Effectively you can't do anything by knowing this unless you are superstar hacker with a lot of luck.
npmjs.com/package/crypto…
But nothing like that is there in the js file.
Did BJP update their website within a day or u faked the screenshot? Hope you will answer
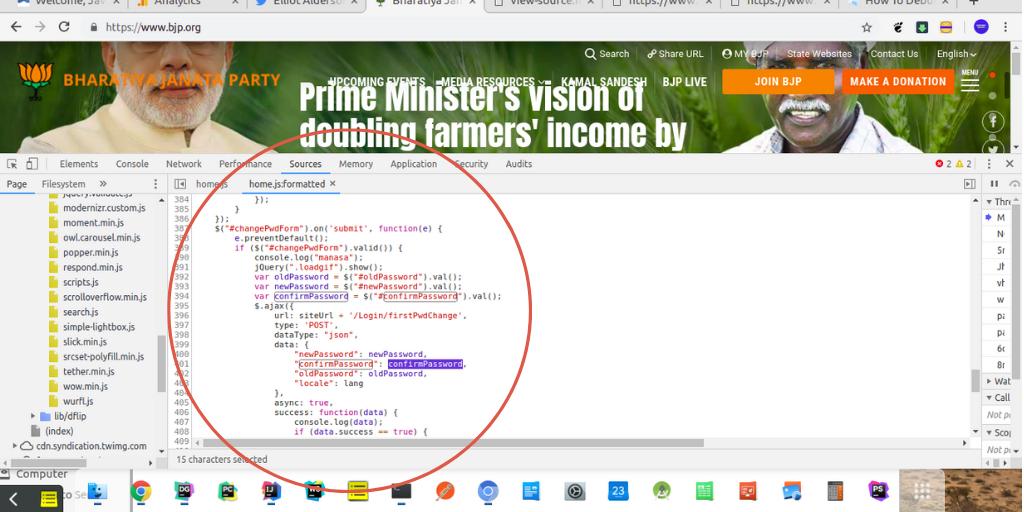
Now, tell the world what vulnerability it was and how it can be misused by the hacker?