Learn...
Reverse Engineering:
github.com/tylerha97/awes…
Reverse Engineering Malware:
malwareunicorn.org/workshops/re10…
malwareunicorn.org/workshops/re10…
Web Hacking:
portswigger.net/web-security
github.com/infoslack/awes…
Exploit Development:
github.com/FabioBaroni/aw…
azeria-labs.com/advanced-persi…
Arm Assembly:
azeria-labs.com/writing-arm-as…
Arm32 Shellcoding:
azeria-labs.com/writing-arm-sh…
azeria-labs.com/tcp-reverse-sh…
Heap Exploitaiton:
azeria-labs.com/heap-exploit-d…
azeria-labs.com/heap-overflows…
azeria-labs.com/grooming-the-i…
The Paradox of Choice: azeria-labs.com/paradox-of-cho…
The Process of Mastering a Skill:
azeria-labs.com/the-process-of…
Deep Work: azeria-labs.com/the-importance…
Windows exploit development by @corelanc0d3r: corelan.be/index.php/arti… and by @FuzzySec: fuzzysecurity.com/tutorials.html
And the ultimate resource list: github.com/Hack-with-Gith…
Part 1: blog.mindedsecurity.com/2018/09/pentes…
Part 2: blog.mindedsecurity.com/2018/10/pentes…
Books and resources: github.com/V33RU/IoTSecur…
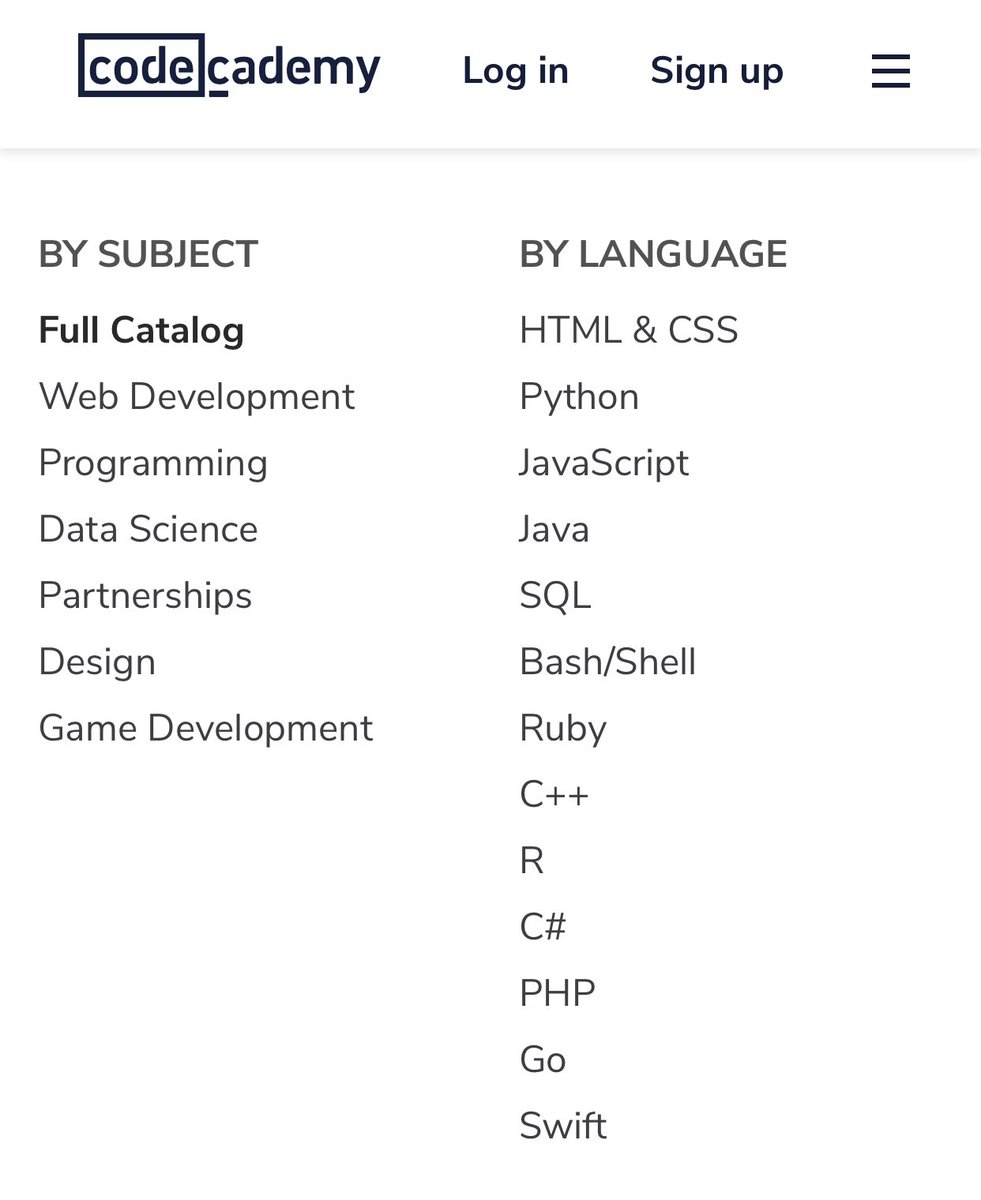
Once you went through the above, you can start pwning boxes on Hack The Box. It’s like OSCP but free! hackthebox.eu
codecademy.com/catalog/subjec…