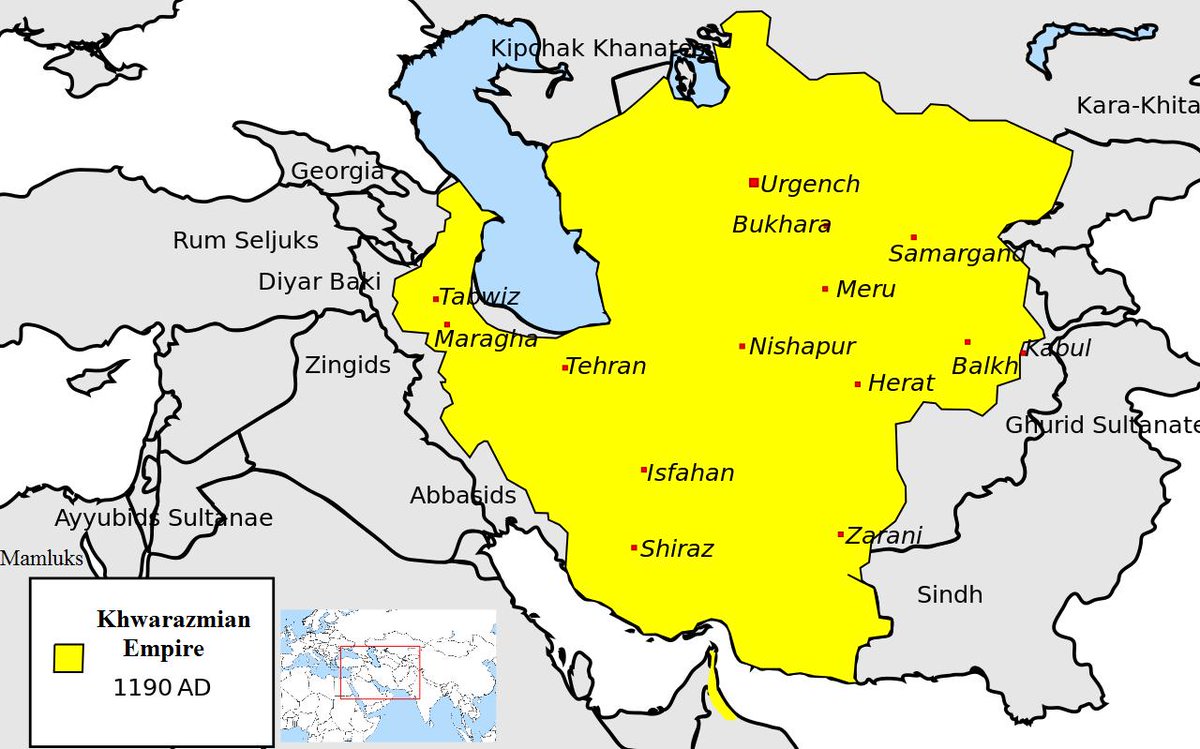
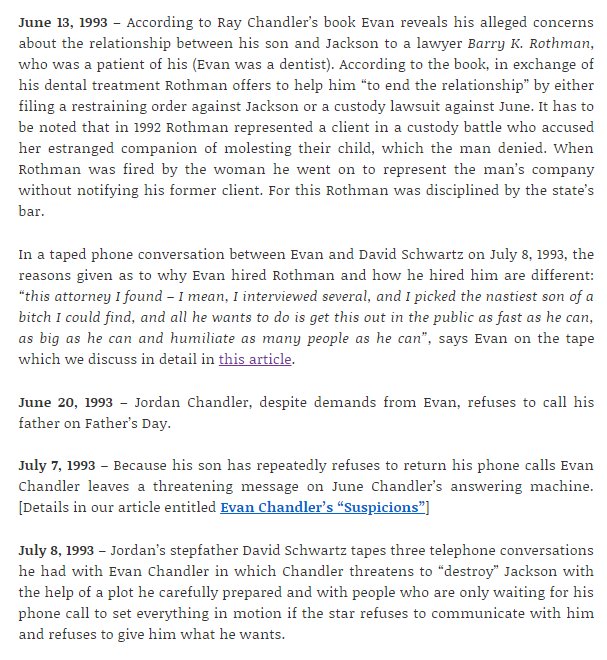
I was recently privy to a conversation in which some really smart people in security shared their favorite papers or articles. Security engineering, like other disciplines, has a rich history worth learning from.
I'm going to list some of these papers in this thread.
It's hard to emphasize just how revolutionary the concept of public key cryptography is. This paper started it all, introducing D-H key agreement and digital signatures.
ee.stanford.edu/~hellman/publi…
This paper succinctly describes the concept that it's not enough to trust software, you also need to trust the software that compiles the software, and the software that compiles the compiler, and so on
archive.ece.cmu.edu/~ganger/712.fa…
Another security paper that explores the reasons why good encryption software can be insufficient in the face of physical attacks.
jhalderm.com/pub/papers/col…
A data-driven study of how well/poorly user interfaces express security features to users in web browsers.
dl.acm.org/citation.cfm?i…
A comedic article that helps emphasize the difference between targeted attacks by well-resourced adversaries and the more pedestrian threats faced by the general populace.
usenix.org/system/files/1…
A new attack methodology that revolutionized offensive security.
seclists.org/bugtraq/1997/A…
Still one of the most pervasive security issues, format string vulnerabilities demonstrate the dangers of mixing abstractions.
forum.ouah.org/FormatString.P…
This paper introduces the idea of a ceremony as a generalization of a security protocol, formalizing the often overlooked human element.
eprint.iacr.org/2007/399.pdf
An exploration of the adversarial models needed to build secure software.
cl.cam.ac.uk/~rja14/Papers/…
This paper introduces The Update Framework (TUF) for secure software updates.
justinsamuel.com/papers/surviva…
The first of many papers exploring some of the subtle risks of elliptic curve cryptography.
iacr.org/archive/pkc200…
A retrospective of a popular mail transfer agent by the author with best practices learned.
cr.yp.to/qmail/qmailsec…
A revealing field study about security, privacy and surveillance.
simplysecure.org/resources/tech…
A series of works derived from the Midori advanced development OS project.
microsoft.com/en-us/research…