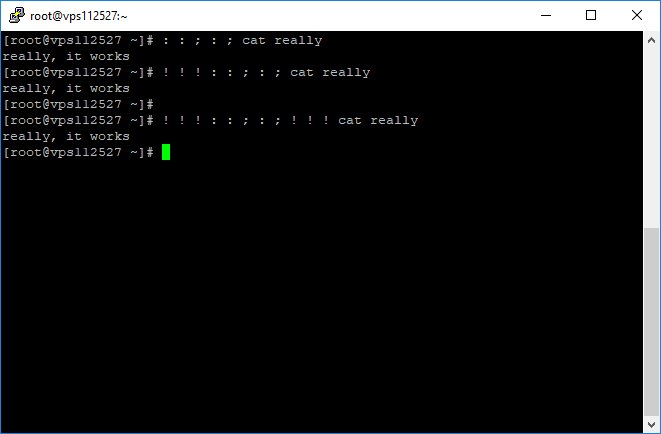
goal: obfuscate /etc/passwd
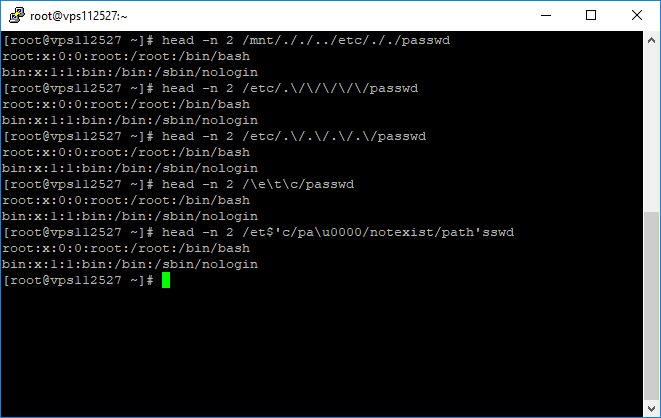
1) #directorytraversal: /mnt/././../etc/././passwd
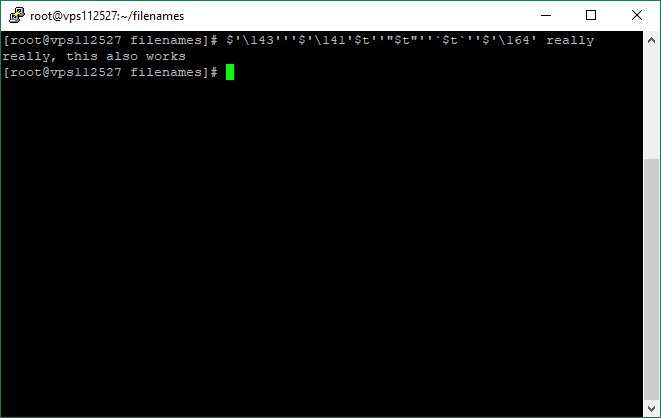
2) escape characher: /etc/.\/\/\/\/\/passwd /etc/.\/.\/.\/.\/passwd /\e\t\c/passwd
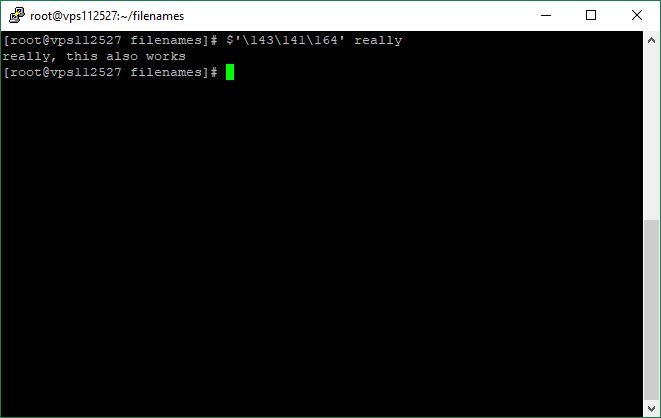
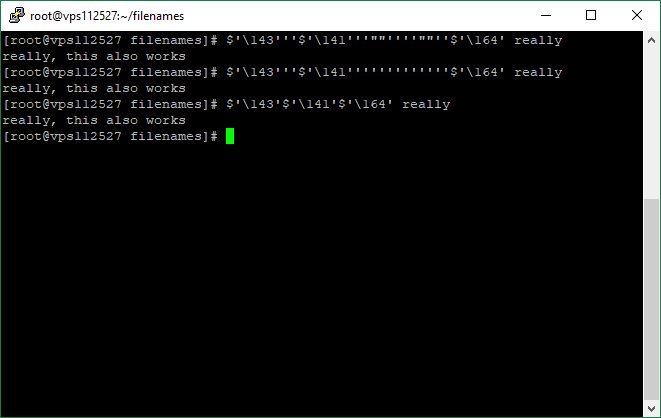
3) null character /et$'c/pa\u0000/notexist/path'sswd
....
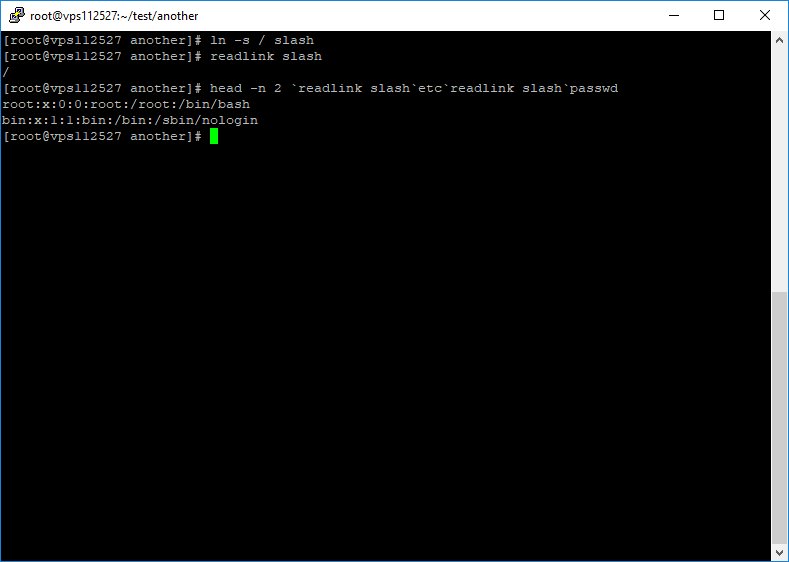
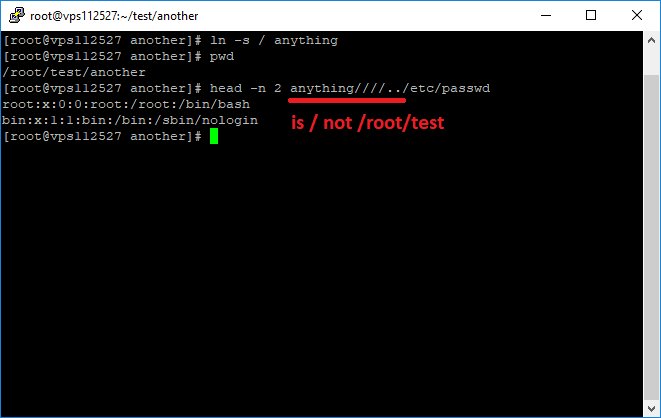
ln -s / anything
head -n 2 anything////../etc/passwd
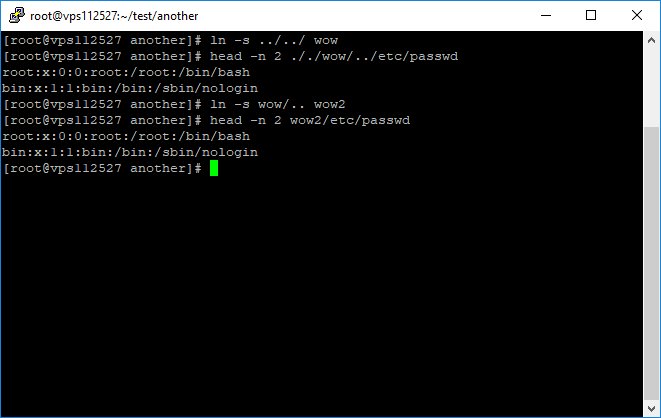
ln -s ../../ wow
head -n 2 ././wow/../etc/passwd
* ../ after a sym link applies to the sym link not the current path
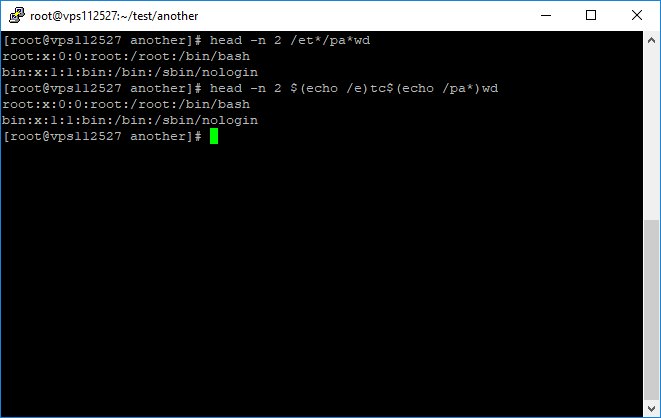
cat /et*/pa**wd
command expansion
$(echo /e)tc$(echo /pa*)wd
+ other string obfuscation techniques
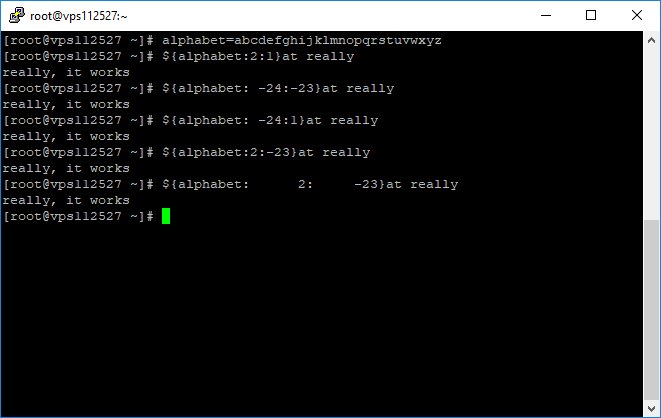
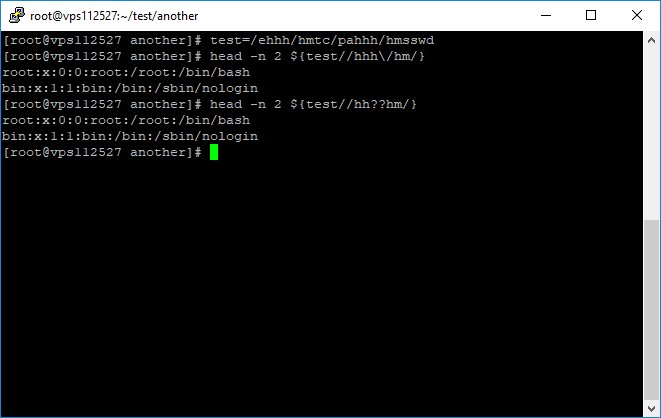
${var//pattern/string} --> Find and replace all occurrences of pattern in var by string
test=/ehhh/hmtc/pahhh/hmsswd
${test//hhh\/hm/}
${test//hh??hm/}
are equal to /etc/passwd
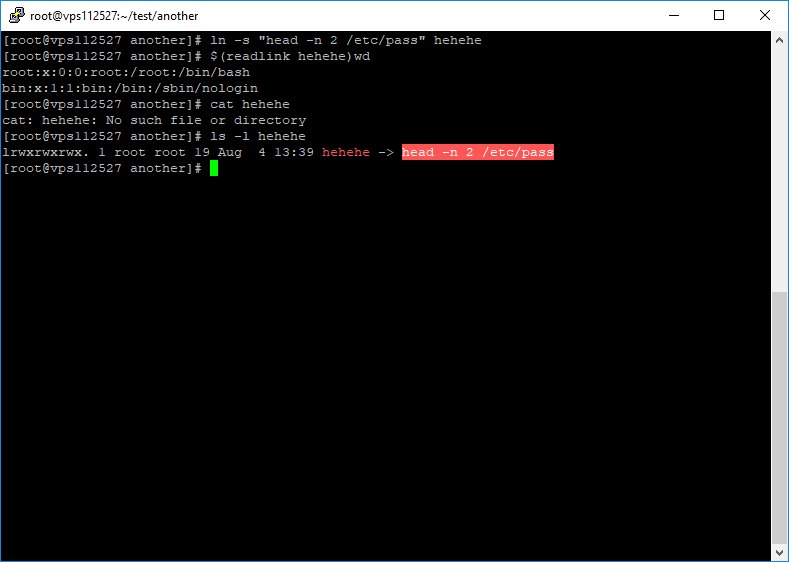
You can read the file path referred to by a soft link with #readlink command.
Note: soft link is a special file that its content is supposed to be a path. But one can store anything there!
#command #obfuscation #bash