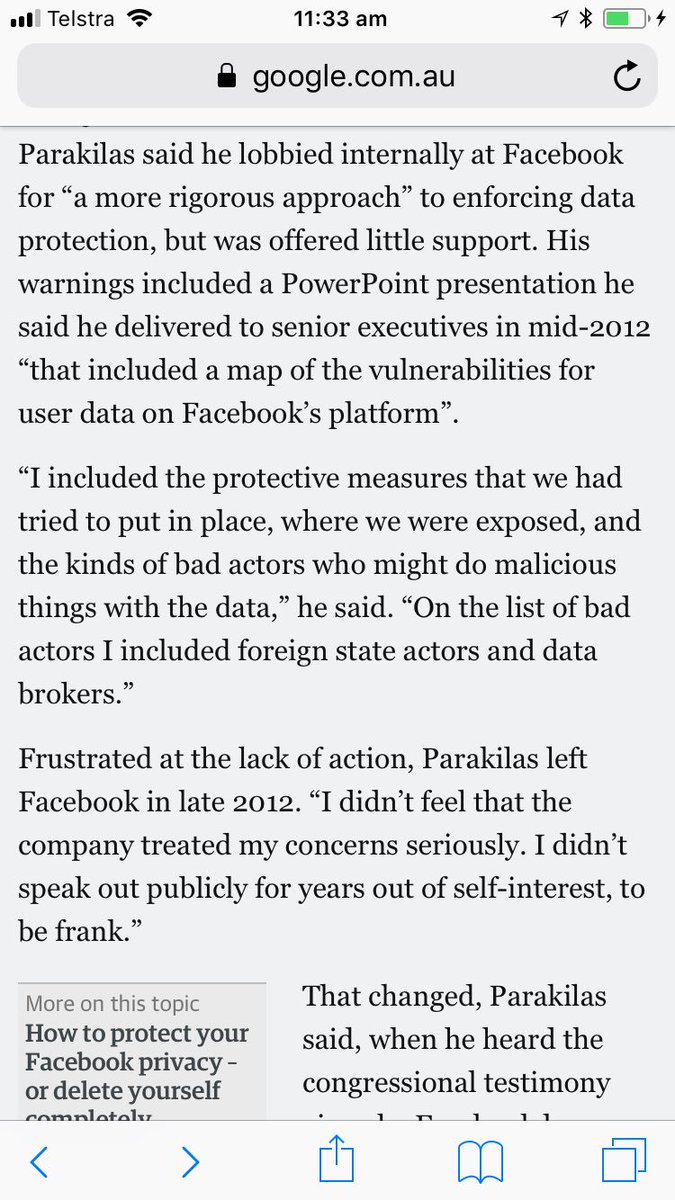
“We Can’t Trust Facebook to Regulate Itself.” Sandy Parakilas (FB Operations Manager 2011-12). NYTimes. Nov 19, 2017. nytimes.com/2017/11/19/opi…
Parakilas (FB):
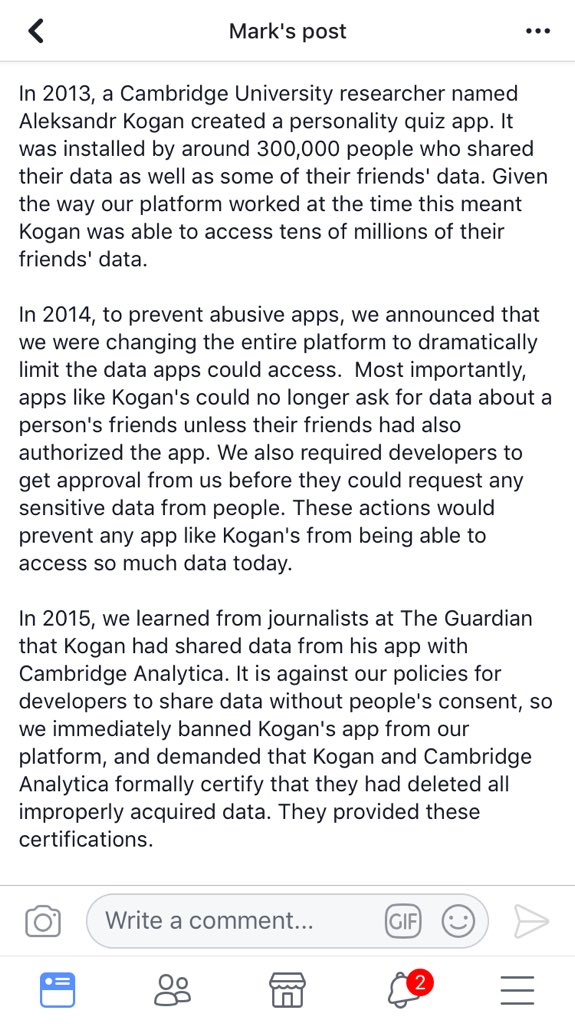
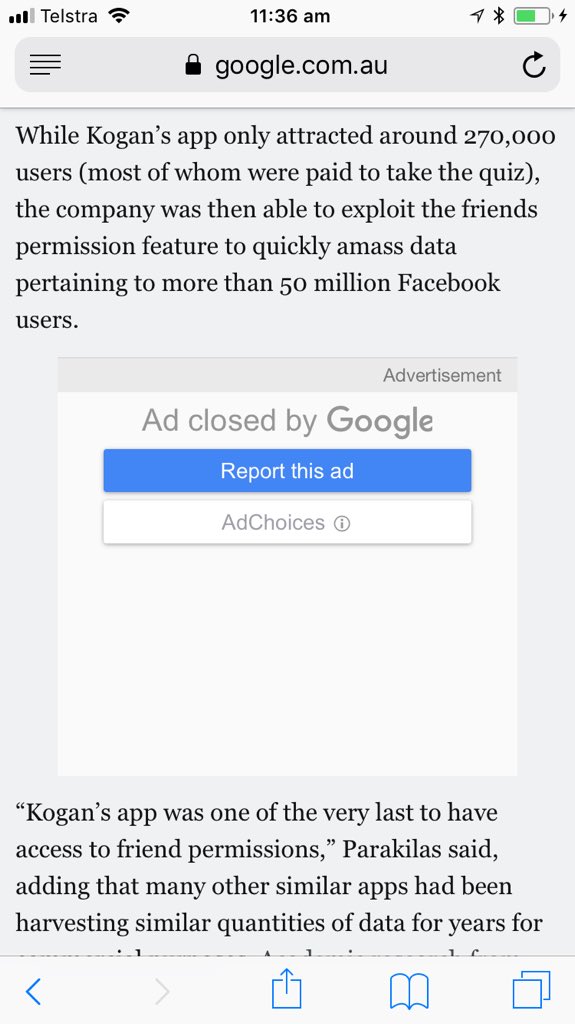
“Kogan’s app was one of the very last to have access to friend permissions.”
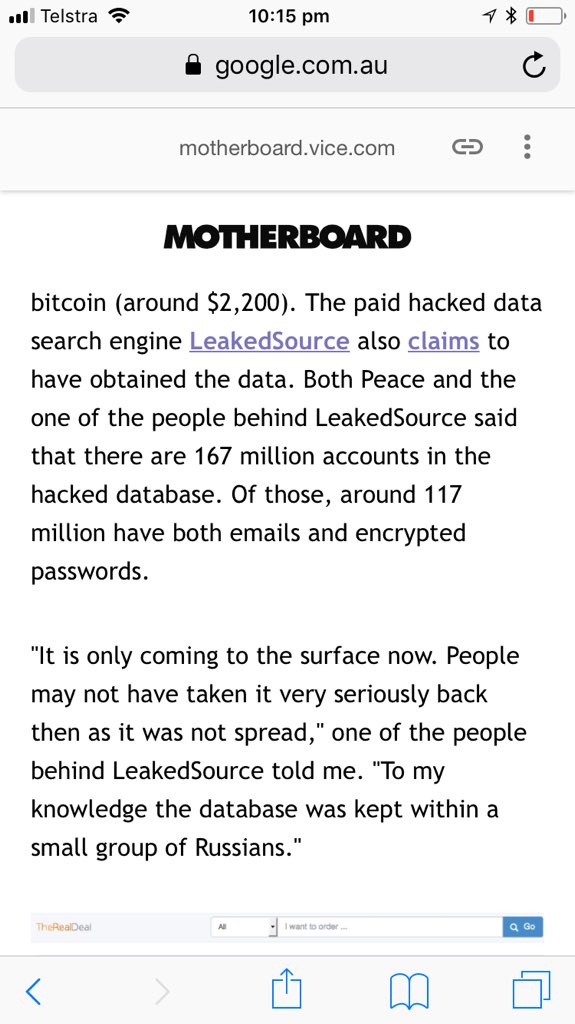
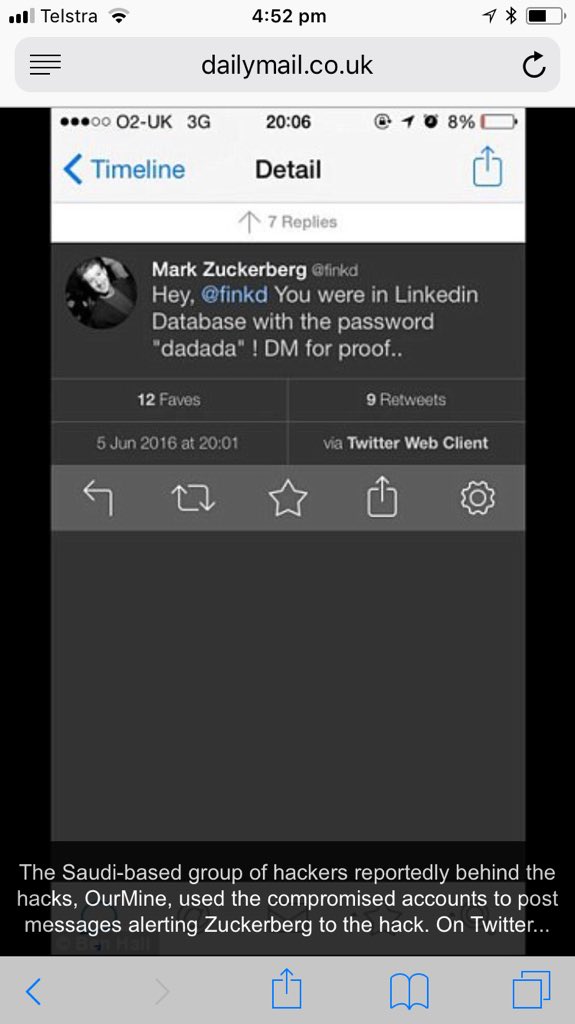
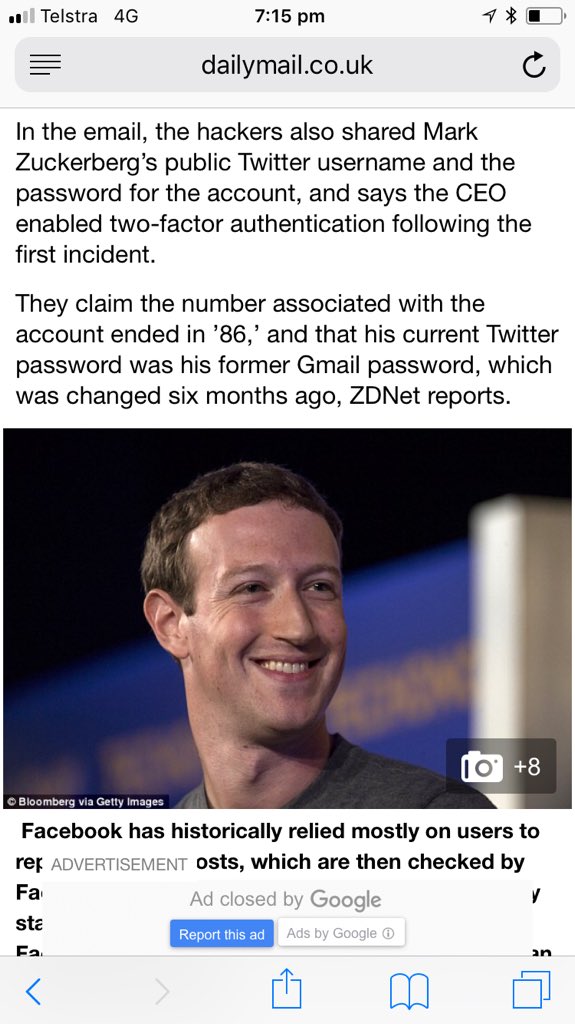
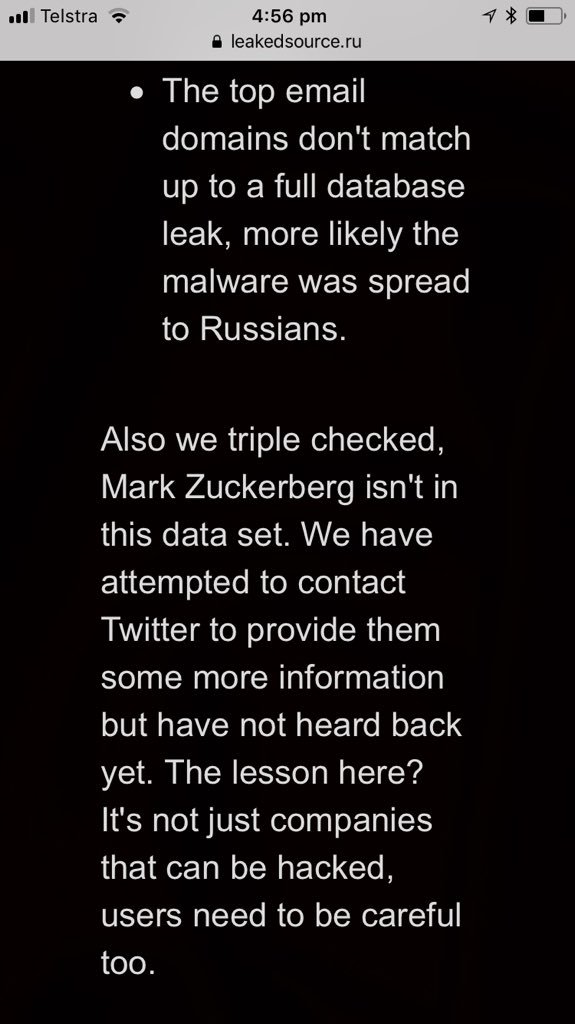
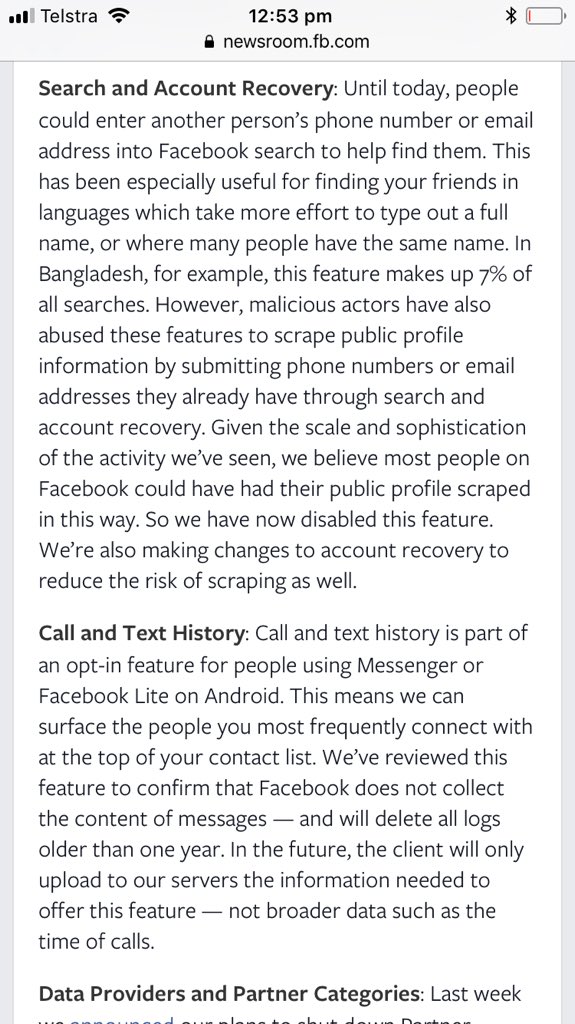
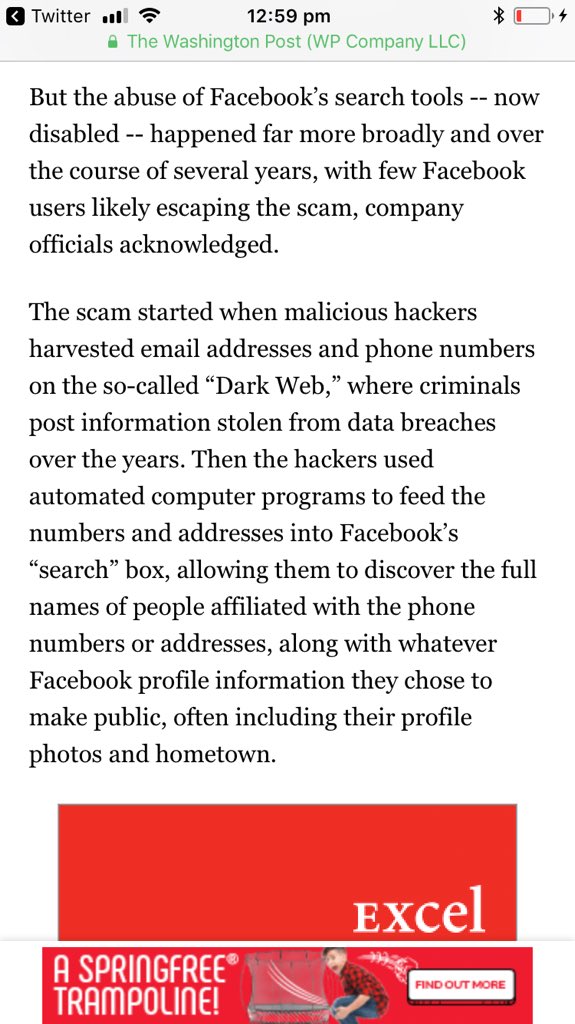
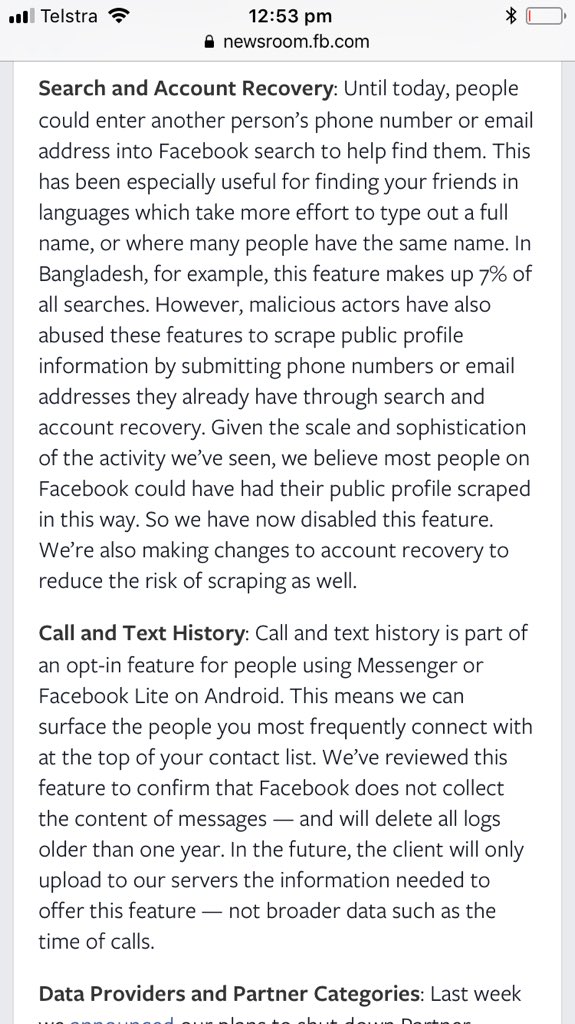
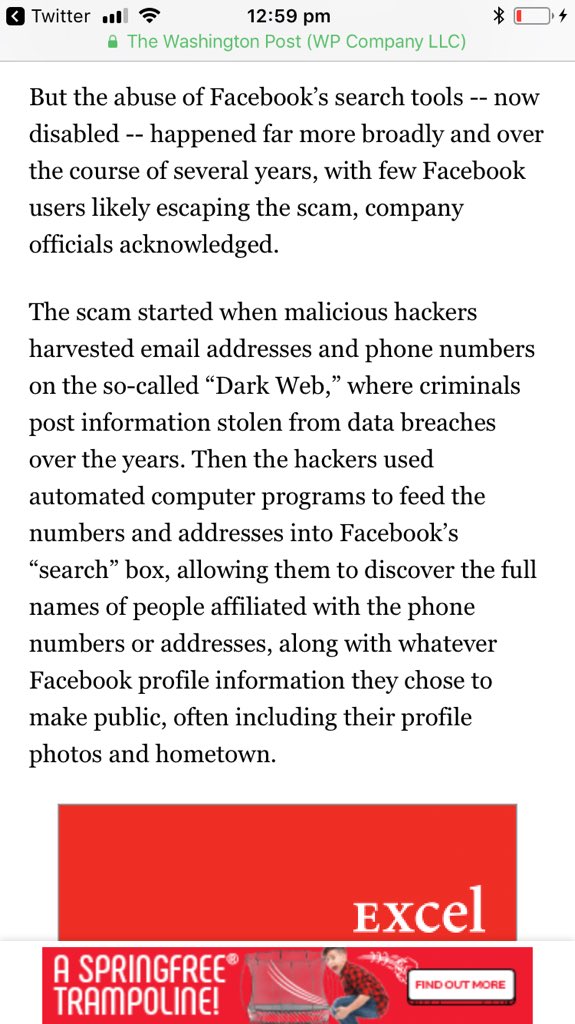
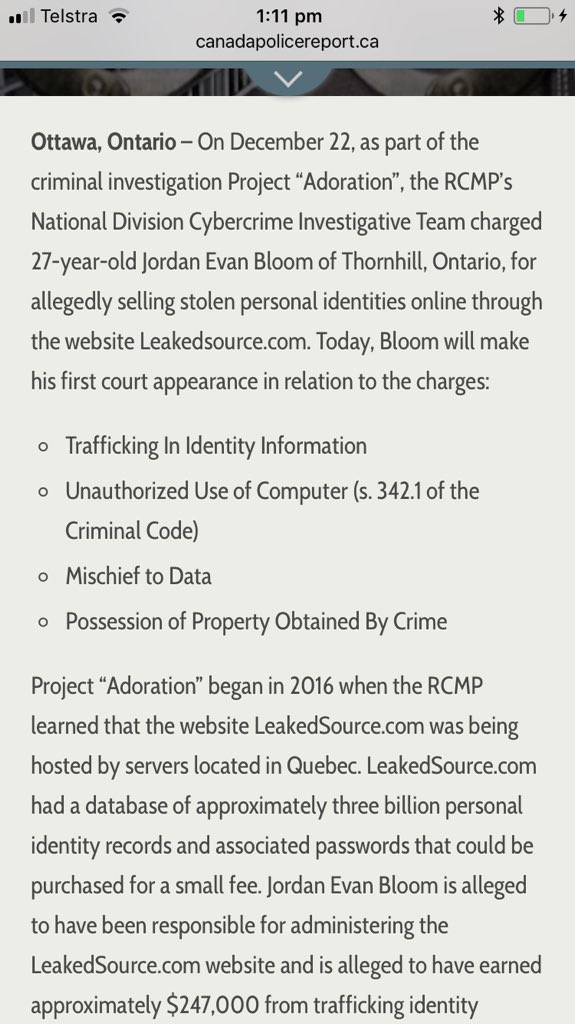
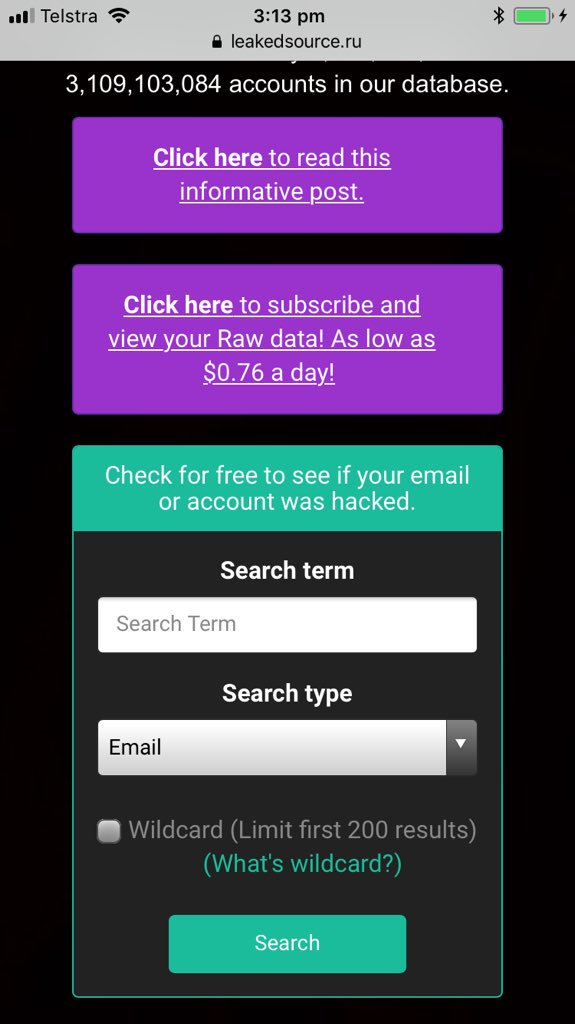
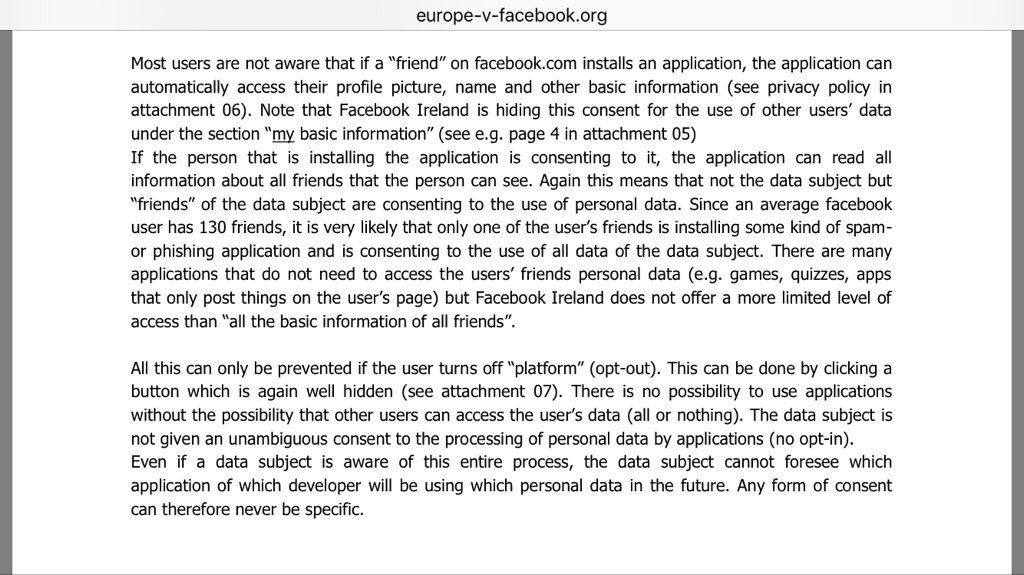
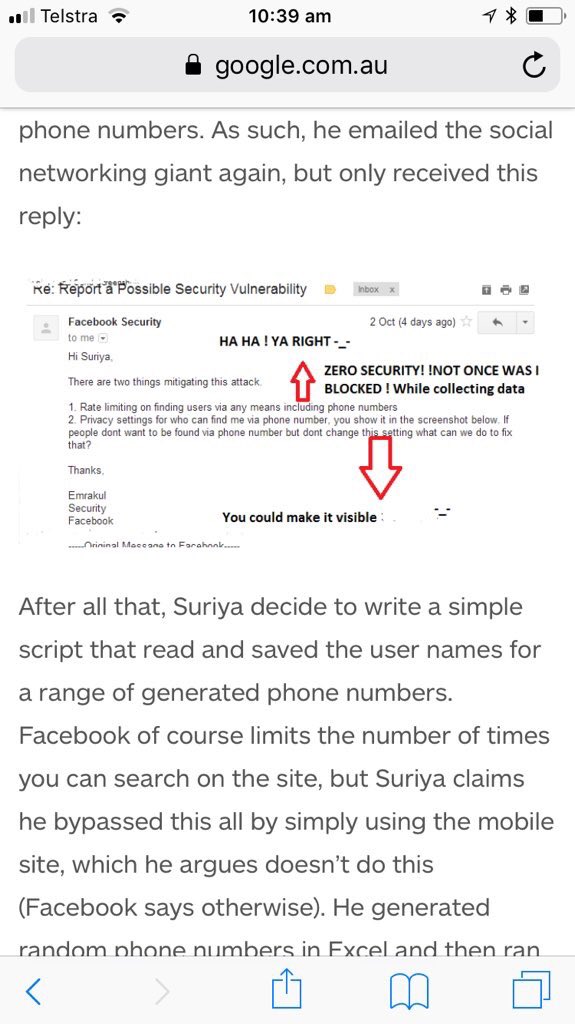
FB was warned about email/ph search tool by Prakash & Borland 2012, Copley & Haselton 2013 & Moaiandin 2015. All users were scraped.
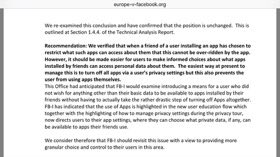
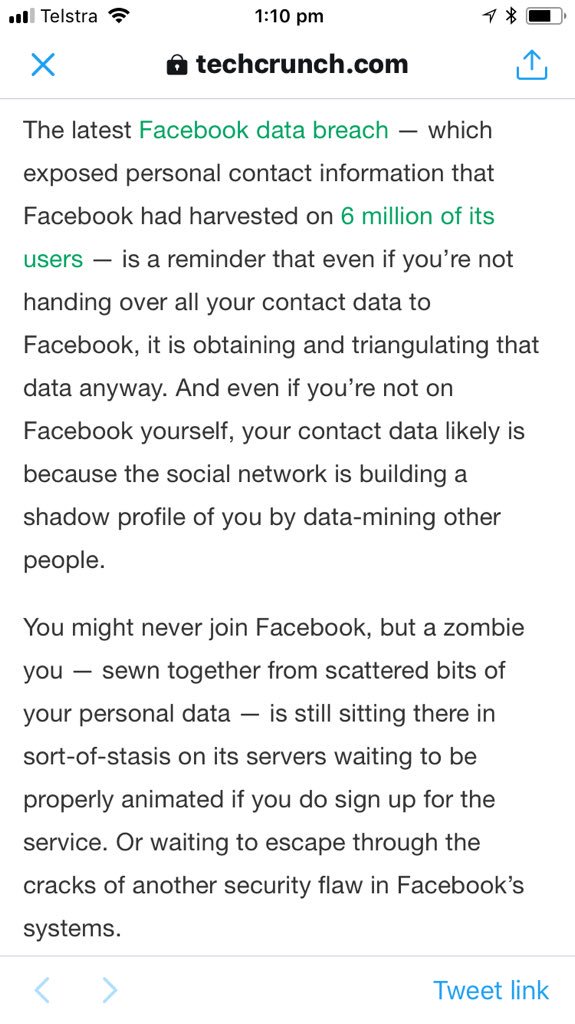
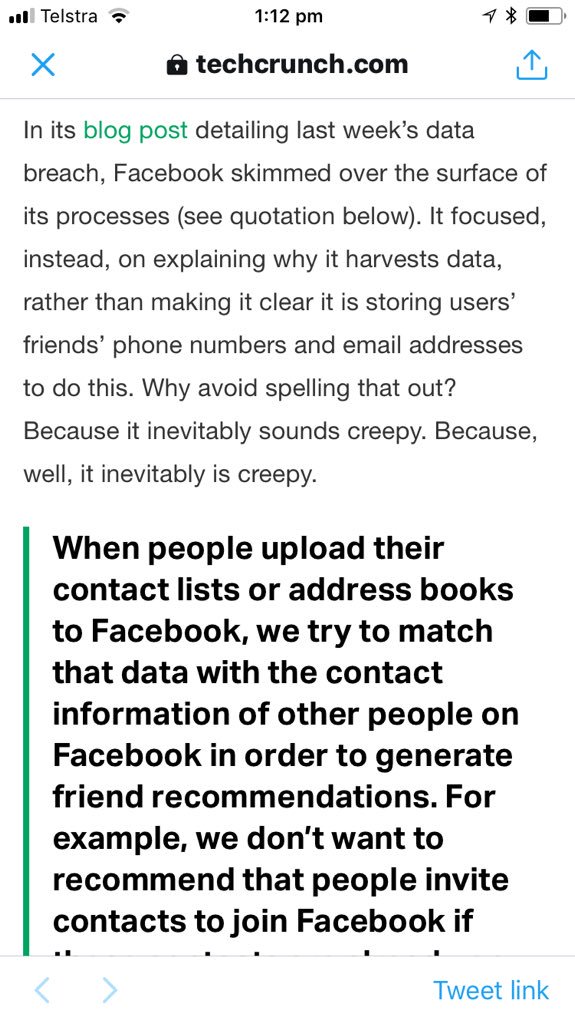
Zuckerberg: “in general we collect data on people who have not signed up for Facebook for security purposes to prevent the kind of scraping you were just referring to [reverse searches based on public info like phone numbers].”
finance.yahoo.com/news/zuckerber…
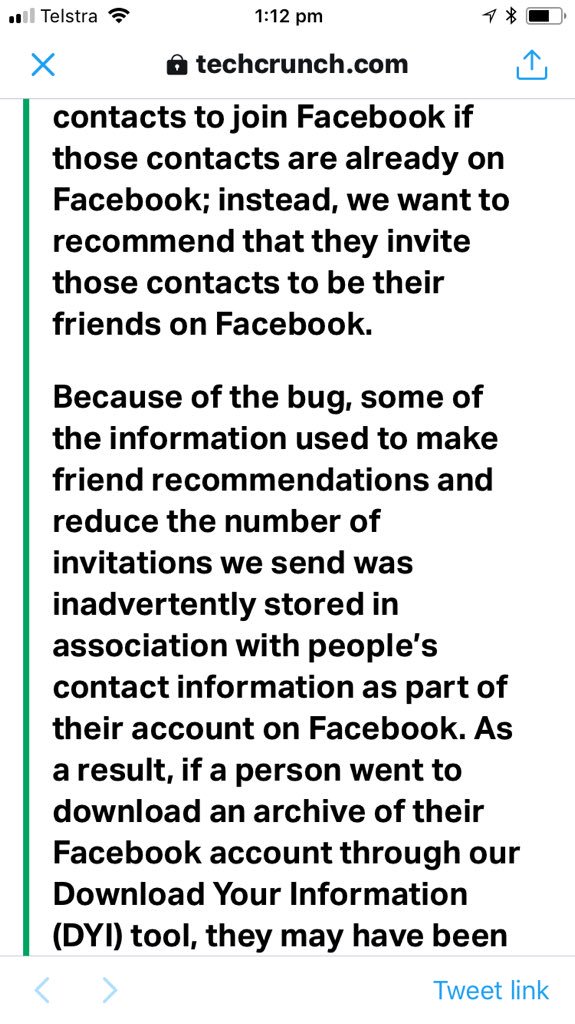
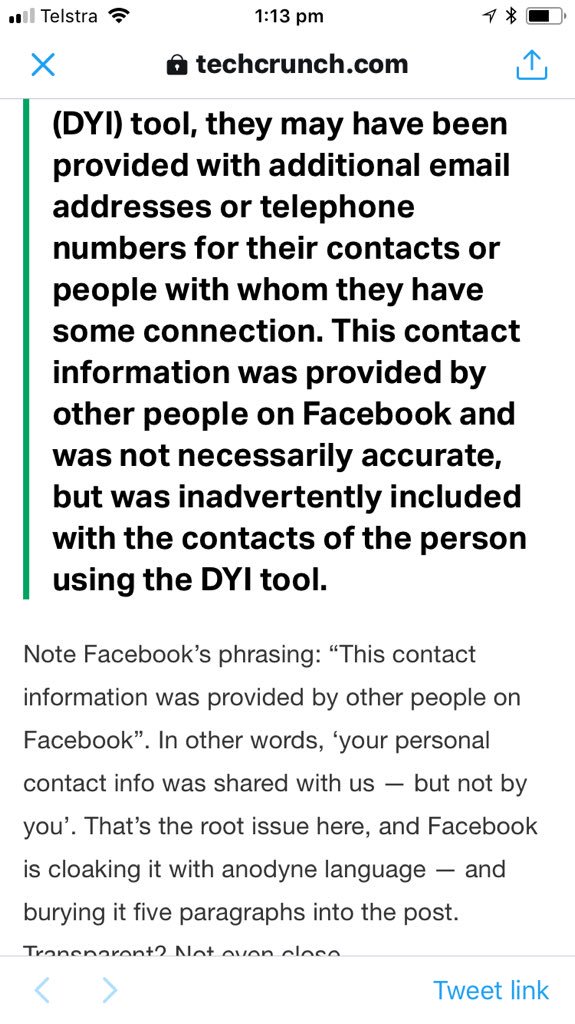
wired.com/story/cambridg…
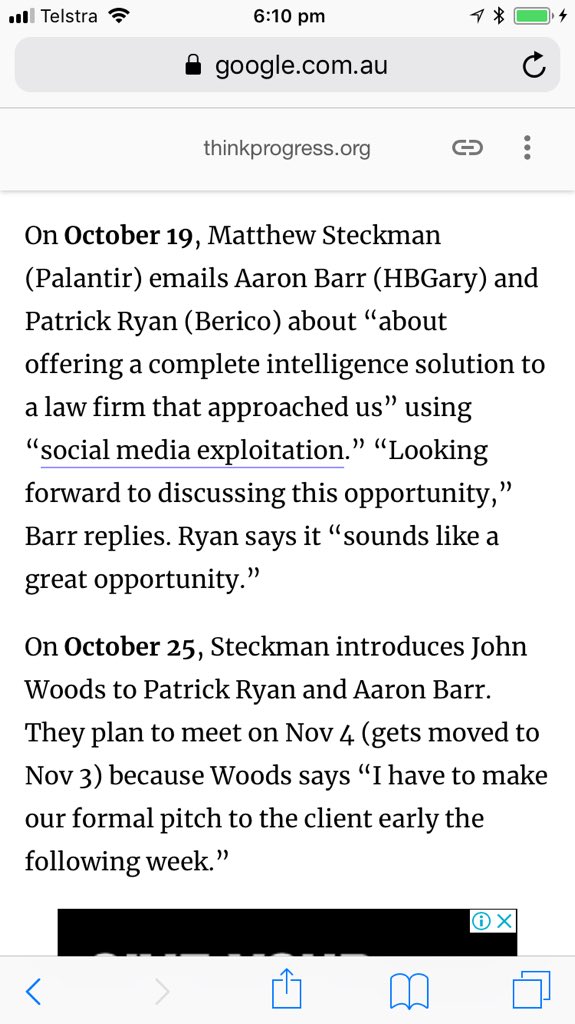
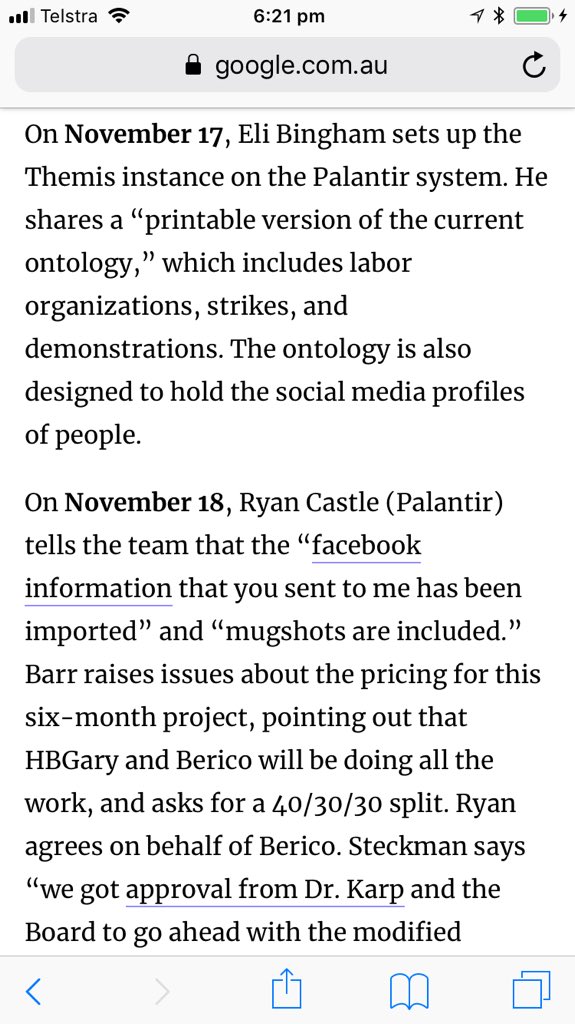
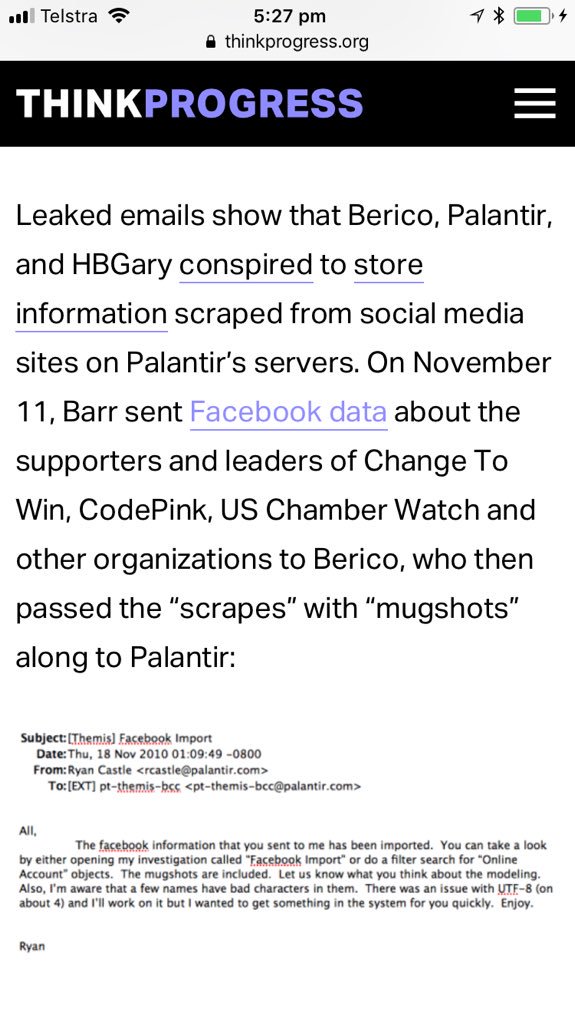
“ChamberLeaks: Pro-Chamber Conspiracy Illicitly Scraped Facebook“ ThinkProgress, Feb 14, 2011
thinkprogress.org/chamberleaks-p…
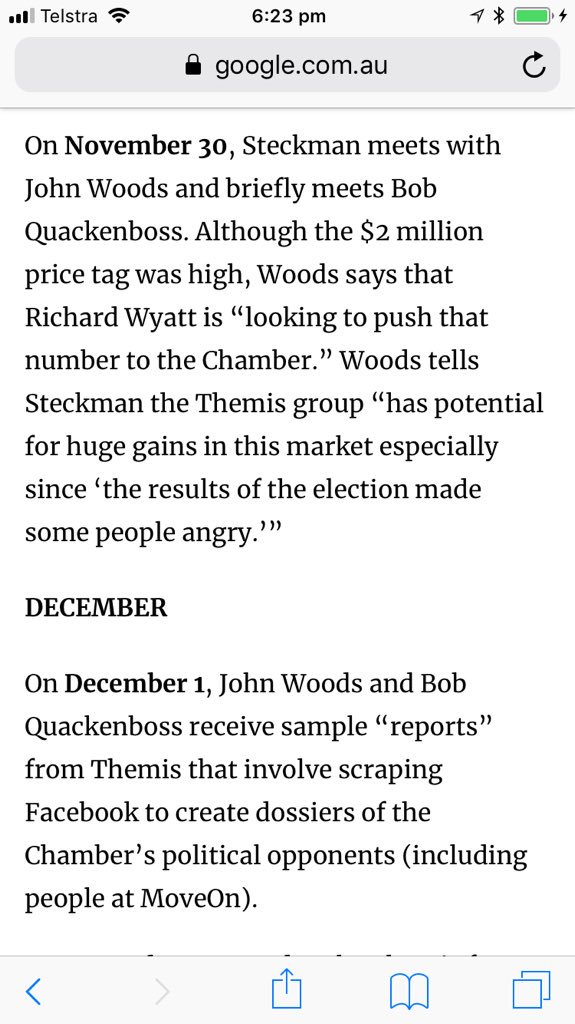
“ChamberLeaks Timeline”
ThinkProgress, Feb 16, 2011
thinkprogress.org/chamberleaks-t…