And what it says is horrifying.
For an awesome lecture on DLP and its applications, check this out:
1.) Ephemeral Diffie-Hellman
2.) Elliptic Curve Cryptography
The benefits of Diffie-Hellman are that it's relatively easy to setup and usually pretty light on communication.
en.wikipedia.org/wiki/Diffie%E2…
But we still have the ID problem...
tls.mbed.org/kb/cryptograph…
For SSH/TLS, the common PKI used for identity is something called ECC
Again these are the components used to identify you're talking to your bank when you login.
That's fucking terrifying.
There's an algorithm called Shor's Algorithm that Quantum Computers can run that allows them to calculate discrete logs orders of magnitudes faster than normal computers.
For more on Shor's and other QC, see: hashicorp.com/blog/quantum-s…
1.) It has so much computing power it sieved that key naturally (frightening)
2.) It has discovered advances in math for a classical discrete log (even scarier)
It's also probably why Monica ends up working at the NSA in the end. An AI that discovers advances in math is worth its weight in antimatter for crypto.
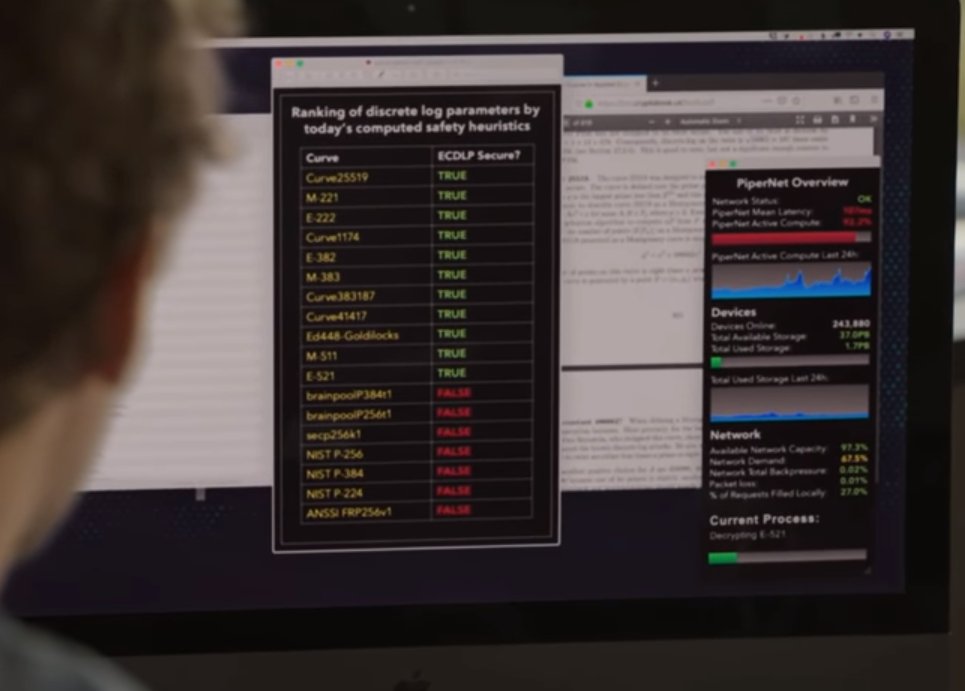
Throughout the screens showing ECDSA curve variants, Gilfoyle and Pipernet both trash NIST-standard cryptography.
csrc.nist.gov/publications/d…
Hell of an in joke, Silicon Valley.
ogryb.blogspot.com/2014/11/why-i-…
1.) Advances in other fields like AI have an impact on security
2.) The devil is in the details when it comes to securing crypto
10 yrs ago I worked at NetApp on what became Volume Level Encryption (aka: encrypt data at rest and deduplicate/compress it).
Some memories in this epp.
docs.netapp.com/ontap-9/index.…