This is a tweet thing about malware PDB paths and their role in the disco, DFIR and/or #threatintel processes, using #KeyBoy as an example.
3/4) What are PDBs?
5) Where/why will I see PDB paths?
6/7) How can I use PDBs paths?
8-n) PDB paths and #KeyBoy
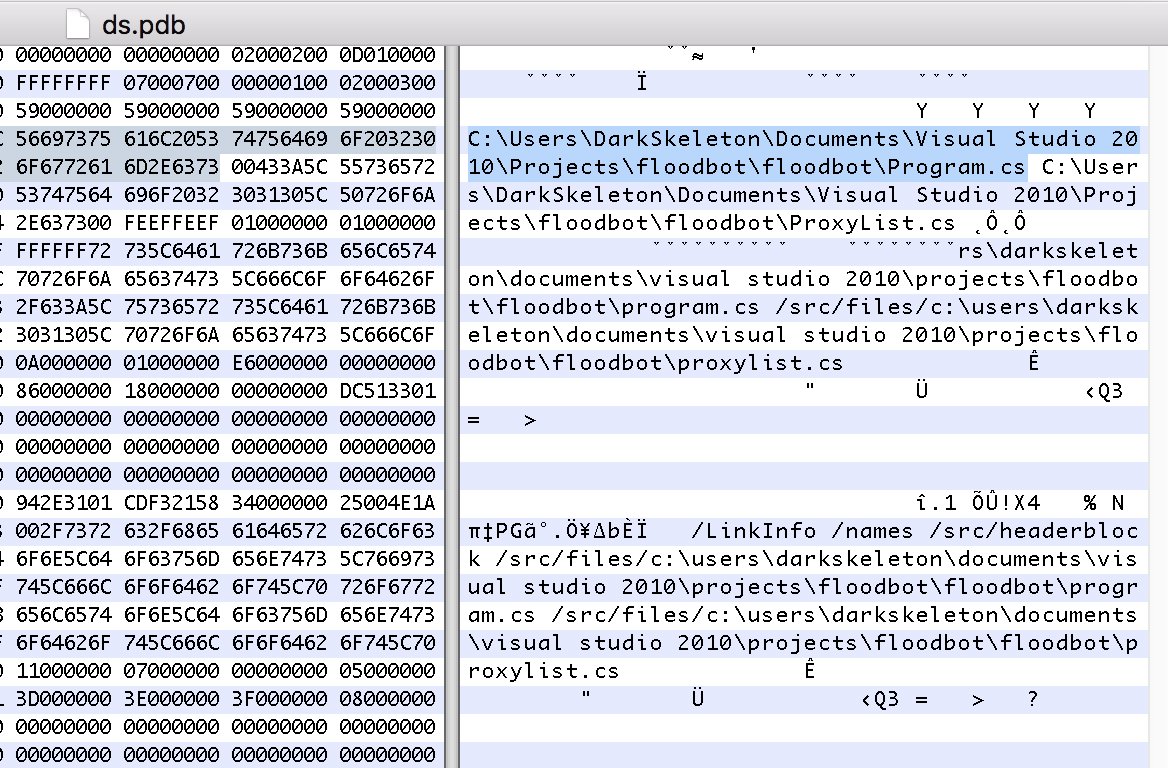
If a malware dev has "debugging enabled", the PDB path is often embedded in the debug portion of a PE upon compilation. The PDB path gives insight into the dev computer and can leave clues that for analysts discover additional malware.
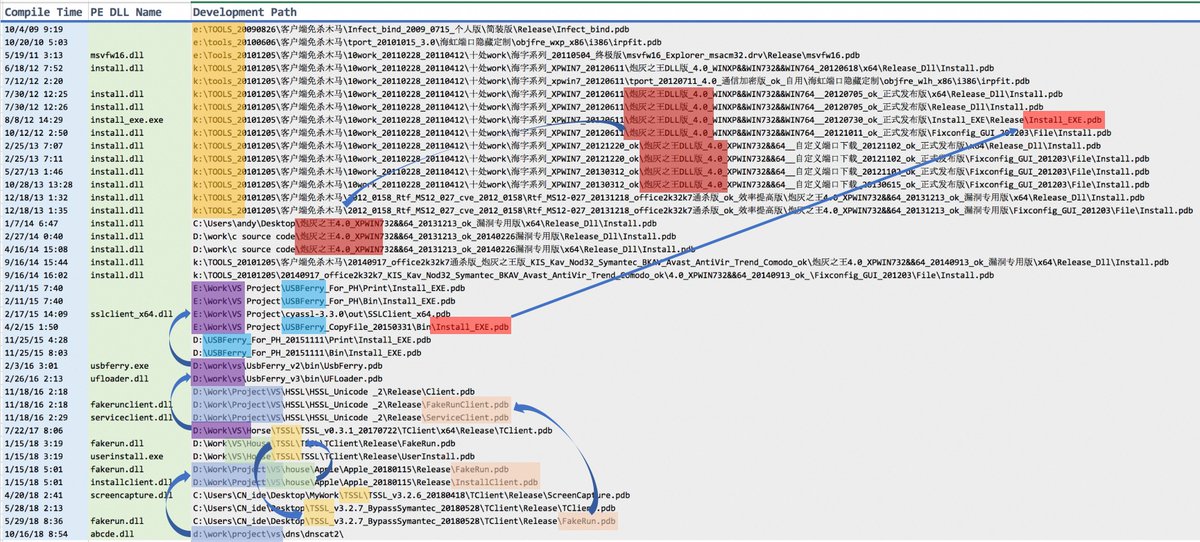
I used the unique values in the PDB to start searching for related malware and ended up with a cluster of ~300 samples, ~250 PEs, ~80 of which had embedded PDB paths in the main file or a subfile.