
At present, every one of these chips appears to be completely broken.
Have I got a headline for you. motherboard.vice.com/amp/en_us/arti…
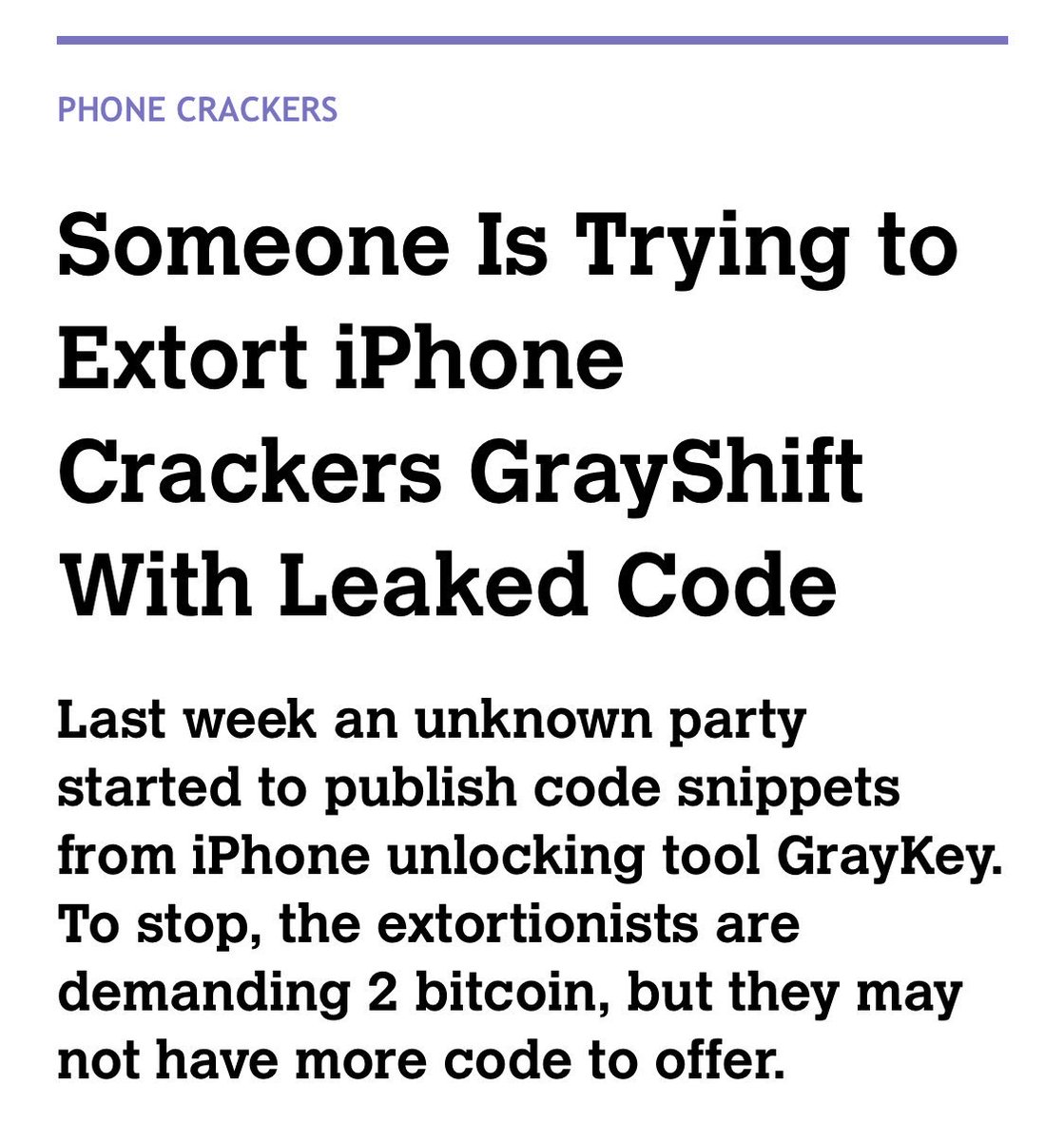
This technology is broken ✅
The break is comically accessible even by random criminals, not sophisticated nation state attackers ✅








