I'm going into this presentation blind, I haven't read this yet, but it's in response to a thread rebutting blog.benpri.me/2019/01/13/why…

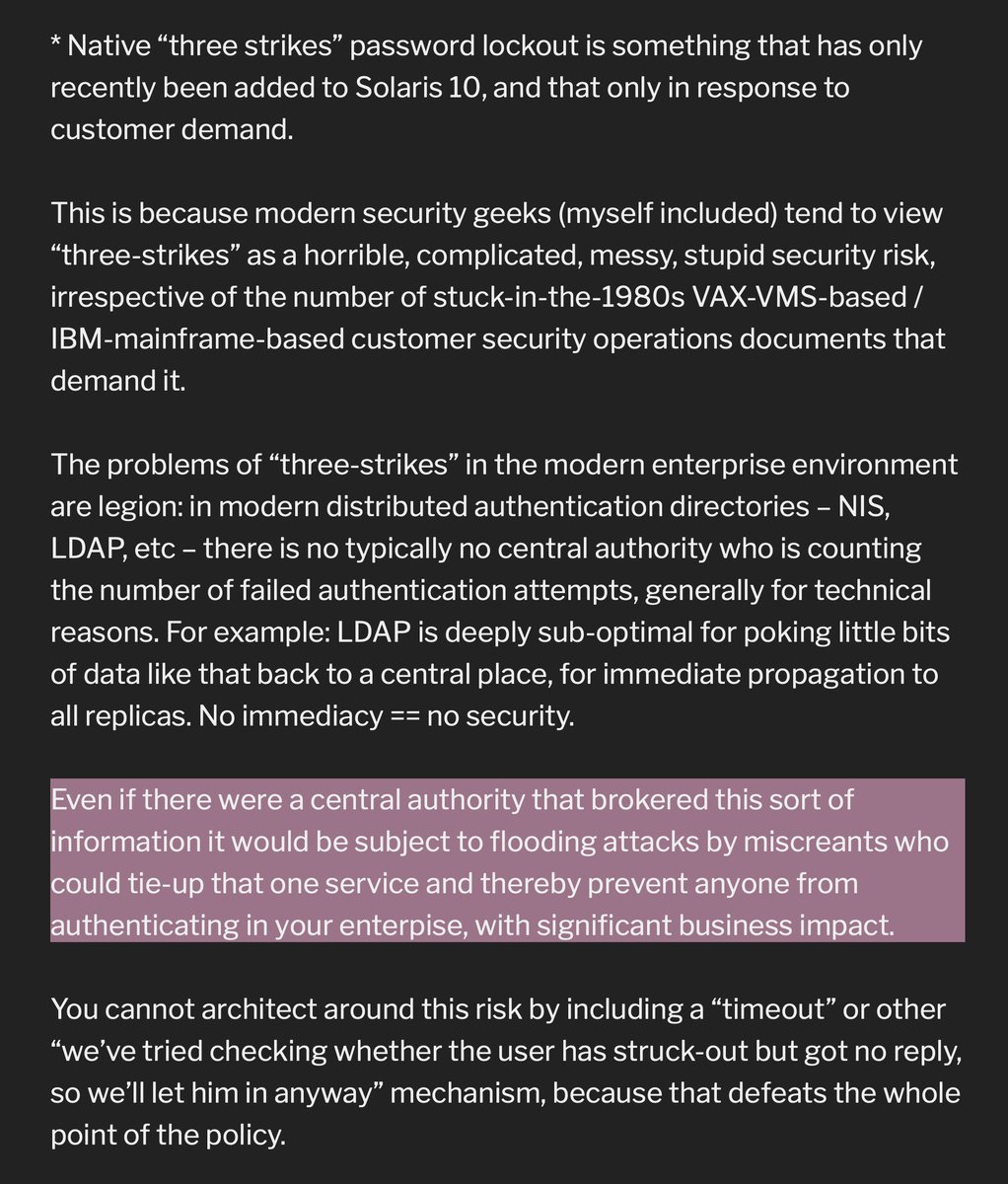
- strong hashing enables shorter passwords
- shorter passwords are bad
- therefore strong hashing is bad

Notably: password cracking requires you to have the hashes to work on. (cont)
$ ypcat passwd
...and get a dump of all the crypt() hashes; now you have to pop a site and exfil the user database, crack it offline, and try replaying 1/more successful breaks at 1/more sites where the credentials might be valid.
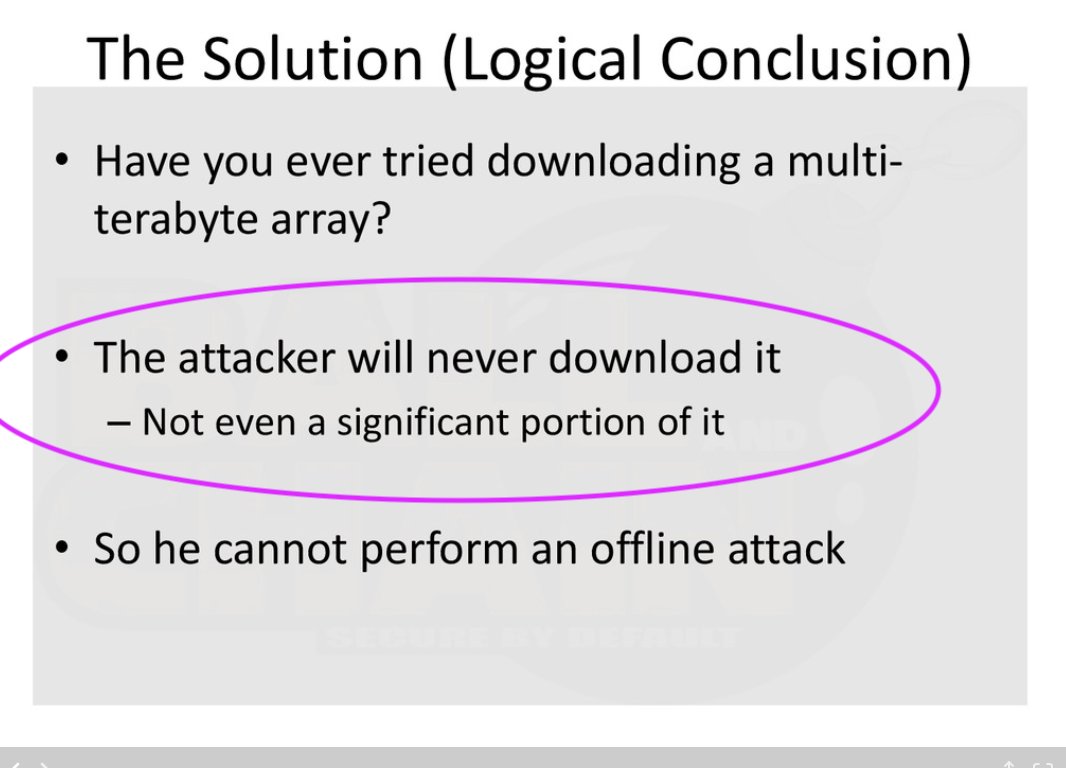
NOBODY IS TELLING ME HOW TO SECURE THIS 2TB FILE, OR WHAT I WILL DO WHEN THE SPINDLE DIES
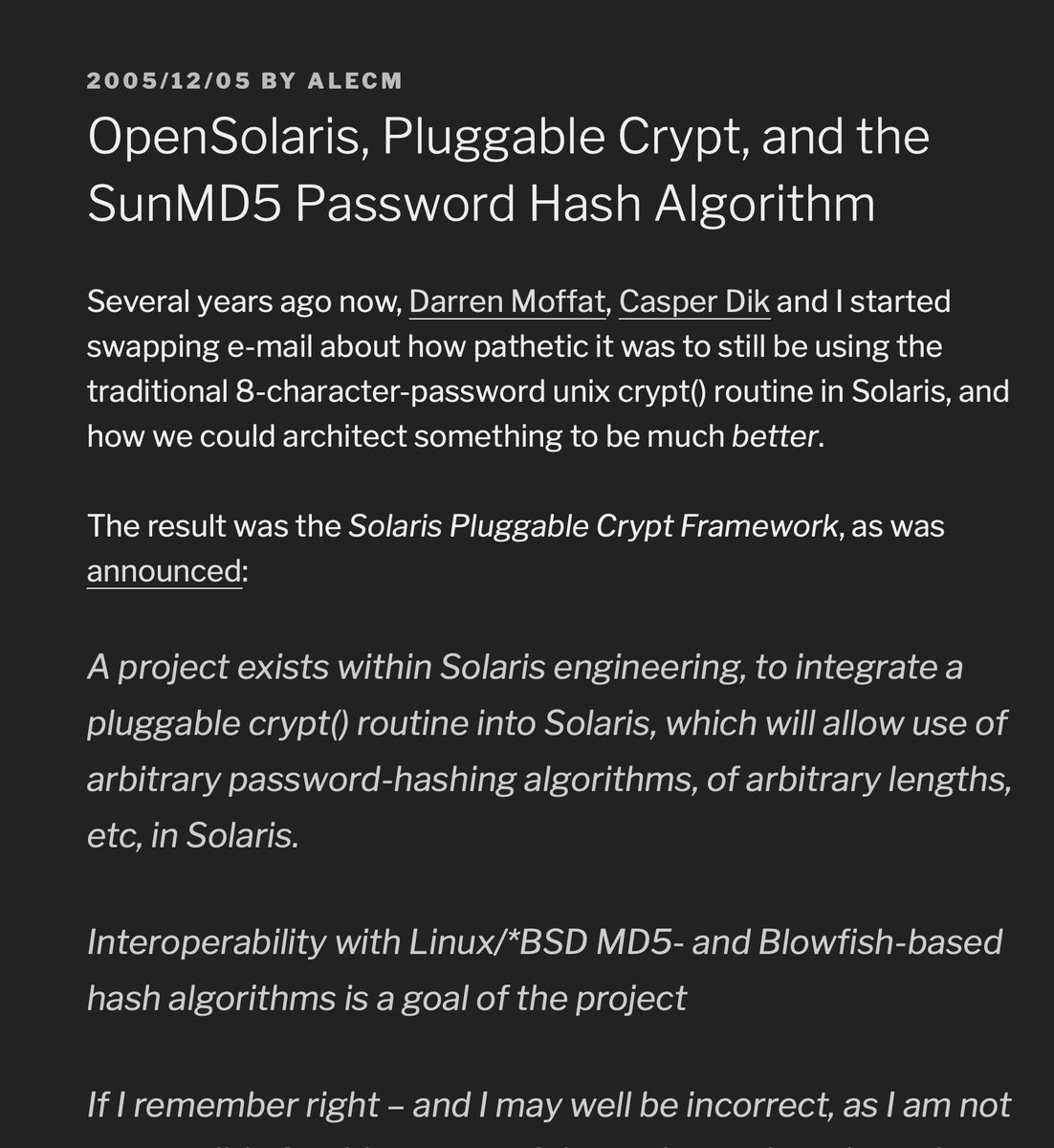
Except it's machine-specific. Which you could replicate in scrypt() by using pluggable-crypt / similar site-local salt
<thinks: "…I wonder if this author has considered using words like `sharding`">
It will not work in distributed environments, it will choke on bandwidth, it will raise operational risk (ie: death of 1 spindle = death of authentication; shard the data and you shard the risk)