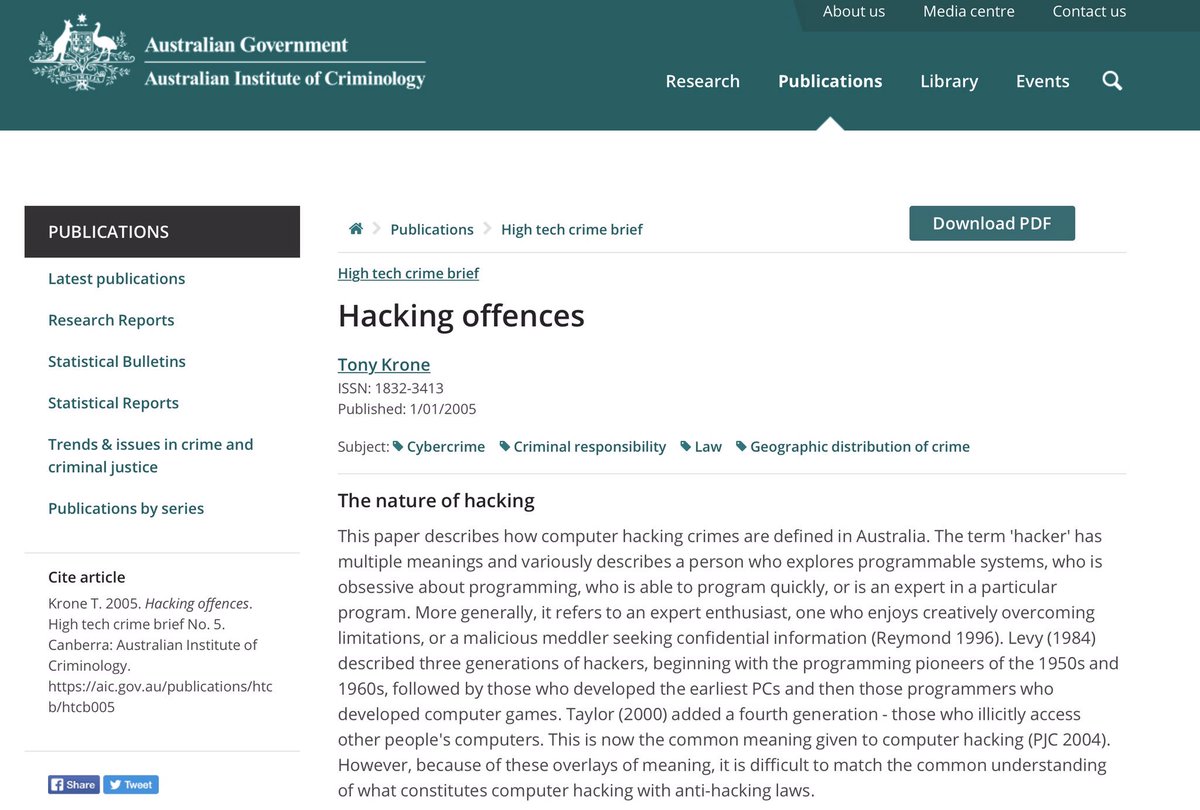
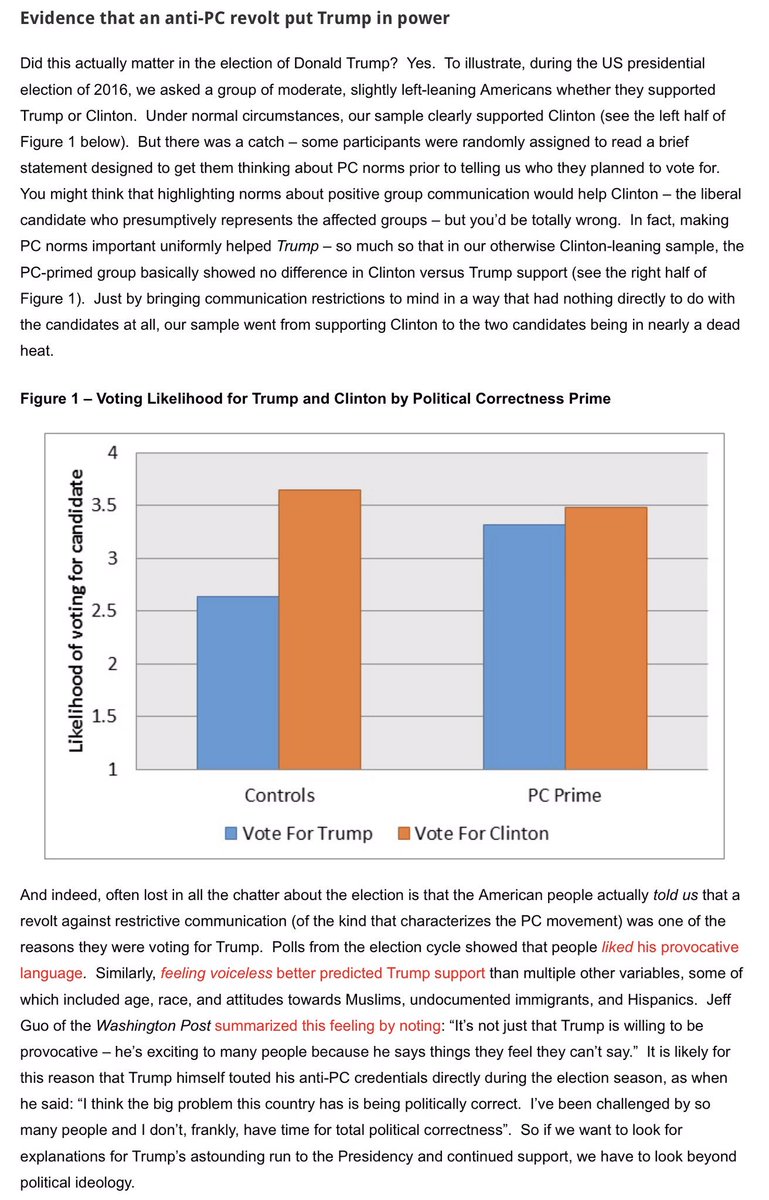
What it comes down to is what constitutes hacking?
This is very important in this day and age.

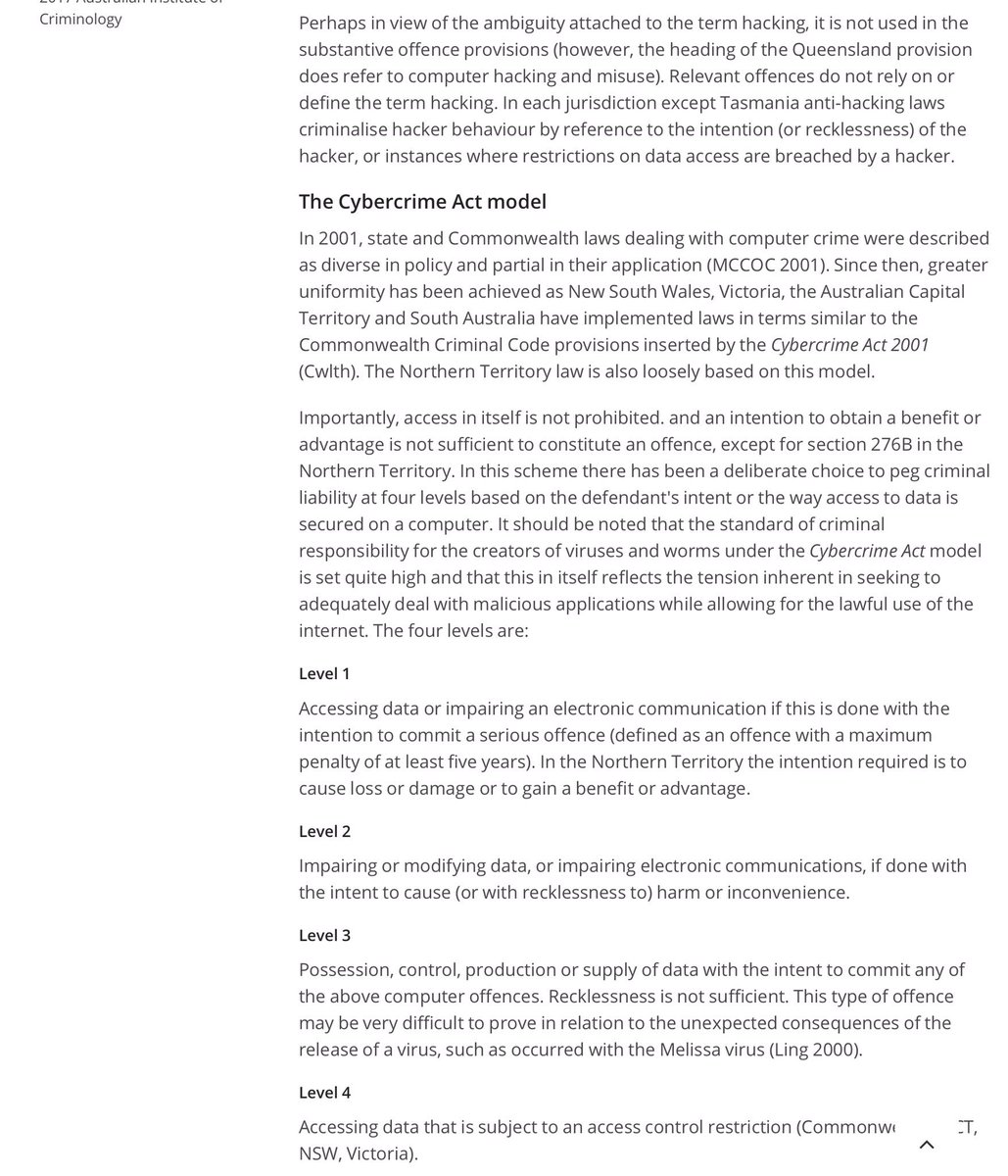
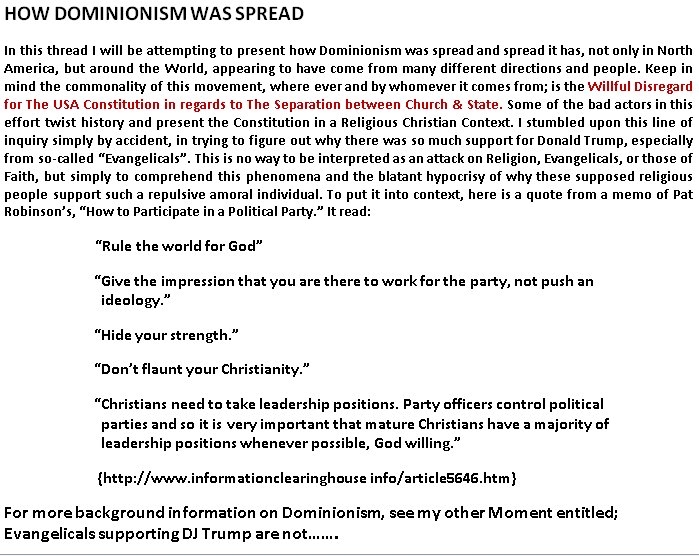
(My apologies for the format. This is a back up. My blog went down Google’s history black hole when I forgot the login to renew it. Interestingly Big Brother Google even deleted access to the published posts.)

Just because someone says they are a hacktivist, it does not necessarily mean they are. Motive really matters. Hacktivists hack in the public interest. But this reason does not necessarily go down well in court (which tend to favour those hacked).

This includes those who hack for financial, political or other gain, or hack to maliciously damage systems or to obtain information to weaponise against people or orgs etc for gain for themselves or gain for those for whom the hacking is done



This is hacking done by or for govts.
Govts that spy/hack on their own people or others generally consider this good form, while hypocritically criticise others for doing it.
Hacking is part of Big Brother think and 1984 style surveillance



This activity may be carried out by or for governments, or by or for others. It is the most dangerous form of hacking - and should not be allowed.