
The #1 trusted source for cybersecurity news, insights, and analysis — built for defenders and trusted by decision-makers.
7 subscribers
How to get URL link on X (Twitter) App



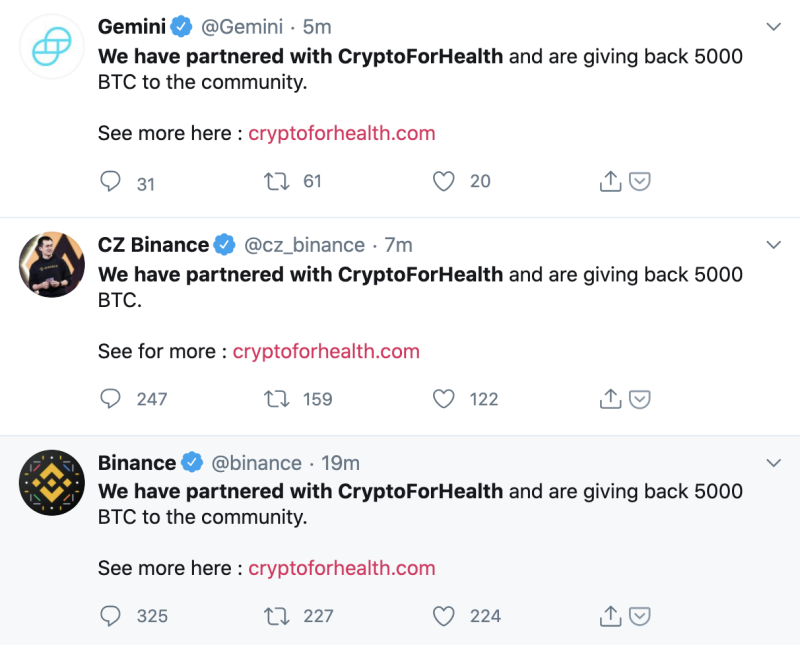
 Elon Musk's account has also been compromised, tweeting a similar cryptocurrency scam.
Elon Musk's account has also been compromised, tweeting a similar cryptocurrency scam.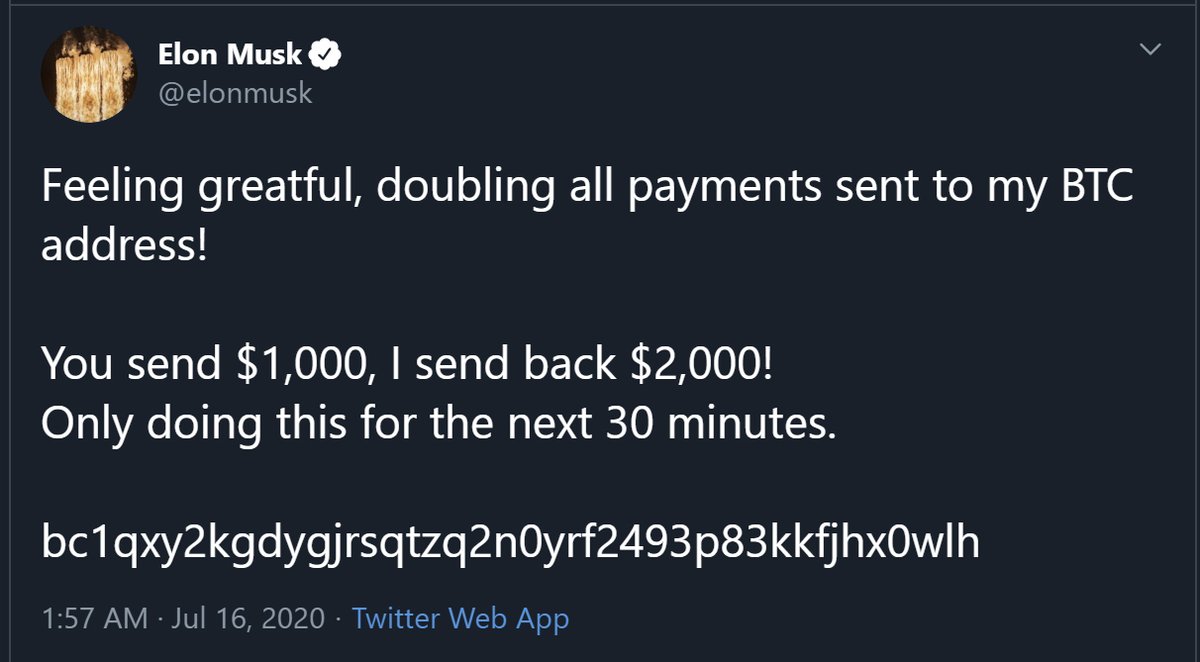

 Researchers confirm the new #Windows vulnerability, dubbed 'SigRed,' is a wormable bug, allowing attackers to launch #malware attacks that can spread from one vulnerable computer to another without any human interaction.
Researchers confirm the new #Windows vulnerability, dubbed 'SigRed,' is a wormable bug, allowing attackers to launch #malware attacks that can spread from one vulnerable computer to another without any human interaction.
 @Swati_THN 1) #Phishing Attacks:
@Swati_THN 1) #Phishing Attacks: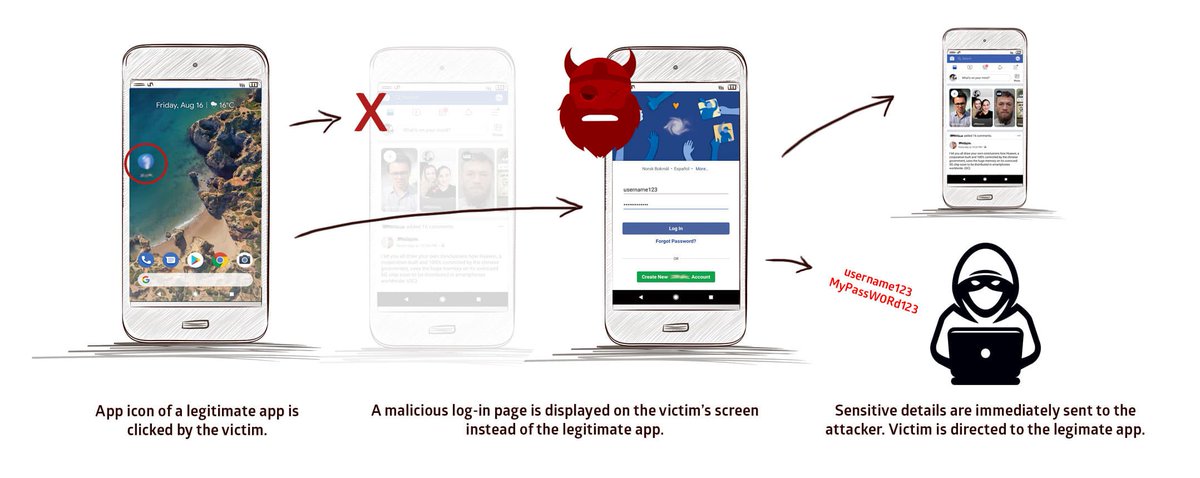
 Starting with Windows 10 1803 and #Windows Server 2019, this flaw exists when login over #RDP requires the clients to authenticate with Network Level Authentication, an option that #Microsoft recently recommended as a workaround against the critical #BlueKeep RDP vulnerability.
Starting with Windows 10 1803 and #Windows Server 2019, this flaw exists when login over #RDP requires the clients to authenticate with Network Level Authentication, an option that #Microsoft recently recommended as a workaround against the critical #BlueKeep RDP vulnerability.
