Syrian-American cyberwarrior & military enthusiast | Find-Fix-Finish | NATO stan | Bayraktar & SIGINT enjoyer | #FreeSyria and #SlavaUkraini!
How to get URL link on X (Twitter) App





 Over the course of a week, I gradually introduced circular error into the GNSS readings, reducing it's accuracy to disrupt their work. At the end of it, both the sensor network and the base station were demolished, to prevent them from fixing the damage caused. 2/4
Over the course of a week, I gradually introduced circular error into the GNSS readings, reducing it's accuracy to disrupt their work. At the end of it, both the sensor network and the base station were demolished, to prevent them from fixing the damage caused. 2/4 




 At 17:00 local time, we assumed control over an @EnstoGroup #grid #automation #controller belonging to the DK Port substation. Timing was chosen to match peak usage hours. In addition to controlling power supply, it was supplying data for Rosenergo's FLISR fault #algorithm 2/4
At 17:00 local time, we assumed control over an @EnstoGroup #grid #automation #controller belonging to the DK Port substation. Timing was chosen to match peak usage hours. In addition to controlling power supply, it was supplying data for Rosenergo's FLISR fault #algorithm 2/4 







 We attacked their #SCADA/#ICS, demolishing 8 expensive Schneider M258s #PLC, w/2400 channels & 16 DOF each for complex machines. This led to a fire that erased an entire workshop building, and took 13 trucks to extinguish! According to locals the first 3 arrived without water😂2/
We attacked their #SCADA/#ICS, demolishing 8 expensive Schneider M258s #PLC, w/2400 channels & 16 DOF each for complex machines. This led to a fire that erased an entire workshop building, and took 13 trucks to extinguish! According to locals the first 3 arrived without water😂2/ 







 We penetrated devices both large and small; many of them were at the heart of #ISP DCs like Rostelecom or Kuban-Telecom, but many also belonged to individual businesses. All had high utilization rates, uptime, and were rich in features: these were all core infrastructure 2/
We penetrated devices both large and small; many of them were at the heart of #ISP DCs like Rostelecom or Kuban-Telecom, but many also belonged to individual businesses. All had high utilization rates, uptime, and were rich in features: these were all core infrastructure 2/ 





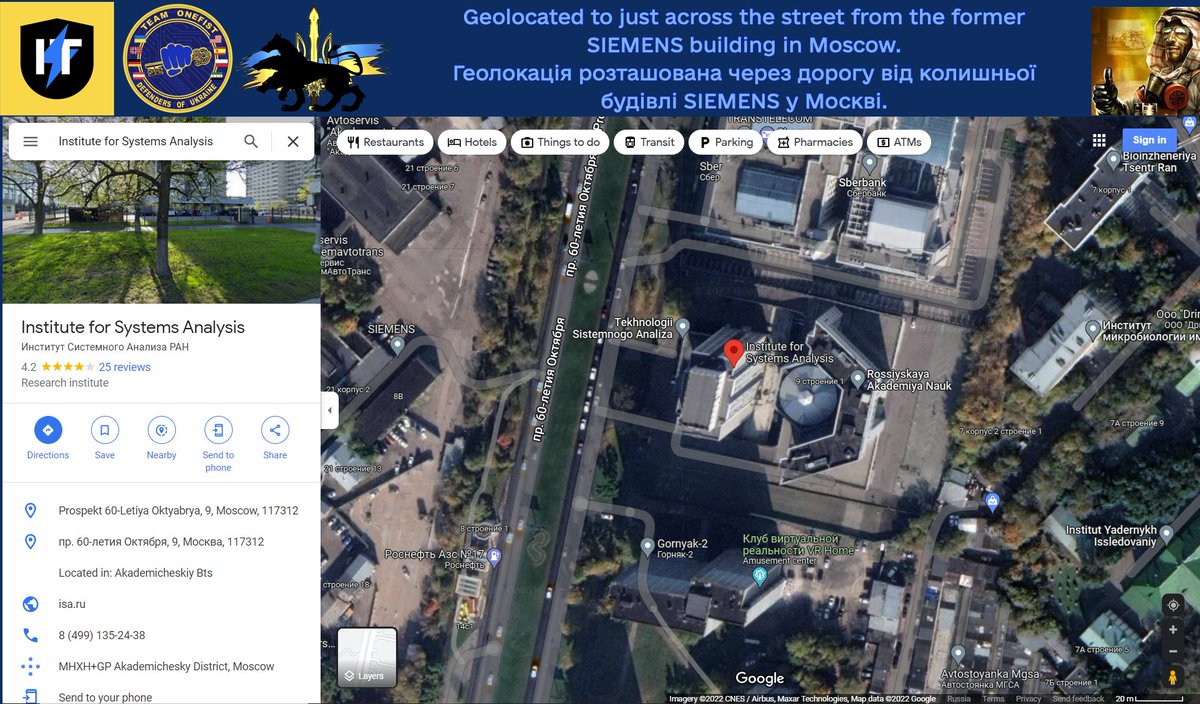
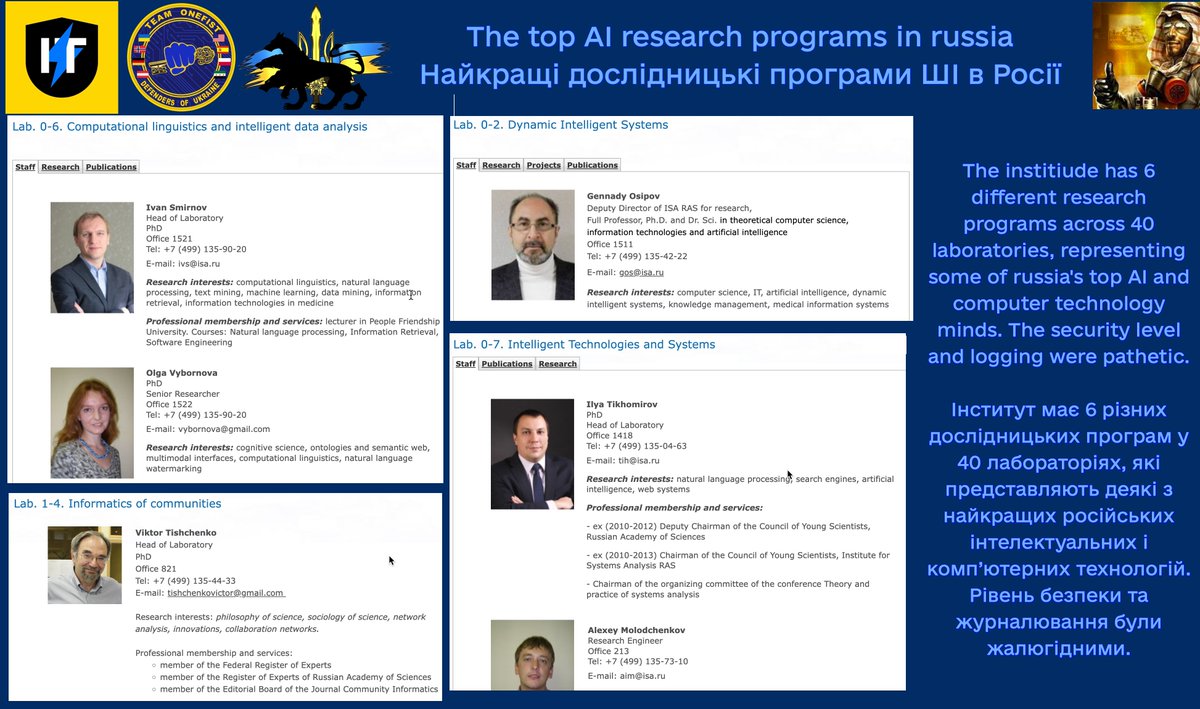
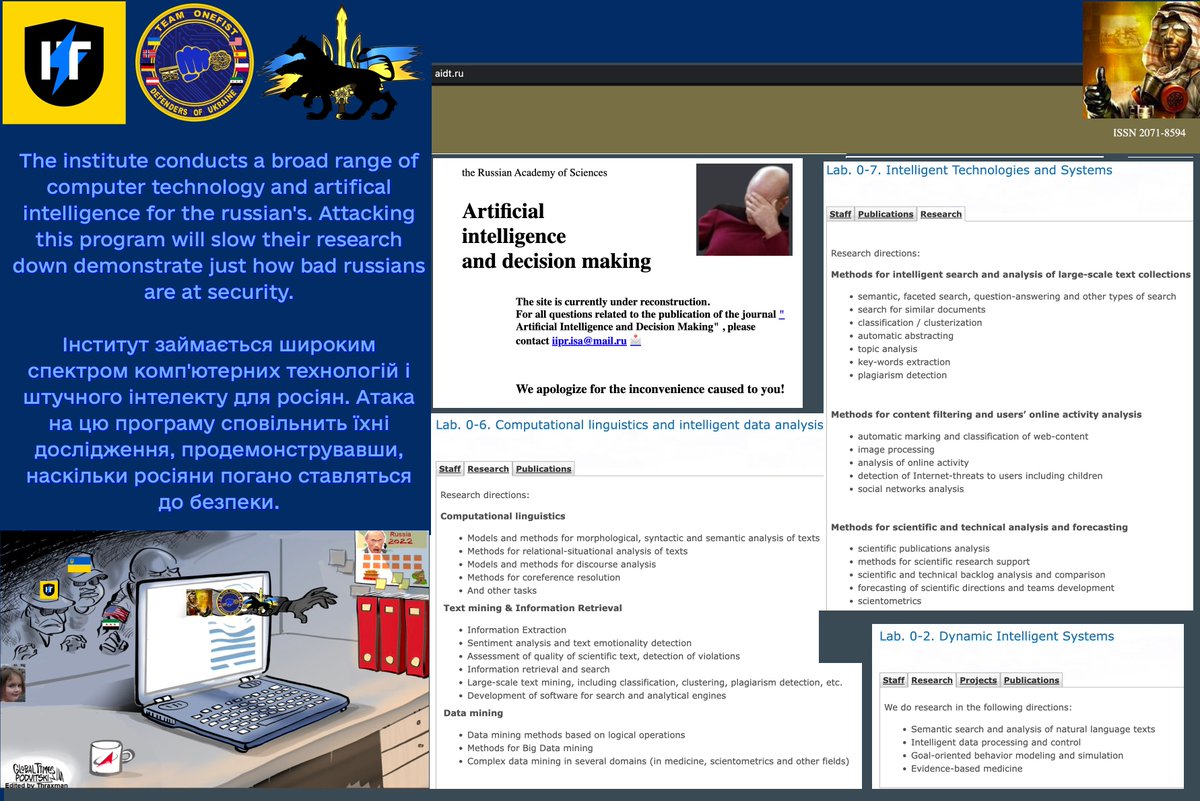 I penetrated this #Cisco switch, which we found to control their entire network: 9 research servers & 100+ devices. All without any #cybersecurity measures! Madness. Bricked it, demolishing their entire research environment; we also gave them a small "gift" from us. 2/
I penetrated this #Cisco switch, which we found to control their entire network: 9 research servers & 100+ devices. All without any #cybersecurity measures! Madness. Bricked it, demolishing their entire research environment; we also gave them a small "gift" from us. 2/ 




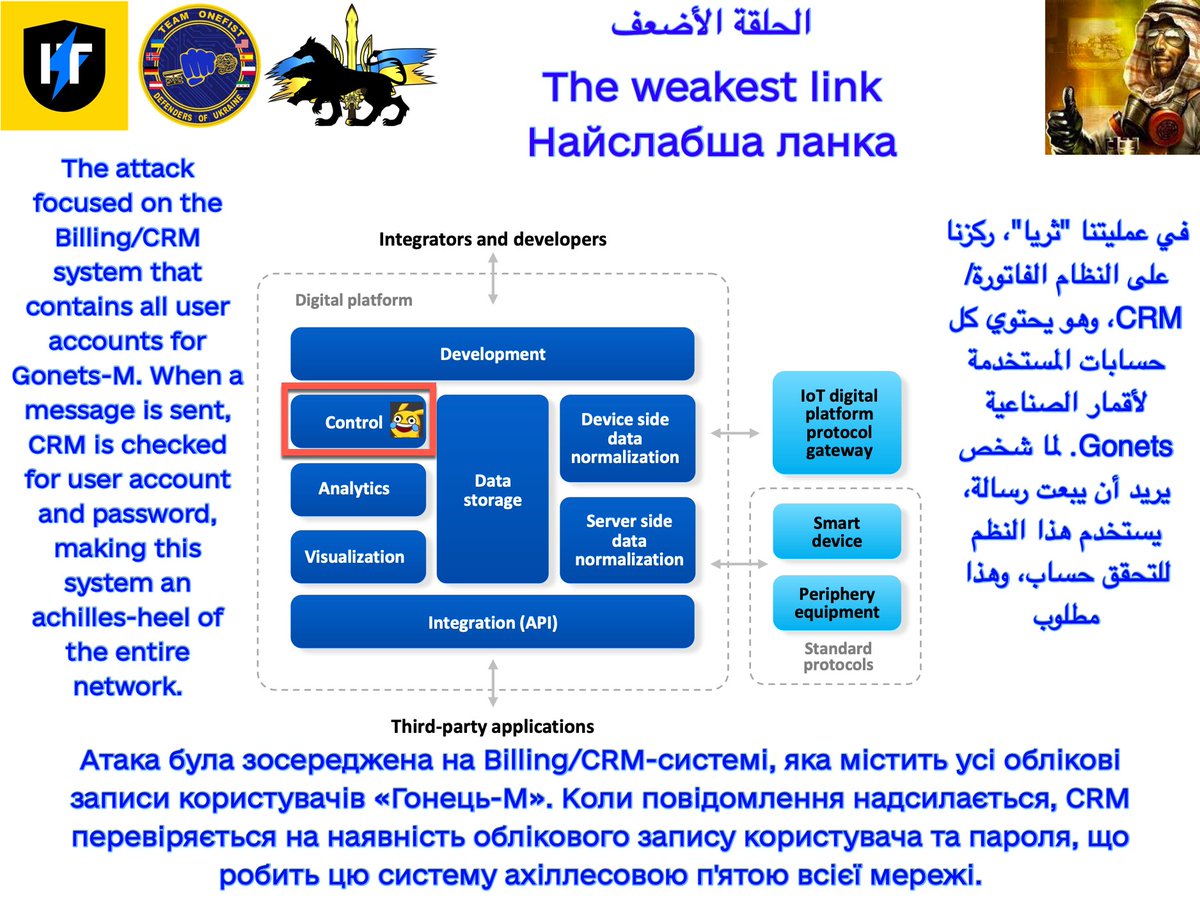
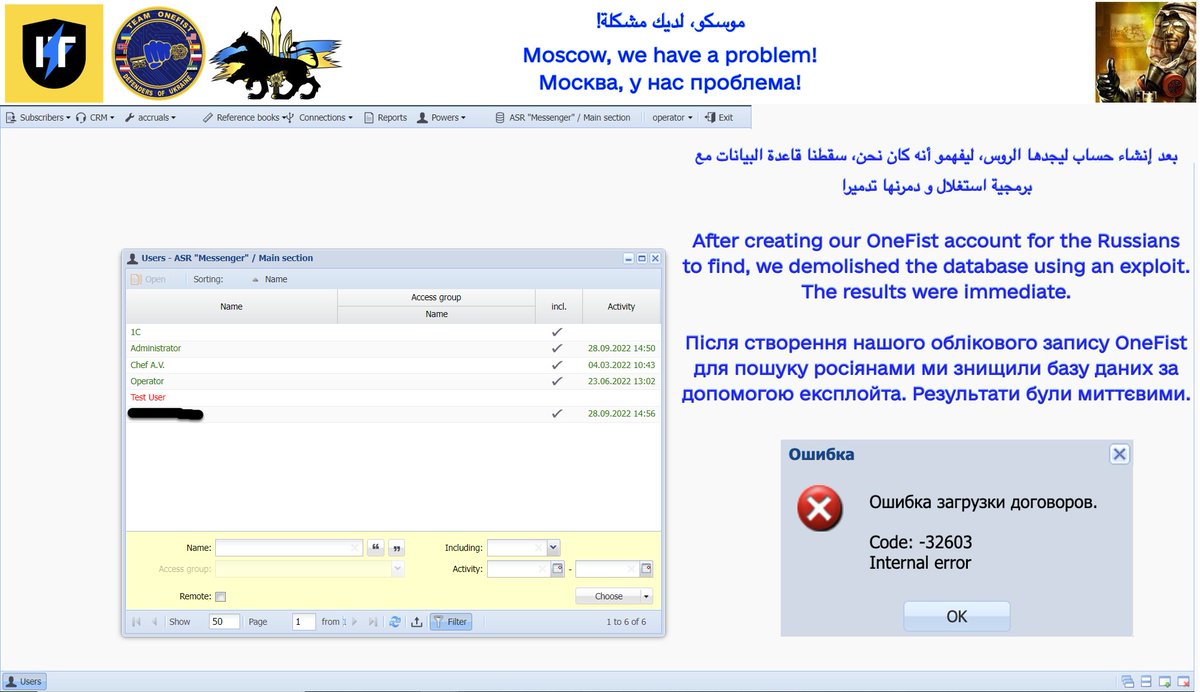
 I successfully penetrated their CRM/client database, which is referenced by the network in order to send/receive messages. We were unable to download the DB and they were monitoring it regularly, so we made the decision to destroy it, which we accomplished without detection. 2/
I successfully penetrated their CRM/client database, which is referenced by the network in order to send/receive messages. We were unable to download the DB and they were monitoring it regularly, so we made the decision to destroy it, which we accomplished without detection. 2/