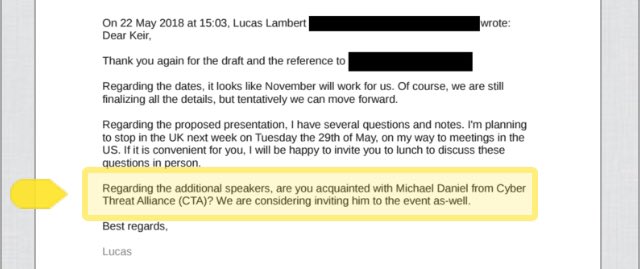
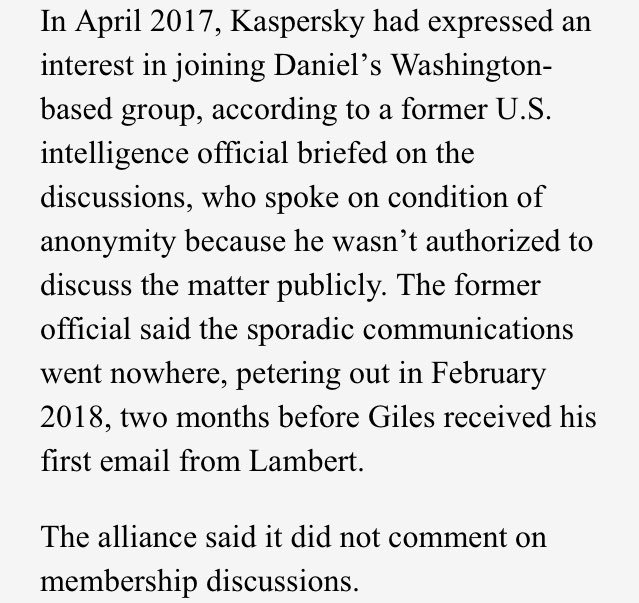
Do these addresses look familiar? Search for "dailyforeignnews" and "dernyalzongy" to see where else addresses have come up ...
His Twitter account does not appear particularly active.
facebook.com/profile.php?id…

webcache.googleusercontent.com/search?q=cache…
Archive of the Google cache:
web.archive.org/web/2018071323…
He gives his hometown as "London"