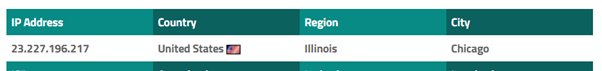
a) 176.31.112.10 (France) - a defunct IP address blown as APT28 in 2015 and pretty much a billboard saying RUSSIA!! RUSSIA!! rather than covert
b) 130.255.184.196-Germany;
c) 45.32.129.185 in San Jose CA (Choopa LLC). I can't help but wonder if this is the "Arizona" server.
In any event, none of three hard-coded addresses on Apr 28 were in Illinois.