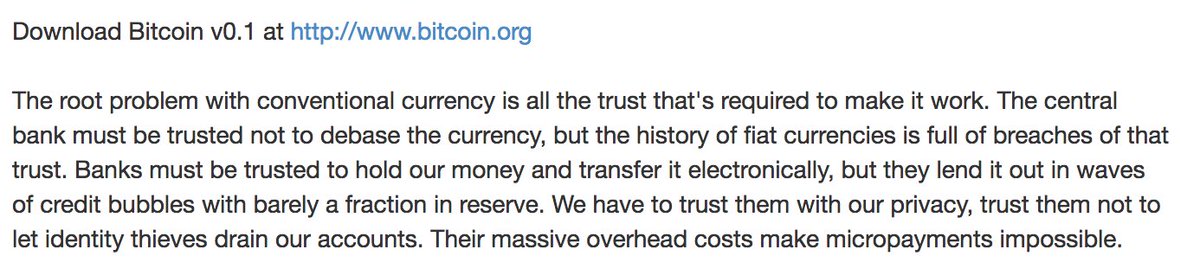
17 years later, the paper is still more relevant than ever: nakamotoinstitute.org/trusted-third-…
Let's dissect what it all means:
MapleChange bit.ly/2OY73vr
Facebook nyti.ms/2NQQNf9
DNS bit.ly/2Svap7n
Yahoo bit.ly/2yIVuOD
Verizon bit.ly/2P1jOFs
Equifax cnnmon.ie/2zegzjn
A TTP is an entity facilitating interactions between parties who don't trust each other but 'trust' the entity. All communication between the parties is reviewed and managed by the TTP.
This implies that a TTP is needed for EVERY key exchange and knows ALL session keys.
1. "Limitations of imagination, effort, knowledge, or time"
2. "Entrenched interests."
3. "Mental transaction costs"
Imagine depending on a TTP for functionality and security of personal property, like jewelry, operating automobiles, or opening your house door by keys
That would be unacceptable.
Currently, security designers invoke or assume TTPs to suit the most secure and computationally efficient security protocols.
"The main point of cryptocurrency was the recognition that trusted third parties are security holes" - @NickSzabo4
iang.org/ssl/pki_consid…
erights.org/talks/pisa/pap…
onion-router.net/Publications.h…
nakamotoinstitute.org/the-god-protoc…
nakamotoinstitute.org/secure-propert…
openssh.com
iang.org/papers/spock.h…