It's time to spread the word!
Alternatively, if you don't have access to ACM, you can get the archived version at secret.inf.ufpr.br/papers/marcus_…
Before starting, a little bit of history! Brazilian banks were
computerized very early, which makes our scenario to present a myriad of threats. We should had learned from them.
Ofc, a banking malware collecting user's data.




of libraries despite presenting almost the same features.






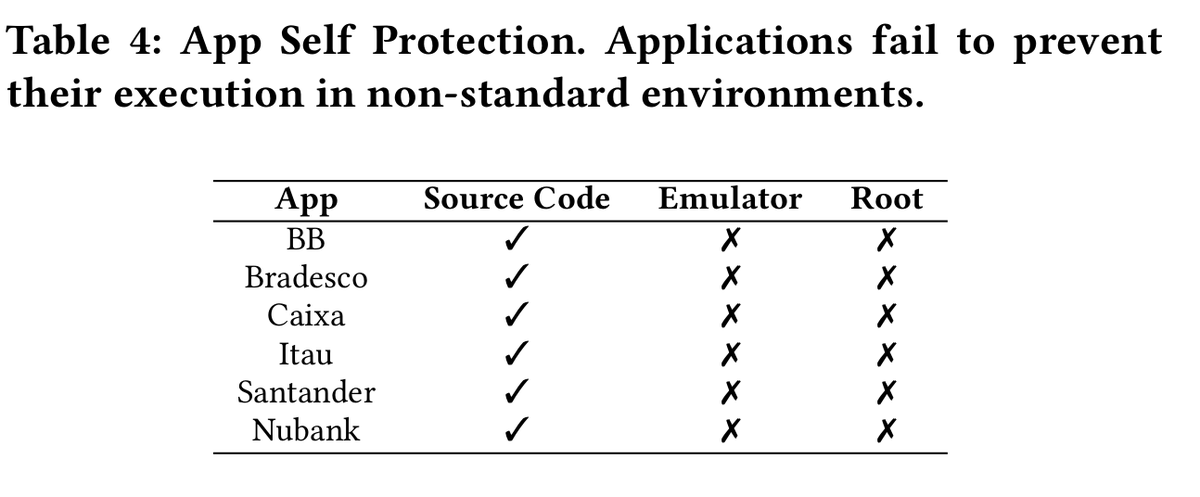







good idea.






overlays) in their own apps, they completely lost control when outsourcing operations to third-parties.
@santander_br and @bradesco never answered me requesting a report; @BB, @Itau, and @Caixa requested the report but didn't answer me back.
making these attacks practical (e.g., an open WiFi network asking users to install the attackers certificate)