First, some basics (this is simplified):
A cookie is a key/value pair (a variable) that allows websites to save data in users' web browsers. 1/
Since this happens automatically, it's mostly invisible to users. 7/
Until very recently, third-party cookies were stored by browsers by default, and a user had to take proactive steps to configure their browser to block them. 9/
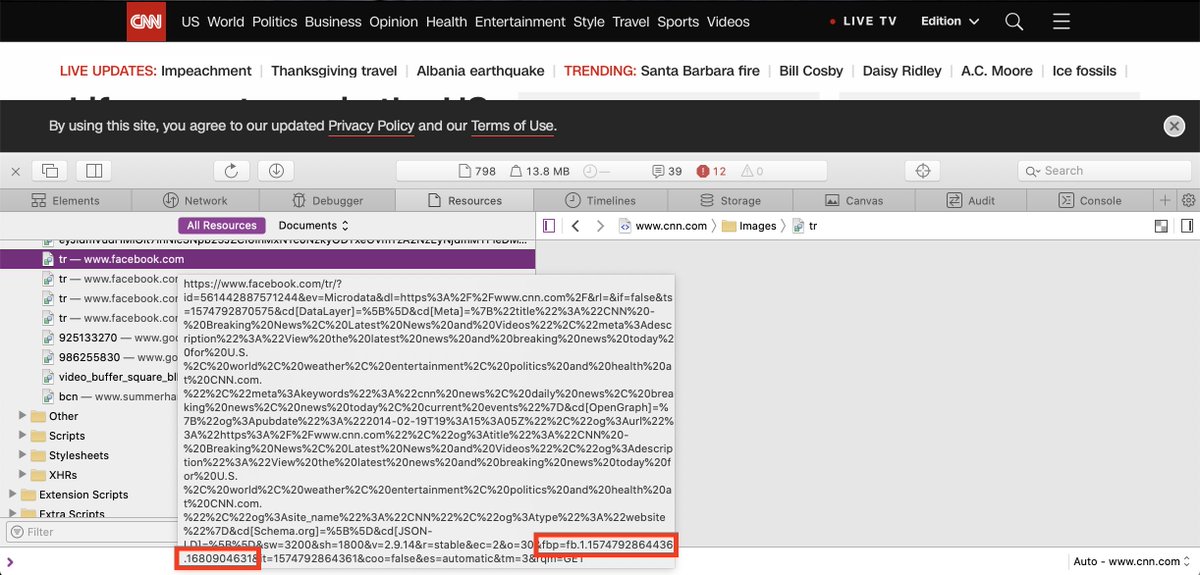
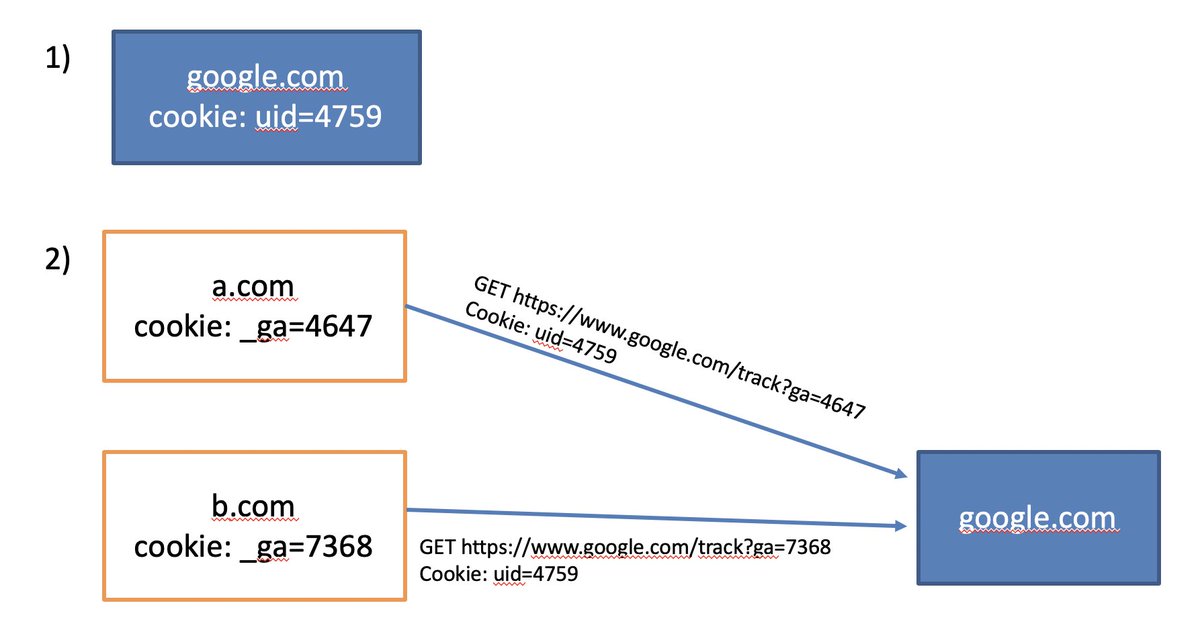
For security, cookies are only sent to the domain that set them: a browser won't send facebook.com cookies set by cnn.com. 11/
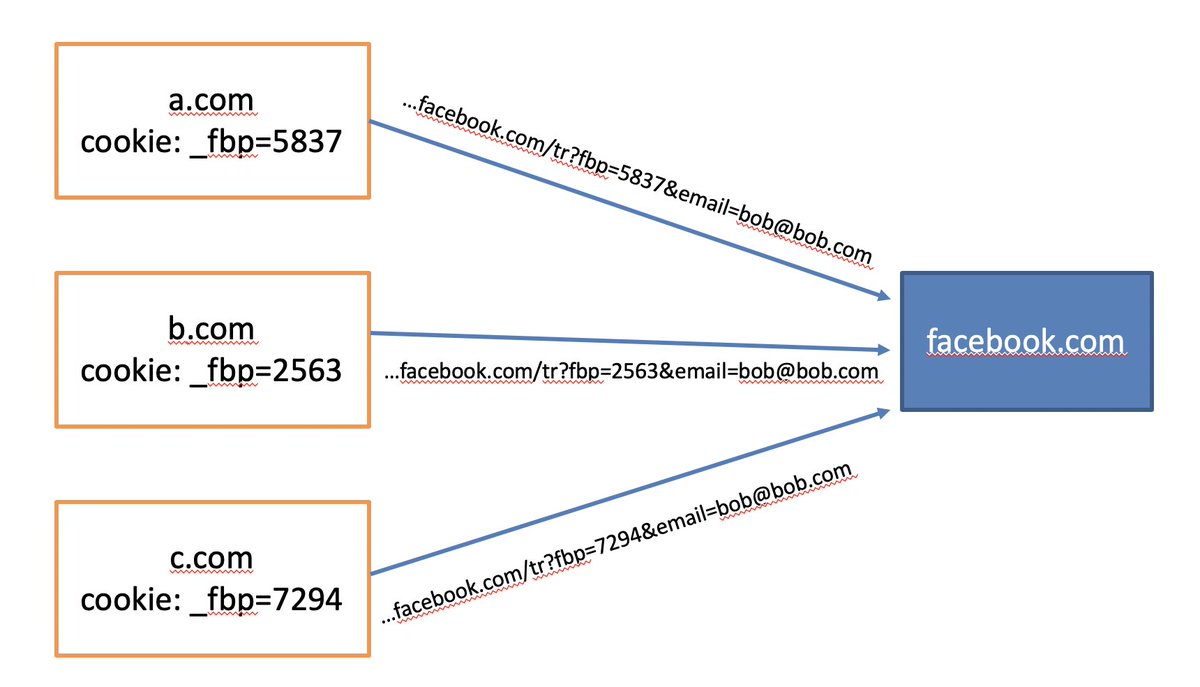
If CNN wants to automatically and uniquely identify its users to Facebook, they can't simply share the same cookie. They need to do what's known as "cookie syncing." 12/
13/
Because many third-party cookies are blocked by privacy tools when users don't want to be tracked, many of the biggest players have shifted to colluding with websites to set first-party cookies instead. 14/
Now, tracking companies use 1 of 2 ways to set these as 1st-party cookies (less likely to be blocked): 18/
facebook.com/business/help/… 19/
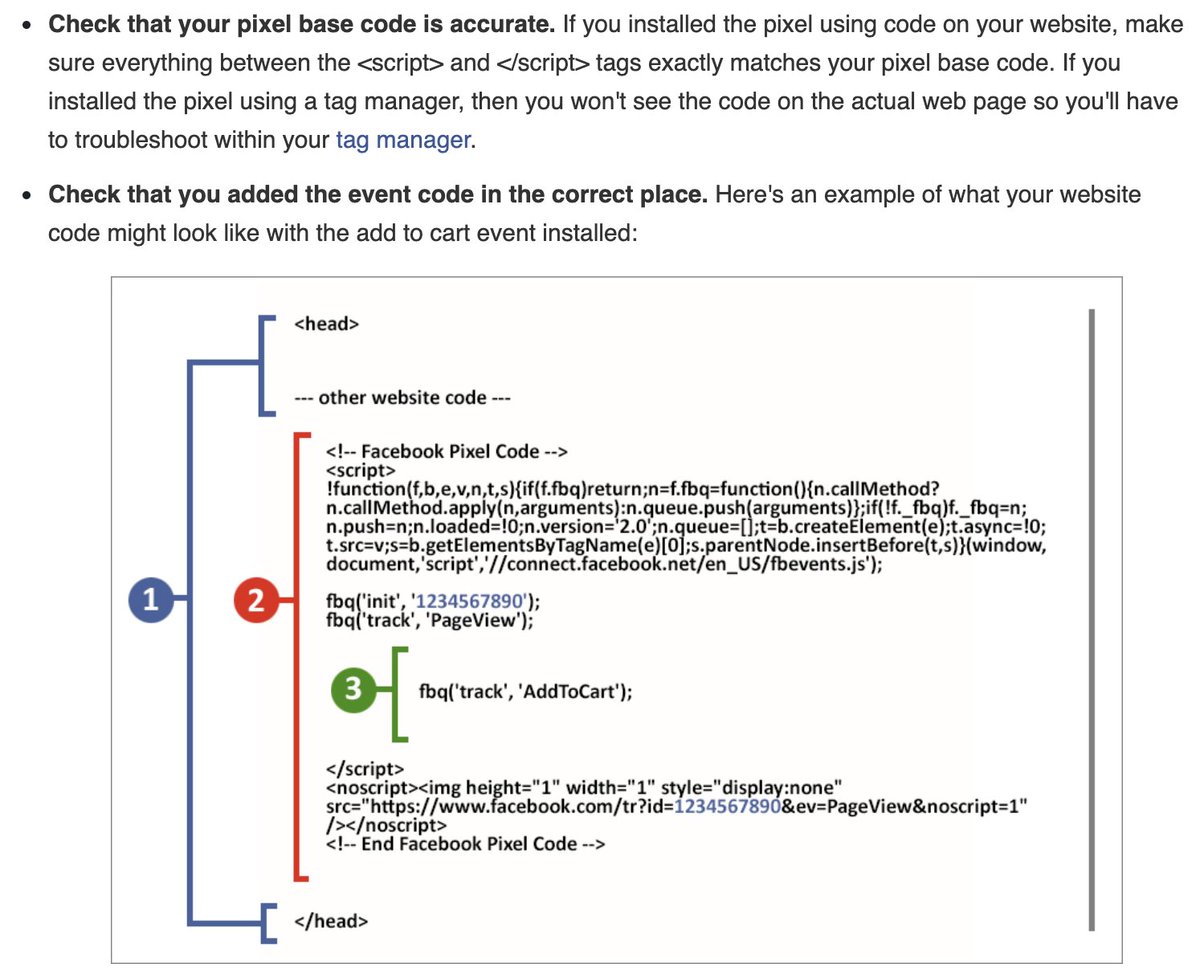
20/
developers.facebook.com/ads/blog/post/…
However, the websites setting the cookies may not have this information. 25/
26/
We previously showed that users can be identified based on the fonts they have installed: guanotronic.com/~serge/papers/… 27/
When software blocks 3rd-party cookies, they generally do so by preventing cookies from being *set* by 3rd-parties; they often don't prevent existing cookies from being *sent* to 3rd parties. 28/
29/
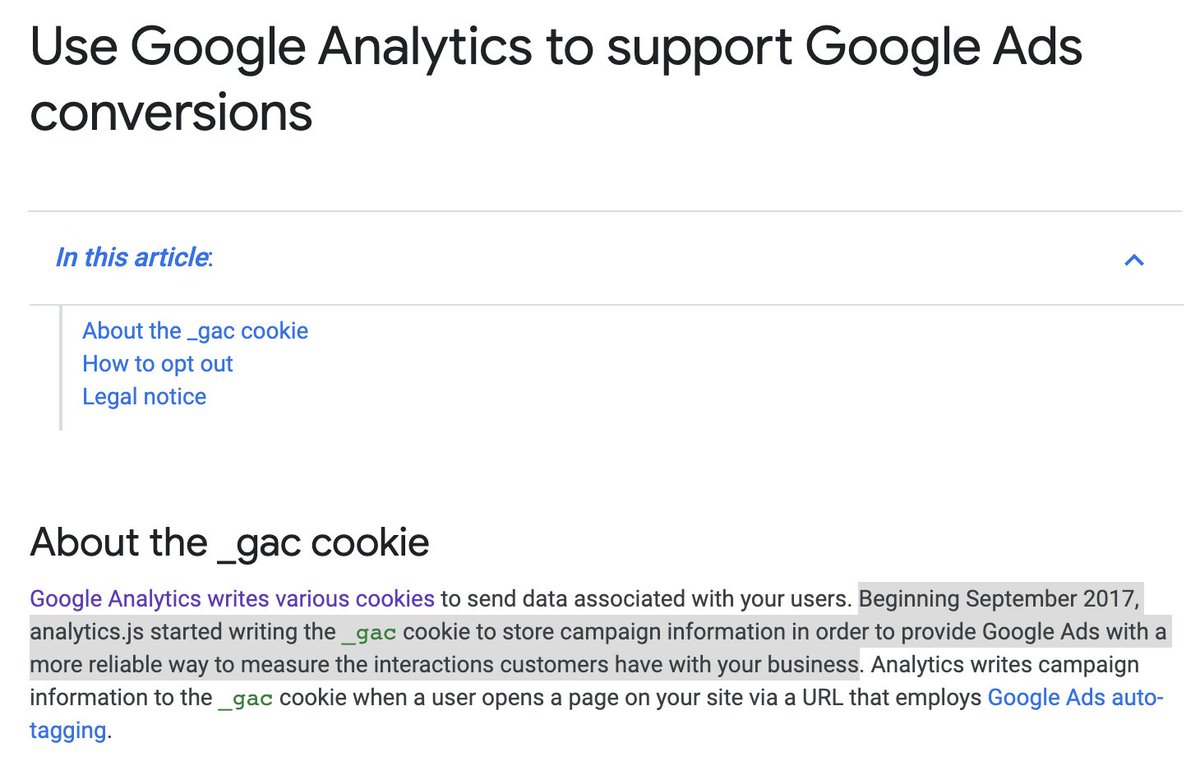
In most of these cases, the companies' marketing materials make this very clear. 33/
Here, "more reliable" means making it harder for users to opt out.
34/
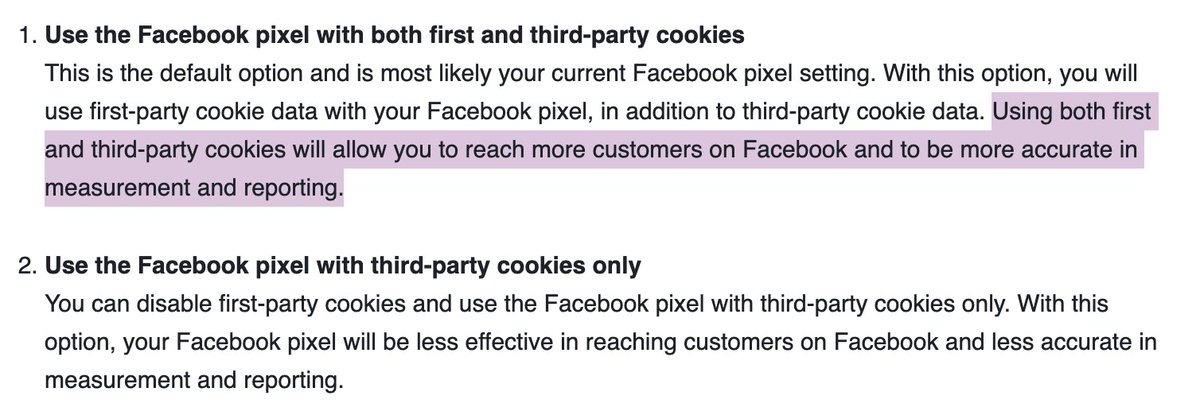
...using only third-party cookies is "less effective." 35/
Fin.