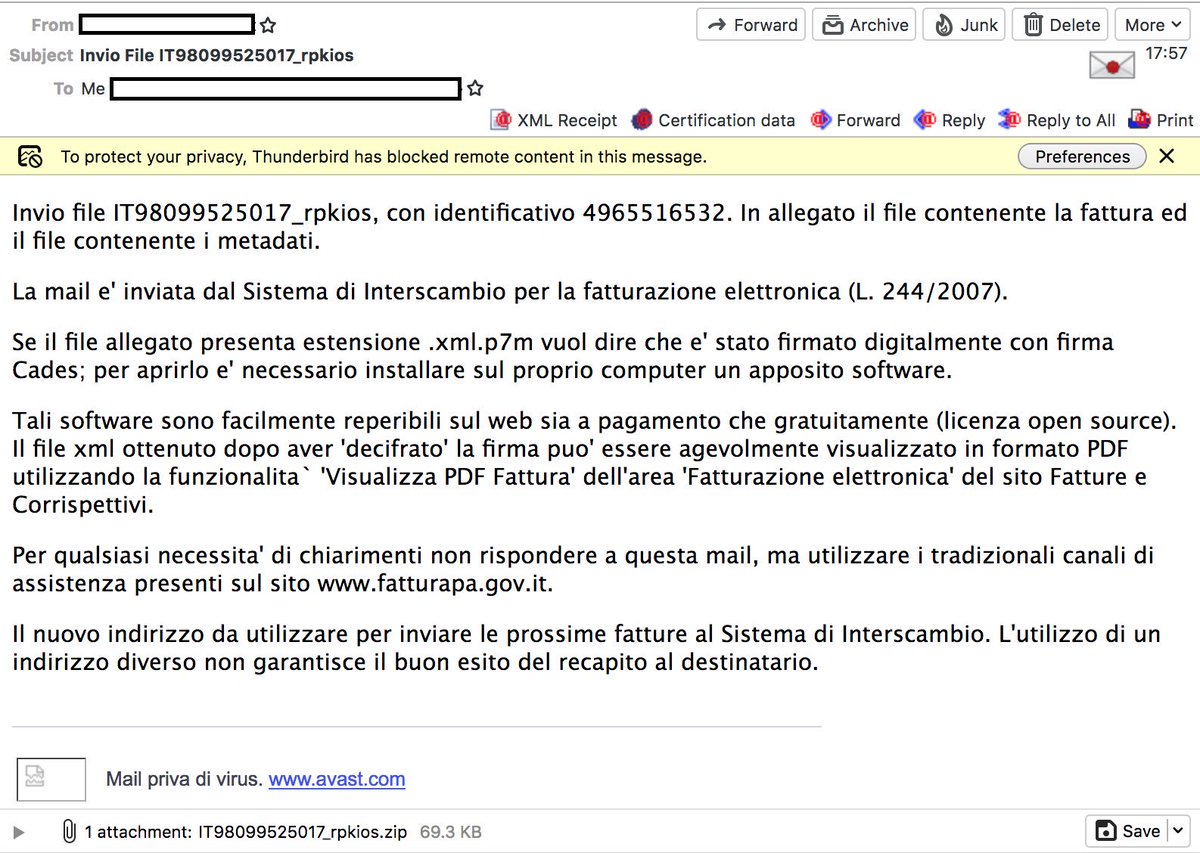
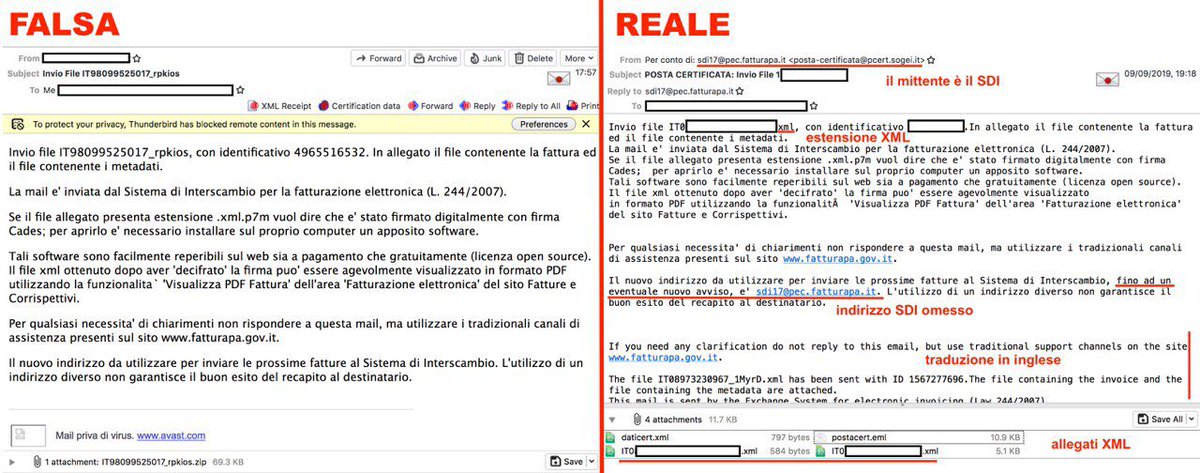
Helps in identifying existing samples, but commercial services limit searches. If you can't index yourself you are probably out of luck here (2/7)
Some blogs contained interesting factual snippets, but only really started being comprehensive around 2012. Previously it was just elements of interest or forum archives. Recording hashes for research wasn't typical. (3/7)
Even commercial PDNS sources rarely go back later than around 2010 when most came online and started collecting data. I'd say 2009 is pretty much the event horizon unless you are really lucky (4/7)
@virustotal came online around 2006 and is pretty much the largest commercial repository available to researchers, but without a hash you are unlikely to retrieve. No doubt there are older private archives but processing that far back is a challenge (5/7)
⚫️🔚 WHOIS (~2000)
Historic WHOIS records can be a spotty the further back you go (h/t @NateBeachW), and it's also worth considering the artificial GDPR event horizon which cloaks data going forward from here. Yes, I'm still salty. (8/7)
Records of IP address assignments can be challenging depending on the registry, and there's no real requirement to publish allocations. RIPE (apps.db.ripe.net/db-web-ui/#/qu…) and APNIC (apnic.net/static/whowas-…) have some ok tools though (9/7)