(thread 🧵 1/10)
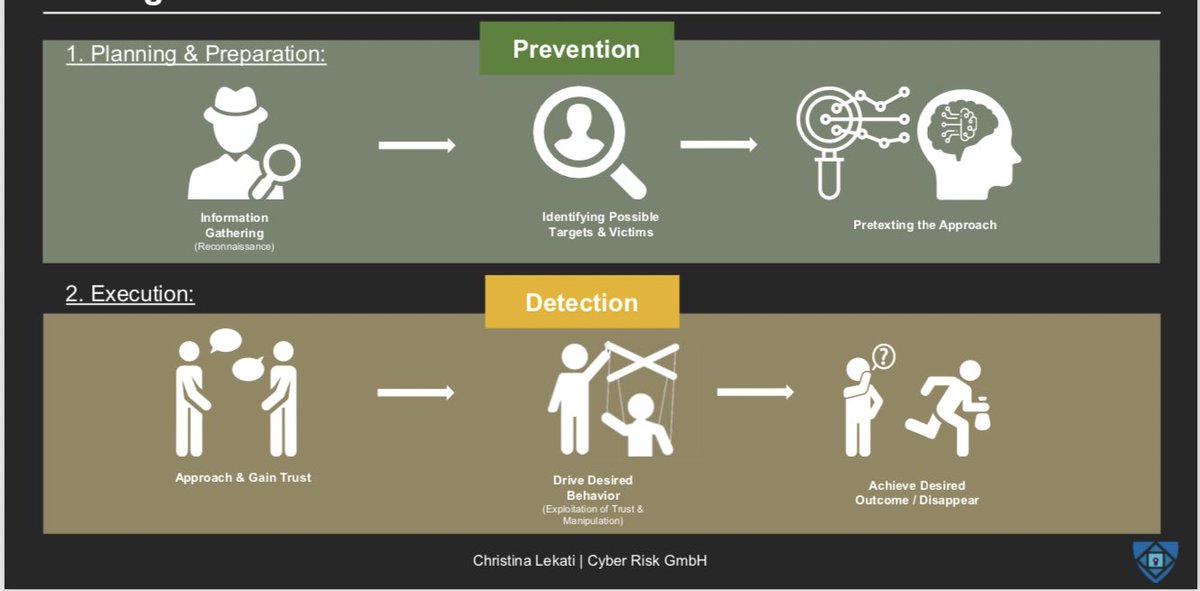
🔸SEs gather information & plan the attack scenario/seek entry points.
To prevent them,defenders can:
🔹Seek to understand their public information exposure & its potential consequences(eg. by conducting an OSINT investigation on their org)in order to manage it
2/10
3/10
4/10
5/10
🔷At this point, defenders should have already been trained to recognize the most common traits of a SE attack, in order to:
a) detect it
b) subtly verify their suspicion
c) thwart the attack
6/10
- training
- attack simulations
But detection is not enough. They need to know how to respond and then...
7/10
8/10
9/10
10/10









