
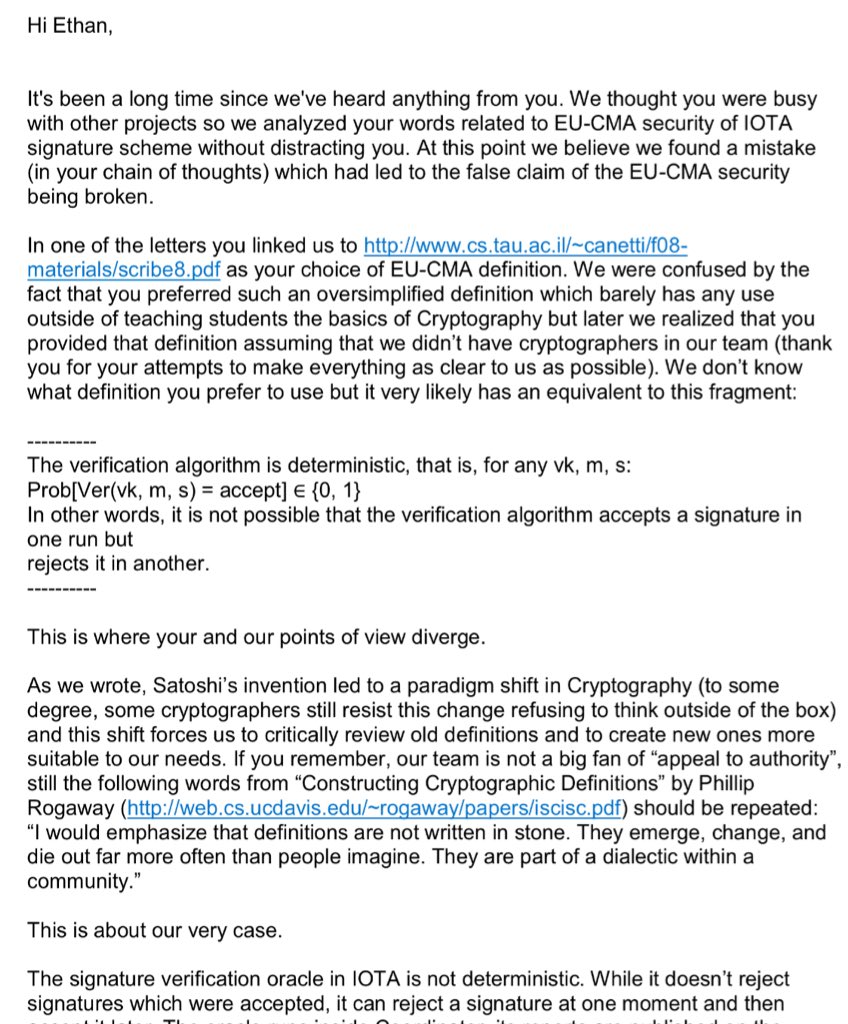







1. The researchers demonstrated a break in the formal EU-CMA security of the scheme (unless you make up your own definition.)
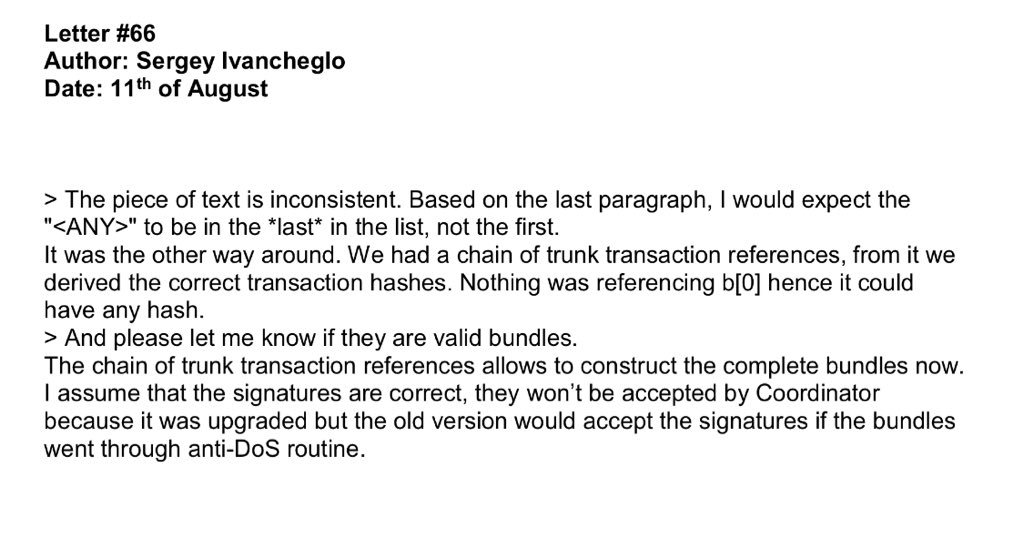
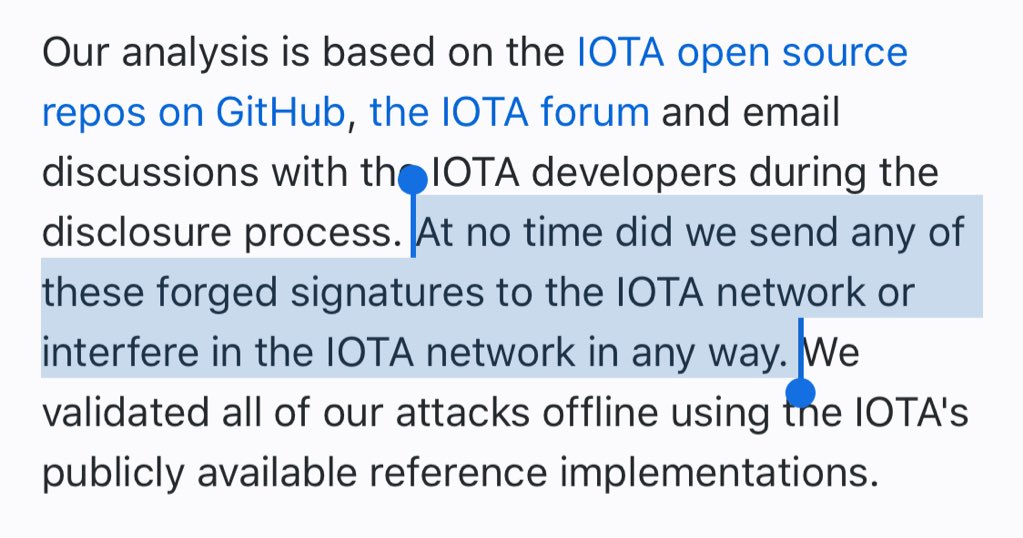
2. The Iota devs confirm that they provided syntactically valid bundles (at significant time investment!)

So I am genuinely grateful you made me invest the time!


















